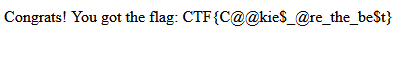CTF Scoreboard https://ectf.nitk.ac.in/scoreboard
CTF Challenges https://ectf.nitk.ac.in/challenges
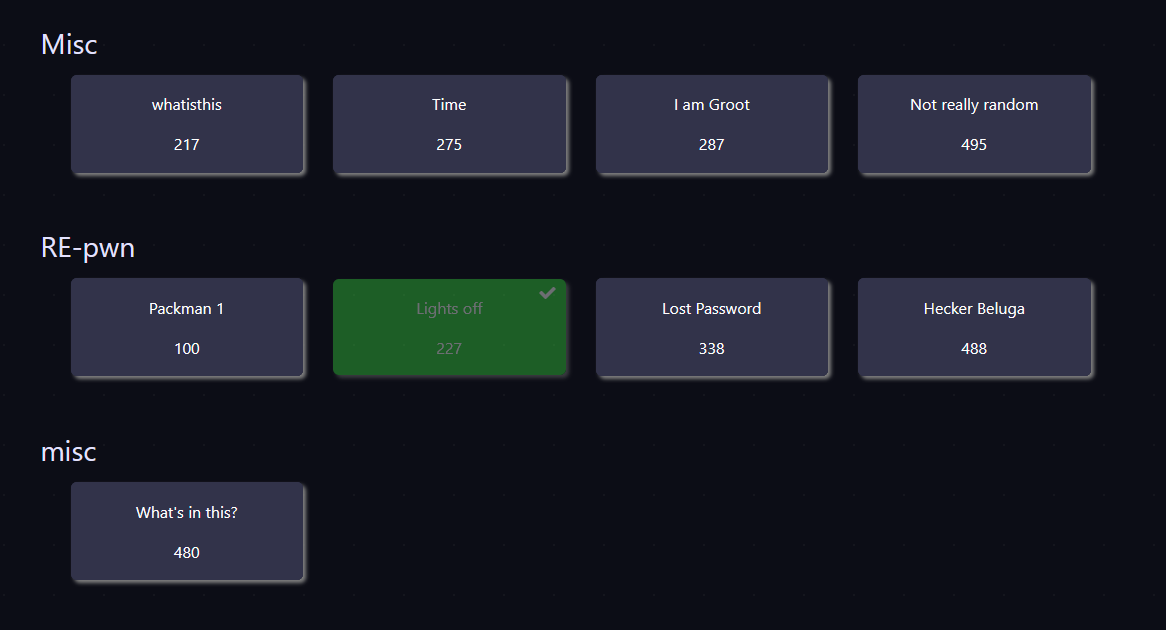
Final Score
DATE : 05/03/22 10h30 UTC+1, to 06/03/22 10h30 UTC+1.
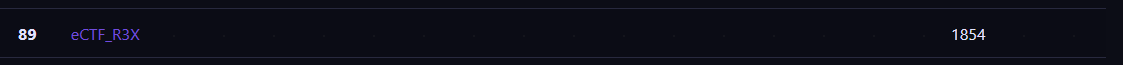
FINAL SCORE : 1854
SCOREBOARD : 89/311
My CTF playing time : 05/03/22 10h30 to 05/03/22 18h
Mode : Solo (pseudo : R3X, Team : eCTF_R3X)
I finished in 89th position out of 311 for this CTF challenge :
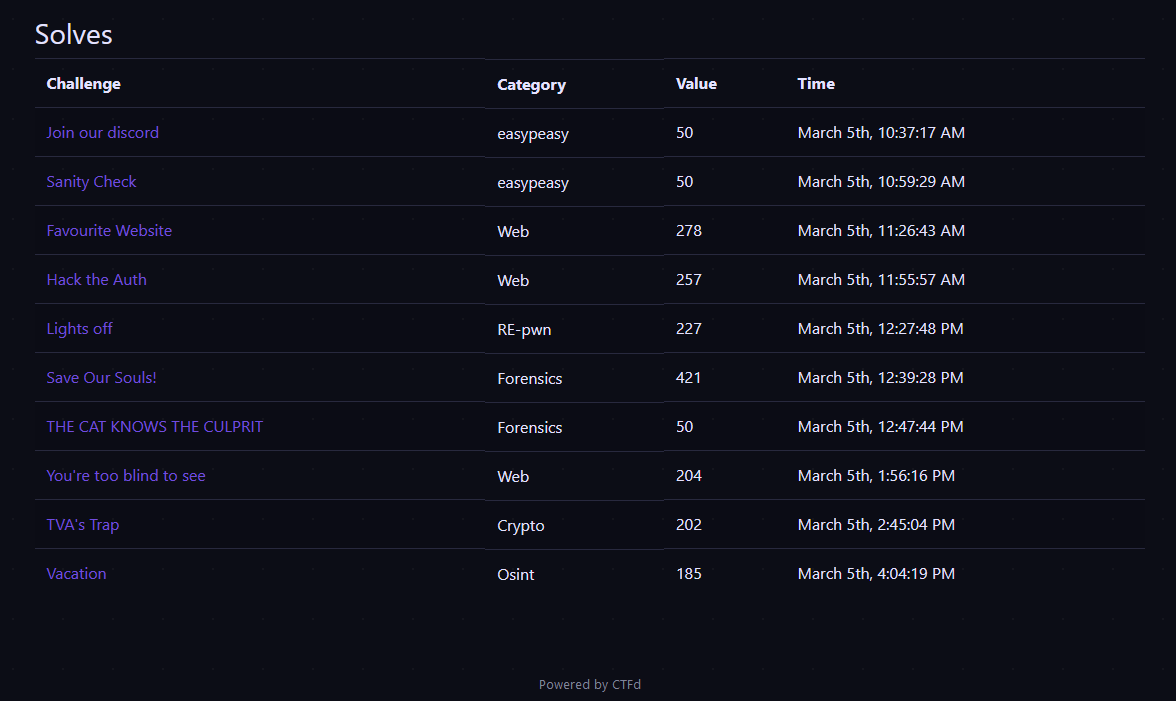
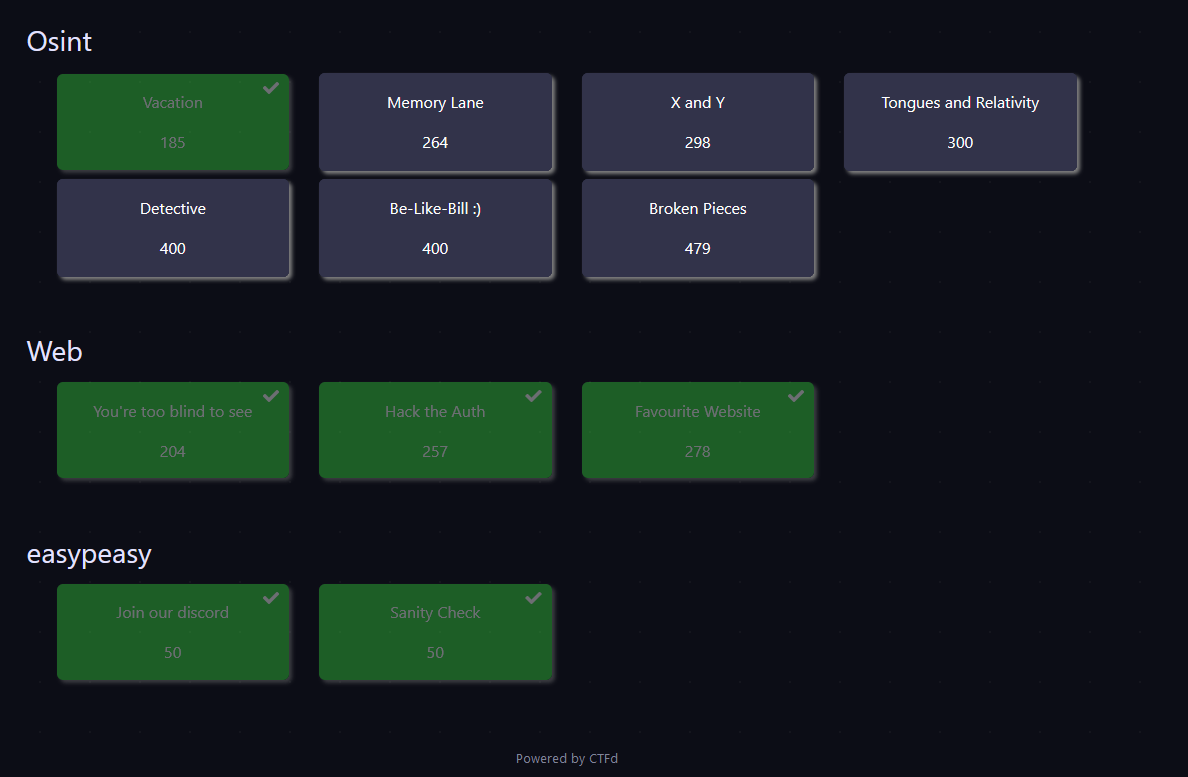
I solved the following chalenges :
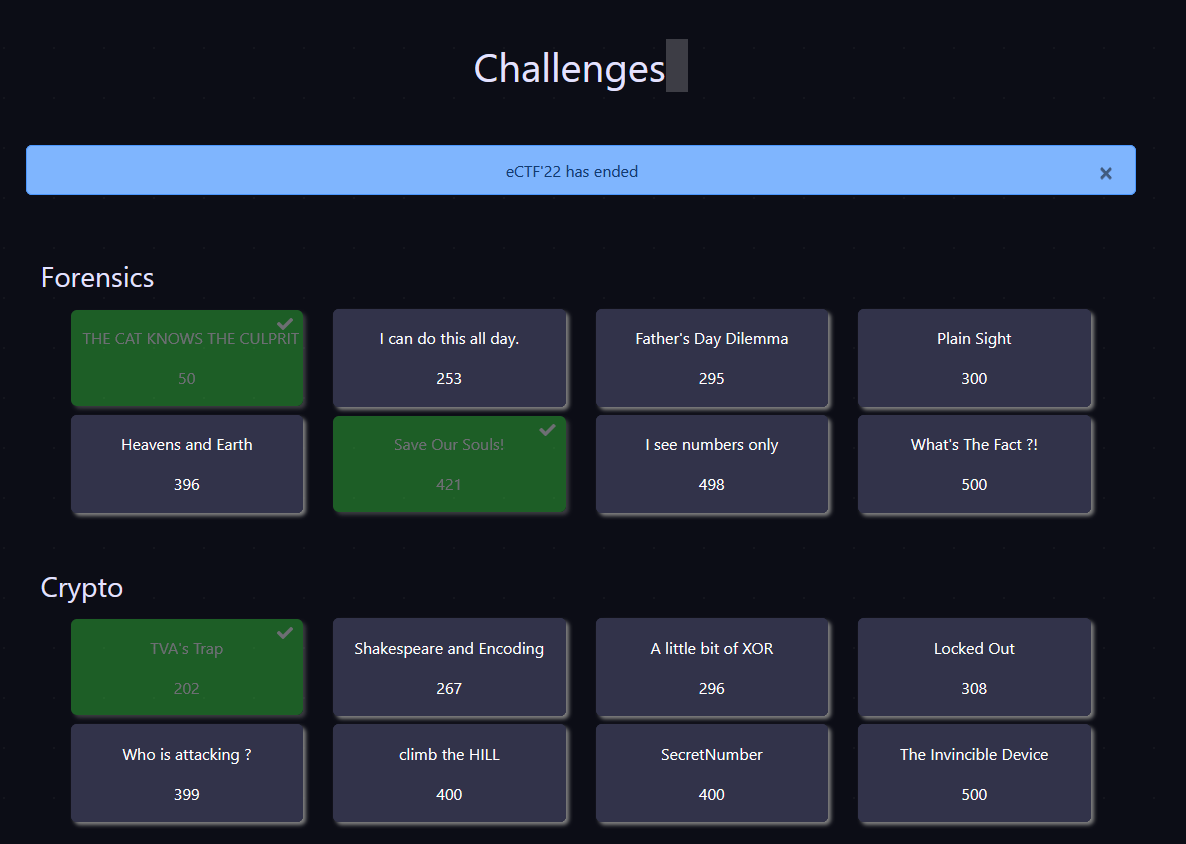
Here’s a view a the available challenges (except Blue Team challenges which were no longer available post event) :
I’ll put only challenges i got through in the next sections.
Easypeasy - Join our Discord
SCORE: 50
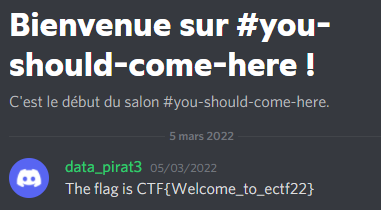
Looking for an interesting channel :
Here we go, i get the first easy flag : CTF{Welcome_to_ectf22}
Easypeasy - Sanity Check
SCORE: 50
The flag appears to us directly : CTF{Welcome}
Web - You’re too blind to see
SCORE: 300
RESSOURCE : website link : https://chinmayasharma-hue.github.io/CTF2022.gitbhub.io/
Open the link of the website :
Ok, let’s look for the source :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
<html>
<!-- bmV2ZXJnb25uYWxldHlvdWRvd24wMTIyQGdtYWlsLmNvbSBrbm93cyB0aGUgcGFzc3dvcmQ -->
<head>
<title>Login Form</title>
<link rel="stylesheet" href="css/style.css">
</head>
<script src="https://ajax.googleapis.com/ajax/libs/jquery/3.4.0/jquery.min.js"></script>
<script src="https://cdnjs.cloudflare.com/ajax/libs/forge/0.8.2/forge.all.min.js"></script>
<script type="text/Javascript">
function generateHash(plainText) {
var md = forge.md.sha256.create();
md.start();
md.update(plainText, "utf8");
var hashText = md.digest().toHex();
return hashText;
}
const loginForm = document.getElementById("login");
const loginButton = document.getElementById("login-form-submit");
function checkLogDetails() {
var username = document.getElementById("Uname").value;
var password = document.getElementById("Pass").value;
if (username == "Rick Astley" && generateHash(password) == "1b638a7a9a56a4485ebd95816d1d8abf0576cdbf39854c6dd5cb47c3c53f48be") {
redirect_site = 'redirect'+ password + '.html';
window.open(redirect_site, '_blank');
} else {
window.open('https://www.youtube.com/watch?v=dQw4w9WgXcQ');
}
}
</script>
<body>
<h2>Login Page</h2>
<div align="center" class='login'>
<form id="login" method="get" onsubmit="checkLogDetails()">
<label><b>User Name
</b>
</label><br><br>
<input type="text" name="Uname" id="Uname" placeholder="Username">
<br><br>
<label>
<b>Password</b>
</label><br><br>
<input type="Password" name="Pass" id="Pass" placeholder="Password">
<br><br><br><br>
<input type="submit" value="Login" id="login-form-submit">
<br><br>
</form>
</div>
</body>
</html>
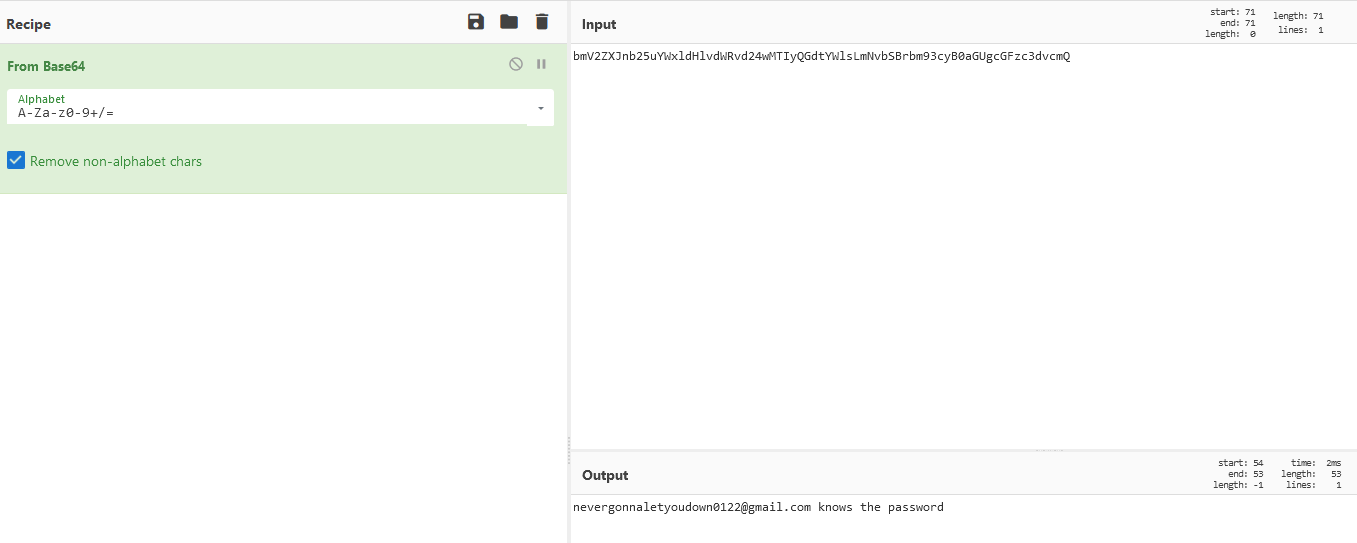
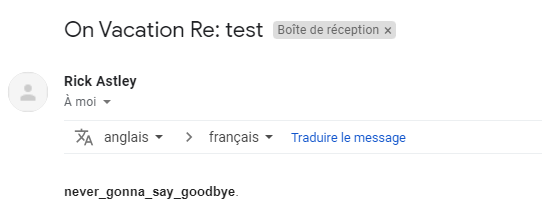
Found a comment to seems to be Base64 :
It’s said that “nevergonnaletyoudown0122@gmail.com” knows the password. Let’s write an email to this person asking the flag :
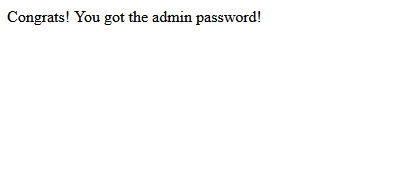
I got the flag : CTF{never_gonna_say_goodbye}
Web - Hack the Auth
SCORE: 300
RESSOURCE : website link : https://wec-ctf-2022-web.herokuapp.com/q1
Let’s take a look at this website :
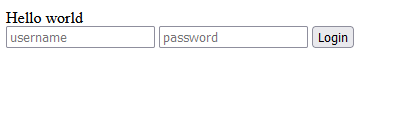
It’s a relatively simple page, what is his source :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>WEC</title>
</head>
<body>
<div> Hello world </div>
<input type="text" name="username" placeholder="username">
<input type="password" name="password" placeholder="password">
<button onclick="userAuthentication()">Login</button>
<script type="text/javascript">
var sha256 = function sha256(ascii) {
function rightRotate(value, amount) {
return (value>>>amount) | (value<<(32 - amount));
};
var mathPow = Math.pow;
var maxWord = mathPow(2, 32);
var lengthProperty = 'length'
var i, j;
var result = ''
var words = [];
var asciiBitLength = ascii[lengthProperty]*8;
var hash = sha256.h = sha256.h || [];
var k = sha256.k = sha256.k || [];
var primeCounter = k[lengthProperty];
var isComposite = {};
for (var candidate = 2; primeCounter < 64; candidate++) {
if (!isComposite[candidate]) {
for (i = 0; i < 313; i += candidate) {
isComposite[i] = candidate;
}
hash[primeCounter] = (mathPow(candidate, .5)*maxWord)|0;
k[primeCounter++] = (mathPow(candidate, 1/3)*maxWord)|0;
}
}
ascii += '\x80'
while (ascii[lengthProperty]%64 - 56) ascii += '\x00'
for (i = 0; i < ascii[lengthProperty]; i++) {
j = ascii.charCodeAt(i);
if (j>>8) return;
words[i>>2] |= j << ((3 - i)%4)*8;
}
words[words[lengthProperty]] = ((asciiBitLength/maxWord)|0);
words[words[lengthProperty]] = (asciiBitLength)
for (j = 0; j < words[lengthProperty];) {
var w = words.slice(j, j += 16);
var oldHash = hash;
hash = hash.slice(0, 8);
for (i = 0; i < 64; i++) {
var i2 = i + j;
var w15 = w[i - 15], w2 = w[i - 2];
var a = hash[0], e = hash[4];
var temp1 = hash[7]
+ (rightRotate(e, 6) ^ rightRotate(e, 11) ^ rightRotate(e, 25))
+ ((e&hash[5])^((~e)&hash[6]))
+ k[i]
+ (w[i] = (i < 16) ? w[i] : (
w[i - 16]
+ (rightRotate(w15, 7) ^ rightRotate(w15, 18) ^ (w15>>>3))
+ w[i - 7]
+ (rightRotate(w2, 17) ^ rightRotate(w2, 19) ^ (w2>>>10))
)|0
);
var temp2 = (rightRotate(a, 2) ^ rightRotate(a, 13) ^ rightRotate(a, 22))
+ ((a&hash[1])^(a&hash[2])^(hash[1]&hash[2]));
hash = [(temp1 + temp2)|0].concat(hash);
hash[4] = (hash[4] + temp1)|0;
}
for (i = 0; i < 8; i++) {
hash[i] = (hash[i] + oldHash[i])|0;
}
}
for (i = 0; i < 8; i++) {
for (j = 3; j + 1; j--) {
var b = (hash[i]>>(j*8))&255;
result += ((b < 16) ? 0 : '') + b.toString(16);
}
}
return result;
};
var userAuthentication = function() {
var username = document.getElementsByName('username')[0].value;
var password = document.getElementsByName('password')[0].value;
var hash = sha256(password);
if(hash === "dfbec338b51c5643ba481625e1075236d3a9a07fbd6393763f253e99024958a4" && username === "admin") {
window.location = "./q1?username=admin&password=" + password;
} else {
alert("Invalid username or password");
}
};
</script>
</body></html>
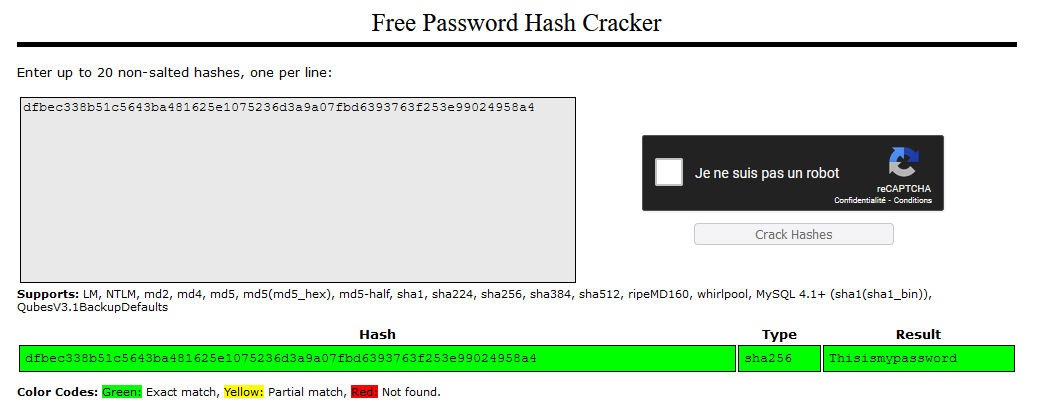
There is an interesting “userAuthentication” function directly in the webpoge. Can we tried to get the clear text of the hash ?
Yes, Crackstation knows this hash :
So i can used the harcode username and the found password to log on the form :
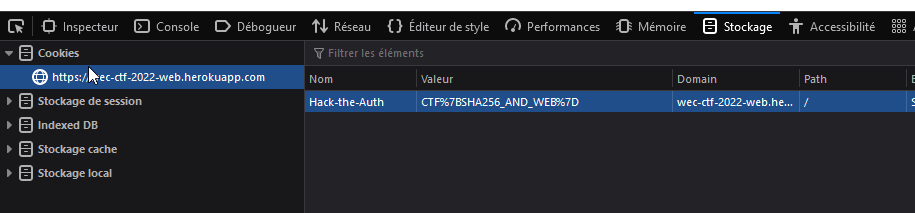
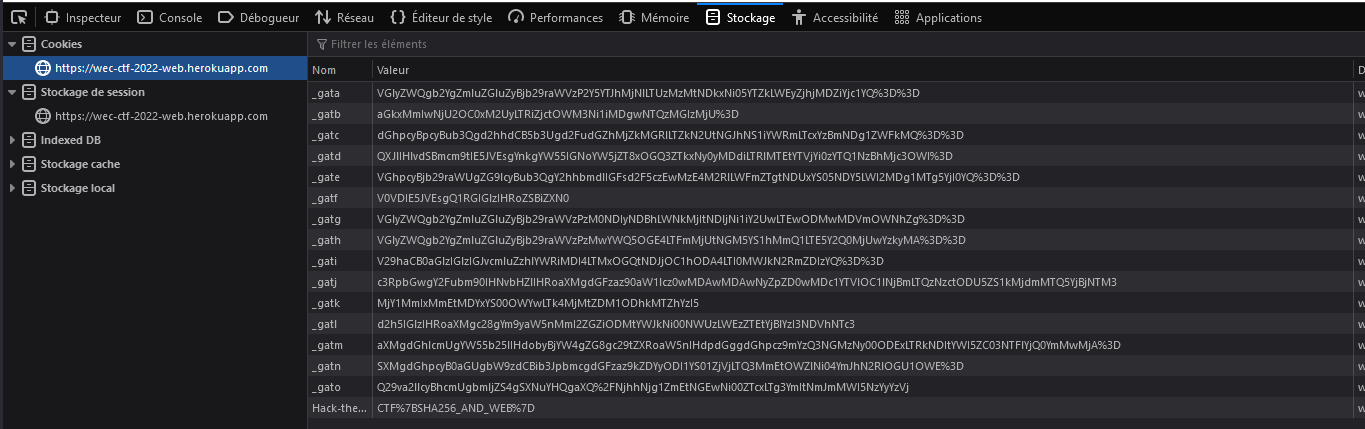
Ok, seems there is one more thing to do. Checked the cookies :
I found the flag there : CTF{SHA256_AND_WEB}
Web - Favourite Website
SCORE: 300
RESSOURCE : website link : https://wec-ctf-2022-web.herokuapp.com/q2
What’s the webiste looks :
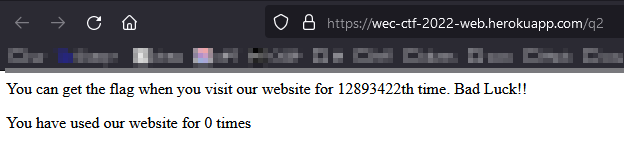
ok, let’s refresh the pages several times to see what does the counter :
Ok, what’s up in the cookies ?
Ok, it’s all base64 messages, let’s decode some of these :
1
2
3
4
5
6
7
Tired of finding cookies?f9a2a23e-5333-4916-9a6d-a2f8c06bb75a
ÃÜ
[...]
WEC NITK CTF is the best
[...]
still cannot solve this task?times=00000007&id=0075a5e8-e60f-4377-859e-d27f149b0c537
[...]
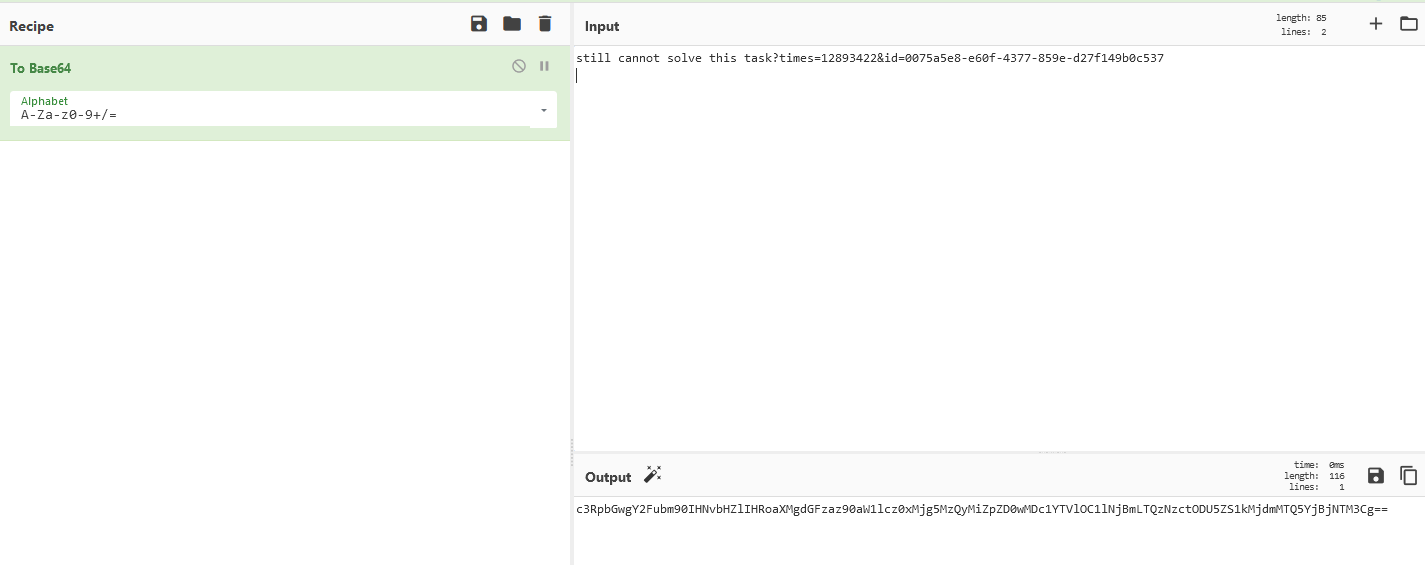
One of the cookies seems intersting. Let’s modify this cookie with ?times=12893422 :
Then refreshed the page :
Flag : CTF{C@@kie$_@re_the_be$t}
Osint - Vacation
SCORE: 200
I turn a lot with no success until i found the @tig3r_and_b3ar on google as an Instagram account.
Only one photo, but nothing interesting.
Checking followers : 6, time loss.
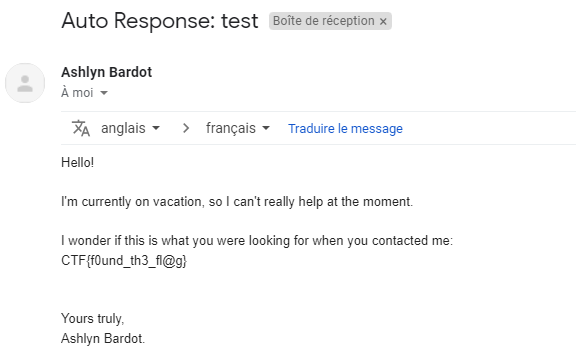
Checking the following : 1 account “ashlynbardot” who is a Photographer. Seems i found the right person. The profile say “contact me at ashlyn_bardot@yahoo.com”.
Like the previous challenge with the email, i sent this email address an hello mail too :
It gives me the flag as intended : CTF{f0und_th3_fl@g}
RE-pwn - Ligts off
SCORE: 300
RESSOURCE : main.c
RESSOURCE : nc40.114.6.1675555
Let’s see the chall :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~]
└─$ nc 40.114.6.167 5555
Starting!
Provide Your Magic Key:
2665
ACCESS DENIED
By trial error for some strategic values (XXX, 1, -1, 0):
┌──(kali㉿kali)-[~]
└─$ nc 40.114.6.167 5555
Starting!
Provide Your Magic Key:
0
ACCESS GRANTED O_o
CTF{L1Ghts=O}
Flag : CTF{L1Ghts=O}
Let’s move to the next challenge.
Crypto - TVA’s Trap
SCORE: 300
RESSOURCE : 8-6-4.txt
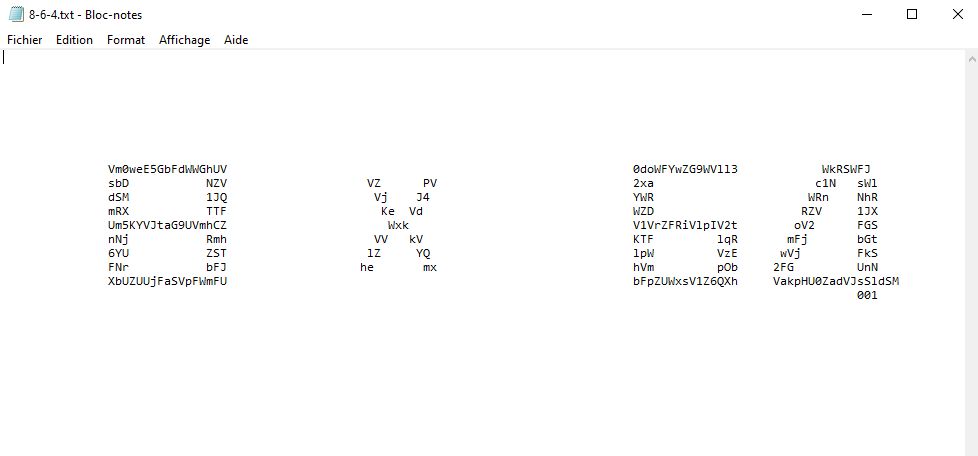
Opened the txt file :
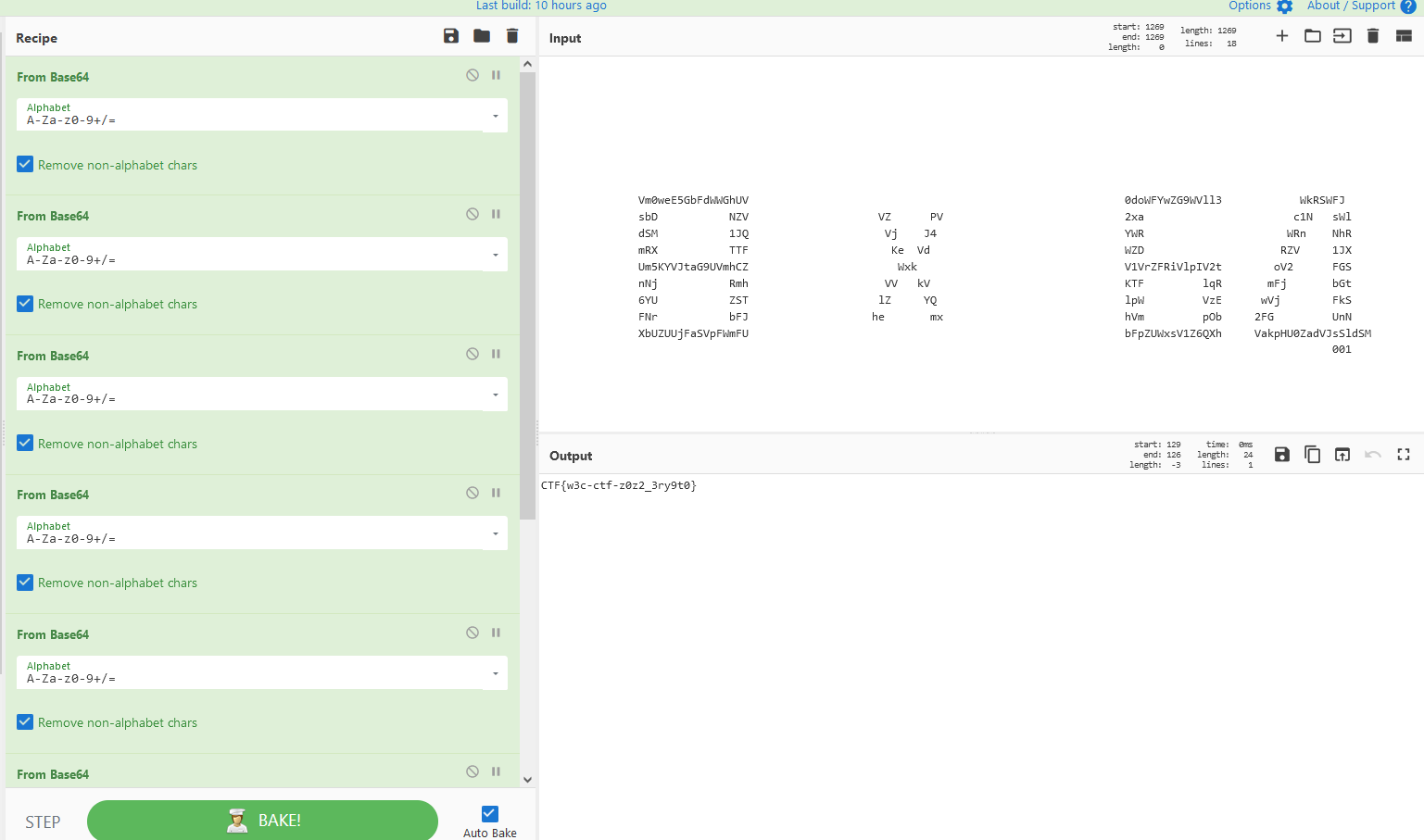
After trying multiple recipe in Cyberchef, i saw that 3 Base64 decode give me a result looking more to something sweet.
As the file name, we should use 8 times the base64 decode function :
Here’s the flag : CTF{w3c-ctf-z0z2_3ry9t0}
Forensics - The Cat Knows The Culprit
SCORE : 50
RESSOURCE : clue.jfif
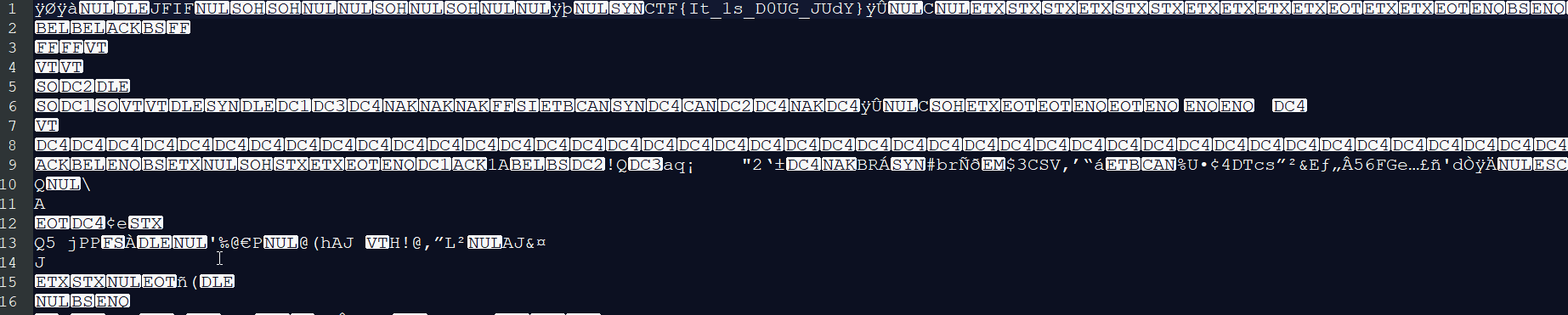
Open the .jfif with notepad++ by curiosity and i found the flag on the first line :
Flag : CTF{It_1s_D0UG_JUdY}
Forensics - Save Our Souls!
SCORE : 450
RESSOURCE : Message.wav
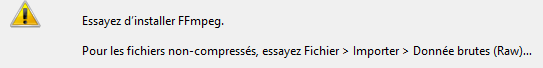
Opened the file with audacity. I got an error saying “For non-compress files, try > file > import > Raw data” :
Then accepted the import settings.
The sound is correctly imported.
Let’s look the spectrogram :
There is the Flag : CTF{WE-NEED-REINFOCEMENTS}