This room will discuss the various resources MITRE has made available for the cybersecurity community. THM Room https://tryhackme.com/room/mitre
TASK 1 : Introduction to MITRE
Read the above
No Answer
TASK 2 : Basic Terminology
Read the above
No Answer
TASK 3 : ATT&CK® Framework
To summarize, we can use the ATT&CK Matrix to map a threat group to their tactics and techniques. There are various methods the search can be initiated. The questions below will help you become more familiar with the ATT&CK®. It is recommended to start answering the questions from the Phishing page. To answer these questions, just read the text and navigate througt MITRE.
Only blue teamers will use the ATT&CK Matrix? (Yay/Nay)
Answer : NAY
What is the ID for this technique?
Answer : T1566
Based on this technique, what mitigation covers identifying social engineering techniques?
Answer : User Training
There are other possible areas for detection for this technique, which occurs after what other technique?
Answer : User Execution
What group has used spear phishing in their campaigns?
Answer : Dragonfly
Based on the information for this group, what are their associated groups?
Answer : TG-4192, Crouching Yeti, IRON LIBERTY, Energetic Bear
What tool is attributed to this group to transfer tools or files from one host to another within a compromised environment?
Answer : PsExec
Based on the information about this tool, what group used a customized version of it?
Answer : FIN5
This group has been active since what year?
Answer : 2008
Instead of Mimikatz, what OS Credential Dumping tool does this group use?
Answer : Windows Credential Editor
TASK 4 : CAR Knowledge Base
To take full advantage of CAR, we can view the Full Analytic List or the CAR ATT&CK® Navigator layer to view all the analytics.
For the above analytic, what is the pseudocode a representation of?
Answer : Splunk search
What tactic has an ID of TA0003?
Answer : Persistence
What is the name of the library that is a collection of Zeek (BRO) scripts?
Answer : BZAR
What is the name of the technique for running executables with the same hash and different names?
Answer : Masquerading
Examine CAR-2013-05-004, what additional information is provided to analysts to ensure coverage for this technique?
Answer : Unit Tests
TASK 5 : Shield Active Defense
Which Shield tactic has the most techniques?
Answer : Detect
Is the technique ‘Decoy Credentials’ listed under the tactic from question #1? (Yay/Nay)
Answer : YAY
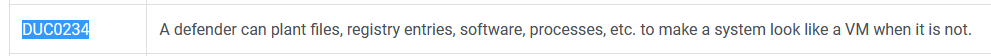
Explore DTE0011, what is the ID where a defender can plant artifacts on a system to make it look like a virtual machine to the adversary?
Answer : DUC0234
Based on the above use case, what is its ATT&CK® Technique mapping?
Answer : T1497
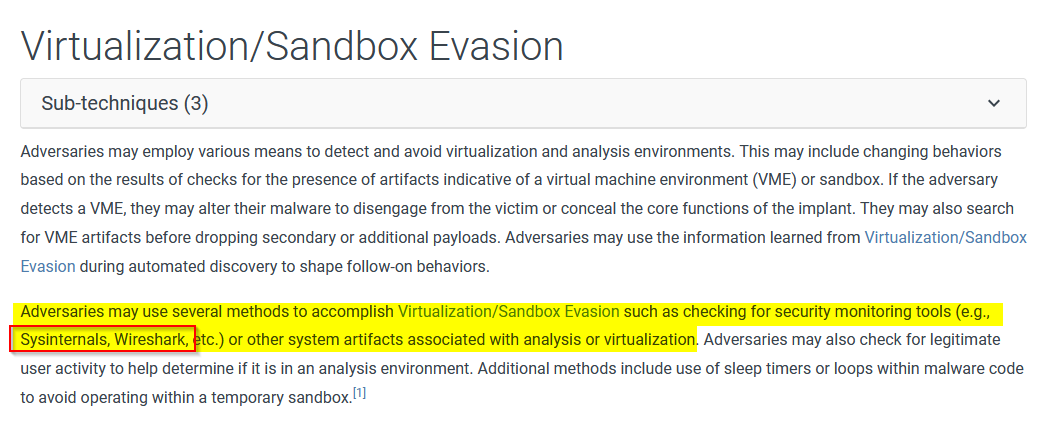
Continuing from the previous question, look at the information for this ATT&CK® Technique, what 2 programs are listed that adversary’s will check for?
Answer : Sysinternals and Wireshark
TASK 6 : ATT&CK® Emulation Plans
How many phases does APT3 Emulation Plan consists of?
Checked : https://attack.mitre.org/resources/adversary-emulation-plans/
Answer : 3
Under Persistence, what binary was replaced with cmd.exe?
take a look here : https://attack.mitre.org/docs/APT3_Adversary_Emulation_Plan.pdf
Answer : sethc.exe
Examining APT29, what 2 tools were used to execute the first scenario?
Read https://github.com/center-for-threat-informed-defense/adversary_emulation_library/tree/master/apt29, it has interesting scenarios !
Answer : Pupy and Metasploit
What tool was used to execute the second scenario?
Answer : PoshC2
TASK 7 : ATT&CK® and Threat Intelligence
What is a group that targets your sector who has been in operation since at least 2013?
I go to ATT&CK from MITRE in the group section then search on the page “aviation” and arrive on APT33 group.
Answer : APT33
Does this group use Stuxnet? (Yay/Nay)
Just searched “Stuxnet” on this page
Answer : NAY
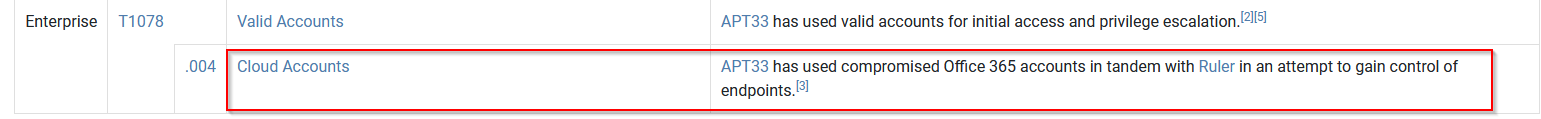
As your organization is migrating to the cloud, is there anything attributed to this APT group that you should focus on? If so, what is it?
Looking for “Cloud” threat on yes they have.
Answer : Cloud Account
What tool is associated with this technique?
Answer : Ruler
Per the detection tip, what should you be detecting?
Check the right page : https://attack.mitre.org/techniques/T1078/004/ !
Answer : Abnormal or malicious behavior
What platforms does this affect?
Answer : Azure AD, Google Workspace, IaaS, Office 365, SaaS
TASK 8 : Conclusion
Read the above
No Answer