This room aims towards helping everyone learn about the basics of “Malware Reverse Engineering”.
THM Room https://tryhackme.com/room/basicmalwarere
TASK 1 : Introduction
Read the above.
No Answer.
TASK 2 : Strings :: Challenge 1
What is the flag of which that MD5 gets generated?
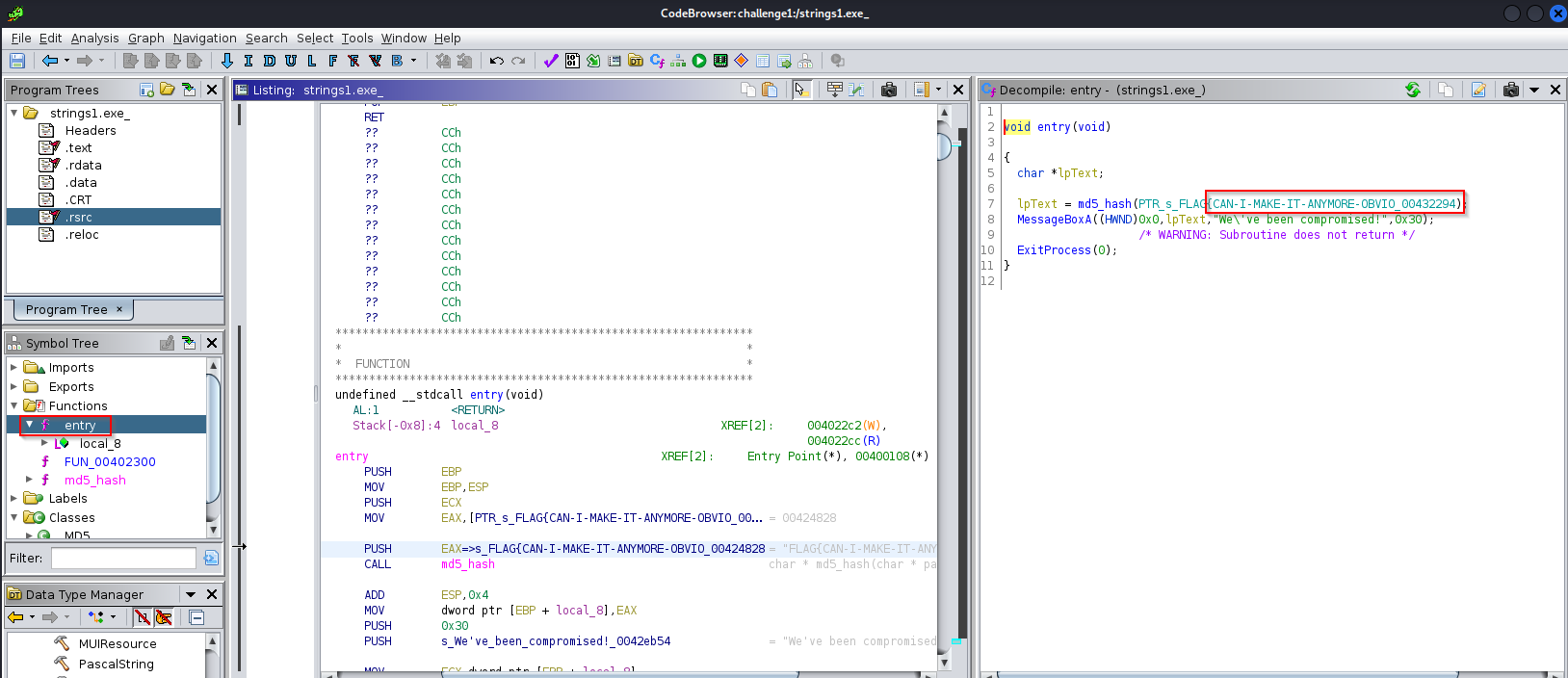
Using Ghidra tool and opening codebrowser then analysing the code, i found in the functions a call to md5_hash with a flag before :
Answer : FLAG{CAN-I-MAKE-IT-ANYMORE-OBVIOUS}
TASK 3 : Strings :: Challenge 2
What is the required password to authenticate with?
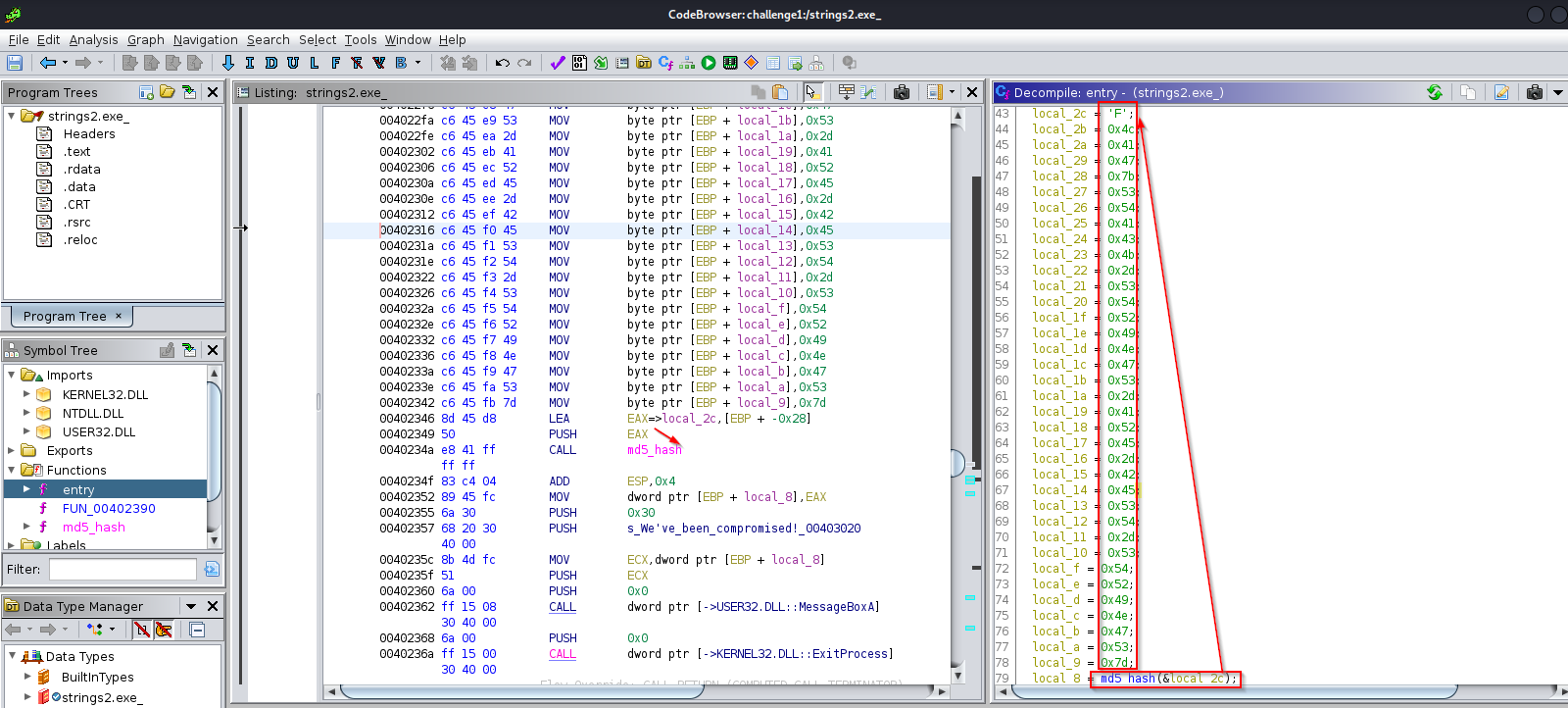
Looking at the code this times the same manner as above, i see that the md5_hash function is called on a pointer to “local_2c” variable. The assembly code is concatenating all of these variables before calling the hash function :
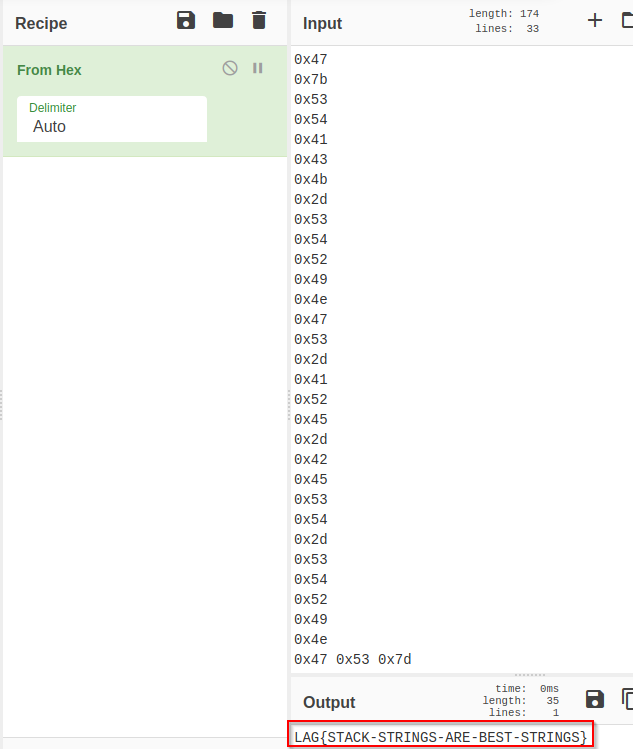
Putting all the strings values in cyberchef i got the flag with the missing F already harcode in “local_2c” :
Answer : FLAG{STACK-STRINGS-ARE-BEST-STRINGS}
TASK 4 : Strings :: Challenge 3
What is the “hidden” THM{} flag?
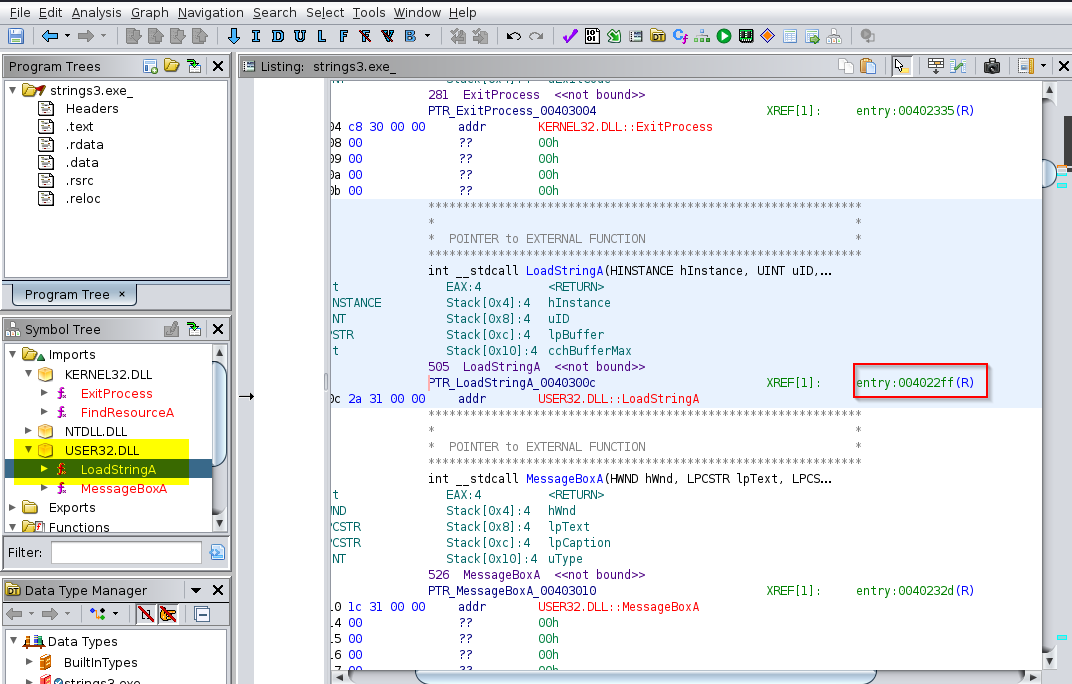
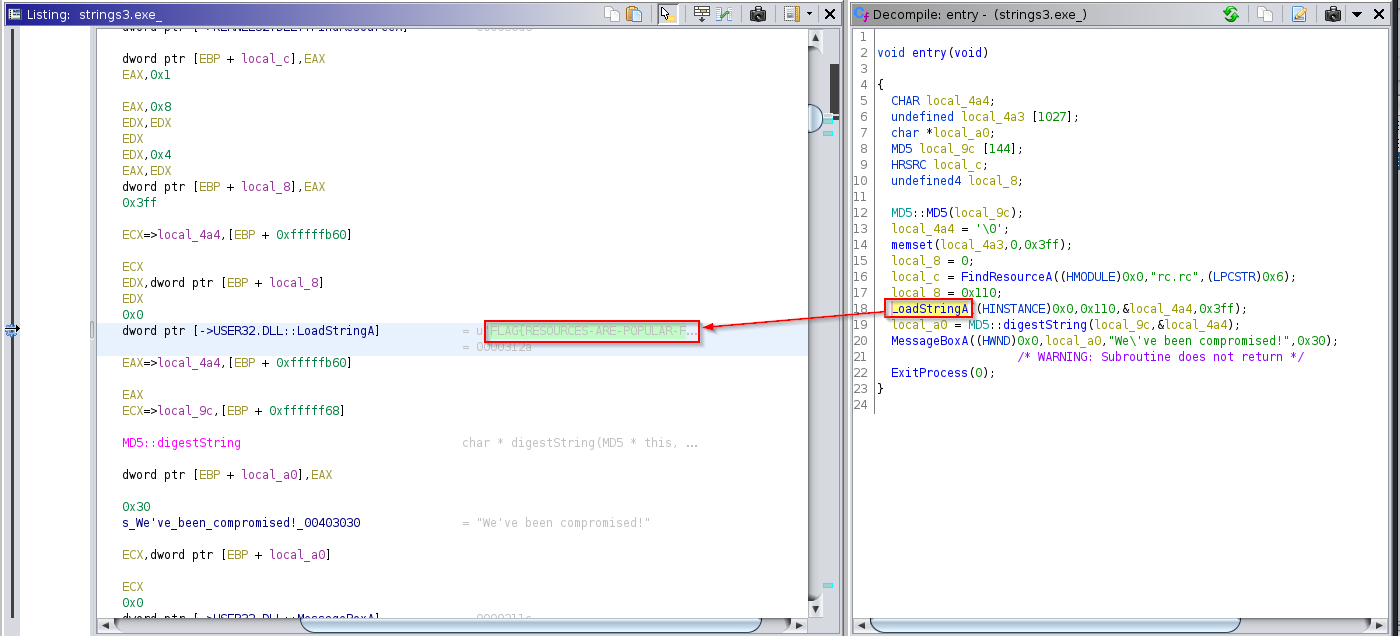
While analysing the code for the 3rd file, i found an entry number in the “LoadStringA” function which is called in the code before the hash part :
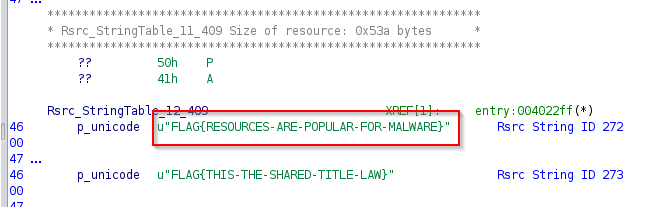
The left panel of Ghidra show me a part of the flag referenced by the call. I need further information to get the full flag. I got this looking the table of the flag strings at the entrey found above (004022ff) :
Answer : FLAG{RESOURCES-ARE-POPULAR-FOR-MALWARE}