THM Room https://tryhackme.com/room/yara
TASK 1 : Introduction
Let’s get started
No Answer
TASK 2 : What is Yara?
2.3. Caveat: Malware Analysis Explaining the functionality of malware is vastly out of scope for this room due to the sheer size of the topic. I have covered strings in much more detail in “Task 12 - Strings” of my MAL: Introductory room. In fact, I am creating a whole Learning Path for it. If you’d like to get a taster whilst learning the fundamentals, I’d recommend my room.
What is the name of the base-16 numbering system that Yara can detect?
Answer : Hex
Would the text “Enter your Name” be a string in an application? (Yay/Nay)
Answer : YAY
TASK 3 : Installing Yara (Ubuntu/Debian & Windows)
I’ve installed Yara and/or are using the attached VM!
No Answer
TASK 4 : Deploy
I’ve either connected to my instance or installed Yara on my own operating system!
No Answer
TASK 5 : Introduction to Yara Rules
One rule to - well - rule them all.
On the deploy machine and connected in SSH :
1
2
3
4
5
6
7
8
9
cmnatic@thm-yara:~/myyara$touch somefile
cmnatic@thm-yara:~/myyara$nano myrule
rule examplerule {
condition:true
}
cmnatic@thm-yara:~/myyara$ yara myfirstrule.yar somefile
examplerule somefile
cmnatic@thm-yara:~/myyara$ yara myfirstrule.yar somefile2
error scanning somefile2: could not open file
No Answer
TASK 6 : Expanding on Yara Rules
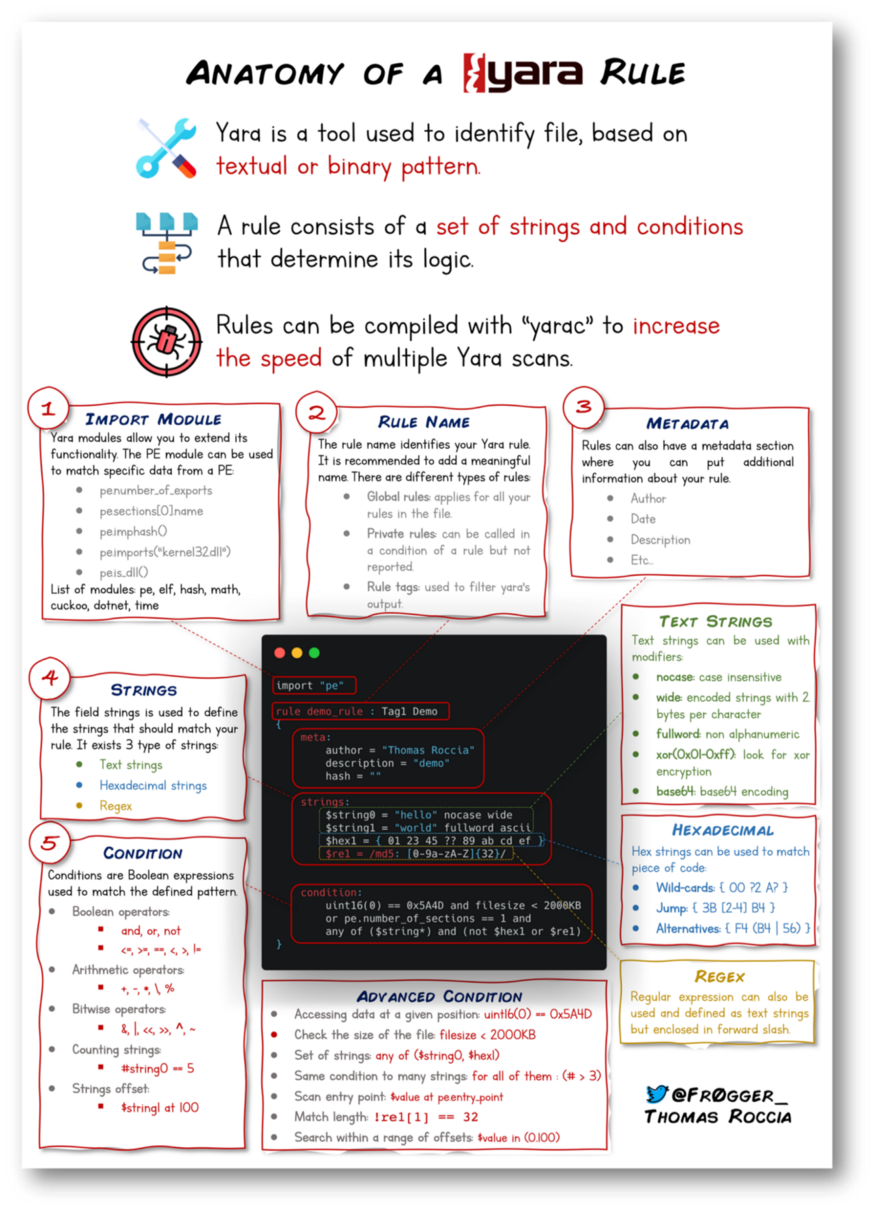
Information security researcher “fr0gger_” has recently created a handy cheatsheet that breaks down and visualises the elements of a YARA rule (shown above, all image credits go to him). It’s a great reference point in getting started!
Upwards and onwards…
No Answer
TASK 7 : Yara Modules
Sounds pretty cool!
No Answer
TASK 8 : Other tools and Yara
Cool tools. I’m ready to use one of them.
1- LOKI 2- THOR 3- FENRIR 4- YAYA
No Answer
TASK 9 : Using LOKI and its Yara rule set
Scenario: You are the security analyst for a mid-size law firm. A co-worker discovered suspicious files on a web server within your organization. These files were discovered while performing updates to the corporate website. The files have been copied to your machine for analysis. The files are located in the suspicious-files directory. Use Loki to answer the questions below.
Scan file 1. Does Loki detect this file as suspicious/malicious or benign?
1
2
3
4
5
6
cmnatic@thm-yara:~/suspicious-files/file1$ python ../../tools/Loki/loki.py -p .
[...]
[RESULT] Suspicious objects detected!
[RESULT] Loki recommends a deeper analysis of the suspicious objects.
[...]
Answer : suspicious
What Yara rule did it match on?
1
2
3
4
5
6
7
8
9
10
11
12
[...]
[INFO] Scanning . ...
[WARNING]
FILE: ./ind3x.php SCORE: 70 TYPE: PHP SIZE: 80992
FIRST_BYTES: 3c3f7068700a2f2a0a09623337346b20322e320a / <?php/*b374k 2.2
MD5: 1606bdac2cb613bf0b8a22690364fbc5
SHA1: 9383ed4ee7df17193f7a034c3190ecabc9000f9f
SHA256: 5479f8cd1375364770df36e5a18262480a8f9d311e8eedb2c2390ecb233852ad CREATED: Mon Nov 9 15:15:32 2020 MODIFIED: Mon Nov 9 13:06:56 2020 ACCESSED: Sat Oct 2 08:50:09 2021
REASON_1: Yara Rule MATCH: webshell_metaslsoft SUBSCORE: 70
DESCRIPTION: Web Shell - file metaslsoft.php REF: -
MATCHES: Str1: $buff .= "<tr><td><a href=\\"?d=".$pwd."\\">[ $folder ]</a></td><td>LINK</t
[...]
Answer : webshell_metaslsoft
What does Loki classify this file as?
1
2
3
4
5
6
7
8
9
10
11
12
[...]
[INFO] Scanning . ...
[WARNING]
FILE: ./ind3x.php SCORE: 70 TYPE: PHP SIZE: 80992
FIRST_BYTES: 3c3f7068700a2f2a0a09623337346b20322e320a / <?php/*b374k 2.2
MD5: 1606bdac2cb613bf0b8a22690364fbc5
SHA1: 9383ed4ee7df17193f7a034c3190ecabc9000f9f
SHA256: 5479f8cd1375364770df36e5a18262480a8f9d311e8eedb2c2390ecb233852ad CREATED: Mon Nov 9 15:15:32 2020 MODIFIED: Mon Nov 9 13:06:56 2020 ACCESSED: Sat Oct 2 08:50:09 2021
REASON_1: Yara Rule MATCH: webshell_metaslsoft SUBSCORE: 70
DESCRIPTION: Web Shell - file metaslsoft.php REF: -
MATCHES: Str1: $buff .= "<tr><td><a href=\\"?d=".$pwd."\\">[ $folder ]</a></td><td>LINK</t
[...]
Answer : Web Shell
Based on the output, what string within the Yara rule did it match on?
1
2
3
4
5
6
7
8
9
10
11
12
[...]
[INFO] Scanning . ...
[WARNING]
FILE: ./ind3x.php SCORE: 70 TYPE: PHP SIZE: 80992
FIRST_BYTES: 3c3f7068700a2f2a0a09623337346b20322e320a / <?php/*b374k 2.2
MD5: 1606bdac2cb613bf0b8a22690364fbc5
SHA1: 9383ed4ee7df17193f7a034c3190ecabc9000f9f
SHA256: 5479f8cd1375364770df36e5a18262480a8f9d311e8eedb2c2390ecb233852ad CREATED: Mon Nov 9 15:15:32 2020 MODIFIED: Mon Nov 9 13:06:56 2020 ACCESSED: Sat Oct 2 08:50:09 2021
REASON_1: Yara Rule MATCH: webshell_metaslsoft SUBSCORE: 70
DESCRIPTION: Web Shell - file metaslsoft.php REF: -
MATCHES: Str1: $buff .= "<tr><td><a href=\\"?d=".$pwd."\\">[ $folder ]</a></td><td>LINK</t
[...]
Answer : Str1
What is the name and version of this hack tool?
1
2
3
4
5
6
7
8
9
10
11
12
[...]
[INFO] Scanning . ...
[WARNING]
FILE: ./ind3x.php SCORE: 70 TYPE: PHP SIZE: 80992
FIRST_BYTES: 3c3f7068700a2f2a0a09623337346b20322e320a / <?php/*b374k 2.2
MD5: 1606bdac2cb613bf0b8a22690364fbc5
SHA1: 9383ed4ee7df17193f7a034c3190ecabc9000f9f
SHA256: 5479f8cd1375364770df36e5a18262480a8f9d311e8eedb2c2390ecb233852ad CREATED: Mon Nov 9 15:15:32 2020 MODIFIED: Mon Nov 9 13:06:56 2020 ACCESSED: Sat Oct 2 08:50:09 2021
REASON_1: Yara Rule MATCH: webshell_metaslsoft SUBSCORE: 70
DESCRIPTION: Web Shell - file metaslsoft.php REF: -
MATCHES: Str1: $buff .= "<tr><td><a href=\\"?d=".$pwd."\\">[ $folder ]</a></td><td>LINK</t
[...]
Answer : b374k 2.2
Inspect the actual Yara file that flagged file 1. Within this rule, how many strings are there to flag this file?
Looking at yara/thor-webshells.yar : 1
Answer : 1
Scan file 2. Does Loki detect this file as suspicious/malicious or benign?
1
2
3
4
[INFO] Scanning . ...
[NOTICE] Results: 0 alerts, 0 warnings, 7 notices
[RESULT] SYSTEM SEEMS TO BE CLEAN.
[INFO] Please report false positives via https://github.com/Neo23x0/signature-base
It’s CLEAN !
Answer : benign
Inspect file 2. What is the name and version of this web shell?
1
2
3
4
5
6
7
8
9
cmnatic@thm-yara:~/suspicious-files/file2$ nano 1ndex.php
<?php
/*
b374k shell 3.2.3
Jayalah Indonesiaku
(c)2014
https://github.com/b374k/b374k
*/
Answer : b374k 3.2.3
TASK 10 : Creating Yara rules with yarGen
From within the root of the suspicious files directory, what command would you run to test Yara and your Yara rule against file 2?
1
yara file2.yar file2/1ndex.php
Answer : yara file2.yar file2/1ndex.php
Did Yara rule flag file 2? (Yay/Nay)
Answer : YAY
Copy the Yara rule you created into the Loki signatures directory.
1
2
3
4
5
cmnatic@thm-yara:~/suspicious-files$ ls
file1 file2 file2.yar
cmnatic@thm-yara:~/suspicious-files$ yara file2.yar file2/1ndex.php
_home_cmnatic_suspicious_files_file2_1ndex file2/1ndex.php
mnatic@thm-yara:~/suspicious-files$ cp file2.yar ../tools/Loki/signature-base/yara/
No Answer
Test the Yara rule with Loki, does it flag file 2? (Yay/Nay)
1
2
cmnatic@thm-yara:~/suspicious-files$ cd file2
cmnatic@thm-yara:~/suspicious-files/file2$ python ../../tools/Loki/loki.py -p .
Answer : YAY
What is the name of the variable for the string that it matched on?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
[INFO] Scanning . ...
[WARNING]
FILE: ./1ndex.php SCORE: 70 TYPE: PHP SIZE: 223978
FIRST_BYTES: 3c3f7068700a2f2a0a09623337346b207368656c / <?php/*b374k shel
MD5: c6a7ebafdbe239d65248e2b69b670157
SHA1: 3926ab64dcf04e87024011cf39902beac32711da
SHA256: 53fe44b4753874f079a936325d1fdc9b1691956a29c3aaf8643cdbd49f5984bf CREATED: Mon Nov 9 15:16:03 2020 MODIFIED: Mon Nov 9 13:09:18 2020 ACCESSED: Sat Oct 2 09:14:14 2021
REASON_1: Yara Rule MATCH: _home_cmnatic_suspicious_files_file2_1ndex SUBSCORE: 70
DESCRIPTION: file2 - file 1ndex.php REF: https://github.com/Neo23x0/yarGen
MATCHES: Str1: var Zepto=function(){function G(a){return a==null?String(a):z[A.call(a)]||"object"}function H(a){return G(a)=="function"}fun Str2: $c ... (truncated)
[WARNING]
FILE: ./loki_thm-yara_2021-10-02_09-14-10.log SCORE: 70 TYPE: UNKNOWN SIZE: 2884
FIRST_BYTES: 32303231313030325430393a31343a31305a2074 / 20211002T09:14:10Z t
MD5: 05cc8d1df6d47cc08f4a64315a820466
SHA1: 2d690db5d408761f99ae4071ea8f0004e2546e52
SHA256: fedc4013d3176d3722caadb3057aa6efe6a588cf5f5ced62f765979d39d193b5 CREATED: Sat Oct 2 09:14:14 2021 MODIFIED: Sat Oct 2 09:14:14 2021 ACCESSED: Sat Oct 2 09:20:09 2021
REASON_1: Yara Rule MATCH: loki_thm_yara_2021_10_02_09_14_10 SUBSCORE: 70
DESCRIPTION: file2 - file loki_thm-yara_2021-10-02_09-14-10.log REF: https://github.com/Neo23x0/yarGen
MATCHES: Str1: 20211002T09:14:10Z thm-yara LOKI: Notice: MODULE: PESieve MESSAGE: PE-Sieve successfully initialized BINARY: /home/cmnatic/tools Str2 ... (truncated)
[WARNING]
FILE: ./loki_thm-yara_2021-10-02_09-20-05.log SCORE: 70 TYPE: UNKNOWN SIZE: 2884
FIRST_BYTES: 32303231313030325430393a32303a30355a2074 / 20211002T09:20:05Z t
MD5: 78fbf9ed13860c9e6ed8b9a263f981f8
SHA1: a718b6d811261e4cdd291109c5e6564bf54f47a4
SHA256: 79acd50f6f233a388c8e822e6d96b9fc6d5aaf7aebdf4d6d1b2b720515f98558 CREATED: Sat Oct 2 09:20:09 2021 MODIFIED: Sat Oct 2 09:20:09 2021 ACCESSED: Sat Oct 2 09:35:38 2021
REASON_1: Yara Rule MATCH: loki_thm_yara_2021_10_02_09_20_05 SUBSCORE: 70
DESCRIPTION: file2 - file loki_thm-yara_2021-10-02_09-20-05.log REF: https://github.com/Neo23x0/yarGen
MATCHES: Str1: 20211002T09:20:05Z thm-yara LOKI: Notice: MODULE: PESieve MESSAGE: PE-Sieve successfully initialized BINARY: /home/cmnatic/tools Str2 ... (truncated)
[NOTICE] Results: 0 alerts, 3 warnings, 7 notices
[RESULT] Suspicious objects detected!
[RESULT] Loki recommends a deeper analysis of the suspicious objects.
[INFO] Please report false positives via https://github.com/Neo23x0/signature-base
[NOTICE] Finished LOKI Scan SYSTEM: thm-yara TIME: 20211002T09:43:04Z
MATCHES: Str1: var Zepto=function()
Answer : Zepto
Inspect the Yara rule, how many strings were generated?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
nano file2.yar
[...]
rule _home_cmnatic_suspicious_files_file2_1ndex {
meta:
description = "file2 - file 1ndex.php"
author = "yarGen Rule Generator"
reference = "https://github.com/Neo23x0/yarGen"
date = "2021-10-02"
hash1 = "53fe44b4753874f079a936325d1fdc9b1691956a29c3aaf8643cdbd49f5984bf"
strings:
$x1 = "var Zepto=function(){function G(a){return a==null?String(a):z[A.call(a)]||\"object\"}function H(a){retu$
$s2 = "$cmd = execute(\"taskkill /F /PID \".$pid);" fullword ascii
$s3 = "$cmd = trim(execute(\"ps -p \".$pid));" fullword ascii
$s4 = "return (res = new RegExp('(?:^|; )' + encodeURIComponent(key) + '=([^;]*)').exec(document.cookie)) ? (r$
$s5 = "$buff = execute(\"wget \".$url.\" -O \".$saveas);" fullword ascii
$s6 = "$buff = execute(\"curl \".$url.\" -o \".$saveas);" fullword ascii
$s7 = "(d=\"0\"+d);dt2=y+m+d;return dt1==dt2?0:dt1<dt2?-1:1},r:function(a,b){for(var c=0,e=a.length-1,g=h;g;){$
$s8 = "$cmd = execute(\"kill -9 \".$pid);" fullword ascii
$s9 = "$cmd = execute(\"tasklist /FI \\\"PID eq \".$pid.\"\\\"\");" fullword ascii
$s10 = "$body = preg_replace(\"/<a href=\\\"http:\\/\\/www.zend.com\\/(.*?)<\\/a>/\", \"\", $body);" fullword $
$s11 = "execute(\"tar xzf \\\"\".basename($archive).\"\\\" -C \\\"\".$target.\"\\\"\");" fullword ascii
$s12 = "execute(\"tar xf \\\"\".basename($archive).\"\\\" -C \\\"\".$target.\"\\\"\");" fullword ascii
$s13 = "ngs.mimeType||xhr.getResponseHeader(\"content-type\")),result=xhr.responseText;try{dataType==\"script\$
$s14 = "$check = strtolower(execute(\"perl -h\"));" fullword ascii
$s15 = "$check = strtolower(execute(\"gcc --help\"));" fullword ascii
$s16 = "$check = strtolower(execute(\"javac -help\"));" fullword ascii
$s17 = "/* Zepto v1.1.2 - zepto event ajax form ie - zeptojs.com/license */" fullword ascii
$s18 = "$check = strtolower(execute(\"node -h\"));" fullword ascii
$s19 = "$check = strtolower(execute(\"nodejs -h\"));" fullword ascii
$s20 = "$buff = execute(\"lynx -source \".$url.\" > \".$saveas);" fullword ascii
condition:
uint16(0) == 0x3f3c and filesize < 700KB and
1 of ($x*) and 4 of them
}
[...]
Answer : 20
One of the conditions to match on the Yara rule specifies file size. The file has to be less than what amount?
Answer : 700KB
TASK 11 : Valhalla
Picking up from our scenario, at this point, you know that the 2 files are related. Even though Loki classified the files are suspicious, you know in your gut that they are malicious. Hence the reason you created a Yara rule using yarGen to detect it on other web servers. But let’s further pretend that you are not code-savvy (FYI - not all security professionals know how to code/script or read it). You need to conduct further research regarding these files to receive approval to eradicate these files from the network.
Time to use Valhalla for some threat intelligence gathering…
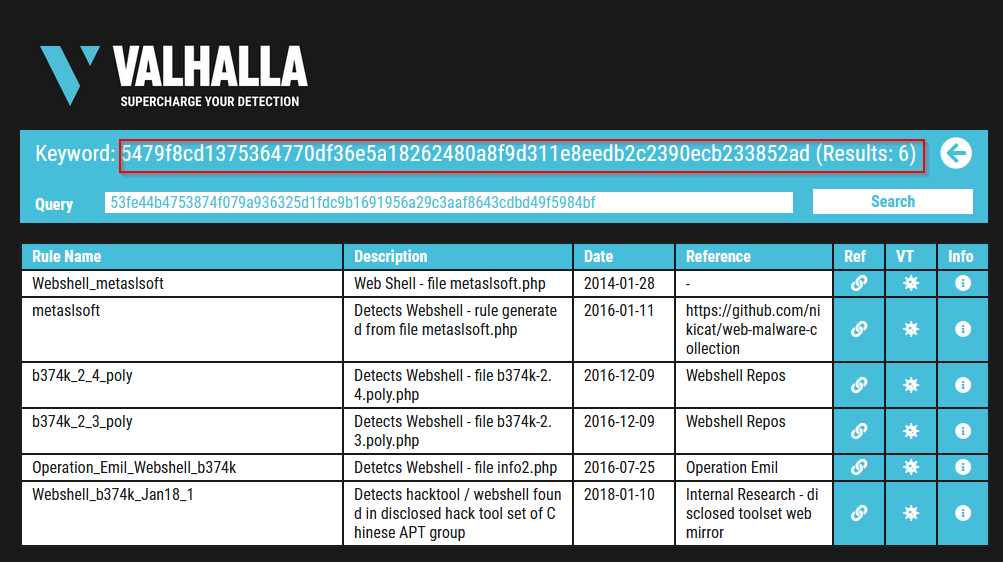
Enter the SHA256 hash of file 1 into Valhalla. Is this file attributed to an APT group? (Yay/Nay)
Answer : YAY
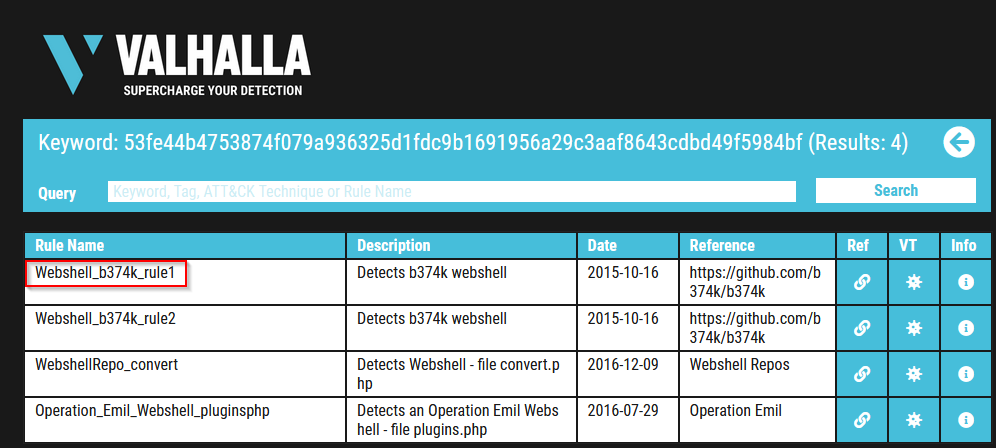
Do the same for file 2. What is the name of the first Yara rule to detect file 2?
Answer : Webshell_b374k_rule1
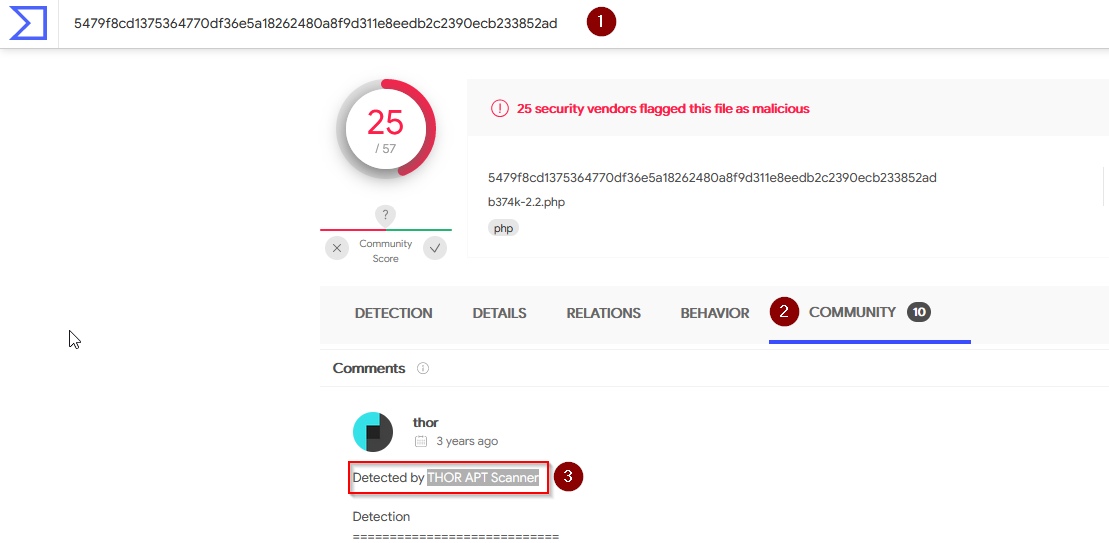
Examine the information for file 2 from Virus Total (VT). The Yara Signature Match is from what scanner?
Answer : THOR APT Scanner
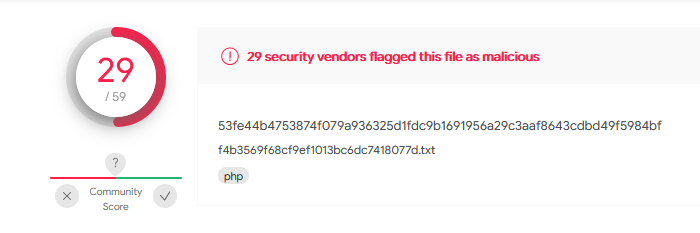
Enter the SHA256 hash of file 2 into Virus Total. Did every AV detect this as malicious? (Yay/Nay)
No only 29 at this time.
Answer : NAY
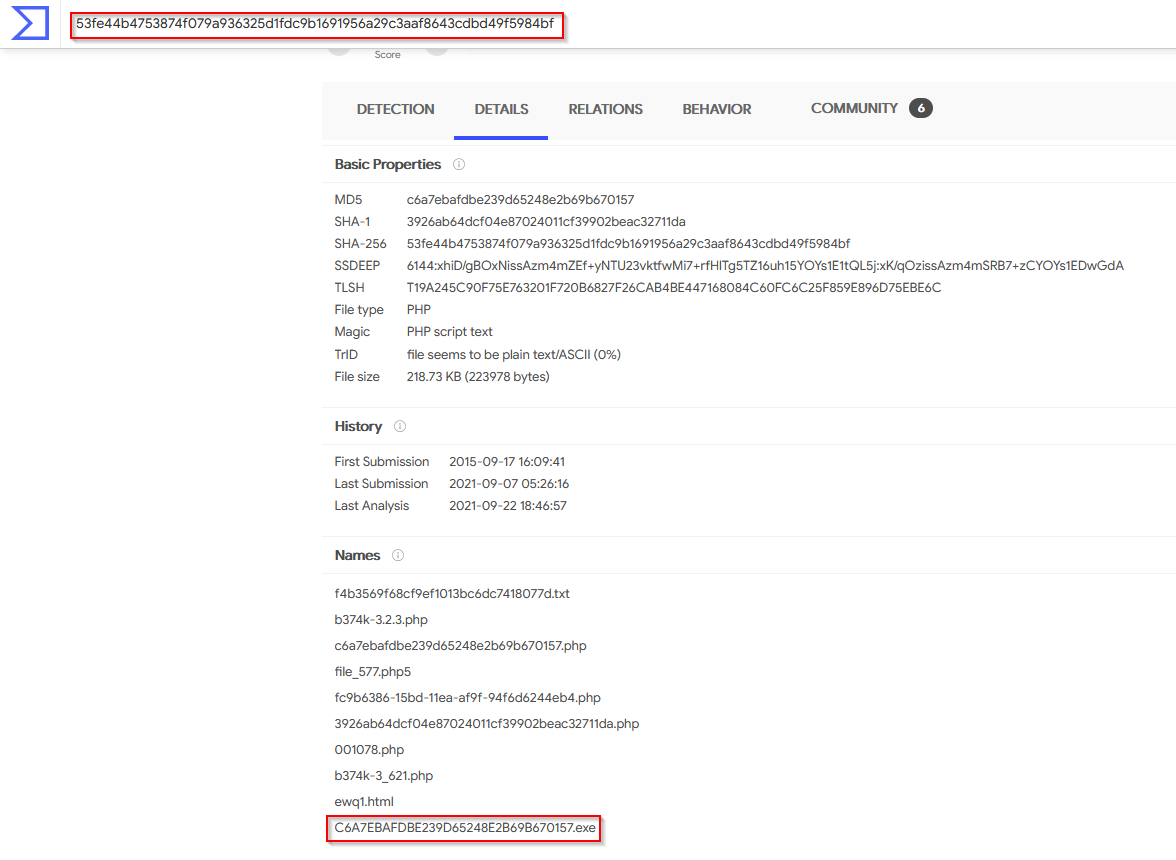
Besides .PHP, what other extension is recorded for this file?
Answer : exe
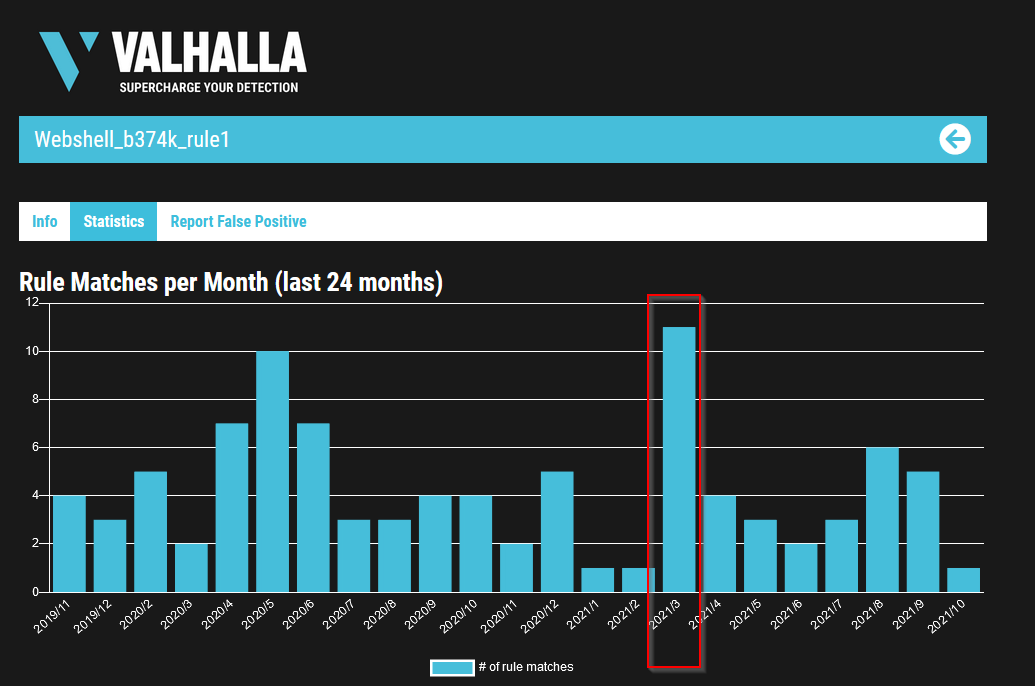
Back to Valhalla, inspect the Info for this rule. Under Statistics what was the highest rule match per month in the last 2 years? (YYYY/M)
Answer : 2021/3
What JavaScript library is used by file 2?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
https://github.com/b374k/b374k/blob/master/index.php
[...]
/* JAVASCRIPT AND CSS FILES START */
$zepto_code = packer_read_file($GLOBALS['packer']['base_dir']."zepto.js");
$js_main_code = "\n\n".packer_read_file($GLOBALS['packer']['base_dir']."main.js");
$js_code = "\n\n".packer_read_file($GLOBALS['packer']['base_dir']."sortable.js").$js_main_code;
$js_code .= "\n\n".packer_read_file($GLOBALS['packer']['base_dir']."base.js");
if(isset($_COOKIE['packer_theme'])) $theme = $_COOKIE['packer_theme'];
else $theme ="default";
$css_code = packer_read_file($GLOBALS['packer']['theme_dir'].$theme.".css");
[...]
Answer : zepto
Is this Yara rule in the default Yara file Loki uses to detect these type of hack tools? (Yay/Nay)
We had to generate this rule !
Answer : NAY
TASK 12 : Conclusion
No answer needed.
No Answer