Learn how to apply Operations Security (OPSEC) process for Red Teams.
THM Room https://tryhackme.com/room/opsec
TASK 1 : Introduction
Aim to memorize the five steps of the OPSEC process as we explain each one in its own task.
As a red team member, your potential adversaries are the blue team and third parties. The blue team is considered an adversary as we are attacking the systems they are hired to monitor and defend. Red vs. blue team exercises are common to help an organization understand what threats exist in a given environment and better prepare their blue team if a real malicious attack occurs. As red teamers, even though we are abiding by the law and authorized to attack systems within a defined scope, it does not change the fact that we are acting against the blue team’s objectives and trying to circumvent their security controls. The blue team wants to protect their systems, while we want to penetrate them.
The OPSEC process has five steps :
1- Identify critical information
2- Analyse threats
3- Analyse vulnerabilities
4- Assess risks
5- Apply appropriate countermeasures
No Answer
TASK 2 : Critical Information Identification
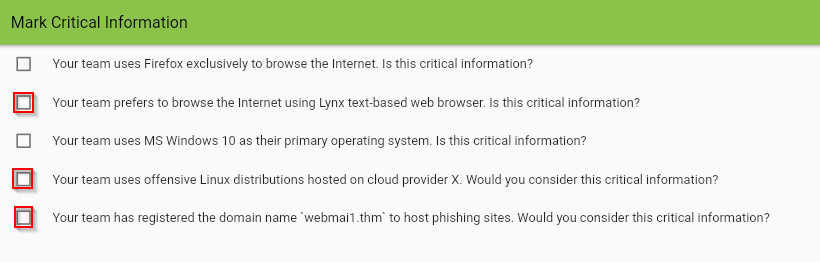
Click on View Site and follow through till you get the flag. (Please note that some browser extensions, such as NoScript, might prevent the site from loading correctly.)
Answer : THM{OPSEC_CRITICAL_INFO}
TASK 3 : Threat Analysis
Try to think of at least one adversary who is not a threat and one who is a threat.
Just read the text.
No Answer
TASK 4 : Vulnerability Analysis
Your red team uses THC-Hydra to find the password for a specific login page. Moreover, they are using the Metasploit framework on the same system as THC-Hydra. Would you consider this an OPSEC vulnerability? (Y/N)
Answer : Y
One of the red team members posts a photo of his cat every day. Would this be considered an OPSEC vulnerability? (Y/N)
Answer : N
Your red team went for dinner, took a photo, and tagged every team member on a popular social media platform. Would you consider this an OPSEC vulnerability? (Y/N)
Answer : Y
Your red team posts on its website a list of clients you regularly conduct red team exercises with. Would you consider this an OPSEC vulnerability? (Y/N)
Answer : Y
One of your red team members posted a photo of her morning coffee. Would you consider this an OPSEC vulnerability? (Y/N)
Answer : N
TASK 5 : Risk Assessment
Your red team uses THC-Hydra to find the password for a specific login page. Moreover, they are using the Metasploit framework on the same system as THC-Hydra. Knowing that your target uses a properly configured Intrusion Detection System (IDS), would you consider this vulnerability as high risk? (Y/N)
Answer : Y
TASK 6 : Countermeasures
This concludes the fifth element in the OPSEC process. Let’s get ready before we apply all five elements to other instances of critical information.
No Answer
TASK 7 : More Practical Examples
Click on View Site and follow through till you get the flag. (Please note that some browser extensions, such as NoScript, might prevent the site from loading correctly.)
There are four subquestions here :
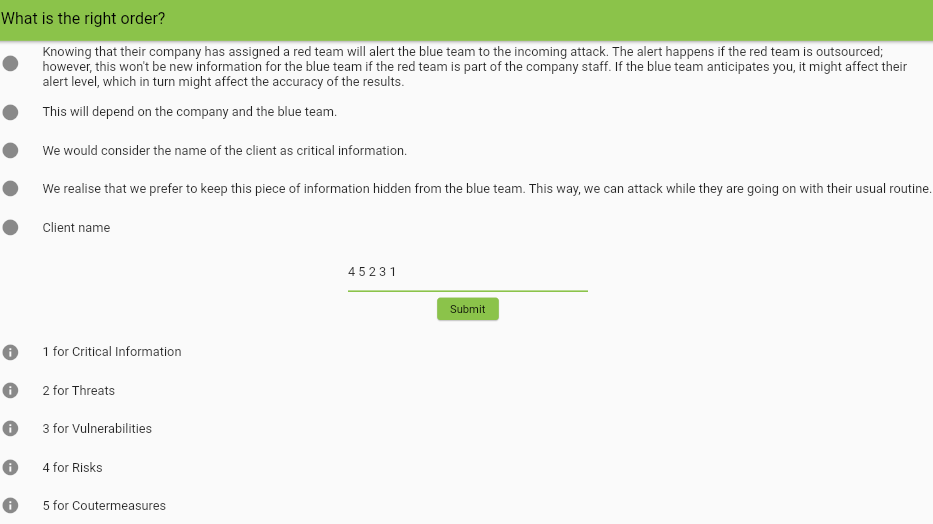
Answer : 4 5 2 3 1
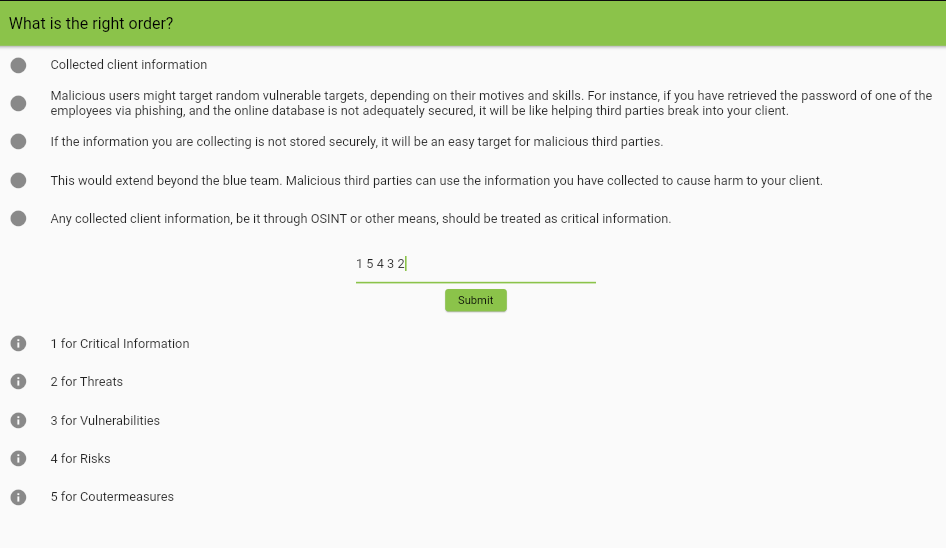
Answer : 1 5 4 3 2
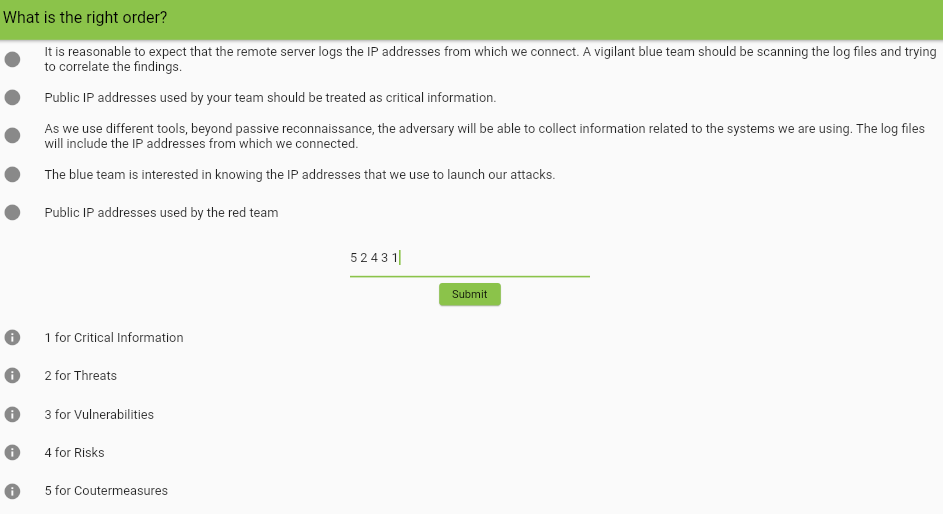
Answer : 5 2 4 3 1
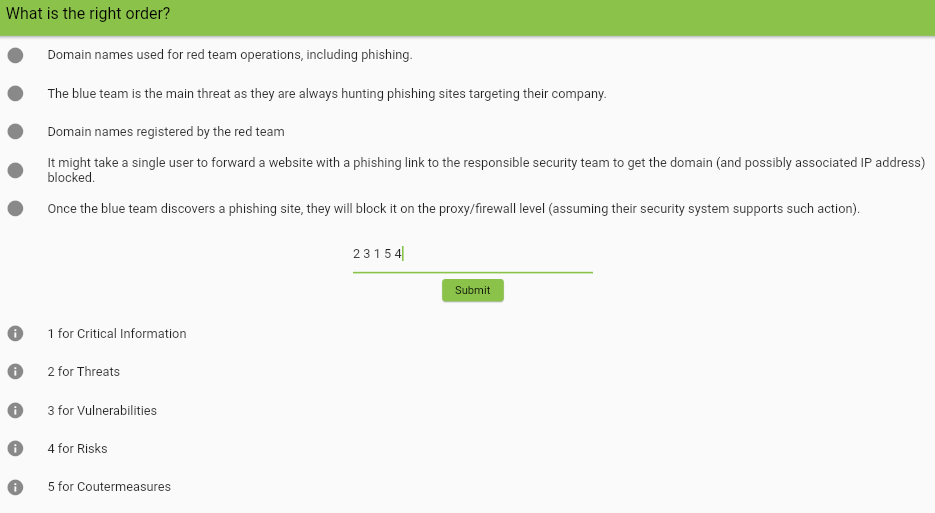
Answer : 2 3 1 5 4
TASK 8 : Summary
Memorise the five elements of the OPSEC process and learn how to apply them to the different aspects of your cybersecurity work.
No Answer