Learn how to identify, detect, mitigate and report a vulnerability effectively.
THM Room : https://tryhackme.com/room/vulnerabilitymanagementkj
TASK 1 Introduction
I have completed the prerequisites and I’m ready to start.
No Answer.
TASK 2 Vulnerability Management vs Vulnerability Scanning
The process encompassing vulnerability scanning and other factors, such as risk acceptance, is called?
Answer : vulnerability management
Is the overall objective of vulnerability management to increase an organisation’s risk exposure? (yea/nay)
The objective is to reduce the exposure.
Answer : NAY
TASK 3 Vulnerability Classification
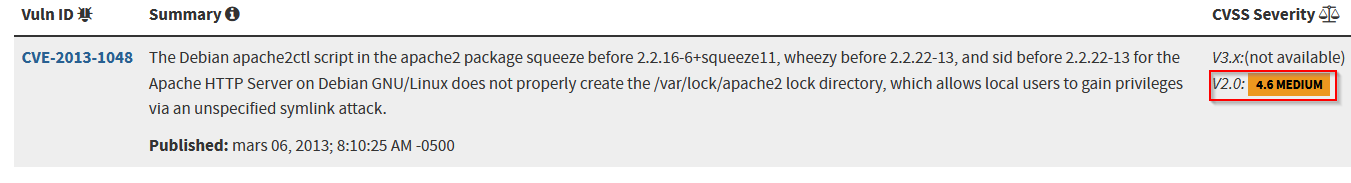
What is the CVSS for CVE-2013-1048?
Answer : 4.6
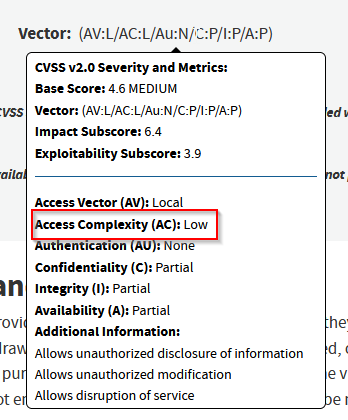
What is the Access Complexity for CVE-2013-1048?
Answer : low
With the fictional CVE-2023-2022, what would the CVE ID assign year be?
The year assigned to a CVE is the first part XXXX of the CVE number CVE-XXXX-YYYY.
Answer : 2023
TASK 4 Vulnerability Management Life Cycle - Discover & Prioritise
We have already scanned an Ubuntu machine; therefore, answer the following questions based on the scan report of LinuxAppTask task.
No Answer.
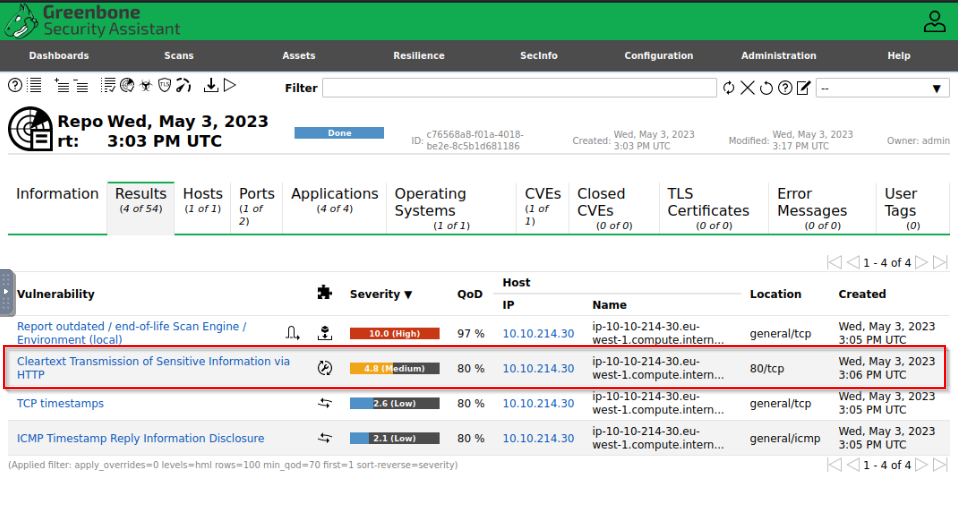
After scanning, what is the total number of medium-level vulnerabilities?
After going in the LinuxApp scan report, we can view the number of vulnerabilities found :
Answer : 1
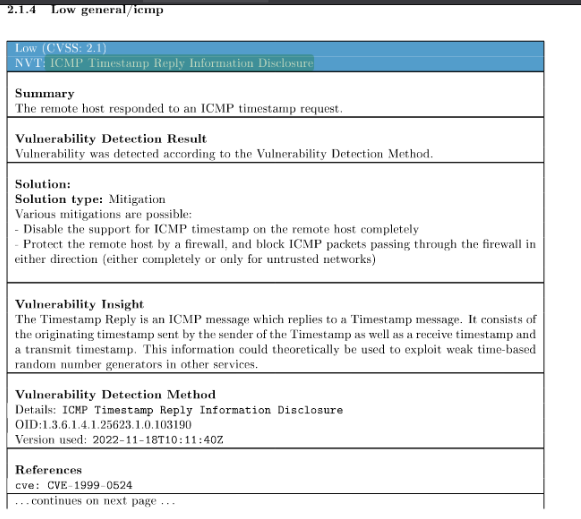
What is the severity score for the vulnerability “ICMP Timestamp Reply Information Disclosure”?
From previous question image.
Answer : 2.1
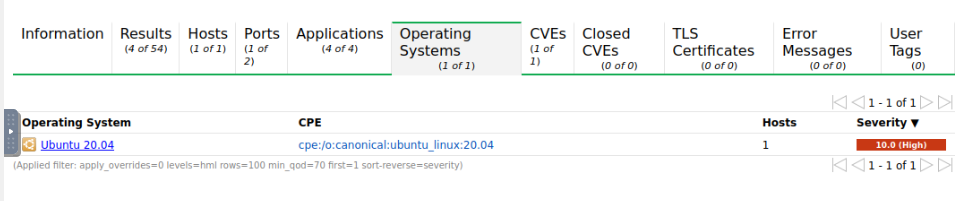
What is the operating system and the version number of the target machine?
Answer : ubuntu 20.04
TASK 5 Vulnerability Management Life Cycle - Assess & Report
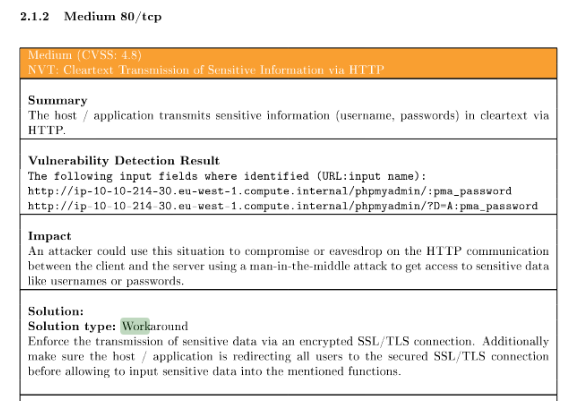
Download the LinuxAppTask report in PDF format. What is the severity rating of the vulnerability in the report, where the solution type is “Workaround”?
Answer : medium
What is the solution type for the “TCP timestamps” vulnerability?
Answer : Mitigation
What is the CVE for “ICMP Timestamp Reply Information Disclosure”?
Answer : CVE-1999-0524
TASK 6 Vulnerability Management Life Cycle - Remediate & Verify
Create a ticket for resolving the “Cleartext Transmission of Sensitive Information via HTTP” vulnerability.
No Answer.
As a Security Engineer, the priority of a remediation ticket for a critical vulnerability must be (high/medium/low)?
Answer : high
TASK 7 Vulnerability Management Framework
The process of listing vulnerabilities as per their order of priority is called?
“Prioritise vulnerabilities: Since every enterprise has a large number of vulnerabilities, it is essential to prioritise vulnerabilities for remediation, ensuring that the responsible team takes adequate measures to fix vulnerabilities based on their priority.”
Answer : Prioritise vulnerabilities
Which phase entails updating and strengthening resilience plans and restoring any compromised capabilities or services caused by a cybersecurity event?
Answer : recover
I have read the details regarding all five phases of the NIST CSF.
No Answer.
TASK 8 Conclusion
I have completed the room successfully.
No Answer.